
What Is SOC 2? A Definitive Guide
SOC 2 is a report that shows a company has clear rules and checks in place to protect customer data and maintain a strong security posture. It focuses on keeping systems secure, keeping services available, processing data correctly, protecting confidential information, and handling personal data responsibly.
Customers often ask for SOC 2 to confirm a vendor takes security seriously and can be trusted with sensitive information, including how the vendor approaches vendor management and service level agreements.
Its importance is clear in recent breach figures, since the Identity Theft Resource Center recorded 3,158 publicly reported US data compromises in 2024 that led to more than 1.3 billion victim notices.
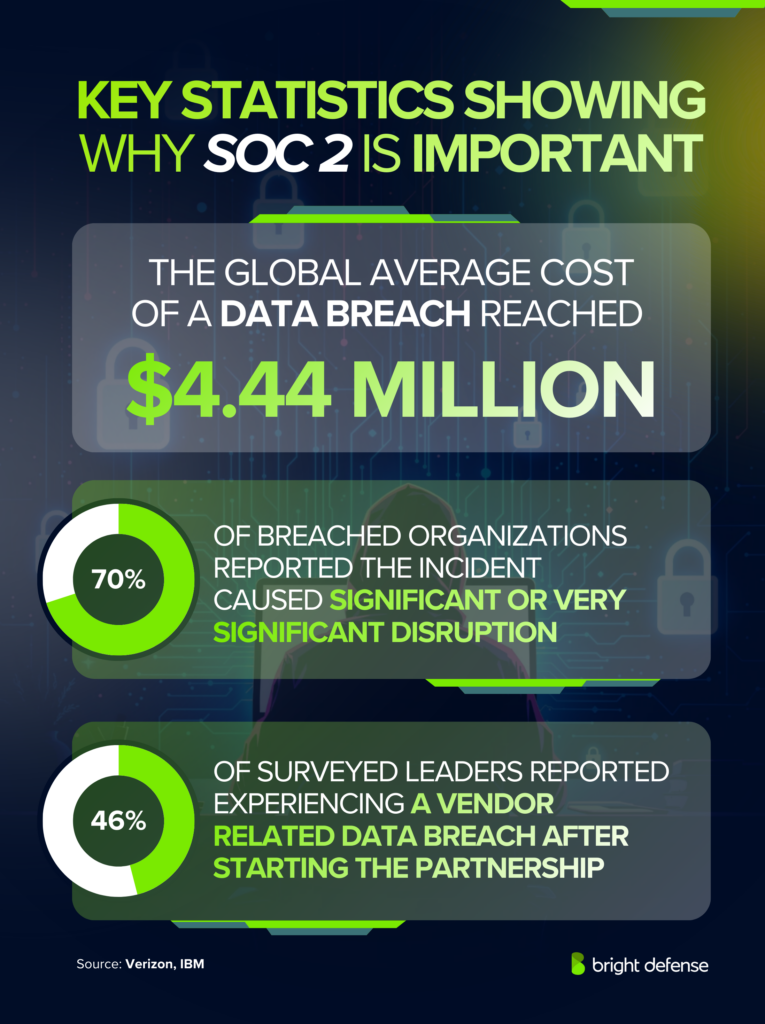
The financial impact is also significant, since IBM reported the global average cost of a data breach reached USD 4.44 million in 2025.

What Does SOC 2 Stand For?
SOC 2 stands for Service Organization Control 2, a reporting framework created by the American Institute of Certified Public Accountants that evaluates how service providers manage and protect customer data.

SOC 2 focuses on controls related to security, availability, processing integrity, confidentiality, and privacy, with reports used to demonstrate how an organization’s systems and practices address these trust service criteria.
What Is SOC 2 Compliance?
SOC 2 compliance refers to meeting the requirements of the SOC 2 reporting framework, which evaluates how well a company designs and operates controls to protect customer data. The framework is based on five Trust Services Criteria that define what auditors review during an assessment.

The five Trust Services Criteria are:
- Security, which covers controls that protect systems and data from unauthorized access, misuse, and security threats.
- Availability, which focuses on whether systems remain accessible and perform as promised in service agreements.
- Processing Integrity, which addresses whether systems process data accurately, completely, and on time.
- Confidentiality, which applies to information that must be restricted, such as proprietary or contractually sensitive data.
- Privacy, which governs how personal information is collected, used, stored, and shared.
To achieve SOC 2 compliance, an organization typically follows a defined process:
- Scope systems and services that handle customer data.
- Design policies and technical controls mapped to the Trust Services Criteria.
- Document how those controls operate in daily business activities.
- Complete an independent audit that tests control design and operating effectiveness over a defined period.
SOC 2 compliance helps customers understand how a company manages security and data protection risks in real operating conditions rather than relying on policy statements alone.
Types Of SOC 2 Reports
There are two types of SOC 2 reports: SOC 2 Type I and SOC 2 Type II, and they differ based on the time period and depth of evaluation. SOC 2 Type I evaluates whether a company’s controls are properly designed at a specific point in time, while SOC 2 Type II evaluates both the design and operating effectiveness of those controls over an extended period, usually three to twelve months.
| SOC 2 Report Type | Time Coverage | What It Evaluates | Typical Use Case |
| SOC 2 Type I | Point in time | Design of controls | Early-stage compliance or readiness validation |
| SOC 2 Type II | Period of time | Design and operating effectiveness of controls | Customer assurance, vendor risk reviews, and enterprise sales |
SOC 2 Type I is commonly used to demonstrate initial control readiness, while SOC 2 Type II is generally required by customers and partners because it provides evidence that controls consistently operate over time.
What’s the Difference Between SOC 2 Type I Vs Type II?
SOC 2 Type I is a point in time report on whether controls are designed and implemented, while SOC 2 Type II also tests whether those controls worked over a defined period.
| Category | SOC 2 Type I | SOC 2 Type II |
| What it covers | Control description and whether controls are implemented as of a specific date | Everything in Type I plus whether controls were effective across the full test period |
| Time coverage | Snapshot as of one date | Period report, commonly measured in months and often set to a year for mature programs, with shorter first periods sometimes used |
| Testing depth | Confirms controls exist and are set up | Samples evidence across time to confirm controls ran as described |
| Typical customer takeaway | Good for showing a control program is in place | Stronger for proving controls worked consistently, which is why customer auditors often ask for Type II |
| Best fit | Early stage, first audit, or when controls are newly implemented | Established controls with enough operating history to produce repeated evidence |
- Choose Type II when customers or their auditors ask for proof that controls worked across a period, not only on a single date.
- Choose Type I when you need an earlier snapshot to confirm the control set exists and is implemented, then plan a move to Type II after controls have run long enough to generate period evidence.
- Pick a Type II period length that matches expectations, since periods commonly range from a few months for a first report to a full year in many programs.
Check out the differences between SOC 1 and SOC 2 in a separate blog
Who Needs A SOC 2 Report?
A SOC 2 report is typically needed by any service provider that stores, processes, or transmits customer data and must give customers detailed assurance about the controls that protect that data.
Organizations that most often need a SOC 2 report include:

- SaaS and cloud application providers that host customer data or run critical customer workloads.
- Managed service providers such as IT outsourcing, monitoring, and security operations vendors that access customer environments or data.
- Cloud infrastructure and hosting providers such as data centers, platform providers, and services that support customer systems and availability commitments.
- Data processors and business platforms such as analytics, identity, HR, payroll, and customer support systems that handle confidential or personal information.
- Vendors selling to regulated or risk sensitive buyers where customers and business partners use SOC 2 reports as part of their risk review of service providers.
You may need a SOC 2 report depending on your business model and customer requirements, and our blog on who needs a SOC 2 report explains whether your organization falls into that category.
What Is A SOC 2 Audit?
A SOC 2 audit is an independent review that examines whether a company has designed and follows controls that protect customer data and critical systems. The audit is performed by a licensed CPA firm and measures controls against the SOC 2 Trust Services Criteria.

A SOC 2 audit typically includes:
- Scope definition, which identifies the systems, services, and data included in the audit.
- Control review, which evaluates whether security, availability, processing integrity, confidentiality, and privacy controls are properly designed.
- Evidence testing, which involves reviewing logs, records, and other proof that controls operate as described.
- Audit reporting, which results in a formal SOC 2 report that customers and partners can review.
SOC 2 audits are issued as either Type I reports, which assess control design at a specific point in time, or Type II reports, which evaluate how well controls operate over a defined period, usually several months.
Who Can Perform A SOC Audit?
A SOC audit must be performed and the SOC report must be issued by an independent licensed CPA, typically through a CPA firm acting as the service auditor.
A SOC examination is an AICPA attestation engagement under the SSAEs and is tied to AICPA professional and ethical requirements, including independence standards reflected in the required independent practitioner reporting language.

A readiness assessment or prep work can be supported by consultants, but a consultant cannot sign or issue the SOC report.
A practical qualifier is that the firm should be a public accounting firm that participates in the AICPA peer review program, since peer review is how the profession evaluates quality for audit and attestation work.
SOC 2 Audit Checklist
A SOC 2 audit checklist is a structured inventory of scope details, required report elements, and evidence items aligned to the AICPA Trust Services Criteria and the SOC 2 Description Criteria.
Engagement Scope And Report Basics
- Report type: SOC 2 Type I or SOC 2 Type II
- Examination period dates or point in time date
- In-scope Trust Services Categories: Security, plus any of Availability, Processing Integrity, Confidentiality, Privacy
- System boundary statement, including in-scope environments and locations
- Subservice organizations list
- Subservice method: carve-out method or inclusive method
- Complementary user entity controls
- Management assertion
- SOC 2 report sections: system description, service auditor’s report, tests of controls, results
System Description Inventory (SOC 2 Description Criteria)
- Services provided
- System components: infrastructure, software, people, procedures, data
- Data flows and key dependencies
- Commitments and system requirements relevant to in-scope categories
- Subservice organization responsibilities and assumed control types when carve-out applies
Trust Services Criteria Evidence Inventory (Common Criteria CC1 Through CC9)
- CC1 Control environment: org chart, role definitions, governance records
- CC2 Communication and information: policy set, training records, internal communications
- CC3 Risk assessment: risk methodology, risk register, risk acceptance records
- CC4 Monitoring: monitoring routines, review records, issue tracking
- CC5 Control activities: SOPs, approvals, segregation of duties evidence=
- CC6 Logical and physical access: IAM configuration, access requests, access reviews, privileged access records, physical access logs
- CC7 System operations: logging scope, alerting, vulnerability records, incident records
- CC8 Change management: SDLC documentation, code review records, deployment records
- CC9 Risk mitigation: incident response materials, backup records, disaster recovery materials, vendor oversight records
Why SOC 2 Compliance Is Important
SOC 2 compliance is important because it provides third parties with independent proof that security and operational controls exist and operate consistently within an organization’s Security Framework.
The reasons why SOC 2 compliance is important are discussed in detail below.

1. Rising Breach Costs Increase Business Risk
The average cost of a data breach reached $4.88 million in 2024, so a security failure can turn into a direct financial problem rather than a limited technical issue. We treat SOC 2 as a practical baseline for Risk Management because it requires documented controls, clear ownership, routine oversight, and repeatable evidence tied to Financial Reporting impacts. That structure reduces confusion during incidents and supports accountability when protecting sensitive business operations.
2. Operational Disruption Shows Why Availability Controls Matter
70% of breached organizations reported significant or very significant operational disruption, showing how incidents quickly affect uptime and internal workflows. SOC 2 addresses this risk through expectations tied to Operational Effectiveness, including system reliability controls, disciplined change management, and monitoring practices that reduce downtime and support structured recovery.
3. Third Party Involvement Continues To Grow
The share of breaches involving a third party increased from 15% to 30%, highlighting the expanded attack surface created through vendors. SOC 2 remains relevant because it requires defined controls over Third Party Vendors, including access boundaries, oversight activities, and accountability mechanisms that integrate vendor risk into the organization’s overall security program.
4. Ransomware Remains Widespread
Ransomware appeared in 44% of reviewed breaches, showing how attackers often succeed after gaining access and moving laterally. SOC 2 expectations emphasize preventive and detective controls such as tighter access management, monitoring, and Intrusion Detection Systems that help identify misuse earlier and limit damage during active incidents.
5. Slow Detection Extends Breach Impact
Breaches involving compromised credentials took 292 days to identify and contain, reflecting gaps in visibility and review. SOC 2 addresses this issue through expectations for logging, review routines, and documented response actions that support faster detection and consistent investigation of Security Incidents.
SOC 2 Requirements
SOC 2 requirements consist of specific documented elements and control conditions evaluated against the AICPA Trust Services Criteria to demonstrate how organizations Protect Data and manage risk across systems.
Key SOC 2 requirements include the following.
- A clearly defined system description covering services, infrastructure, software, people, processes, and data, including how organizations Store Customer Data.
- Documented control objectives mapped to applicable Trust Services Criteria.
- Security controls addressing logical access, authentication, authorization, and Network Security.
- Availability controls supporting uptime, capacity planning, and recovery.
- Change management controls governing system and code changes.
- Monitoring and logging controls that support detection, investigation, and review.
- Incident response controls covering detection, escalation, containment, and resolution.
- Vendor and third party risk controls governing access, oversight, and accountability.
- Evidence demonstrating control operation over the examination period through consistent documentation.
- An independent CPA attestation supported by External Auditors resulting in a SOC 2 Type I or Type II report.
Learn about the SOC 2 requirements in full detail in a dedicated blog!
What Are Access Control Models?
| Model | Description |
|---|---|
| Discretionary Access Control (DAC) | Data owners manage access to their own resources, offering flexibility with limited centralized oversight. |
| Mandatory Access Control (MAC) | A central authority enforces strict access rules suited for high-security environments. |
| Role-Based Access Control (RBAC) | Permissions are assigned based on job roles, supporting consistent access management. |
| Attribute-Based Access Control (ABAC) | Access decisions rely on user, resource, and contextual attributes for fine-grained control. |
| Relationship-Based Access Control (ReBAC) | Permissions depend on relationships between users and resources, often used in collaborative systems. |
Final Thoughts
SOC 2 is a trust framework that shows how an organization Protects Sensitive Data across security, availability, processing integrity, confidentiality, and privacy while supporting long term confidence in its Organization’s Ability to manage operational and security risk.
FAQs
SOC 2 stands for Service Organization Control 2, also called Systems and Organization Controls 2. It is an auditing framework created by the American Institute of Certified Public Accountants to evaluate whether service organizations protect customer data through defined security criteria aligned with the AICPA’s trust service principles, which cover security, availability, processing integrity, confidentiality, and privacy.
A SOC 2 audit involves an independent auditor assessing a service organization’s information security practices and internal controls against one or more trust service principles. The auditor performs evidence collection, interviews staff, and reviews security policies, risk management activities, and system processing controls to confirm operational effectiveness. Reports include an opinion letter, management’s assertion, a system description, and detailed audit results; Type I reports assess control design at a point in time, while Type II reports evaluate performance over a defined period.
SOC 2 compliance is voluntary and not required by law, but it is widely adopted to support regulatory compliance expectations from customers, partners, and procurement teams reviewing a vendor’s security posture.
SOC 2 applies to service organizations that handle data processing functions and operate in cloud environments, including SaaS providers, data centers, and managed service firms. Organizations that work with third party vendors often rely on SOC 2 reports to assess vendor management practices and controls designed to protect sensitive data, including protected health information in regulated industries.
A data owner is the individual or business unit responsible for governing how information is used and protected. Data owners define access rules, oversee data quality, and coordinate safeguards related to network security and physical access controls while supporting compliance obligations across the organization.
A privacy policy is a legal document that explains how an organization collects, uses, stores, shares, and protects personal data. It outlines retention practices, disclosure to external auditors when applicable, and user rights related to transparency and accountability.
Get In Touch



