SOC 2
Bright Defense empowers small to medium businesses and startups to achieve SOC 2 compliance. Our continuous compliance services ensure your company meets SOC 2 requirements while enhancing your security posture and fostering trust with customers and stakeholders. Partner with Bright Defense and achieve SOC 2 compliance!
Monthly Service
Our monthly service offering includes:
Continuous Cybersecurity Compliance
Managed Compliance Automation
Managed Security Awareness and Phishing
Virtual Chief Information Security Officer (vCISO)
Continuous Cybersecurity Compliance
Our CISSP and CISA-certified security experts will develop and execute a cybersecurity plan to meet compliance frameworks. Our continuous compliance service includes:
Gap Analysis
Risk Assessment
Policy Generation and Implementation
Business Continuity Planning
Certification Assistance
Managed Compliance Automation
Security awareness training modules, AI-driven phishing tests, and reporting and progress monitoring.
Managed Security Awareness and Phishing
Automate your compliance journey with a single platform for all your frameworks that allows you to monitor your compliance status continuously.
Virtual Chief Information Security Officer (vCISO)
Our experienced and certified vCISOs work with your team through every phase of the compliance journey to ensure your security program is tailored to your unique business requirements
SOC 2 Optymize
Benefits
-
Boost Your Brand’s Trustworthiness
Improve your cybersecurity posture and build a security-conscious culture to minimize financial risk and reputational harm.
-
Gain a Competitive Advantage
44% of companies require proof of cybersecurity measures in their requests for proposals. SOC 2 compliance demonstrates a commitment to safeguarding customer data and allows you to win more customers.
-
Minimize Risks and Maximize Peace of Mind
SOC 2 compliance reduces risk by enforcing strict data security controls and protecting against unauthorized access and breaches. Reduce risk by improving your cybersecurity posture with SOC 2.
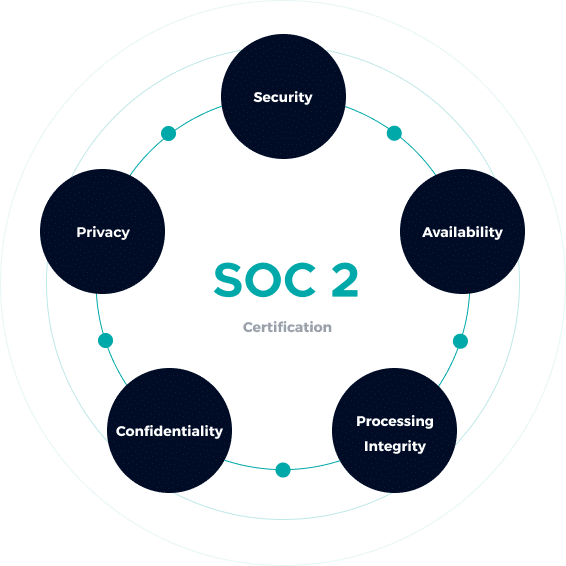
Trust Services Criteria
The Trust Services Criteria are your roadmap to a successful SOC 2 audit. These are categorized into:
Security
Availability
Processing Integrity
Confidentiality
Privacy
Encryption Access controls Network/application firewalls
Access controls Two-factor authentication Encryption
Network/application firewalls Two-Factor authentication Intrusion Detection
Performance monitoring Disaster recovery Security Incident handling
Quality assurance Processing monitoring
Get In Touch