
500+ Ransomware Statistics for 2026
The team at Bright Defense has compiled a detailed list of staggering 500+ up-to-date ransomware statistics for 2025. This is without a shadow of doubt the biggest collection of ransomware statistics to date, containing data from trusted industry leaders such as Mandiant, Fortinet, IBM, and Sophos.
In this article, you’ll find carefully selected data points covering:
- Global ransomware attack trends
- Industry-specific ransomware activity
- Financial impact of ransomware incidents
- Statistics on attack frequency and downtime
- Regional ransomware data across North America, Europe, Asia, Africa, Australia, and South America
Let’s get into the numbers.
Global Ransomware Trends and Impact
- In 2024, ransomware groups claimed 5,461 successful attacks on organizations worldwide (Ransomware Roundup – Comparitech).
- Ransomware has existed for 35 years and remains the fastest-growing category of cybercrime, showing no signs of slowing down. (Cybersecurity Ventures)
- Average ransomware breaches and attack costs by year:
- The global cost of ransomware is projected to reach $275 billion annually by 2031, highlighting the escalating financial toll of this long-running cyber threat. The total estimated costs include not only ransom payments and negotiation expenses, but also the damage or destruction of data, theft of money, operational downtime, and lost productivity.
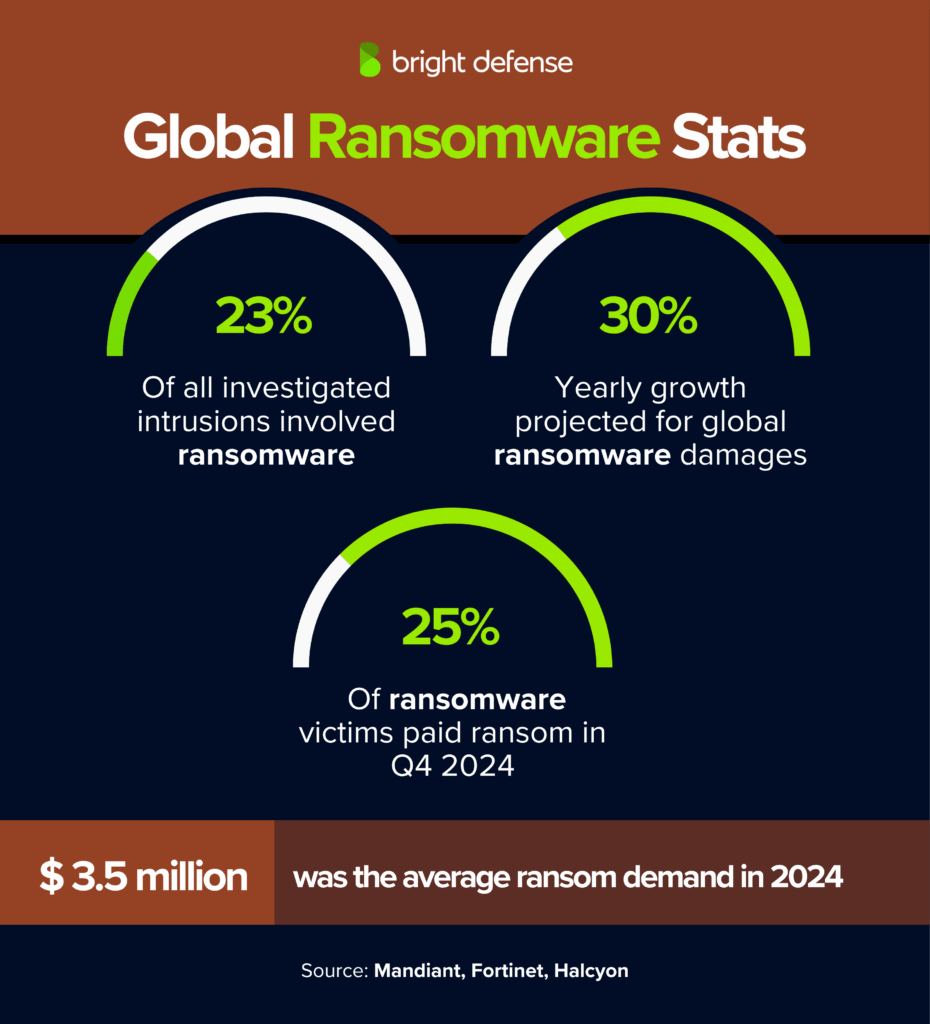
(Cybersecurity Ventures) - Ransomware accounted for 23% of all investigated intrusions, slightly down from 24% in 2023 . (Mandiant – M Trends 2025 Report)
- The average ransom demand in 2024 was more than USD 3.5 million (Mandiant – M Trends 2025 Report)
- Average ransom paid: USD 9.53M. (Mandiant – M Trends 2025 Report)
- Total ransom paid: USD 133.5M. (Mandiant – M Trends 2025 Report)
- Only 60% of data was typically recovered after ransom payment, and just 4% regained all data (Fortinet – Ransomware Stats).
- 73% of organizations reported at least one ransomware attack (Fortinet – Ransomware Stats).
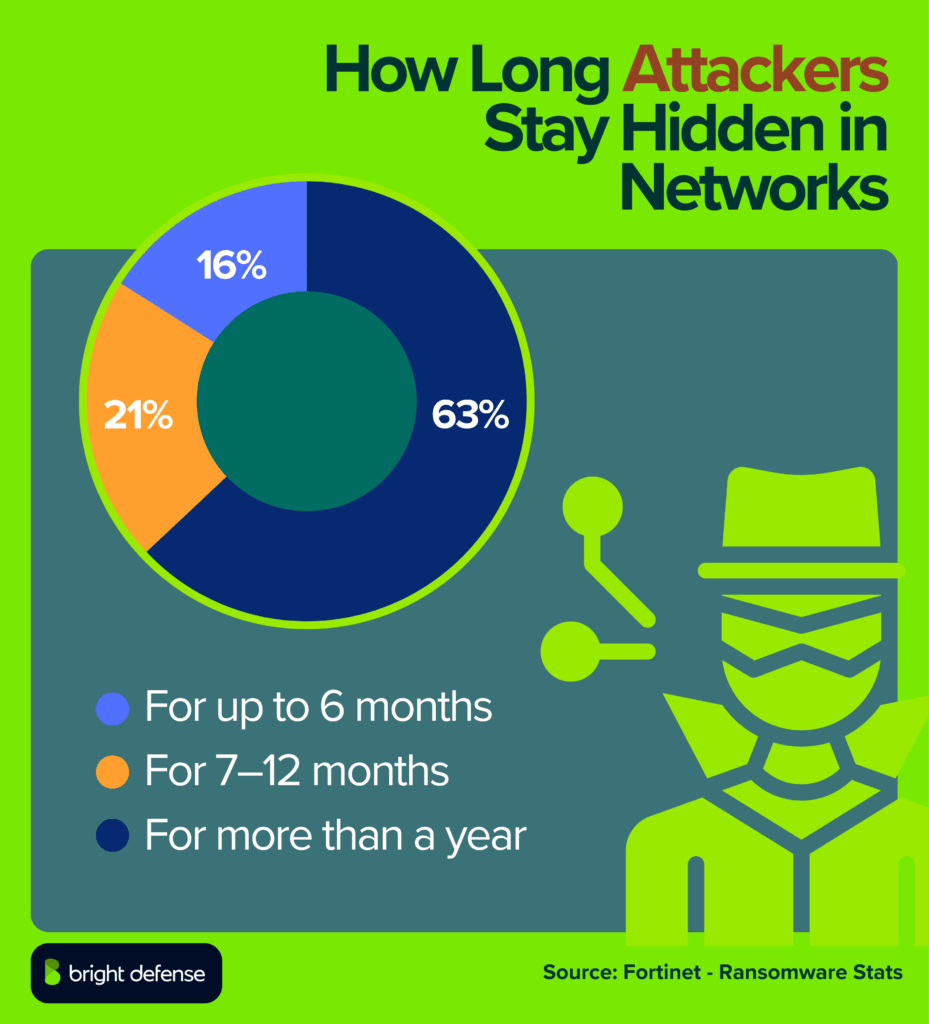
- Attackers remained undetected in networks:
- 63% for up to 6 months
- 21% for 7–12 months, and
- 16% for more than a year (Fortinet – Ransomware Stats).
- Global ransomware damages projected to grow 30% per year (Fortinet – Ransomware Stats).
- A ransomware attack projected to occur every two seconds by 2031 (Fortinet – Ransomware Stats).
- There were around 832 breach incidents in 2022, with 130 confirmed data losses. Nearly 80% caused by ransomware (Fortinet – Ransomware Stats).
- Only 50% of U.S. small businesses had a cybersecurity plan (Fortinet – Ransomware Stats).
- 71% of global businesses reported impact from ransomware, and 62.9% of victims paid ransom (Fortinet – Ransomware Stats).
- After-effects of ransomware attacks included 40% layoffs, 35% C-level resignations, and 33% temporary suspension of operations (Fortinet – Ransomware Stats).
- 49% paid ransom to prevent revenue loss, 41% to speed up recovery (Fortinet – Ransomware Stats).
- 67% of victims lost between $1 and $10 million (Fortinet – Ransomware Stats).
- More than half had corrupted data even after paying ransom (Fortinet – Ransomware Stats).
- 80% of businesses that paid ransom suffered another attack, and 68% were attacked again within one month (Fortinet – Ransomware Stats).
- 24% of all breaches involved ransomware (Fortinet – Ransomware Stats).
- In Q4 2024, 1,663 ransomware attacks were published, the highest quarterly volume on record (Halcyon – Ransomware Stats).
- In 2024, ransomware attacks increased by 70% in Latin America, compared to just 8% in North America (Halcyon – Ransomware Stats).
- In 2024, 42% of executives claimed to have cyber resilience measures, while only 35% of organizations actually had a formal recovery playbook (Halcyon – Ransomware Stats).
- Ransomware detections dropped by 18% from 2023 to 2024 (Halcyon – Ransomware Stats).
- In 2023, 59% of organizations were attacked, but only 22% recovered within one week (Halcyon – Ransomware Stats).
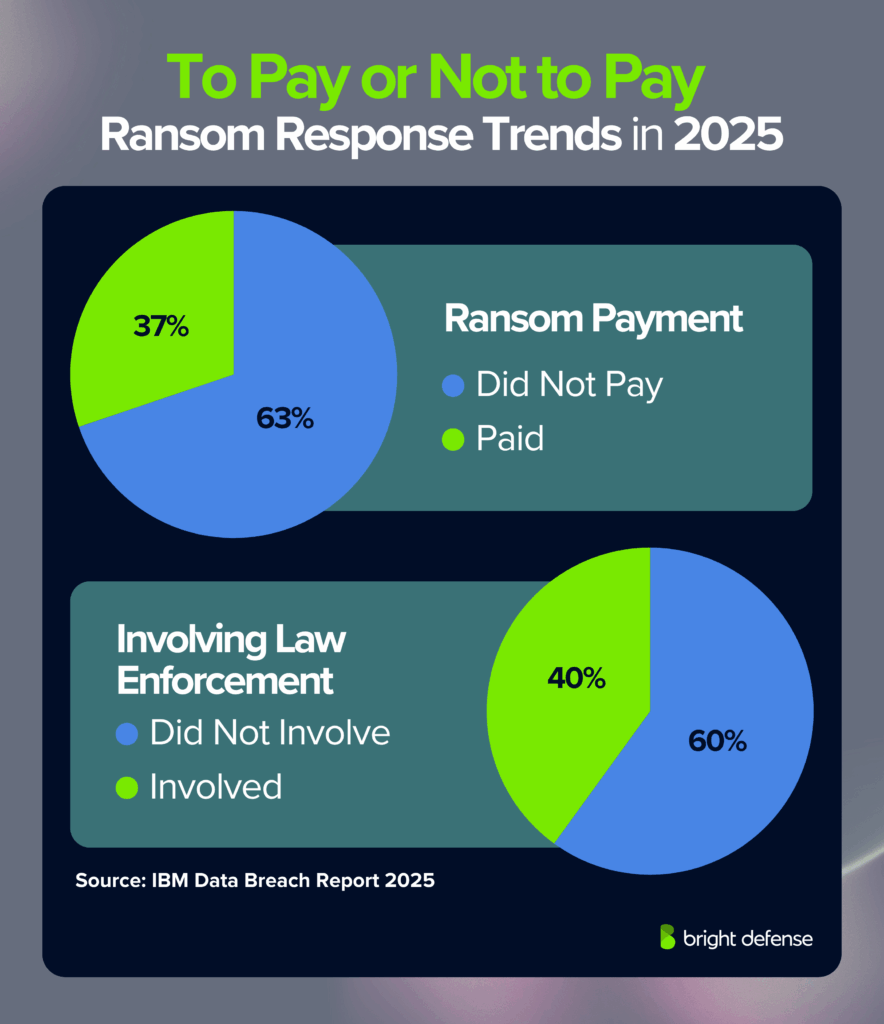
- 2024: 52% of ransomware victims involved law enforcement. This reduced average breach costs from USD 5.37 million to USD 4.38 million (a nearly USD 1 million difference). It also shortened breach lifecycles from 297 days to 281 days (IBM Data Breach Report – 2025)
- 2025: Only 40% of organizations involved law enforcement, a decline from 52% in 2024. (IBM Data Breach Report – 2025)
- In 2024, North America recorded 3,259 ransomware incidents, remaining the most targeted region globally. This figure reflects continued dominance of ransomware activity across the United States and Canada. (Group IB)
- Europe reported 1,136 ransomware incidents, confirming the region’s persistent exposure to financially motivated groups despite several law enforcement operations.(Group IB)
- The Asia-Pacific (APAC) region experienced 467 ransomware attacks, showing significant concentration in manufacturing and financial services. (Group IB)
- The Middle East and Africa (MEA) region registered 184 ransomware incidents, reflecting steady targeting of professional services and government institutions. (Group IB)
- Across all regions, manufacturing was the most affected industry, suffering 660 attacks, followed by real estate with 553, and professional services with 487. (Group IB)
- The LockBit ransomware group remained the most active globally, responsible for 673 attacks during 2024. RansomHub ranked second with 548 incidents, followed by Play with 348, and Akira with 333. (Group IB)
- In Europe, LockBit carried out 182 attacks, while RansomHub executed 126. The manufacturing sector was the leading target, with 164 incidents, followed by professional services (113) and real estate (107). (Group IB)
- Within the Asia-Pacific region, LockBit launched 74 attacks, and RansomHub followed with 68. The real estate and manufacturing industries each suffered 51 attacks, showing equal targeting intensity. (Group IB)
- In the Middle East and Africa, LockBit recorded 36 attacks, with RansomHub responsible for 29. The professional services and manufacturing sectors each faced 21 incidents, while healthcare registered 14. (Group IB)
- North America remained the core battleground for ransomware operations. LockBit conducted 337 attacks, RansomHub 270, and Play 312. The manufacturing industry topped the list with 386 attacks, followed by real estate (353) and professional services (289). (Group IB)
- In Latin America, RansomHub led with 55 attacks, and Hunters International followed with 44. The manufacturing sector saw 34 incidents, while healthcare and professional services experienced 27 and 25 respectively. (Group IB)
- The typical recovery cost for ransomware incidents was nearly $2.0 million.

Ransomware Payment Trends
- In 2024, 63% of ransomware victims that involved law enforcement avoided paying ransom. (IBM Data Breach Report – 2024)
- In 2025, across all victims (not just those with law enforcement), 63% refused to pay ransom (up from 59% in 2024), while 37% chose to pay (down from 41% in 2024). (IBM Data Breach Report – 2025)
- In Q4 2024, the average ransom payment reached USD 553,959, marking a 16% jump from Q3 levels (Coveware).
- The median ransom payment in Q4 2024 was USD 110,890, a decrease of 45% compared to Q3 2024 (Coveware).
- Among victims of data-exfiltration-only attacks, 41% paid a ransom in Q4 2024 (Coveware).
- Some groups collected over $180 million in cryptocurrency payments in a single year (Fortinet – Ransomware Stats).
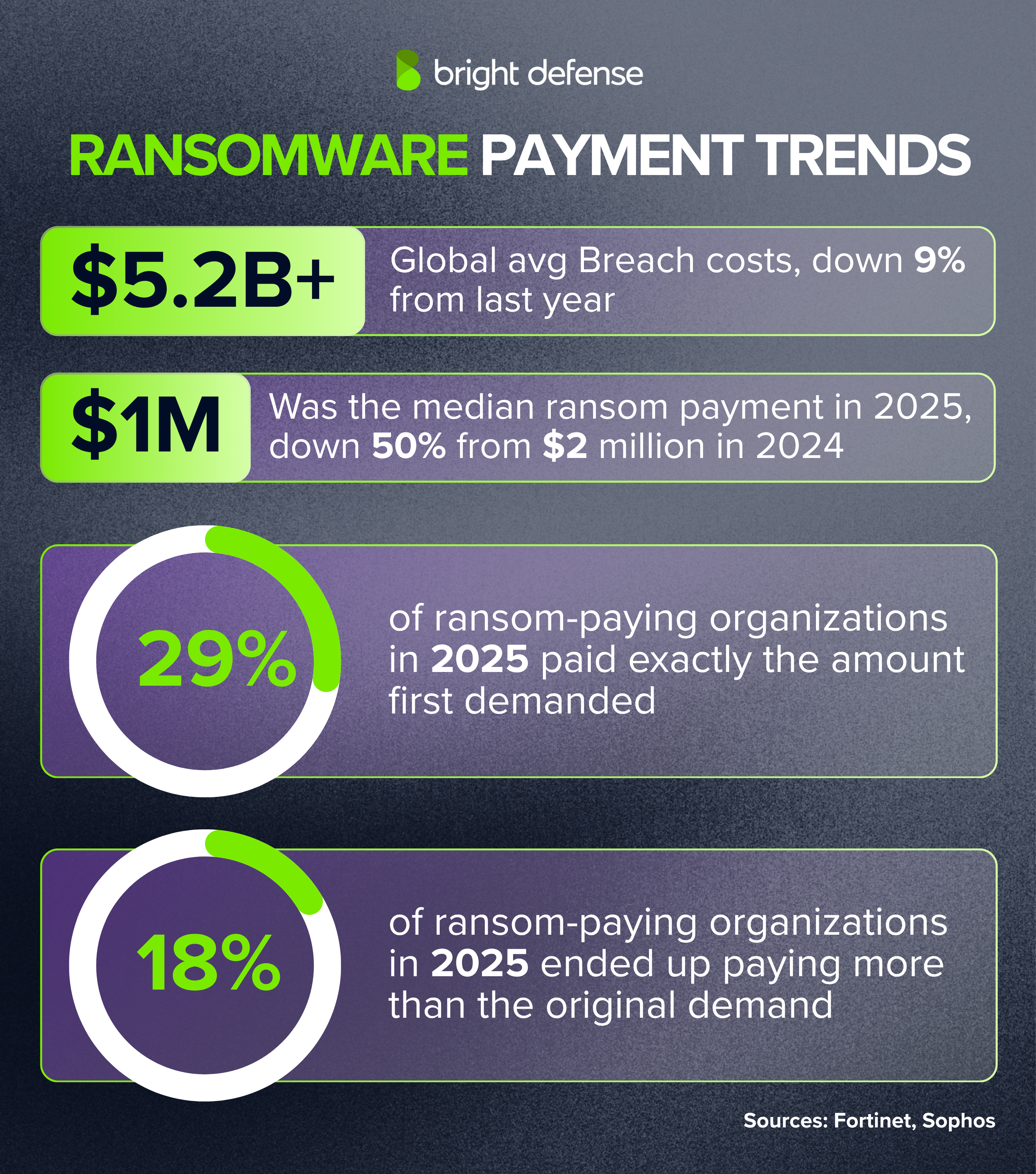
- The median ransom demand in 2025 was $1.32 million, down from $2 million in 2024 (Sophos State of Ransomware 2025).
- The median ransom payment in 2025 was $1 million, a 50% decrease from $2 million in 2024 (Sophos State of Ransomware 2025).
- 53% of organizations that paid ransoms in 2025 negotiated a lower amount than the attackers’ initial demand (Sophos State of Ransomware 2025).
- 29% of ransom-paying organizations in 2025 paid exactly the amount first demanded (Sophos State of Ransomware 2025).
- 18% of ransom-paying organizations in 2025 ended up paying more than the original demand (Sophos State of Ransomware 2025).
Want to learn about other types of cybercrimes? Explore our verified list of 256 updated Cybercrime Stats for a clear overview of various cybercrimes, including ransomware.
Common Ransomware Groups and Variants
- Akira and Fog ransomware each accounted for 11% of observed cases, tying for the top spot (Coveware).
- RansomHub made up 8% of cases (Coveware).
- Lone wolf actors also represented 8%, highlighting the continued presence of independent operators (Coveware).
- Medusa and BlackSuit each accounted for 5% of cases (Coveware).
- BianLian and Black Basta each represented 4% of cases (Coveware).
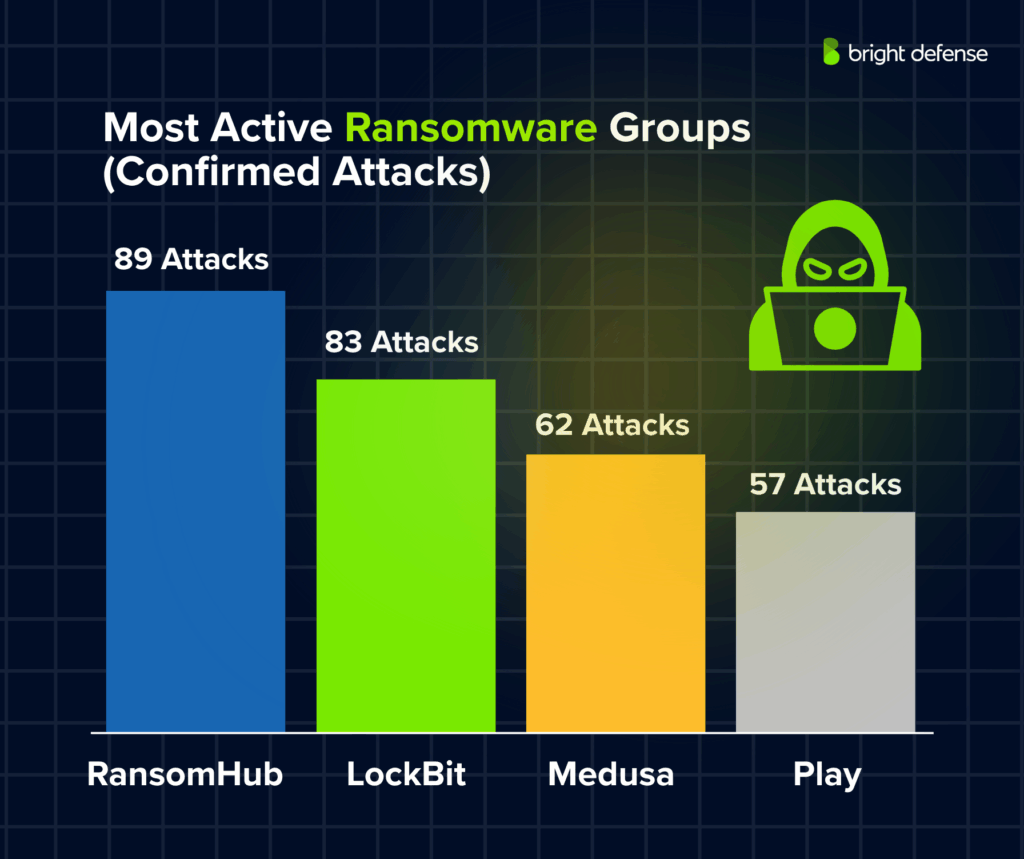
- RansomHub carried out the highest number of confirmed attacks (89) (Ransomware Roundup – Comparitech).
- 195.4 million records breached in these confirmed cases (2023 had 1,474 confirmed attacks with 261.5 million records). (Mandiant – M Trends 2025 Report)
- Most active ransomware groups (confirmed attacks): RansomHub (89), LockBit (83), Medusa (62), Play (57). (Mandiant – M Trends 2025 Report)
- Although it had fewer confirmed cases, ALPHV/BlackCat was linked to the highest number of breached records (119.6 million in total)(Mandiant – M Trends 2025 Report)
- Dark Angels received the largest single ransom payment: USD 75M. (Mandiant – M Trends 2025 Report)
- In Europe, SafePay was the most active ransomware group, responsible for 24 attacks, which marked a 118% increase in its activity. (Group IB – Intelligence Report)
- The Qilin ransomware group remained active across both Europe and APAC, with 9 attacks in Europe (a 50% decrease) and 5 attacks in APAC (a 37.5% decrease). (Group IB – Intelligence Report)
- The Akira ransomware group carried out 6 attacks in Europe, showing a 71% decline compared to previous months. (Group IB – Intelligence Report)
- The Everest, Gunra, Nemesis, and fSociety groups each conducted 2 ransomware attacks in the META region during June 2025. (Group IB – Intelligence Report)
Explore our verified 120 most recent Data Breach Stats for a detailed look at exposure trends, affected industries, and global data loss figures
Ransomware Attack Vectors and Tactics
- Exfiltration tactics appeared in 87% of ransomware cases in Q4 2024, up from 76% in Q3 2024 (Coveware).
- Lateral movement tactics appeared in 74% of cases, down from 84% in Q3 2024 (Coveware).
- Data encryption was present in 85% of cases despite declining ransom payment rates (Coveware).
- Discovery tactics were present in 39% of cases (Coveware).
- Collection tactics also appeared in 39% of cases (Coveware).
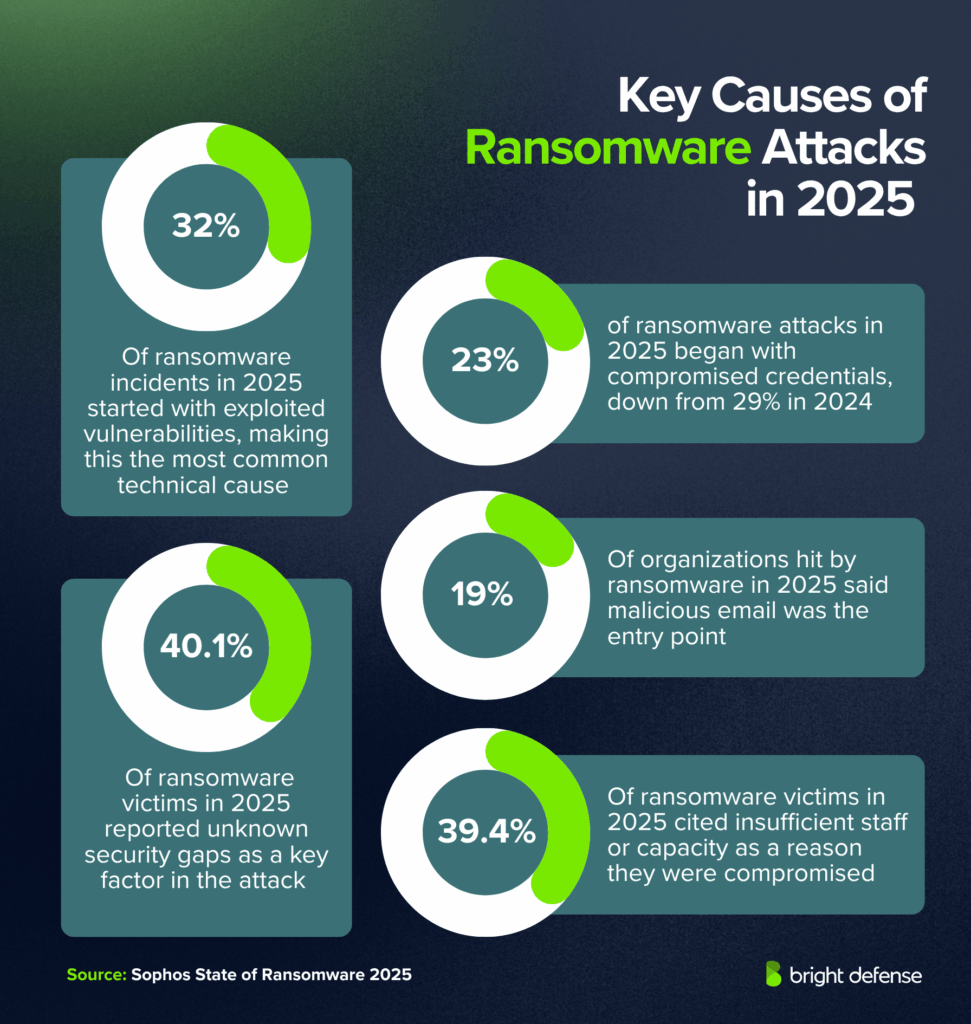
- 32% of ransomware incidents in 2025 started with exploited vulnerabilities, making this the most common technical cause (Sophos State of Ransomware 2025).
- 23% of ransomware attacks in 2025 began with compromised credentials, down from 29% in 2024 (Sophos State of Ransomware 2025).
- Median time from initial intrusion to ransomware execution was 9 days. (Mandiant – M Trends 2025 Report)
- Increased to 11 days. (Mandiant – M Trends 2025 Report)
- Dropped sharply to 5 days, reflecting attackers’ push to deploy faster and limit detection. (Mandiant – M Trends 2025 Report)
- 19% of organizations hit by ransomware in 2025 said malicious email was the entry point (Sophos State of Ransomware 2025).
- 18% of ransomware attacks in 2025 were triggered through phishing, up from 11% in 2024 (Sophos State of Ransomware 2025).
- 40.2% of ransomware victims in 2025 said lack of cybersecurity expertise contributed to their breach (Sophos State of Ransomware 2025).
- 40.1% of ransomware victims in 2025 reported unknown security gaps as a key factor in the attack (Sophos State of Ransomware 2025).
- 39.4% of ransomware victims in 2025 cited insufficient staff or capacity as a reason they were compromised (Sophos State of Ransomware 2025).
- Between 2022 and 2024, ransomware attackers had unrestricted access to victim data for an average of 70+ days before being removed (Halcyon – Ransomware Stats).
- The average active time of a ransomware incident in 2024 lasted 73 days (Halcyon – Ransomware Stats).
- In Q4 2024, 75% of paying victims sent ransom payments within 48 hours of the attack (Halcyon – Ransomware Stats).
- By 2024, there were 95 active ransomware gangs, a 40% increase from 68 in 2023 (Halcyon – Ransomware Stats).
- In Q4 2024, 84% of paying victims failed to fully recover their data after the attack (Halcyon – Ransomware Stats).
- In 2024, 93% of ransomware binaries were Windows-based executables (Halcyon – Ransomware Stats).
- Ransomware payments exceeded $600 million in cryptocurrency (Fortinet – Ransomware Stats).
- In Q4 2024, 59% of organizations worldwide reported being hit by ransomware within the year (Halcyon – Ransomware Stats).
- In 2023, 47% of global ransomware attacks targeted organizations in the United States (Halcyon – Ransomware Stats).
- In 2024, ransomware accounted for 32% of all malware incidents (Halcyon – Ransomware Stats).
- In 2023, ransomware made up 44% of all financially motivated breaches (Halcyon – Ransomware Stats).
- In 2024, an average of 15 organizations per day became ransomware victims (Halcyon – Ransomware Stats).
- In 2023, 11% of all observed malware families were classified as ransomware (Halcyon – Ransomware Stats).
- 80% of employers allow workers to access company systems from unmanaged personal devices. (Varonis)
- 60% of organizations experienced repeat ransomware incidents after paying once. (Varonis)
- 96% of government agencies strengthened cybersecurity defenses following insurance mandates. (Varonis)
Curious about how companies stay compliant in an age of constant threats? Our verified 150 updated Cybersecurity Compliance Statistics break it down for you
Industries Targeted by Ransomware
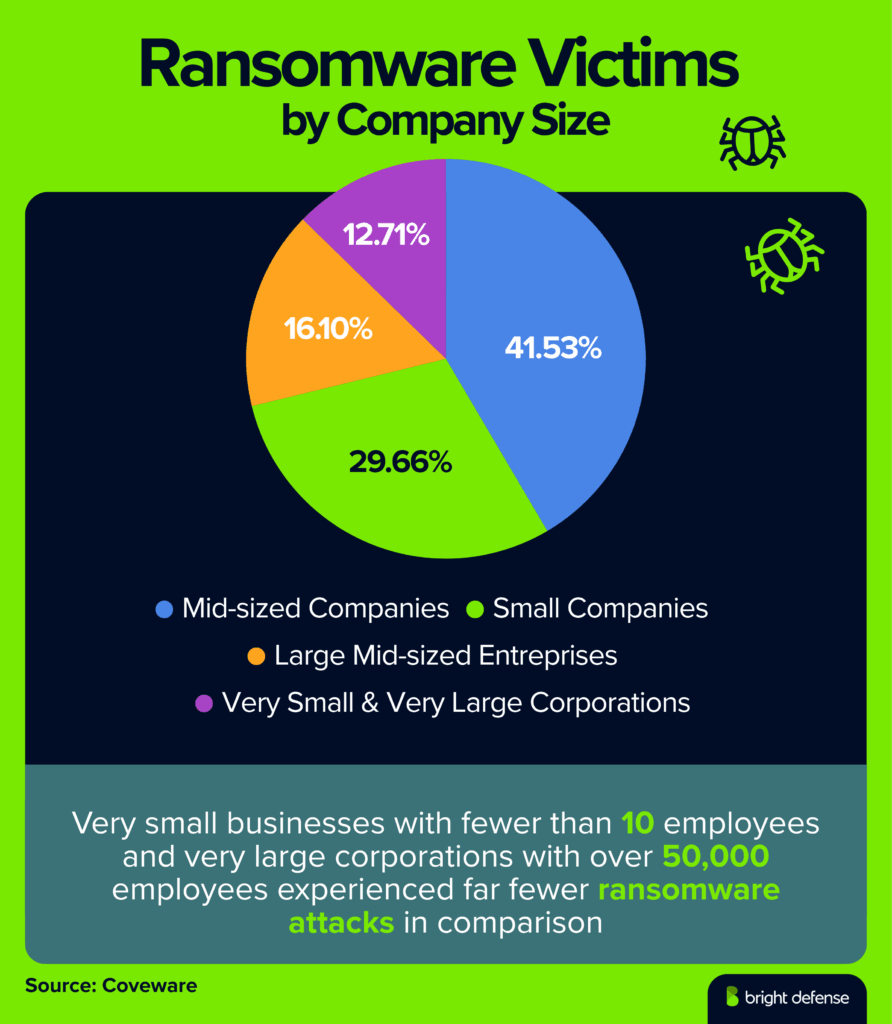
- Mid-sized companies (101 to 1,000 employees) made up 41.53% of ransomware victims in Q4 2024 (Coveware).
- Small companies (11 to 100 employees) accounted for 29.66% of victims (Coveware).
- Large mid-sized enterprises (1,001 to 10,000 employees) represented 16.10% of victims (Coveware).
- Very small businesses with fewer than 10 employees and very large corporations with over 50,000 employees experienced far fewer ransomware attacks in comparison (Coveware).
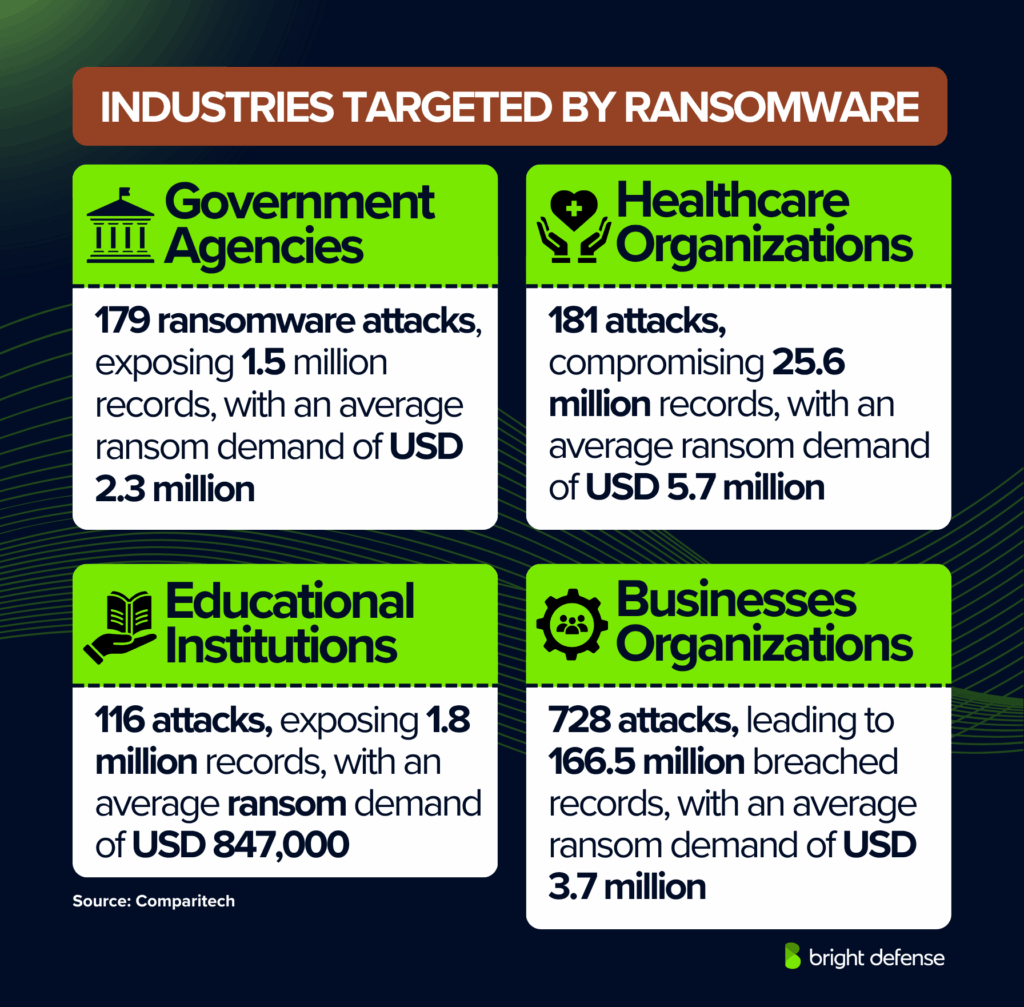
- Government agencies faced 179 confirmed ransomware attacks, which exposed 1.5 million records (Ransomware Roundup – Comparitech). The average ransom demand against governments was USD 2.3 million.
- The average ransom payment was USD 923,000.
- Healthcare organizations suffered 181 confirmed attacks, which compromised 25.6 million records. The average ransom demand in healthcare was USD 5.7 million, and payment $9000. (Ransomware Roundup – Comparitech).
- Educational institutions were hit by 116 confirmed ransomware attacks, which exposed 1.8 million records. The average ransom demand n education was USD 847,000. (Ransomware Roundup – Comparitech).
- Businesses experienced the majority of attacks, with 728 confirmed cases, leading to 166.5 million breached records (Ransomware Roundup – Comparitech).
- The average ransom demand in business was USD 3.7 million.
- The average ransom payment in business was USD 14.4 million, significantly higher than in other sectors.
- Within businesses, the technology sector saw attacks decline from 106 in 2023 to 52 in 2024, and law firms dropped from 52 in 2023 to 20 in 2024.
- Average cost of a healthcare breach reached $10.1 million, 42% higher than in 2020 (Fortinet – Ransomware Stats).
- 57% of healthcare organizations reported a ransomware attack within three years (Fortinet – Ransomware Stats).
- Some individual incidents cost as much as $67 million (Fortinet – Ransomware Stats).
- 30% of breaches in 2022 occurred in education, totaling 1,241 incidents, with 282 confirmed data losses (Fortinet – Ransomware Stats).
- External actors caused 75% of incidents; internal sources caused 25%. (Fortinet – Ransomware Stats)
- Recovery cost averaged $1.58 million for lower education and $1.42 million for higher education.
- Nearly half paid ransom, but only 2% recovered all their data. (Fortinet – Ransomware Stats)
- 58% of government breaches were detected through attacker disclosure (Fortinet – Ransomware Stats).
- Ransomware targeted 14 of 16 critical infrastructure sectors (Fortinet – Ransomware Stats).
- 2,337 breaches in manufacturing in 2022, with 338 confirmed disclosures (Fortinet – Ransomware Stats).
- Organized cybercrime accounted for 79% of ransomware breaches in banking (Fortinet – Ransomware Stats).
- A large U.S. bank spent more than $1 billion annually on cybersecurity (Fortinet – Ransomware Stats).
- U.S. banks processed $1.2 billion in ransomware transactions (Fortinet – Ransomware Stats).
- The typical recovery cost for ransomware incidents was nearly $2.0 million. (Varonis)
- Ransom-related breaches took 49 days longer to detect and contain than average attacks. (Varonis)
- One major oil company reportedly paid over $90 million in Bitcoin to attackers. (Varonis)
- On average, 64.8% of encrypted healthcare data was recovered after ransom payments. (Varonis)
- Around 630 ransomware incidents affected healthcare organizations in 2022. (Varonis)
- Since 2020, 84 higher-education institutions have experienced ransomware attacks. (Varonis)
- 66% of universities still lack fundamental cybersecurity configurations. (Varonis)
- 37% of universities had unsecured or open databases. (Varonis)
- Each week, roughly 204,000 people encounter phishing that leads to ransomware infections. (Varonis)
- The banking and insurance sectors lost approximately $2.06 billion to ransomware. (Varonis)
Phishing attacks are everywhere these days. Curious how bad it’s gotten? Take a look at 200+ phishing stats that might surprise you.
Largest Data Breaches Caused by Ransomware
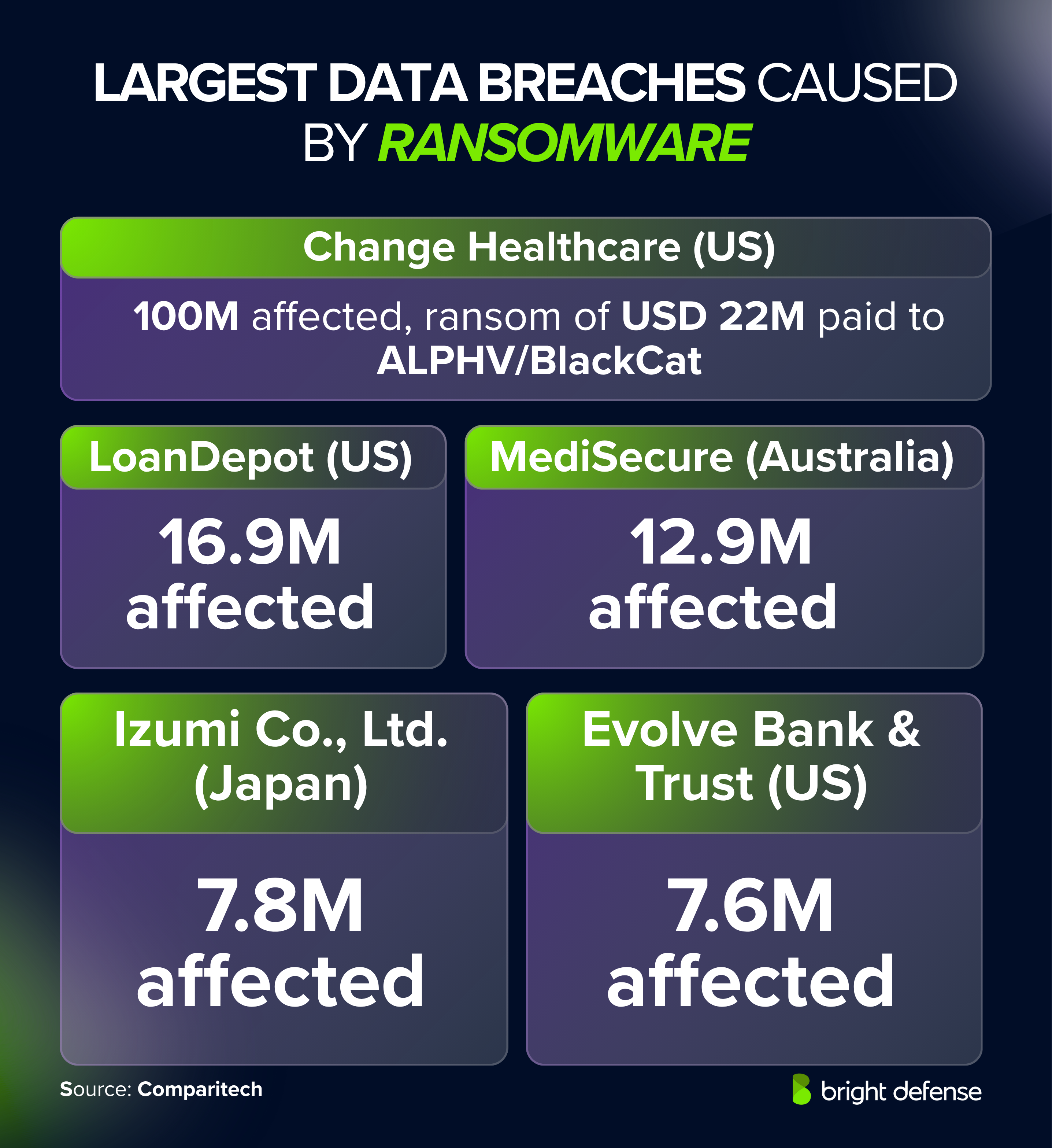
- Change Healthcare (US): 100M affected, ransom of USD 22M paid to ALPHV/BlackCat. (Comparitech – Ransomware Roundup)
- LoanDepot (US): 16.9M affected, ransom demand USD 6M not paid. (Comparitech – Ransomware Roundup)
- MediSecure (Australia): 12.9M affected, stolen data listed for sale at USD 50,000. (Comparitech – Ransomware Roundup)
- Izumi Co., Ltd. (Japan): 7.8M affected, ransom group unidentified. (Comparitech – Ransomware Roundup)
- Evolve Bank & Trust (US): 7.6M affected, LockBit attack, ransom not paid. (Comparitech – Ransomware Roundup)
- Other major breaches:
- Ascension (5.6M)
- FBCS (4.3M)
- Acadian Ambulance (2.9M)
- Prudential Insurance (2.6M)
- Rite Aid (2.2M) (Comparitech – Ransomware Roundup)
Want to check other major breaches? Read our latest article on recent data breaches.
Highest Ransom Demands
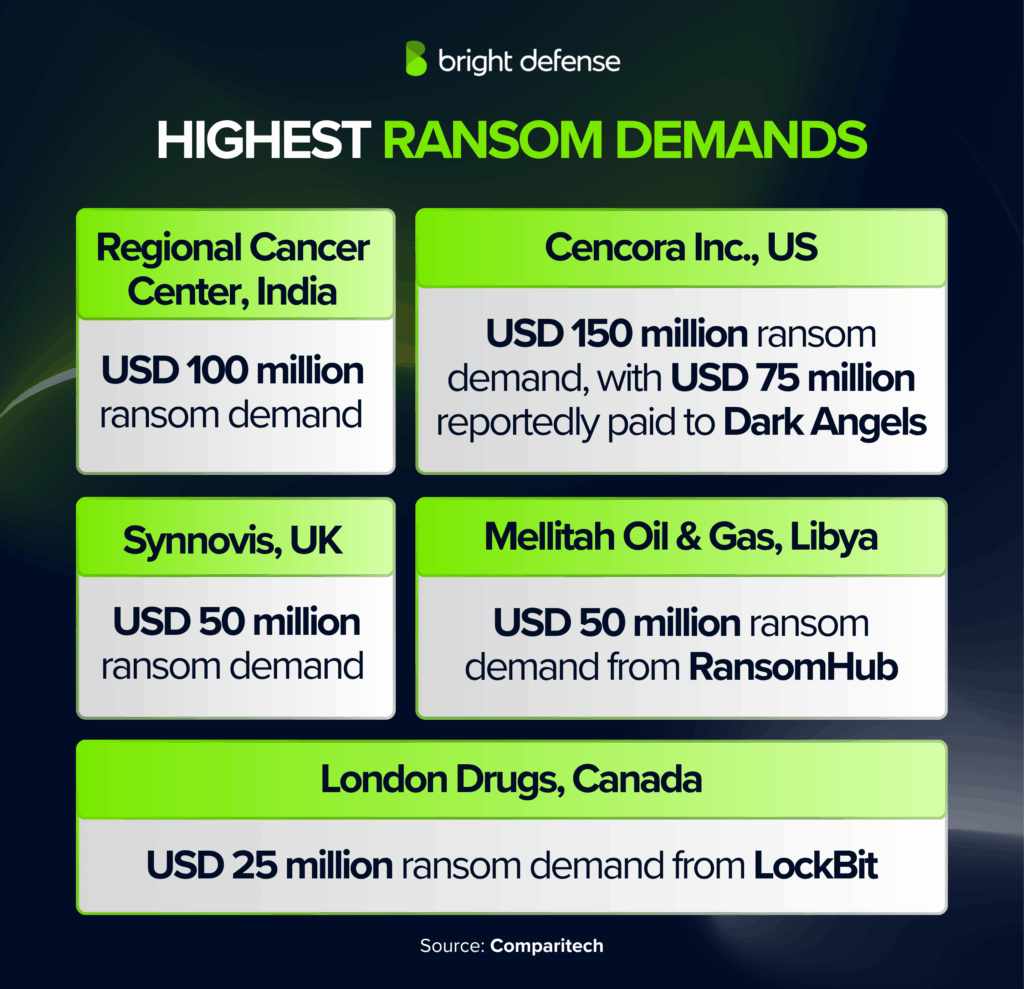
- Regional Cancer Center, India: USD 100 million ransom demand (Ransomware Roundup – Comparitech).
- Cencora Inc., US: USD 150 million ransom demand, with USD 75 million reportedly paid to Dark Angels (Ransomware Roundup – Comparitech).
- Synnovis, UK: USD 50 million ransom demand, which was refused (Ransomware Roundup – Comparitech).
- Mellitah Oil & Gas, Libya: USD 50 million ransom demand from RansomHub (Ransomware Roundup – Comparitech).
- London Drugs, Canada: USD 25 million ransom demand from LockBit; company offered USD 8 million, which was rejected (Ransomware Roundup – Comparitech).
- Other notable demands included
- CDK Global (USD 25M, paid to BlackSuit)
- RIBridges (USD 23M)
- Change Healthcare (USD 22M, paid)
- Ajuntament de Calvià (USD 11M, unpaid)
- Claro/América Móvil (USD 10M, unpaid) (Ransomware Roundup – Comparitech)
Ransomware Timeline: Rising Costs and Shifts in Response
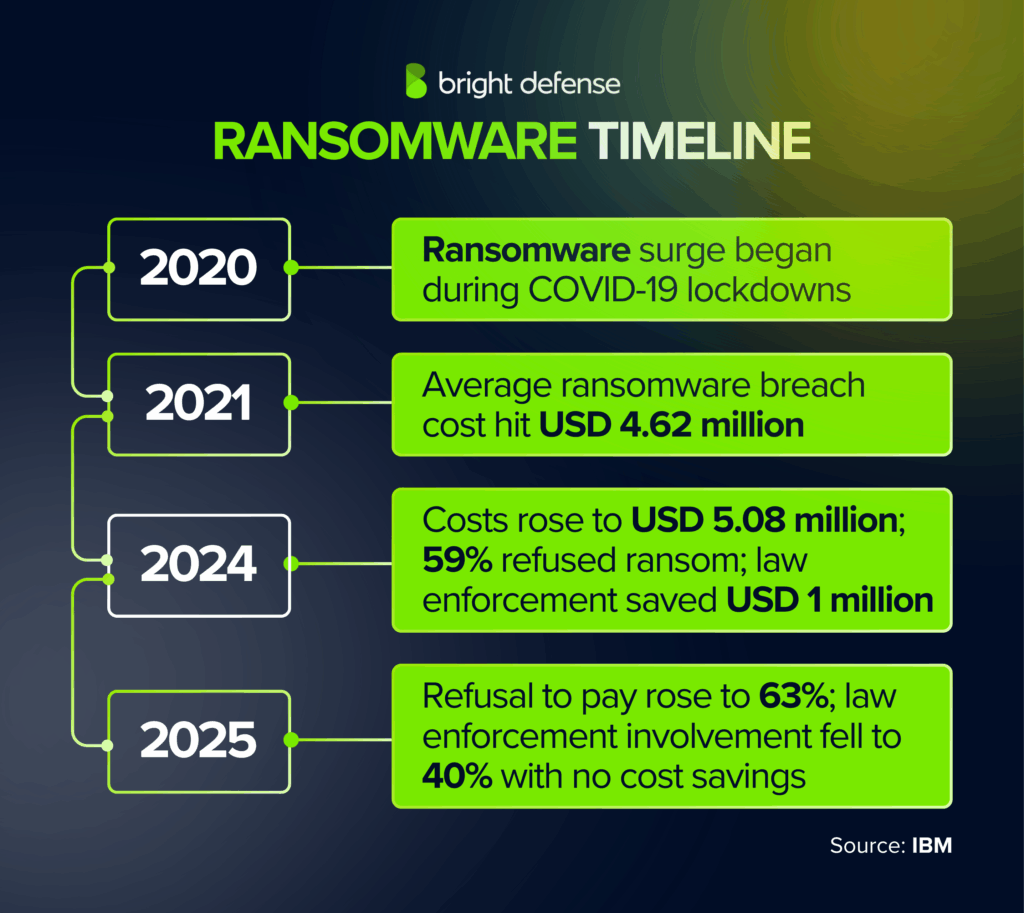
- 2020: Surge in ransomware activity began during COVID-19 lockdowns (IBM Data Breach Report – 2025)
- 2021: Average ransomware breach cost reported at USD 4.62 million (IBM Data Breach Report – 2025)
- 2024: Costs rose to USD 5.08 million, refusal to pay ransom reached 59%, and law enforcement involvement saved about USD 1 million (IBM Data Breach Report – 2025)
- 2025: Refusal to pay ransom increased further to 63%, law enforcement involvement dropped to 40%, and no cost savings were tied to law enforcement (IBM Data Breach Report – 2025)
Cost of Ransomware Attacks
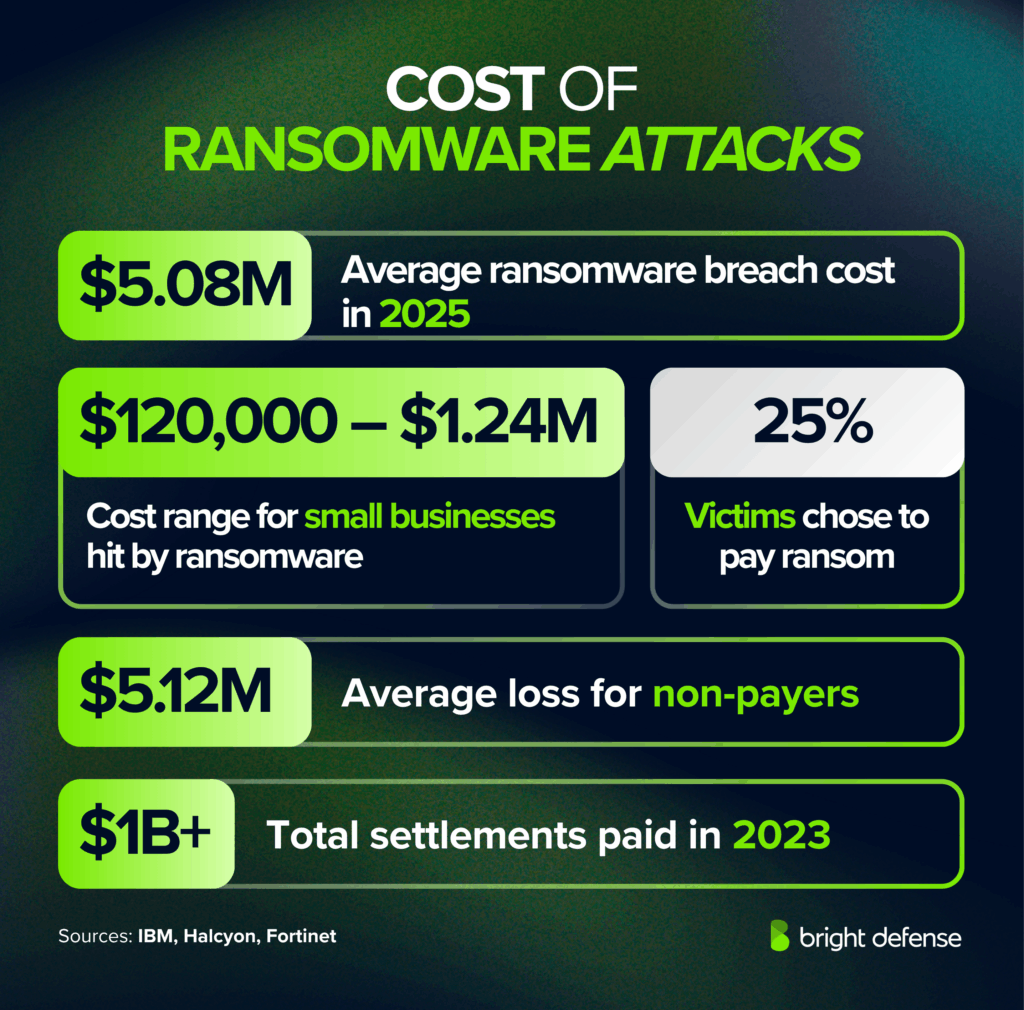
- The global average cost of an extortion or ransomware breach reached a staggering USD 5.08 million in 2025 (IBM Data Breach Report – 2025)
- Ransomware attacks had an average cost ranging USD 4.38 million to USD 5.37 million, depending on law enforcement involvement in 2024 (IBM Data Breach Report – 2025)
- Small businesses impacted by ransomware in 2024 faced costs ranging between $120,000 and $1.24 million (Halcyon – Ransomware Stats).
- Victims who paid ransom in Q4 2024 spent an average of $550,000 (Halcyon – Ransomware Stats).
- In Q4 2024, 25% of ransomware victims chose to pay ransom (Halcyon – Ransomware Stats).
- Non-paying victims lost an average of $5.12 million (Fortinet – Ransomware Stats).
- The largest ransom demand attempted was $7.5 million (Fortinet – Ransomware Stats).
- More than $1 billion in settlements were paid in 2023 (Fortinet – Ransomware Stats).
Response to Ransomware Attacks
- In Q4 2024, 57% of ransomware incidents were first detected by external parties rather than the organizations themselves (Halcyon – Ransomware Stats).
- Organizations using automated playbooks in 2024 contained breaches in a median of 51 days, compared to 79 days without playbooks (Halcyon – Ransomware Stats).
- The mean time to identify a breach in 2024 was 194 days, down from 204 days in 2023, marking a 7-year low (Halcyon – Ransomware Stats).
- The median dwell time for ransomware in Q4 2024 was just 4 days from initial compromise to encryption (Halcyon – Ransomware Stats).
- The average time to contain a ransomware breach in 2024 was 64 days (Halcyon – Ransomware Stats).
- In 2023, only 22% of organizations were able to fully restore operations within one week after a ransomware attack (Halcyon – Ransomware Stats).
Recovering from Ransomware Attacks
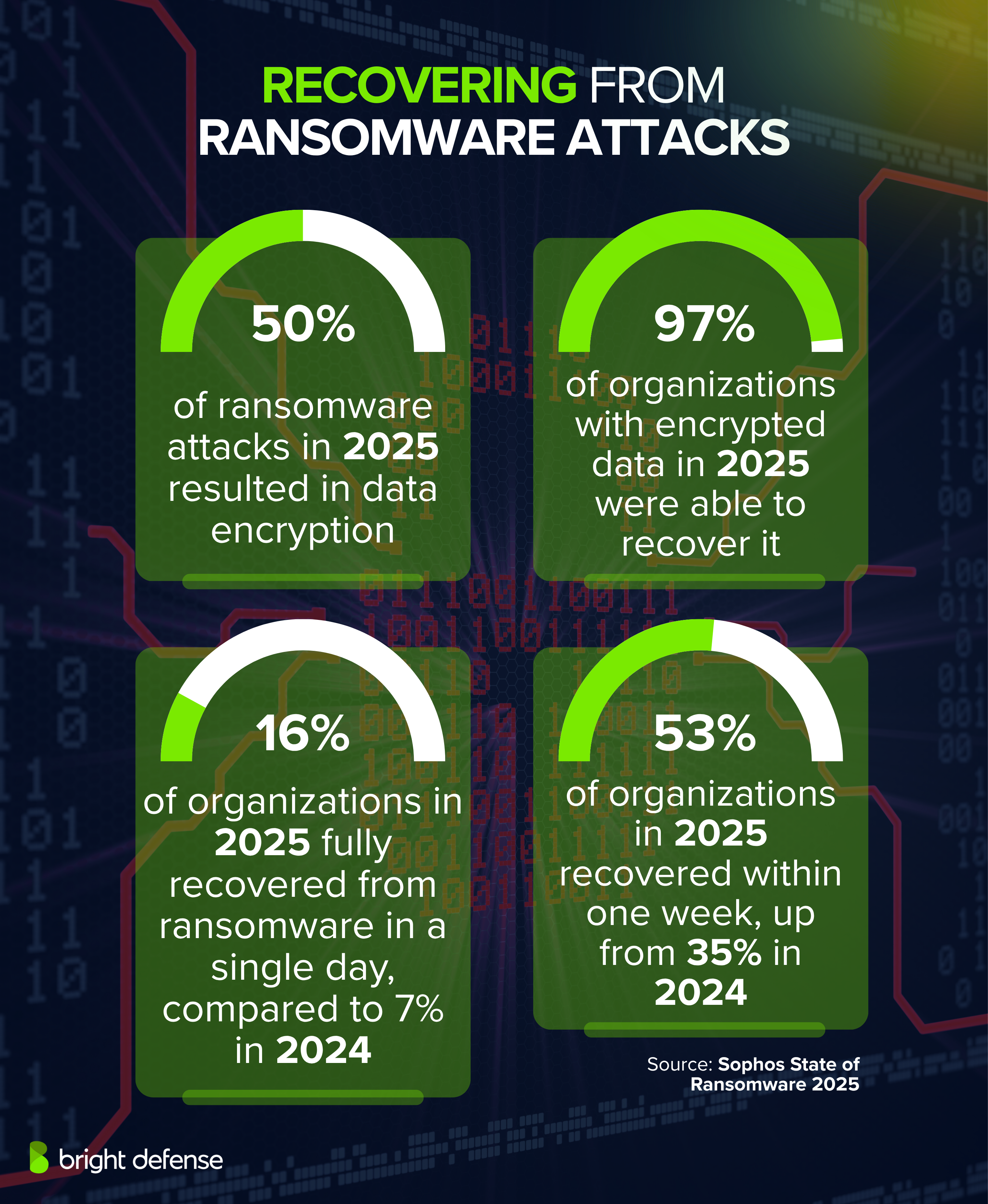
- 50% of ransomware attacks in 2025 resulted in data encryption, the lowest level in six years and a drop from 70% in 2024 (Sophos State of Ransomware 2025).
- 28% of organizations with encrypted data in 2025 also experienced data theft (Sophos State of Ransomware 2025).
- 97% of organizations with encrypted data in 2025 were able to recover it (Sophos State of Ransomware 2025).
- 54% of victims with encrypted data in 2025 restored it using backups, the lowest backup recovery rate in six years (Sophos State of Ransomware 2025).
- 49% of victims with encrypted data in 2025 paid the ransom to regain access (Sophos State of Ransomware 2025).
- 6% of ransomware attacks in 2025 involved extortion without encryption, double the 3% reported in 2024 (Sophos State of Ransomware 2025).
- The average cost to recover from ransomware in 2025 (excluding ransom payments) was $1.53 million, down from $2.73 million in 2024 (Sophos State of Ransomware 2025).
- 16% of organizations in 2025 fully recovered from ransomware in a single day, compared to 7% in 2024 (Sophos State of Ransomware 2025).
- 53% of organizations in 2025 recovered within one week, up from 35% in 2024 (Sophos State of Ransomware 2025).
- 97% of organizations in 2025 recovered within three months of a ransomware incident (Sophos State of Ransomware 2025).
Human Impact of Ransomware
- 41% of IT and security teams in 2025 reported increased anxiety or stress after their organization’s data was encrypted (Sophos State of Ransomware 2025).
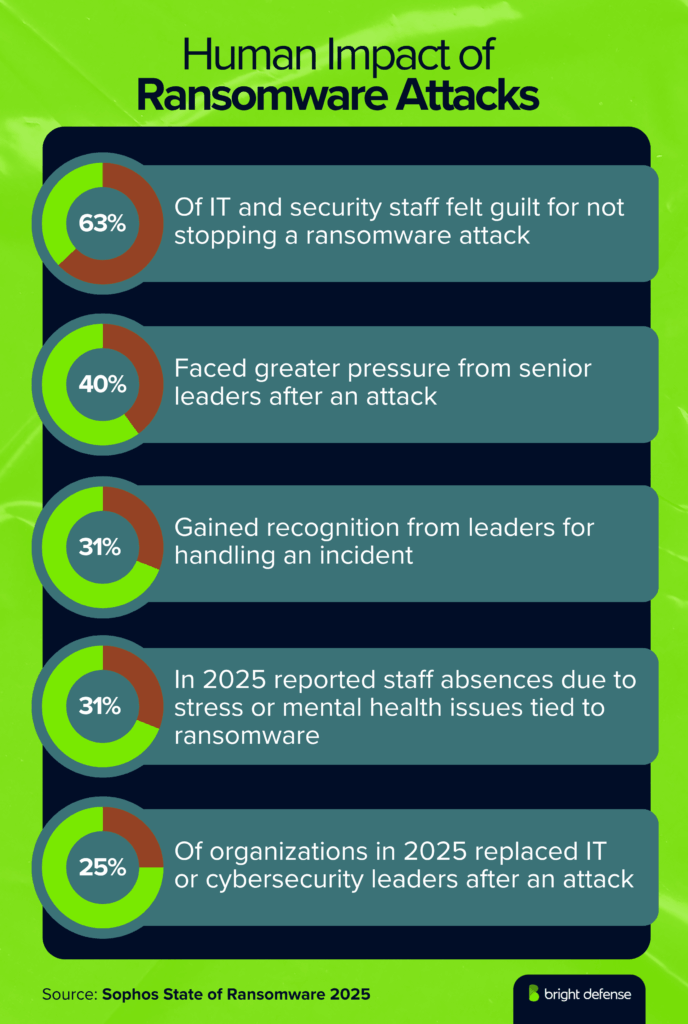
- 34% of IT and security teams in 2025 said they felt guilt for not stopping the ransomware attack (Sophos State of Ransomware 2025).
- 40% of IT and security teams in 2025 experienced greater pressure from senior leaders after a ransomware event (Sophos State of Ransomware 2025).
- 31% of IT and security teams in 2025 gained recognition from senior leaders for their handling of a ransomware attack (Sophos State of Ransomware 2025).
- 31% of IT and security teams in 2025 reported staff absences caused by stress or mental health issues linked to ransomware (Sophos State of Ransomware 2025).
- 25% of organizations in 2025 replaced their IT or cybersecurity leadership following a ransomware attack (Sophos State of Ransomware 2025).
Check out our verified 195 latest Cybersecurity Stats to gain insights into the latest threats and protection measures worldwide
Countrywise Ransomware Statistics
Here is a list of ransomware statistics from different countries. If you want to know the state of ransomware for a particular country, you can check this list. Currently, we have data for the following countries: Australia, Brazil, Chile, Colombia, France, Germany, India, Italy, Japan, Mexico, Singapore, South Africa, Spain, Switzerland, UAE, UK, and United States.
Most of the information comes from Sophos’ State of Ransomware Report published in 2025. You can also view their full report directly at: https://www.sophos.com/en-us/content/state-of-ransomware
Ransomware Statistics for the United States
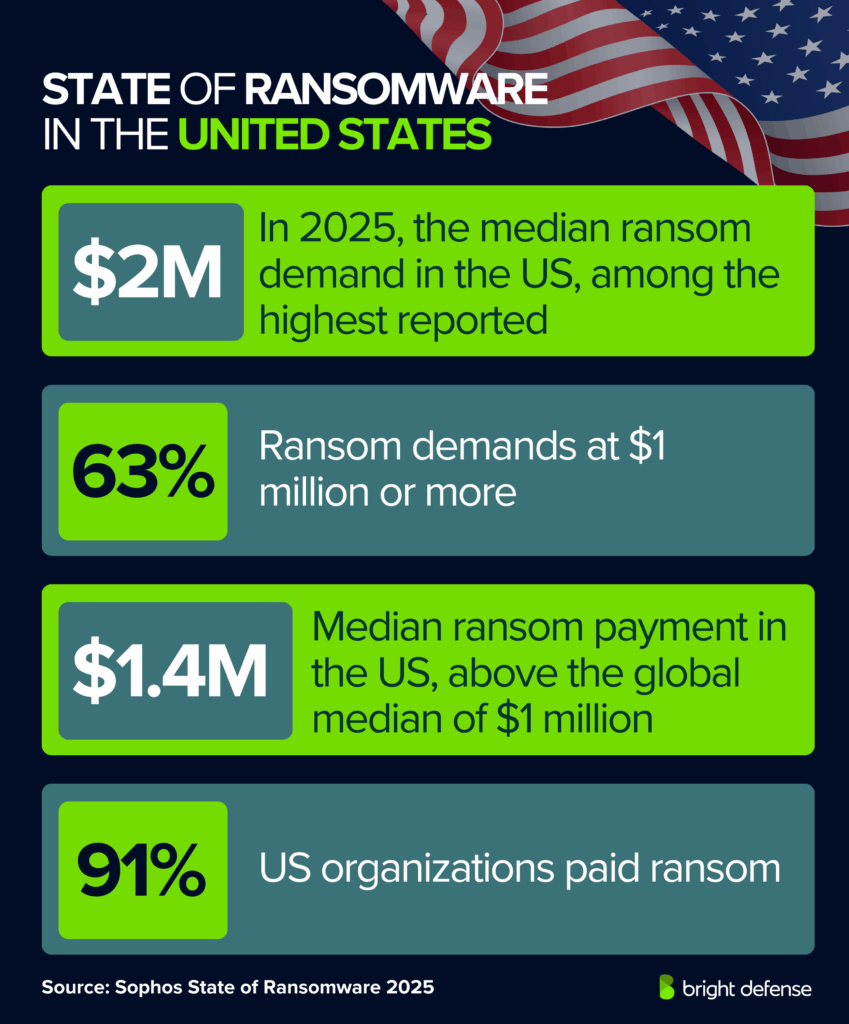
- In 2025, the median ransom demand in the US is $2 million, one of the highest among surveyed countries (Source).
- 63% of ransom demands are for $1 million or more (Source).
- The median ransom payment is $1.4 million, above the global median of $1 million (Source).
- On average, US organizations pay 91% of the ransom demanded, compared with the global average of 85% (Source).
- Outcomes vary: 28% of victims negotiate and pay less, 51% pay the full demand, and 21% end up paying more (Source).
- Ransomware in the US most often begins with exploited vulnerabilities (34%), followed by compromised credentials (22%) and malicious email (20%) (Source).
- Weaknesses contributing to incidents include lack of protection (45%) and unknown security gaps (43%) (Source).
- 40% of ransomware attacks in the US result in data encryption, down sharply from 61% in 2024 (Source).
- When data is encrypted, 29% of organizations also have data stolen (Source).
- 98% of organizations with encrypted data are able to recover it (Source).
- Recovery methods include ransom payments (47%) and restoring from backups (55%) (Source).
- The average cost to recover, excluding ransom payments, is $2.06 million, down from $3.26 million in 2024 (Source).
- Recovery speeds have improved: 54% of organizations recover within one week, compared with 35% last year, while 14% take one to six months, down from 29% in 2024 (Source).
- The human impact is significant: 47% of IT and security staff report stress or anxiety about future ransomware attacks, 44% feel guilty for not stopping them, and 43% face added pressure from leadership (Source).
- Workloads rise for 35% of teams, and 21% of staff experience absences linked to stress or mental health issues (Source).
- Leadership changes occur in 24% of organizations after ransomware incidents (Source).
Ransomware Stats for the United Kingdom
- In 2025, the median ransom demand in the UK is $2 million, similar to 2024 levels (Source).
- 61% of ransom demands in the UK are for $1 million or more (Source).
- The median ransom payment is $1.5 million, compared with $2 million in 2024 (Source).
- On average, UK organizations pay 89% of the ransom demanded, slightly above the global average of 85% (Source)
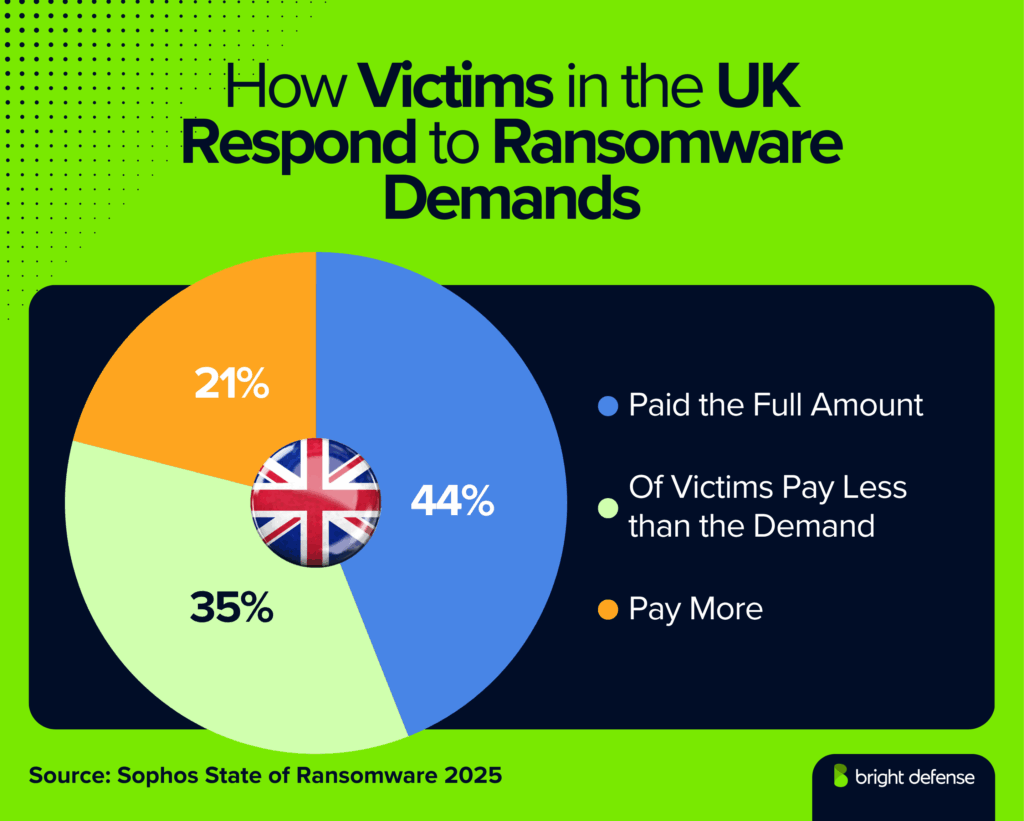
- Payment outcomes differ: 35% of victims pay less than the demand, 44% pay the full amount, and 21% pay more (Source).
- Ransomware in the UK most often starts with exploited vulnerabilities (37%), compromised credentials (21%), or malicious emails (18%) (Source).
- Contributing weaknesses include lack of staff or capacity (44%) and unknown security gaps (42%) (Source).
- 52% of ransomware incidents in the UK result in data encryption, down from 70% in 2024 (Source).
- When data is encrypted, 30% of organizations also experience data theft (Source).
- 97% of UK organizations with encrypted data are able to recover it, often through backups (57%) or ransom payments (49%) (Source).
- The average cost to recover, excluding ransom, is $1.7 million, down from $3.1 million in 2024 (Source).
- Recovery speeds improve: 57% of organizations recover within one week, up from 34% last year, while only 12% now take one to six months, down from 29% in 2024 (Source).
- The human impact is clear: 48% of IT and security staff report stress or anxiety about future attacks, 43% feel guilty for not stopping them, and 40% face added pressure from leadership (Source).
- Workloads increase for 36% of teams, 22% of staff experience absences tied to stress or mental health issues, and leadership changes occur in 25% of organizations after ransomware incidents (Source).
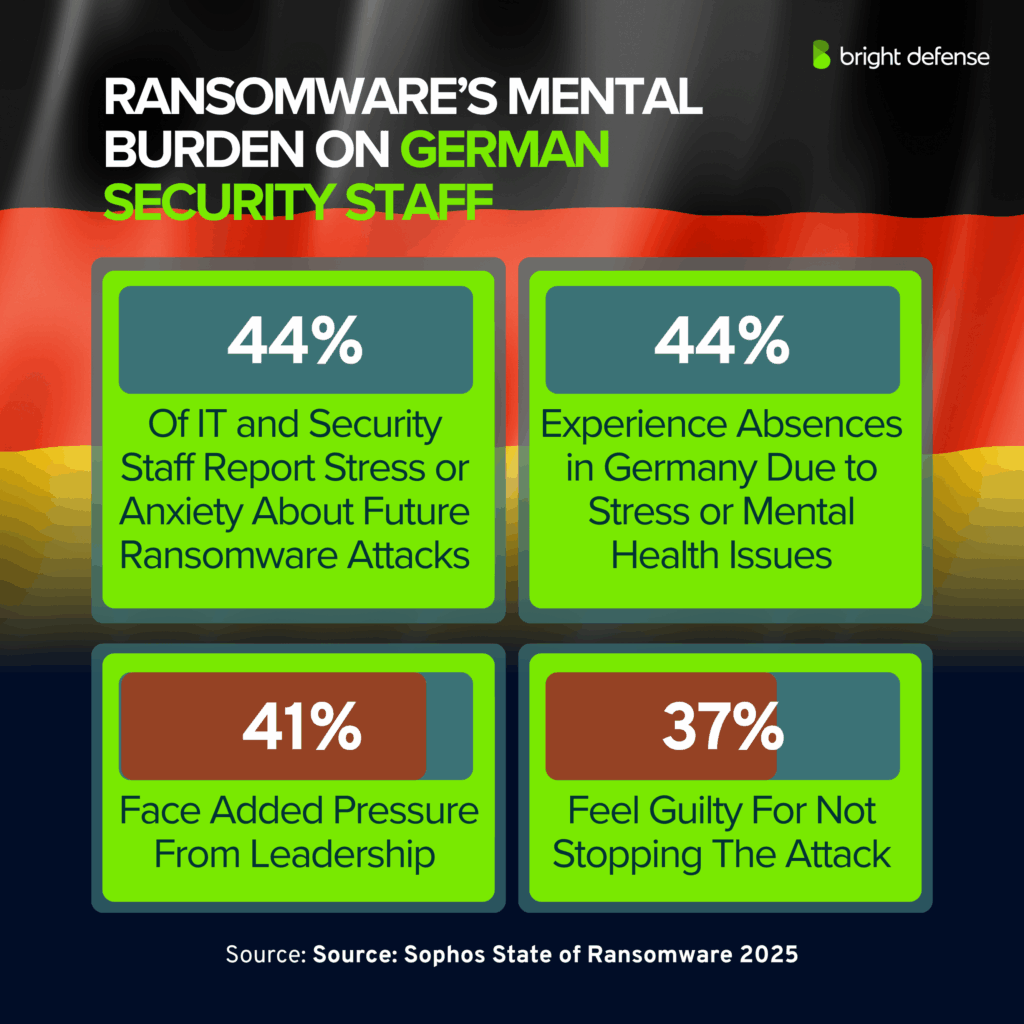
Ransomware Statistics for Germany
- In 2025, the median ransom demand in Germany is $600,000, a steep drop from $4.4 million in 2024 (Source).
- 49% of ransom demands are for $1 million or more, down from 62% last year (Source).
- The median ransom payment is $411,600, compared with $5.5 million in 2024 (Source).
- On average, German organizations pay 86% of the ransom demanded, close to the global average (Source).
- Payment outcomes vary: 47% of victims pay less than the demand, 32% pay the full demand, and 20% pay more (Source).
- Ransomware in Germany most often starts with exploited vulnerabilities (42%), followed by compromised credentials (20%) and malicious emails (19%) (Source).
- 51% of ransomware attacks result in data encryption, down from 79% in 2024 (Source).
- When data is encrypted, 24% of organizations also lose data to theft (Source).
- 95% of German organizations recover encrypted data, either through ransom payments (63%) or backups (59%) (Source).
- The average cost to recover, excluding ransom, is $1.56 million, down from $2.2 million in 2024 (Source).
- Recovery speeds improve: 64% of organizations recover within one week, compared with 24% in 2024, while only 9% now need one to six months, down from 34% last year (Source).
- The human impact is serious: 44% of IT and security staff report stress or anxiety about future ransomware attacks, 44% experience absences due to stress or mental health issues, 41% face added pressure from leadership, and 37% feel guilty for not stopping the attack (Source).
- Leadership changes follow in 27% of organizations after ransomware incidents (Source).
Ransomware Statistics for France
- 30% of ransomware attacks in France began with exploited vulnerabilities. (Source: Sophos – State of Ransomware)
- 24% of ransomware attacks in France started with malicious emails. (Source: Sophos – State of Ransomware)
- 23% of ransomware attacks in France were triggered by compromised credentials. (Source: Sophos – State of Ransomware)
- 43% of French organizations cited a known security gap as the main operational root cause of ransomware. (Source: Sophos – State of Ransomware)
- 42% of French organizations reported lack of expertise as a contributing factor in ransomware incidents. (Source: Sophos – State of Ransomware)
- The median ransom demand received by French organizations in 2024–2025 was $643,125. (Source: Sophos – State of Ransomware)
- The median ransom payment made by French organizations was $231,525. (Source: Sophos – State of Ransomware)
- French organizations typically paid 87% of ransom demands, slightly above the global average of 85%. (Source: Sophos – State of Ransomware)
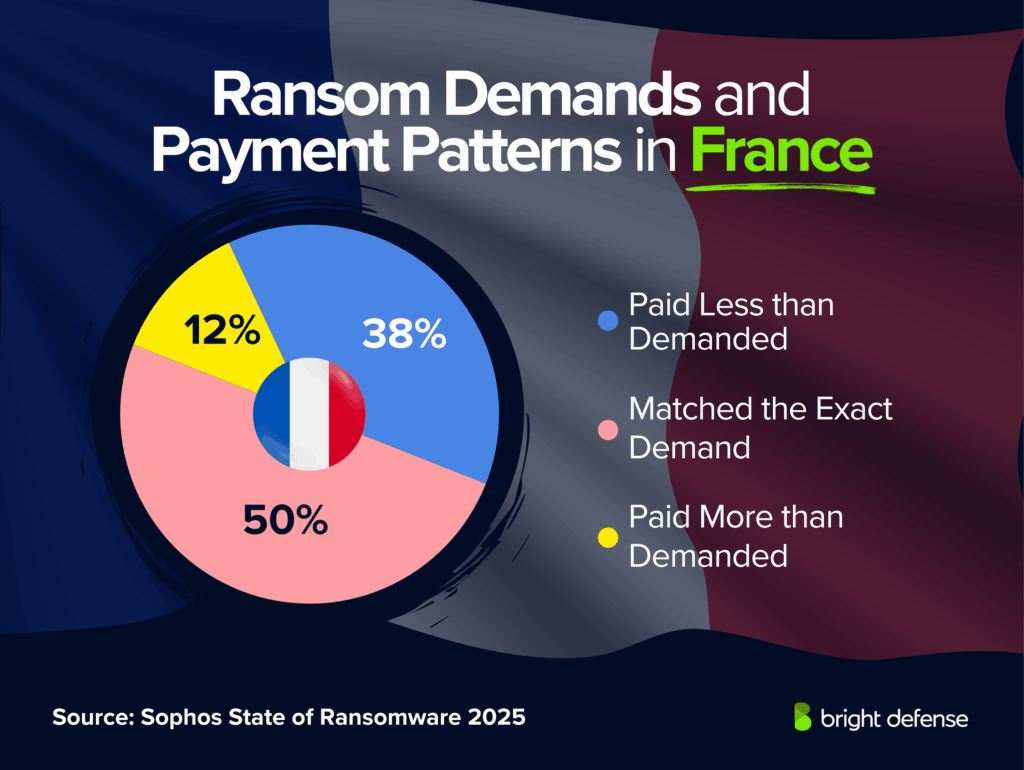
- 38% of French organizations that paid ransom ended up paying less than demanded. (Source: Sophos – State of Ransomware)
- 50% of French organizations that paid ransom matched the exact demand. (Source: Sophos – State of Ransomware)
- 12% of French organizations that paid ransom ended up paying more than demanded. (Source: Sophos – State of Ransomware)
- 58% of ransomware attacks in France led to data encryption, above the global average of 50%. (Source: Sophos – State of Ransomware)
- 44% of encrypted ransomware attacks in France also involved data theft. (Source: Sophos – State of Ransomware)
- 98% of French organizations that lost data to encryption managed to recover it. (Source: Sophos – State of Ransomware)
- 33% of French organizations recovered encrypted data by paying ransom, compared to 49% globally. (Source: Sophos – State of Ransomware)
- 60% of French organizations restored their data using backups after encryption. (Source: Sophos – State of Ransomware)
- The average cost for a French organization to recover from a ransomware attack was $1,220,000, down from $3.27 million in 2024. (Source: Sophos – State of Ransomware)
- 53% of French organizations fully recovered from ransomware within a week, up from 16% in 2024. (Source: Sophos – State of Ransomware)
- 18% of French organizations took between one and six months to fully recover from ransomware. (Source: Sophos – State of Ransomware)
- 50% of French cybersecurity staff reported higher anxiety or stress about future ransomware attacks. (Source: Sophos – State of Ransomware)
- 48% of French cybersecurity teams experienced increased workload after ransomware incidents. (Source: Sophos – State of Ransomware)
- 47% of French cybersecurity professionals felt guilt for not stopping ransomware attacks. (Source: Sophos – State of Ransomware)
- 22% of French cybersecurity teams reported staff absences due to stress or mental health issues. (Source: Sophos – State of Ransomware)
- 14% of French cybersecurity teams reported leadership replacement after a ransomware incident. (Source: Sophos – State of Ransomware)
Ransomware Statistics for Italy
- 35% of ransomware attacks in Italy began with exploited vulnerabilities. (Source: Sophos – State of Ransomware)
- 23% of ransomware attacks in Italy started with phishing. (Source: Sophos – State of Ransomware)
- 16% of ransomware attacks in Italy were triggered by compromised credentials. (Source: Sophos – State of Ransomware)
- 45% of Italian organizations cited lack of expertise as the main operational root cause of ransomware. (Source: Sophos – State of Ransomware)
- 37% of Italian organizations reported a known security gap as a contributing factor in ransomware incidents. (Source: Sophos – State of Ransomware)
- 36% of Italian organizations said weaknesses in defenses they were unaware of played a role in ransomware exposure. (Source: Sophos – State of Ransomware)
- The median ransom demand received by Italian organizations in 2024–2025 was $4,120,000. (Source: Sophos – State of Ransomware)
- The median ransom payment made by Italian organizations was $2,060,000. (Source: Sophos – State of Ransomware)
Italian organizations typically paid 97% of ransom demands, far higher than the global average of 85%. (Source: Sophos – State of Ransomware) - 62% of Italian organizations that paid ransom ended up paying less than demanded. (Source: Sophos – State of Ransomware)
- 14% of Italian organizations that paid ransom matched the exact demand. (Source: Sophos – State of Ransomware)
- 24% of Italian organizations that paid ransom ended up paying more than demanded. (Source: Sophos – State of Ransomware)
- 55% of ransomware attacks in Italy led to data encryption, above the global average of 50%. (Source: Sophos – State of Ransomware)
- 11% of encrypted ransomware attacks in Italy also involved data theft. (Source: Sophos – State of Ransomware)
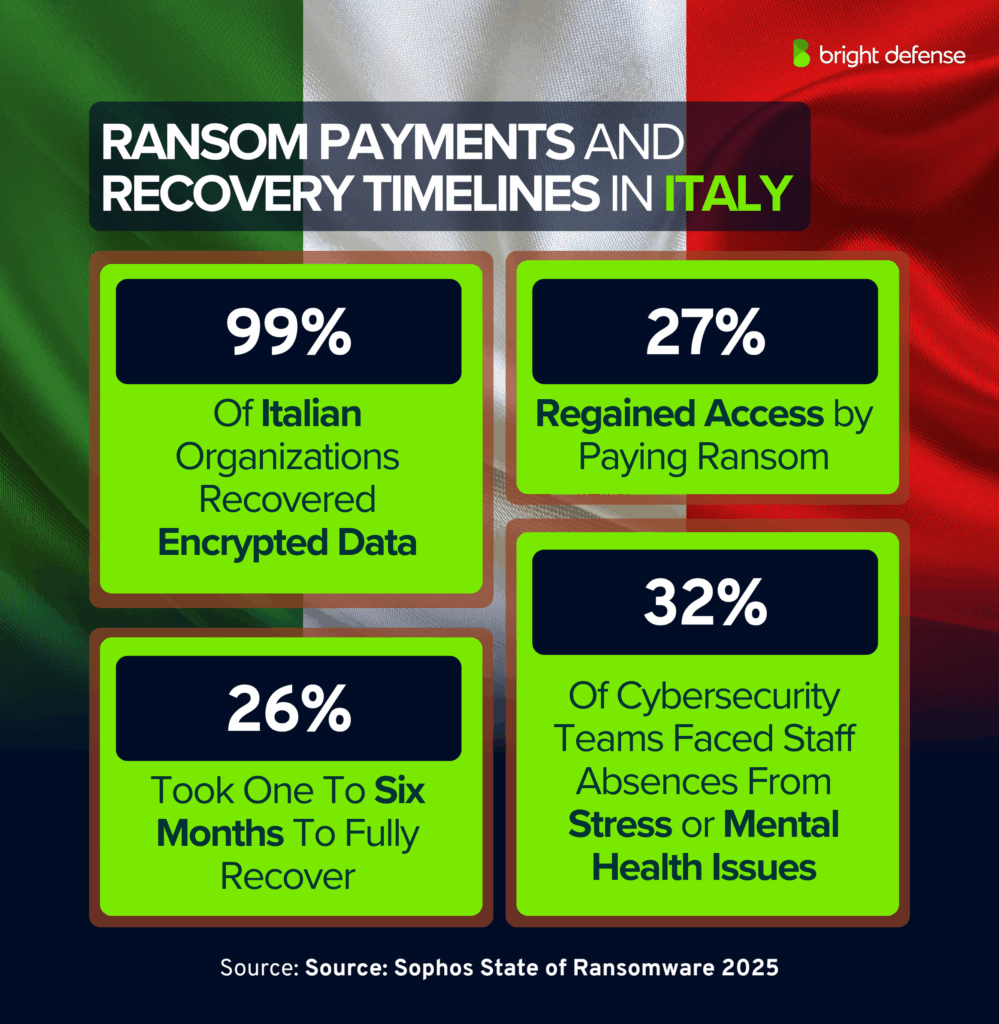
- 99% of Italian organizations that lost data to encryption managed to recover it. (Source: Sophos – State of Ransomware)
- 27% of Italian organizations recovered encrypted data by paying ransom, compared to 49% globally. (Source: Sophos – State of Ransomware)
- 58% of Italian organizations restored their data using backups after encryption. (Source: Sophos – State of Ransomware)
- The average cost for an Italian organization to recover from a ransomware attack was $3,550,000, down from $5.38 million in 2024. (Source: Sophos – State of Ransomware)
- 46% of Italian organizations fully recovered from ransomware within a week, up from 23% in 2024. (Source: Sophos – State of Ransomware)
- 26% of Italian organizations took between one and six months to fully recover from ransomware. (Source: Sophos – State of Ransomware)
- 39% of Italian cybersecurity teams reported changes to team or organizational structure after ransomware incidents. (Source: Sophos – State of Ransomware)
- 36% of Italian cybersecurity teams reported increased workload after ransomware incidents. (Source: Sophos – State of Ransomware)
- 35% of Italian cybersecurity staff reported higher anxiety or stress about future ransomware attacks. (Source: Sophos – State of Ransomware)
- 32% of Italian cybersecurity teams reported staff absences due to stress or mental health issues. (Source: Sophos – State of Ransomware)
Ransomware Statistics for Spain
- 30% of ransomware attacks in Spain began with exploited vulnerabilities. (Source: Sophos – State of Ransomware)
- 21% of ransomware attacks in Spain started with compromised credentials. (Source: Sophos – State of Ransomware)
- 17% of ransomware attacks in Spain were triggered by malicious emails. (Source: Sophos – State of Ransomware)
- 42% of Spanish organizations cited a known security gap as the main operational root cause of ransomware. (Source: Sophos – State of Ransomware)
- 41% of Spanish organizations reported a lack of people or capacity as a contributing factor in ransomware incidents. (Source: Sophos – State of Ransomware)
- 39% of Spanish organizations said lack of expertise and unknown gaps played a role in ransomware exposure. (Source: Sophos – State of Ransomware)
- The median ransom demand received by Spanish organizations in 2024–2025 was $911,600. (Source: Sophos – State of Ransomware)
- The median ransom payment made by Spanish organizations was $322,500. (Source: Sophos – State of Ransomware)
- Spanish organizations typically paid 80% of ransom demands, below the global average of 85%. (Source: Sophos – State of Ransomware)
- 72% of Spanish organizations that paid ransom ended up paying less than demanded. (Source: Sophos – State of Ransomware)
- 28% of Spanish organizations that paid ransom matched the exact demand. (Source: Sophos – State of Ransomware)
- 47% of ransomware attacks in Spain led to data encryption, slightly below the global average of 50%. (Source: Sophos – State of Ransomware)
- 36% of encrypted ransomware attacks in Spain also involved data theft. (Source: Sophos – State of Ransomware)
- 100% of Spanish organizations that lost data to encryption managed to recover it. (Source: Sophos – State of Ransomware)
- 36% of Spanish organizations recovered encrypted data by paying ransom, compared to 49% globally. (Source: Sophos – State of Ransomware)
- 70% of Spanish organizations restored their data using backups after encryption. (Source: Sophos – State of Ransomware)
- The average cost for a Spanish organization to recover from a ransomware attack was $1,150,000, down from $3.43 million in 2024. (Source: Sophos – State of Ransomware)
- 49% of Spanish organizations fully recovered from ransomware within a week, an increase from 27% in 2024. (Source: Sophos – State of Ransomware)
- 24% of Spanish organizations took between one and six months to fully recover from ransomware. (Source: Sophos – State of Ransomware)
- 36% of Spanish cybersecurity teams reported increased workload after ransomware incidents. (Source: Sophos – State of Ransomware)
- 33% of Spanish cybersecurity staff reported higher anxiety or stress about future ransomware attacks. (Source: Sophos – State of Ransomware)
- 28% of Spanish cybersecurity staff faced greater pressure from senior leadership after a ransomware incident. (Source: Sophos – State of Ransomware)
- 27% of Spanish cybersecurity professionals felt guilt for not stopping ransomware attacks. (Source: Sophos – State of Ransomware)
- 25% of Spanish cybersecurity teams reported staff absences due to stress or mental health issues after ransomware incidents. (Source: Sophos – State of Ransomware)
Ransomware Statistics for Switzerland
- In 2025, the median ransom demand in Switzerland is $328,748, a sharp drop from $3.97 million in 2024 (Source).
- 46% of ransom demands are for $1 million or more, down from 81% last year (Source).
- The median ransom payment is $1.1 million (Source).
- On average, organizations pay 76% of the ransom demanded, below the global average of 85% (Source).
- Outcomes vary: 65% of victims negotiate and pay less than the demand, 15% pay the exact demand, and 20% end up paying more (Source).
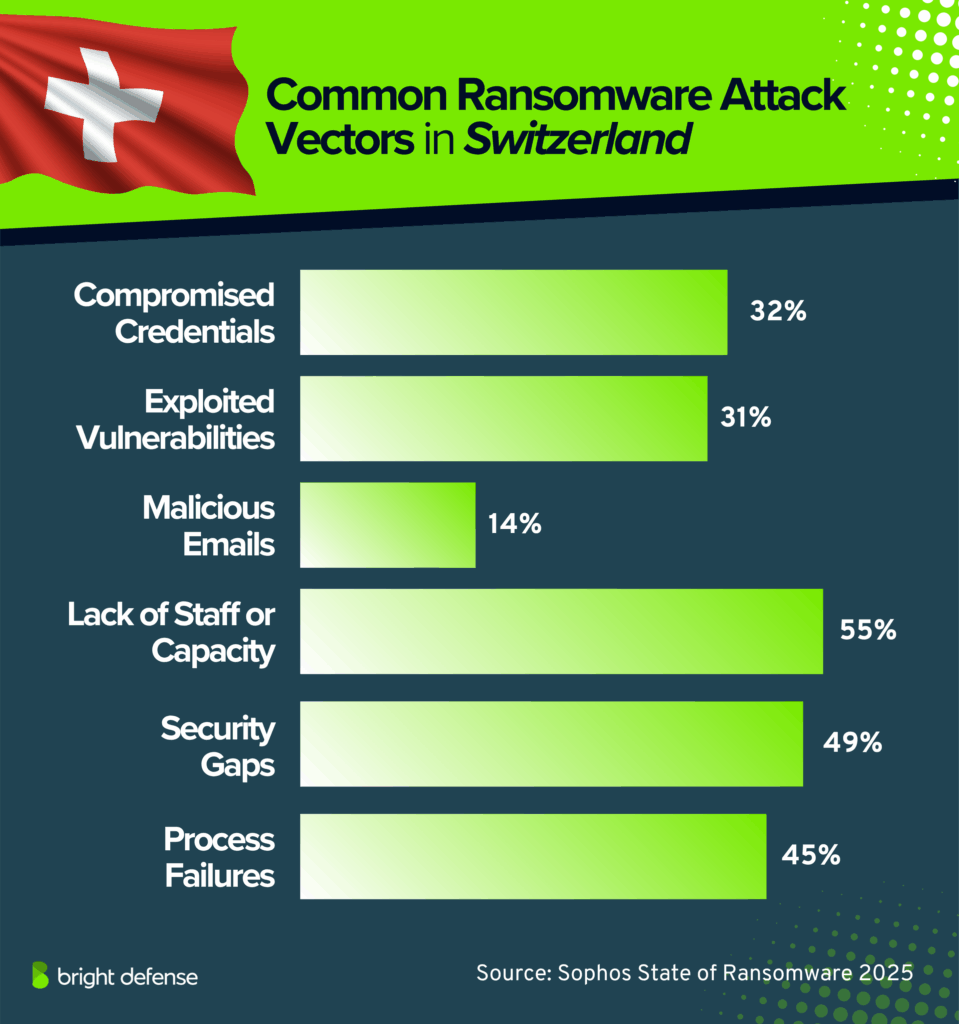
- Ransomware in Switzerland most often starts with compromised credentials (32%) or exploited vulnerabilities (31%), while 14% of attacks begin with malicious emails (Source).
- Human and operational weaknesses contribute: 55% cite lack of staff or capacity, 49% cite known security gaps, and 45% blame mistakes or process failures (Source).
- 53% of ransomware incidents result in data encryption, down from 68% in 2024 (Source).
- When data is encrypted, 10% of organizations also lose data to theft, down from 29% last year (Source).
- 97% of victims recover encrypted data, typically through backups (56%) or ransom payments (54%) (Source).
- The average cost to recover, excluding ransom, is $1.04 million, a drop from $3.11 million in 2024 (Source).
- Recovery times improve: 58% of organizations are back on their feet within one week, up from 26% in 2024, while only 9% now need one to six months, down from 41% last year (Source).
- The human toll is clear: 64% of IT and security teams report staff absences linked to stress or mental health issues, 38% feel guilty for not stopping attacks, 31% face added pressure from leadership, and 28% suffer heightened anxiety (Source).
- Leadership changes follow in 26% of organizations after ransomware incidents (Source).
Ransomware Statistics for Australia
- In 2025, $217,000 is the median ransom demand, a large drop from $4.42 million in 2024. (Sophos – State of Ransomware in Australia)
- 41% of Australian organizations pay the ransom to recover their data, down sharply from 66% last year. (Sophos – State of Ransomware in Australia)
- On average, Australian organizations pay 88% of the ransom demanded. (Sophos – State of Ransomware in Australia)
- 52% of victims pay less than the initial demand. (Sophos – State of Ransomware in Australia)
- The most common technical cause of attacks is exploited vulnerabilities (28%), followed by phishing (24%) and compromised credentials (21%). (Sophos – State of Ransomware in Australia)
- Operational weaknesses contributing to attacks include lack of protection (45%), lack of people/capacity (44%), and security gaps (known or unknown) cited by 41%. (Sophos – State of Ransomware in Australia)
- 33% of ransomware attacks in Australia result in data being encrypted, well below both the global average and last year’s rate. (Sophos – State of Ransomware in Australia)
- Of those Australian organizations with encrypted data, 98% are able to recover it. (Sophos – State of Ransomware in Australia)
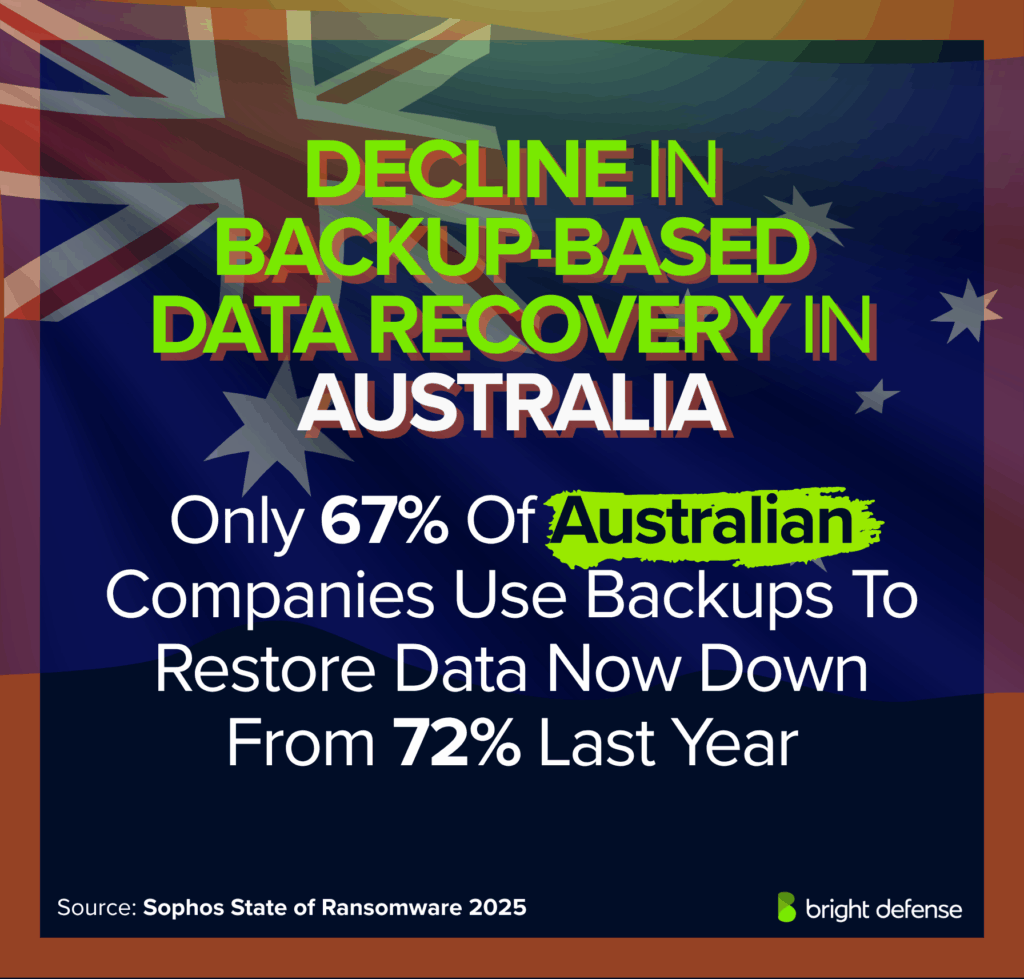
- Backup use is falling: 67% of Australian companies use backups to restore data, down from 72% last year. (Sophos – State of Ransomware in Australia)
- The average cost to recover (excluding ransom) drops to $650,000, from $2.37 million in 2024. (Sophos – State of Ransomware in Australia)
- 47% of Australian organizations fully recover from a ransomware attack within one week, up from 36% last year. (Sophos – State of Ransomware in Australia)
- Only 13% of organizations take between one to six months to recover, a drop from 33% in 2024. (Sophos – State of Ransomware in Australia)
The State of Ransomware in Japan
- In 2025, the median ransom demand in Japan is $1.3 million, down from $2.5 million in 2024 (Source).
- 58% of ransom demands are for $1 million or more (Source).
- The median ransom payment is $1 million, compared with $2.3 million in 2024 (Source).
- On average, Japanese organizations pay 88% of the ransom demanded, above the global average of 85% (Source).
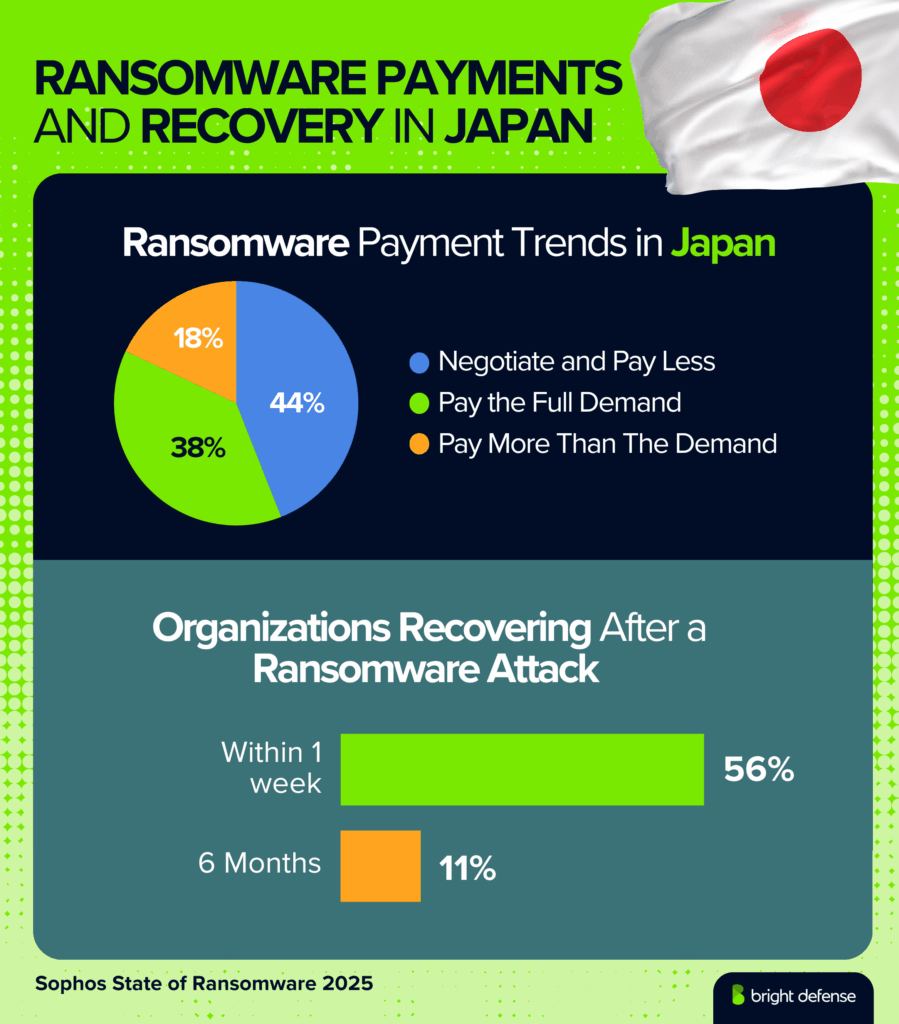
- Victim outcomes vary: 44% negotiate and pay less, 38% pay the full demand, and 18% pay more (Source).
- Ransomware most often begins with exploited vulnerabilities (39%), compromised credentials (23%), or malicious emails (17%) (Source).
- Contributing weaknesses include lack of protection (42%) and unknown security gaps (40%) (Source).
- 47% of ransomware attacks in Japan result in data encryption, down from 64% in 2024 (Source).
- 27% of organizations experience data theft despite data encryption (Source).
- 98% of Japanese organizations with encrypted data are able to recover it, often through backups (60%) or ransom payments (45%) (Source).
- The average cost to recover, excluding ransom payments, is $1.32 million, down from $2.7 million in 2024 (Source).
- Recovery times are improving: 56% of organizations recover within one week, up from 33% last year, while only 11% now take one to six months, down from 31% in 2024 (Source).
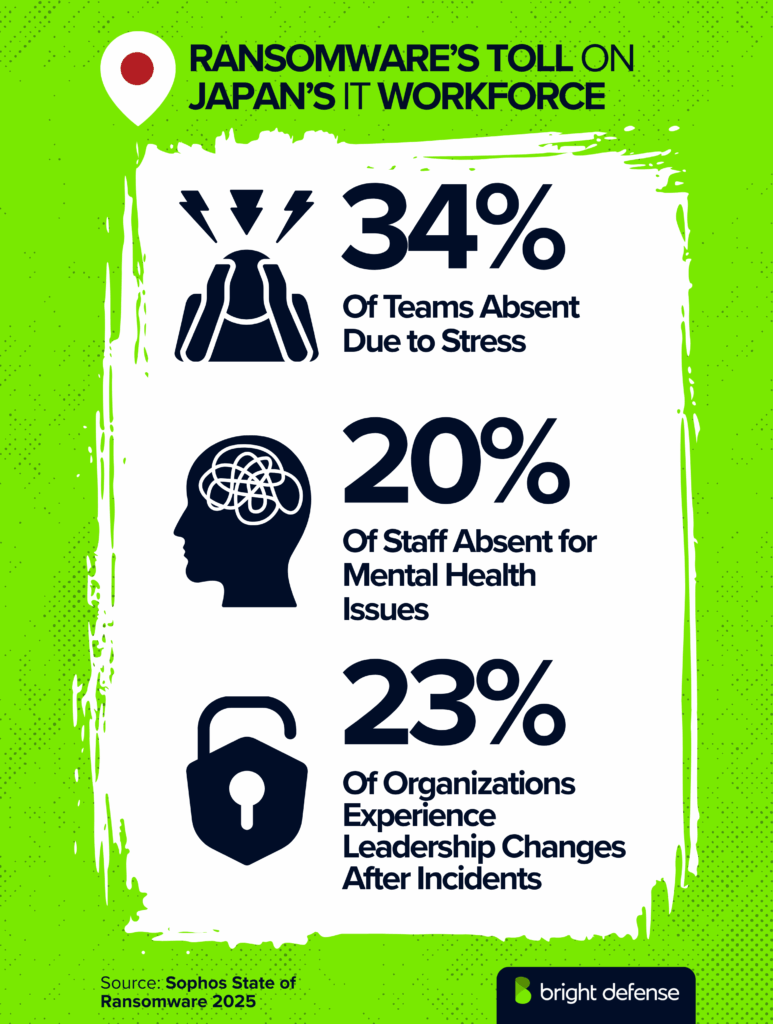
- The human impact is heavy: 46% of IT and security staff feel stressed or anxious about future attacks, 42% feel guilty for not stopping them, and 41% face added pressure from senior leadership (Source).
- Workloads rise for 34% of teams, 20% of staff are absent due to stress or mental health issues, and leadership changes occur in 23% of organizations after incidents (Source).
Ransomware Statistics for the United Arab Emirates
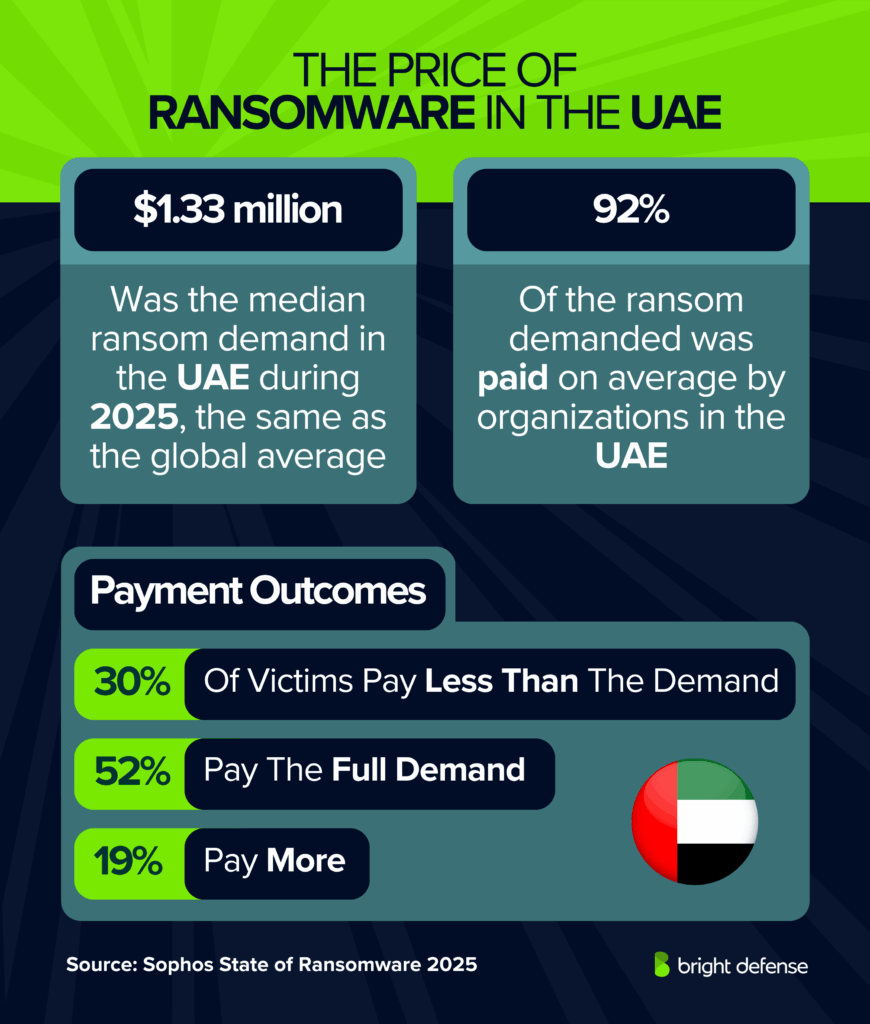
- In 2025, the median ransom demand and payment in the UAE is $1.33 million, the same as the global average (Source).
- 59% of ransom demands are for $1 million or more (Source).
- On average, organizations in the UAE pay 92% of the ransom demanded, higher than the global average of 85% (Source).
- Payment outcomes differ: 30% of victims pay less than the ransom demand, 52% pay the full demand, and 19% pay more (Source).
- Ransomware most often begins with exploited vulnerabilities (42% of cases), followed by malicious email (23%) and compromised credentials (18%) (Source).
- Operational weaknesses include unknown security gaps (49%), lack of protection (36%), and poor-quality protection (36%) (Source).
- 55% of ransomware incidents result in data encryption, higher than the global average of 50% (Source).
- When data is encrypted, 43% of organizations also experience data theft, far above the 28% global average (Source).
- 98% of UAE organizations are able to recover encrypted data (Source).
- Recovery often comes through backups (68%) or ransom payments (43%) (Source).
- The average cost to recover, excluding ransom, is $1.41 million, slightly below the global average of $1.53 million (Source).
- Recovery times are improving: 63% of organizations recover within a week, compared to the global average of 53%, while 15% need one to six months, slightly below the global average of 18% (Source).
- The human impact is significant: 42% of IT and security staff feel more stress or anxiety about future attacks, 40% feel guilty for not stopping them, 40% face pressure from senior leadership, and 37% report heavier workloads after incidents (Source).
- 18% of staff experience absences linked to stress or mental health issues, and leadership changes follow in 18% of organizations (Source).
Ransomware Statistics for Singapore
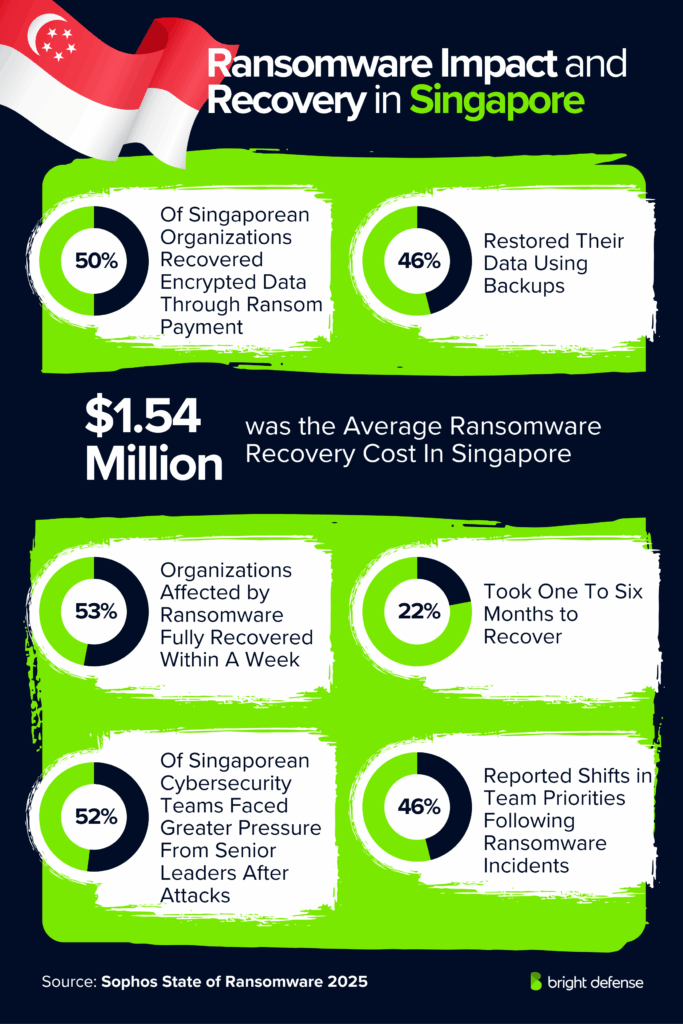
- 36% of ransomware attacks in Singapore began with phishing. (Source: Sophos – State of Ransomware)
- 29% of ransomware attacks in Singapore started with malicious emails. (Source: Sophos – State of Ransomware)
- 17% of ransomware attacks in Singapore were triggered by compromised credentials. (Source: Sophos – State of Ransomware)
- 47% of Singaporean organizations cited lack of protection as the main operational root cause of ransomware. (Source: Sophos – State of Ransomware)
- 43% of Singaporean organizations reported lack of people or capacity as a contributing factor in ransomware incidents. (Source: Sophos – State of Ransomware)
- 39% of Singaporean organizations said their cybersecurity tools failing to prevent attacks contributed to exposure. (Source: Sophos – State of Ransomware)
- The median ransom demand received by Singaporean organizations in 2024–2025 was $365,565. (Source: Sophos – State of Ransomware)
- Singaporean organizations typically paid 94% of ransom demands, above the global average of 85%. (Source: Sophos – State of Ransomware)
- 35% of Singaporean organizations that paid ransom matched the exact demand. (Source: Sophos – State of Ransomware)
- 26% of Singaporean organizations that paid ransom ended up paying more than demanded. (Source: Sophos – State of Ransomware)
- 53% of ransomware attacks in Singapore led to data encryption, slightly above the global average of 50%. (Source: Sophos – State of Ransomware)
- 10% of encrypted ransomware attacks in Singapore also involved data theft. (Source: Sophos – State of Ransomware)
- 100% of Singaporean organizations that lost data to encryption managed to recover it. (Source: Sophos – State of Ransomware)
- 50% of Singaporean organizations recovered encrypted data by paying ransom, compared to 49% globally. (Source: Sophos – State of Ransomware)
- 46% of Singaporean organizations restored their data using backups after encryption. (Source: Sophos – State of Ransomware)
- The average cost for a Singaporean organization to recover from a ransomware attack was $1,540,000, down from $2.20 million in 2024. (Source: Sophos – State of Ransomware)
- 53% of Singaporean organizations fully recovered from ransomware within a week, down from 77% in 2024. (Source: Sophos – State of Ransomware)
- 22% of Singaporean organizations took between one and six months to fully recover from ransomware. (Source: Sophos – State of Ransomware)
- 52% of Singaporean cybersecurity teams reported increased pressure from senior leaders after ransomware incidents. (Source: Sophos – State of Ransomware)
- 46% of Singaporean cybersecurity teams reported a change of team priorities or focus after ransomware incidents. (Source: Sophos – State of Ransomware)
- 42% of Singaporean cybersecurity staff reported higher anxiety or stress about future ransomware attacks. (Source: Sophos – State of Ransomware)
- 25% of Singaporean cybersecurity professionals felt guilty for not stopping ransomware attacks. (Source: Sophos – State of Ransomware)
Ransomware Statistics for India
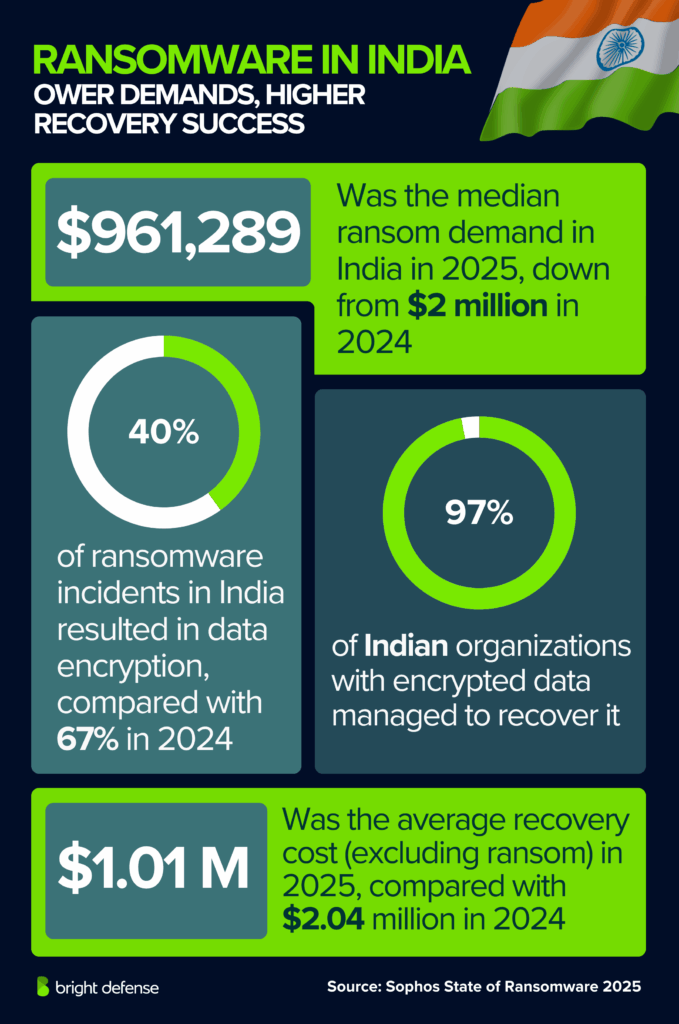
- In 2025, the median ransom demand in India is $961,289, down from $2 million in 2024 (Source).
- 49% of ransom demands are for $1 million or more, compared with 62% last year (Source).
- The median ransom payment is $481,636, far lower than $2.3 million in 2024 (Source).
- On average, Indian organizations pay 80% of the ransom demanded, slightly below the global average (Source).
- 53% of victims pay the ransom to restore data, down from 65% last year (Source).
- Ransomware most often starts with exploited vulnerabilities (29%), compromised credentials (22%), or malicious emails (21%) (Source).
- Contributing weaknesses include lack of staff or capacity (41%) and lack of security tools or services (39%) (Source).
- 40% of ransomware incidents in India result in data encryption, down from 67% in 2024 (Source).
- When data is encrypted, 31% of organizations also experience data theft, up from 22% in 2024 (Source).
- 97% of Indian organizations with encrypted data are able to recover it, usually through backups (47%) or ransom payments (53%) (Source).
- The average cost to recover, excluding ransom, is $1.01 million, compared with $2.04 million in 2024 (Source).
- Recovery speeds are improving: 51% of organizations recover within one week, up from 31% last year, while 13% now take one to six months, down from 36% in 2024 (Source).
- The human impact is heavy: 43% of IT and security staff report stress or anxiety about future attacks, 40% feel guilty for not stopping them, and 36% face increased pressure from leadership (Source).
- Workloads rise for 32% of teams, 21% of staff are absent due to stress or mental health issues, and leadership changes occur in 22% of organizations after incidents (Source).
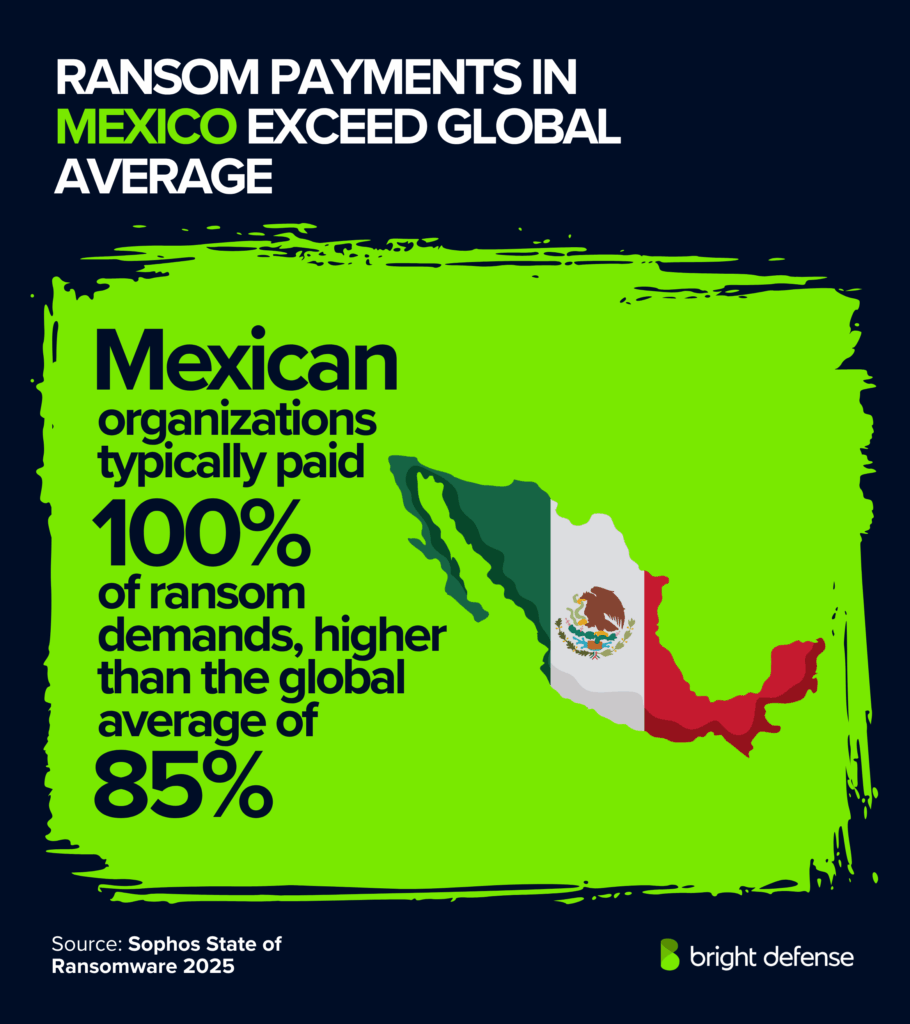
Ransomware Statistics for Mexico
- 45% of ransomware attacks in Mexico began with exploited vulnerabilities. (Source: Sophos – State of Ransomware)
- 28% of ransomware attacks in Mexico started with compromised credentials. (Source: Sophos – State of Ransomware)
- 13% of ransomware attacks in Mexico were triggered by malicious emails. (Source: Sophos – State of Ransomware)
- 47% of Mexican organizations cited a known security gap as the main operational root cause of ransomware. (Source: Sophos – State of Ransomware)
- 43% of Mexican organizations reported an unknown security gap as a contributing factor in ransomware incidents. (Source: Sophos – State of Ransomware)
- 40% of Mexican organizations said a lack of skills or knowledge played a role in their ransomware exposure. (Source: Sophos – State of Ransomware)
- The median ransom demand received by Mexican organizations in 2024–2025 was $2,000,000. (Source: Sophos – State of Ransomware)
- The median ransom payment made by Mexican organizations was $1,000,000. (Source: Sophos – State of Ransomware)
- Nearly 70% of ransom demands in Mexico were for $1 million or more. (Source: Sophos – State of Ransomware)
- Mexican organizations typically paid 100% of ransom demands, higher than the global average of 85%. (Source: Sophos – State of Ransomware)
- 46% of Mexican organizations that paid ransom ended up paying less than demanded. (Source: Sophos – State of Ransomware)
- 23% of Mexican organizations that paid ransom met the exact demand from attackers. (Source: Sophos – State of Ransomware)
- 31% of Mexican organizations that paid ransom ended up paying more than demanded. (Source: Sophos – State of Ransomware)
- 50% of ransomware attacks in Mexico led to data encryption, equal to the global average. (Source: Sophos – State of Ransomware)
- 52% of encrypted ransomware attacks in Mexico also involved data theft. (Source: Sophos – State of Ransomware)
- 100% of Mexican organizations that lost data to encryption managed to recover it. (Source: Sophos – State of Ransomware)
- Only 23% of Mexican organizations recovered encrypted data by paying ransom, compared to 49% globally. (Source: Sophos – State of Ransomware)
- 68% of Mexican organizations restored their data using backups after encryption. (Source: Sophos – State of Ransomware)
- The average cost for a Mexican organization to recover from a ransomware attack was $1,350,000, slightly below the $1.53 million global average. (Source: Sophos – State of Ransomware)
- 64% of Mexican organizations fully recovered from ransomware within a week, higher than the 53% global average. (Source: Sophos – State of Ransomware)
- Only 10% of Mexican organizations took between one and six months to fully recover from ransomware. (Source: Sophos – State of Ransomware)
- 39% of Mexican cybersecurity teams experienced increased workload after ransomware incidents. (Source: Sophos – State of Ransomware)
- 32% of Mexican cybersecurity staff reported higher anxiety or stress about future ransomware attacks. (Source: Sophos – State of Ransomware)
- 32% of Mexican cybersecurity staff faced greater pressure from senior leadership after a ransomware incident. (Source: Sophos – State of Ransomware)
- 30% of Mexican cybersecurity professionals felt guilt for not stopping ransomware attacks. (Source: Sophos – State of Ransomware)
- 21% of Mexican cybersecurity teams reported staff absences due to stress or mental health issues after ransomware incidents. (Source: Sophos – State of Ransomware)
Ransomware Statistics for Brazil
- 44% of ransomware attacks in Brazil began with exploited vulnerabilities. (Source: Sophos – State of Ransomware)
- 20% of ransomware attacks in Brazil started with compromised credentials. (Source: Sophos – State of Ransomware)
- 18% of ransomware attacks in Brazil were triggered by malicious emails. (Source: Sophos – State of Ransomware)
- 47% of Brazilian organizations cited a known security gap as the main operational root cause of ransomware. (Source: Sophos – State of Ransomware)
- 39% of Brazilian organizations reported lack of people or capacity as a contributing factor in ransomware incidents. (Source: Sophos – State of Ransomware)
- 35% of Brazilian organizations said internal mistakes or failures to follow processes played a role in ransomware exposure. (Source: Sophos – State of Ransomware)
- The median ransom demand received by Brazilian organizations in 2024–2025 was $392,500. (Source: Sophos – State of Ransomware)
- The median ransom payment made by Brazilian organizations was $400,000. (Source: Sophos – State of Ransomware)
- Brazilian organizations typically paid 86% of ransom demands, in line with the global average of 85%. (Source: Sophos – State of Ransomware)
- 55% of Brazilian organizations that paid ransom ended up paying less than demanded. (Source: Sophos – State of Ransomware)
- 11% of Brazilian organizations that paid ransom matched the exact demand. (Source: Sophos – State of Ransomware)
- 34% of Brazilian organizations that paid ransom ended up paying more than demanded. (Source: Sophos – State of Ransomware)
- 54% of ransomware attacks in Brazil led to data encryption, above the global average of 50%. (Source: Sophos – State of Ransomware)
- 22% of encrypted ransomware attacks in Brazil also involved data theft. (Source: Sophos – State of Ransomware)
- 100% of Brazilian organizations that lost data to encryption managed to recover it. (Source: Sophos – State of Ransomware)
- 66% of Brazilian organizations recovered encrypted data by paying ransom. (Source: Sophos – State of Ransomware)
- 73% of Brazilian organizations restored their data using backups after encryption. (Source: Sophos – State of Ransomware)
- The average cost for a Brazilian organization to recover from a ransomware attack was $1,190,000, down from $2.73 million in 2024. (Source: Sophos – State of Ransomware)
- 55% of Brazilian organizations fully recovered from ransomware within a week, up from 28% in 2024. (Source: Sophos – State of Ransomware)
- 20% of Brazilian organizations took between one and six months to fully recover from ransomware. (Source: Sophos – State of Ransomware)
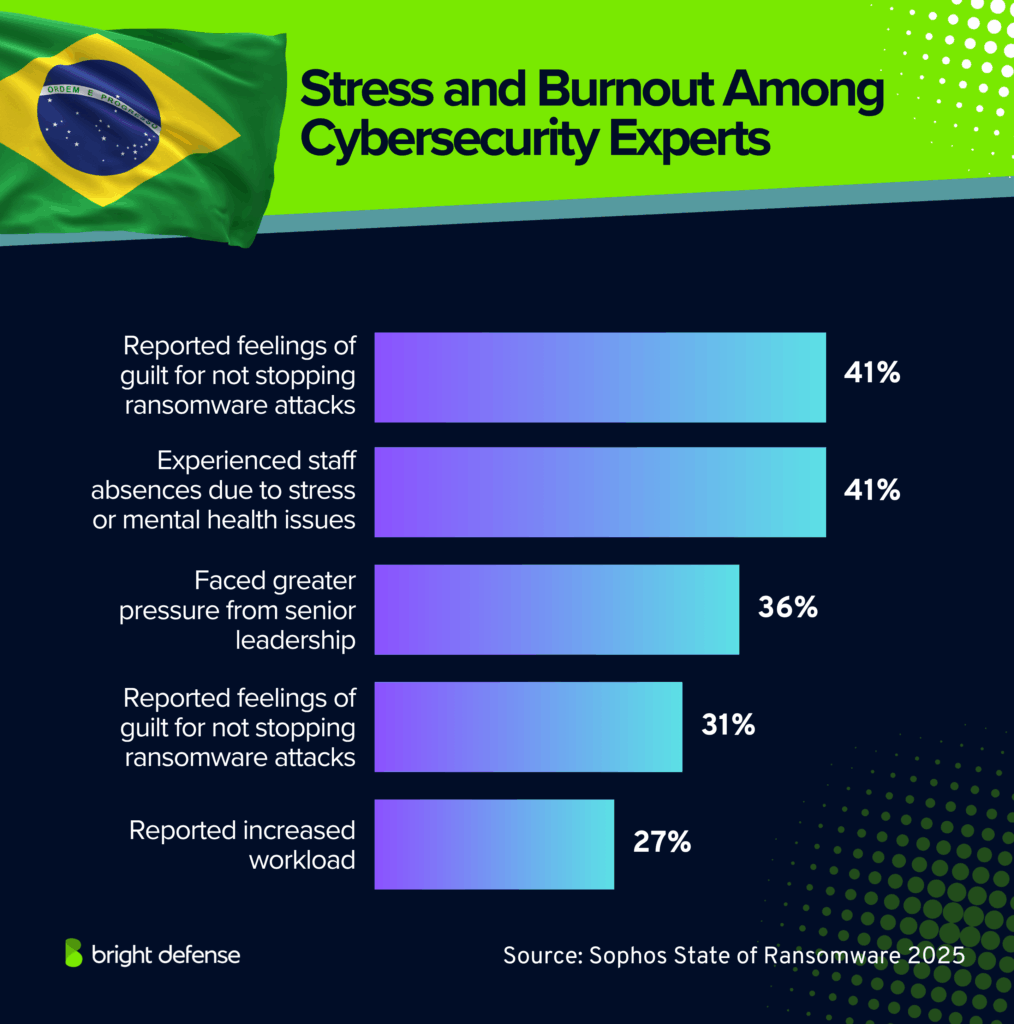
- 41% of Brazilian cybersecurity professionals reported feelings of guilt for not stopping ransomware attacks. (Source: Sophos – State of Ransomware)
- 41% of Brazilian cybersecurity teams experienced staff absences due to stress or mental health issues after ransomware incidents. (Source: Sophos – State of Ransomware)
- 36% of Brazilian cybersecurity staff faced greater pressure from senior leadership after a ransomware incident. (Source: Sophos – State of Ransomware)
- 31% of Brazilian cybersecurity staff reported higher anxiety or stress about future ransomware attacks. (Source: Sophos – State of Ransomware)
- 27% of Brazilian cybersecurity teams reported increased workload after ransomware incidents. (Source: Sophos – State of Ransomware)
Ransomware Statistics for Colombia
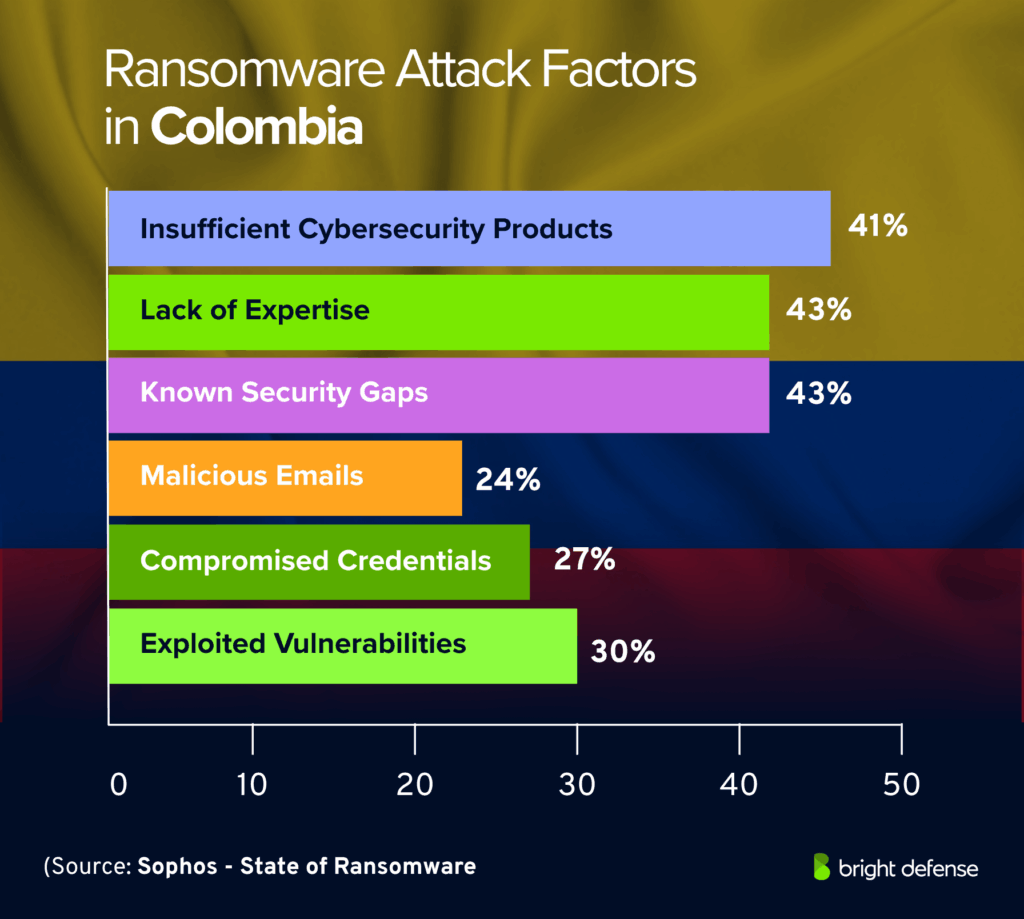
- 30% of ransomware attacks in Colombia began with exploited vulnerabilities. (Source: Sophos – State of Ransomware)
- 27% of ransomware attacks in Colombia started with compromised credentials. (Source: Sophos – State of Ransomware)
- 24% of ransomware attacks in Colombia were triggered by malicious emails. (Source: Sophos – State of Ransomware)
- 43% of Colombian organizations cited known security gaps as a key reason for falling victim to ransomware. (Source: Sophos – State of Ransomware)
- 43% of Colombian organizations admitted that lack of expertise contributed to ransomware incidents. (Source: Sophos – State of Ransomware)
- 41% of Colombian organizations reported that not having the right cybersecurity products or services left them exposed to ransomware. (Source: Sophos – State of Ransomware)
- The median ransom demand received by Colombian organizations in 2024–2025 was $60,000. (Source: Sophos – State of Ransomware)
- The median ransom payment made by Colombian organizations was $40,000. (Source: Sophos – State of Ransomware)
- On average, Colombian organizations paid 78% of the initial ransom demand, compared to the global average of 85%. (Source: Sophos – State of Ransomware)
- 70% of Colombian organizations that paid ransom ended up paying less than the original demand. (Source: Sophos – State of Ransomware)
- 20% of Colombian organizations that paid ransom matched the exact demand from attackers. (Source: Sophos – State of Ransomware)
- 10% of Colombian organizations that paid ransom ended up paying more than what was demanded. (Source: Sophos – State of Ransomware)
- 45% of ransomware attacks in Colombia led to data encryption, slightly below the 50% global average. (Source: Sophos – State of Ransomware)
- 18% of Colombian organizations that experienced encryption also had their data stolen. (Source: Sophos – State of Ransomware)
- 98% of Colombian organizations that lost data to encryption were able to recover it. (Source: Sophos – State of Ransomware)
- Only 18% of Colombian organizations recovered encrypted data by paying the ransom, compared to 49% globally. (Source: Sophos – State of Ransomware)
- 56% of Colombian organizations restored their data using backups after ransomware encryption. (Source: Sophos – State of Ransomware)
- The average cost for a Colombian organization to recover from a ransomware attack was $870,000, lower than the $1.53 million global average. (Source: Sophos – State of Ransomware)
- 50% of Colombian organizations fully recovered from ransomware within a week, just under the 53% global average. (Source: Sophos – State of Ransomware)
- 25% of Colombian organizations needed between one and six months to fully recover from ransomware. (Source: Sophos – State of Ransomware)
- 45% of Colombian cybersecurity teams reported at least one team member taking absence due to stress or mental health issues after a ransomware incident. (Source: Sophos – State of Ransomware)
- 44% of Colombian cybersecurity staff felt guilt for failing to stop ransomware attacks. (Source: Sophos – State of Ransomware)
- 33% of Colombian cybersecurity teams experienced increased workload following a ransomware attack. (Source: Sophos – State of Ransomware)
- 29% of Colombian cybersecurity staff reported higher levels of anxiety or stress about future attacks. (Source: Sophos – State of Ransomware)
- 24% of Colombian cybersecurity staff experienced greater pressure from senior leaders after a ransomware incident. (Source: Sophos – State of Ransomware)
Ransomware Statistics for Chile
- 46% of ransomware attacks in Chile began with exploited vulnerabilities. (Source: Sophos – State of Ransomware in Chile)
- 22% of ransomware attacks in Chile started with compromised credentials. (Source: Sophos – State of Ransomware in Chile)
- 20% of ransomware attacks in Chile were triggered by malicious emails. (Source: Sophos – State of Ransomware in Chile)
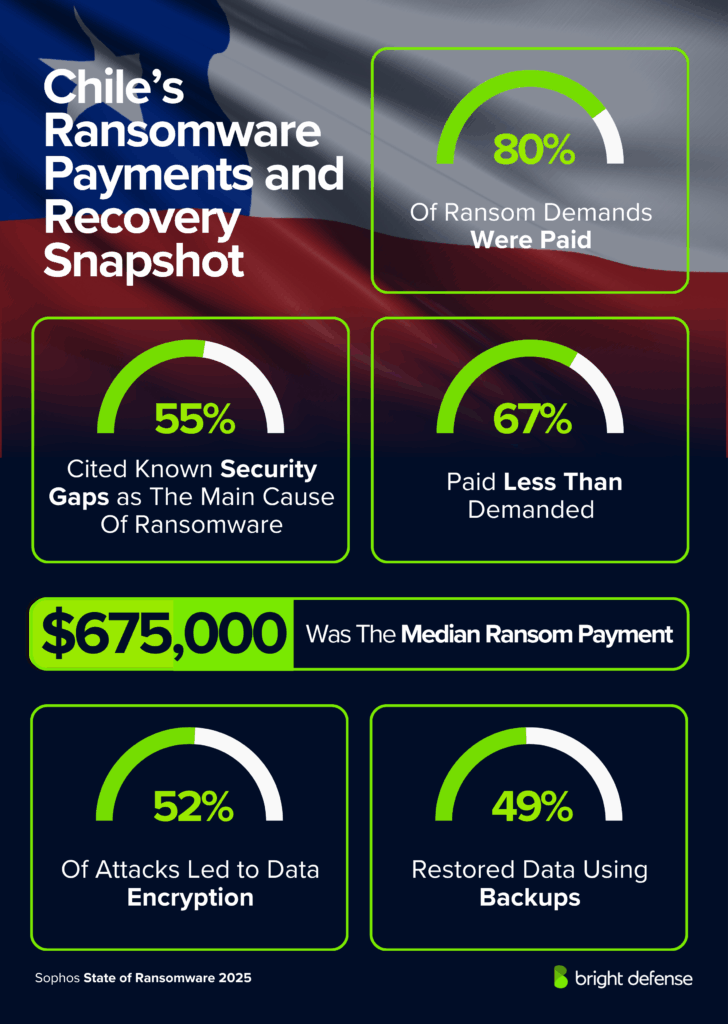
- 55% of Chilean organizations cited a known security gap as the main operational root cause of ransomware. (Source: Sophos – State of Ransomware)
- 44% of Chilean organizations said lack of people or monitoring capacity played a role in ransomware exposure. (Source: Sophos – State of Ransomware in Chile)
- The median ransom demand received by Chilean organizations in 2024–2025 was $1,000,000. (Source: Sophos – State of Ransomware in Chile)
- The median ransom payment made by Chilean organizations was $675,000. (Source: Sophos – State of Ransomware in Chile)
- Chilean organizations typically paid 80% of ransom demands, lower than the global average of 85%. (Source: Sophos – State of Ransomware in Chile)
- 67% of Chilean organizations that paid ransom ended up paying less than demanded. (Source: Sophos – State of Ransomware in Chile)
- 19% of Chilean organizations that paid ransom matched the exact demand. (Source: Sophos – State of Ransomware in Chile)
- 14% of Chilean organizations that paid ransom ended up paying more than demanded. (Source: Sophos – State of Ransomware in Chile)
- 52% of ransomware attacks in Chile led to data encryption. (Source: Sophos – State of Ransomware)
- 17% of encrypted ransomware attacks in Chile also involved data theft. (Source: Sophos – State of Ransomware)
- 97% of Chilean organizations that lost data to encryption managed to recover it. (Source: Sophos – State of Ransomware)
- 56% of Chilean organizations recovered encrypted data by paying ransom. (Source: Sophos – State of Ransomware)
- 49% of Chilean organizations restored their data using backups after encryption. (Source: Sophos – State of Ransomware in Chile)
- The average cost for a Chilean organization to recover from a ransomware attack was $1,200,000, below the $1.53 million global average. (Source: Sophos – State of Ransomware)
- 65% of Chilean organizations fully recovered from ransomware within a week, well above the 53% global average. (Source: Sophos – State of Ransomware in Chile)
- Only 8% of Chilean organizations took between one and six months to fully recover from ransomware. (Source: Sophos – State of Ransomware in Chile)
- 37% of Chilean cybersecurity teams reported increased pressure from senior leaders. (Source: Sophos – State of Ransomware in Chile)
- 35% of Chilean cybersecurity staff reported increased workload after ransomware incidents. (Source: Sophos – State of Ransomware in Chile)
- 33% of Chilean cybersecurity teams reported staff absences due to stress or mental health issues. (Source: Sophos – State of Ransomware in Chile)
Ransomware Statistics for South Africa
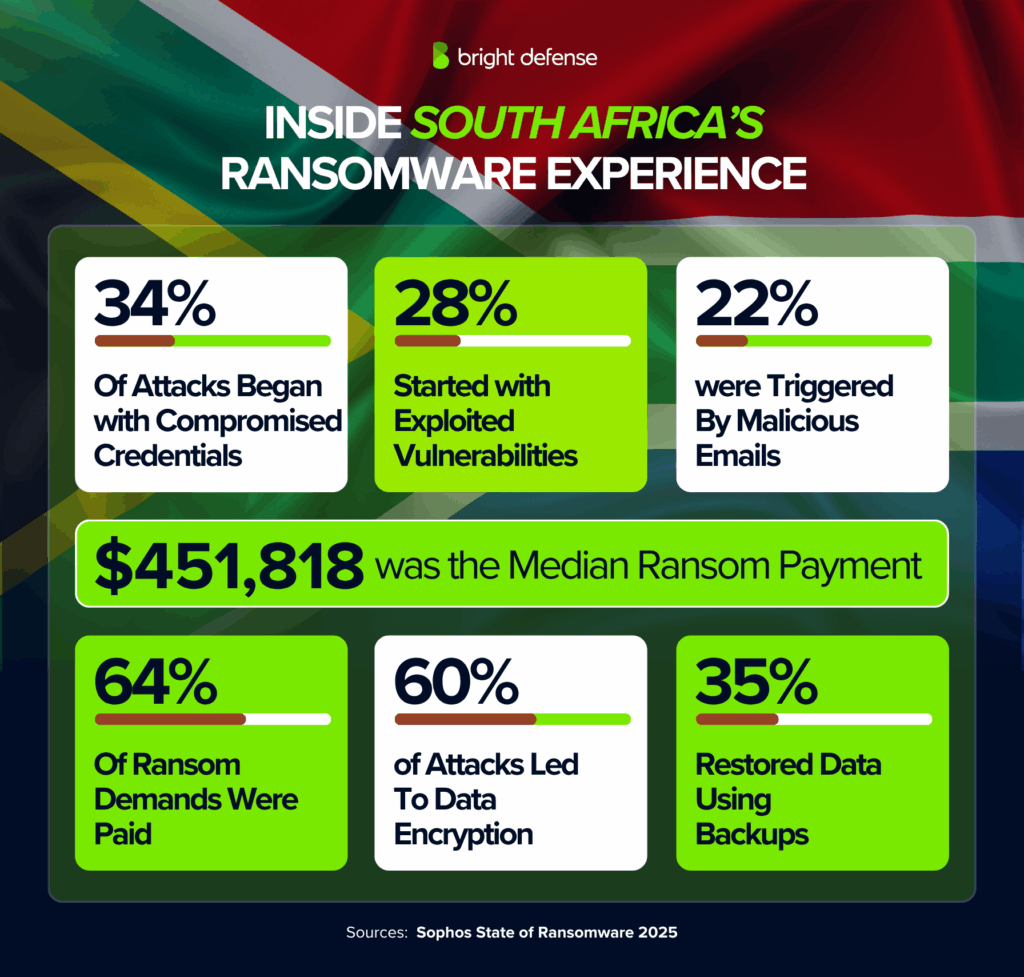
- 34% of ransomware attacks in South Africa began with compromised credentials, reflecting how successful attacks often exploit weak access controls. (Source: Sophos – State of Ransomware in South Africa)
- 28% of ransomware attacks in South Africa started with exploited vulnerabilities, and the same period showed a rise in phishing as a secondary infection path. (Source: Sophos – State of Ransomware in South Africa)
- 22% of ransomware attacks in South Africa were triggered by malicious emails, which law enforcement has warned remain a primary channel for global ransomware attacks. (Source: Sophos – State of Ransomware in South Africa)
- 58% of South African organizations cited lack of expertise as the main operational root cause of ransomware, with many victims reporting difficulty containing incidents. (Source: Sophos – State of Ransomware in South Africa)
- 55% of South African organizations reported lack of protection as a contributing factor in ransomware incidents, and mitigation strategies were often missing from security policies. (Source: Sophos – State of Ransomware in South Africa)
- 53% of South African organizations said unknown weaknesses in defenses played a role in ransomware exposure, leading to reputational harm when breaches became public. (Source: Sophos – State of Ransomware in South Africa)
- The median ransom payment made by South African organizations was $451,818, yet the actual number of reported cases is believed to be higher according to ransomware statistics released in 2025. (Source: Sophos – State of Ransomware in South Africa)
- South African organizations typically paid 64% of ransom demands, much lower than the global average of 85%, showing that falling victim did not always lead to full compliance with demands. (Source: Sophos – State of Ransomware in South Africa)
- 60% of South African organizations that paid ransom ended up paying less than demanded, while the healthcare sector reported higher sensitivity to downtime and data exposure. (Source: Sophos – State of Ransomware in South Africa)
- 35% of South African organizations that paid ransom matched the exact demand, even though cybersecurity professionals continued to warn against paying the ransom directly.(Source: Sophos – State of Ransomware in South Africa)
- 4% of South African organizations that paid ransom ended up paying more than demanded, which created growing threat concerns for regulators.(Source: Sophos – State of Ransomware in South Africa)
- 60% of ransomware attacks in South Africa led to data encryption, above the global average of 50%, and in many cases, attackers threatened to exfiltrate data as additional pressure. (Source: Sophos – State of Ransomware in South Africa)
- 39% of encrypted ransomware attacks in South Africa also involved data theft, which resulted in lost productivity and damaged trust among customers. (Source: Sophos – State of Ransomware in South Africa)
- 90% of South African organizations that lost data to encryption managed to recover it, though reputational damage sometimes lingered long after technical recovery. (Source: Sophos – State of Ransomware in South Africa)
- 71% of South African organizations recovered encrypted data by paying ransom, despite experts advising that new attack variants often make restoration incomplete. (Source: Sophos – State of Ransomware in South Africa)
- 35% of South African organizations restored their data using backups after encryption, but without stronger defenses, threats may repeat in the first half of the following year. (Source: Sophos – State of Ransomware in South Africa)
- The average cost for a South African organization to recover from a ransomware attack was $1,310,000, up from $1.04 million in 2024, showing a growing financial impact beyond technical response. (Source: Sophos – State of Ransomware in South Africa)
- 47% of South African organizations fully recovered from ransomware within a week, up from 41% in 2024, though others continued to respond for longer periods. (Source: Sophos – State of Ransomware in South Africa)
- 19% of South African organizations took between one and six months to fully recover from ransomware, revealing how threatening campaigns strain both operations and morale. (Source: Sophos – State of Ransomware in South Africa)
- 76% of South African cybersecurity staff reported increased pressure from senior leaders after ransomware incidents, as global ransomware trends pushed executives to demand faster protection. (Source: Sophos – State of Ransomware in South Africa)
- 47% of South African cybersecurity staff reported higher anxiety or stress about future ransomware attacks, with some pointing to the lack of mitigation strategies at the organizational level. (Source: Sophos – State of Ransomware in South Africa)
- 42% of South African cybersecurity teams reported increased workload after ransomware incidents, and many victims described the burden as overwhelming. (Source: Sophos – State of Ransomware in South Africa)
- 37% of South African cybersecurity teams reported a change of team priorities or focus, showing how organizations adapt only after successful attacks disrupt operations. (Source: Sophos – State of Ransomware in South Africa)
- 29% of South African cybersecurity professionals felt guilt for not stopping ransomware attacks, highlighting how reputational harm and operational failures affect staff directly. (Source: Sophos – State of Ransomware in South Africa)
Cyber threats are everywhere, and the numbers back it up. Check out 200+ cybersecurity stats that show what’s really happening across the digital world.
How Many People Were Affected by Ransomware?
Ransomware surged through 2024 and 2025, with over 5,000 incidents in 2024, 10–15% higher than 2023, after a 77% spike the year before.
More than 195 million records were exposed, including the Lurie Children’s Hospital breach that hit 791,000 people. The United States accounted for about half of the victims, followed by Europe and Eurasia.
Commercial services faced the most attacks, while healthcare, manufacturing, and technology suffered major impacts. UnitedHealth Group’s Change Healthcare breach alone cost around 3 billion dollars. About two-thirds of schools and universities reported attacks.
Ransom demands climbed, including a 75 million dollar payout to Dark Angels. LockBit stayed the most active strain, and at least 55 new groups appeared despite law enforcement actions like Operation Cronos.
In early 2025, momentum rose sharply. Q1 saw 2,063 victims, more than double Q1 2024, with Clop behind 17% through mass software exploitation. H1 2025 leak site counts hit 3,734 victims, up 67% year over year, with 88 active groups midyear—35 of them new. RaaS models allowed fast toolset changes, while tactics leaned toward data theft and extortion.
Total ransom payments dropped 35% in 2024 to about 813 million dollars, though recovery costs stayed high. Governments logged 208 incidents in H1 2025, up 65%, with the United States accounting for over a third. Healthcare and education remained major targets, with recovery averaging 4 million dollars per case. Overall, ransomware reached record levels through 2025, with more actors, shifting methods, and heavy financial tolls.
Lazarus: The Ransomware Masterminds That Shook the World
The Lazarus Group is a state-sponsored hacking organization widely believed to operate under North Korea’s direction. Feared across the cybersecurity world, the group blends espionage, financial theft, and digital warfare with remarkable precision. Its operations stretch from major banks to global corporations, leaving a trail of chaos and financial loss.
Lazarus’s growing reliance on ransomware has made it one of the most dangerous cyber actors of the modern age. These attacks are not just about profit—they serve as tools of intimidation, disruption, and geopolitical strategy. Three major operations—Sony Pictures, Bangladesh Bank Heist, and WannaCry—define the group’s rise from covert saboteurs to ransomware masterminds.
1. Sony Pictures Attack – 2014
In 2014, Lazarus struck Sony Pictures Entertainment, leaking internal files, emails, and unreleased films. The attackers deployed wiper malware that crippled systems, causing widespread disruption. The U.S. government traced the operation to North Korea, linking it to the satirical film The Interview. This attack displayed Lazarus’s willingness to weaponize code for political revenge.
2. Bangladesh Bank Heist – 2016
In 2016, Lazarus breached the Bangladesh Central Bank’s SWIFT payment system, attempting to steal nearly $1 billion. While most transactions were halted, $81 million vanished through accounts in the Philippines. This attack revealed Lazarus’s shift toward financially driven cybercrime, laying the groundwork for later ransomware operations designed to generate funding under global sanctions.
3. WannaCry Ransomware
WannaCry was a massive ransomware attack that struck on May 12, 2017, infecting more than 200,000 computers across 150 countries. It spread through a Windows vulnerability known as EternalBlue, a cyber tool originally developed by the U.S. National Security Agency (NSA) and later leaked online by a hacker group called the Shadow Brokers.
The ransomware encrypted files on infected computers, appending the extension “.WNCRY”, and demanded $300 in Bitcoin for decryption. It crippled vital systems, most notably the UK’s National Health Service (NHS), which lost access to patient records and had to cancel surgeries.
A cybersecurity researcher, Marcus Hutchins, accidentally stopped the spread by registering a hidden “kill switch” domain embedded in the code. Investigations later linked the attack to North Korea’s Lazarus Group, suggesting the operation was less about money and more about disruption.
The incident exposed the danger of stockpiling cyber exploits and marked one of the most destructive ransomware outbreaks in history.
What Are the Top Five Ransomware Attacks that Happened Recently?
Several ransomware incidents in 2025 demonstrated severe disruption and broad impact across industries.
MGM Resorts faced lasting fallout from its September 2023 breach, which disrupted Las Vegas hotel and casino systems and exposed data of about 37 million people. The company refused to pay ransom, restored operations within a week, and later agreed to a 45 million dollar class-action settlement in January 2025.
Slovakia’s Land Registry suffered a major ransomware attack in January 2025 that froze national property transactions, mortgages, and local services for weeks. The government declined to pay millions of euros in ransom, rebuilt from backups, and confirmed that records remained intact.
Kuala Lumpur International Airport was crippled on March 23, 2025, as flight systems and baggage handling went offline for over 10 hours. Malaysia’s Prime Minister rejected a 10 million dollar ransom demand linked to the Qilin gang. Though systems were restored, the attack exposed major aviation security gaps.
DaVita Healthcare disclosed an April 2025 breach after the Interlock group stole about 20 terabytes of sensitive patient and financial data affecting 2.7 million people. Dialysis operations continued, but the company incurred 13.5 million dollars in Q2 costs and saw stolen data leaked online.
Poland’s Big Cheese Studio was attacked on January 24, 2025, with hackers stealing source code and employee data and demanding $25,000 in cryptocurrency. The breach forced the website offline and caused a 7% share drop before recovery efforts began.
These incidents highlight ransomware’s continued reach across healthcare, government, aviation, and entertainment. Financial losses varied, but the operational damage and reputational harm remained severe across all sectors.
How Bright Defense Protects You from Ransomware?
Bright Defense protects organizations against ransomware through a mix of prevention, response, and recovery measures. Its monitoring systems detect suspicious activity before encryption begins, while its engineers apply secure configurations and patch management to close known weaknesses.
When an attack occurs, Bright Defense teams contain the incident quickly, isolate infected systems, and guide safe data restoration from verified backups. Employee training programs strengthen awareness against phishing and social engineering threats that often lead to ransomware infections. After recovery, detailed reviews pinpoint how the attack entered and recommend stronger controls to prevent a repeat event.
Through these steps, Bright Defense helps maintain operational continuity and protect critical data from disruption. Contact Bright Defense now, to strengthen your defenses and keep ransomware from threatening your organization.
FAQs
In 2025, ransomware remains one of the most common forms of cyberattack. About one in five reported cyberattacks are ransomware incidents. On average, over a million attempted ransomware attacks occur each day worldwide.
Median ransom demands hover around 1.3 million dollars, while the average ransom payment is close to 1 million. Recovery costs for affected organizations average about 1.5 million dollars, and the global cost per ransomware or extortion incident is estimated above 5 million.
Roughly half of successful attacks result in data encryption, and nearly a third involve data theft. Law enforcement agencies in multiple countries continue to pressure ransomware groups while also warning small businesses and government facilities about growing threats.
The 3-2-1 backup rule is a simple guideline for protecting data:
– Keep 3 copies of your data
– Store those copies on 2 different types of media
– Make sure 1 copy is kept off-site or in the cloud
This approach helps protect organizations against ransomware threats, system failures, or natural disasters so that data recovery remains possible even when all their data seems at risk.
Ransomware makes up about 20 to 25% of reported cyber incidents globally. That means roughly one out of every four attacks involves ransomware victims across industries, including healthcare and the manufacturing industry.
– Median ransom demand: About 1.3 million USD
– Average ransom payment: Roughly 1 million USD
– Average recovery cost: Around 1.5 million USD (not including ransom)
– Average overall incident cost: Over 5 million USD when business disruption and reputational damage are included
Yes, ransomware activity is still increasing. The number of variants and ransomware groups behind attacks continues to grow, and some quarters in 2025 saw more than double the number of organizations listed on extortion sites compared to the previous year. At the same time, ransom payments and average payments have slightly decreased, showing that threat actors are adjusting methods to increase pressure on victims.
Security labs track more than 1.2 billion known malicious software programs worldwide. Every day, over 450,000 new malware samples are detected. Malware creation and distribution remain constant at a massive scale, which continues to affect company operations and brand damage when attackers succeed.
The most widely recognized categories are:
1. Virus – attaches to files and spreads when the file is run.
2. Worm – self-replicates and spreads without user action.
3. Trojan – disguises itself as legitimate software.
4. Ransomware – encrypts files and demands payment.
5. Spyware – secretly monitors activity and steals information.
6. Adware – floods devices with unwanted ads.
7. Botnet malware – turns devices into remotely controlled bots.
On average, 200,000 new malware variants appear every day. In a single year, more than 100 million new malware strains are recorded. Malware accounted for billions of attempted attacks globally in recent years, affecting both individuals and organizations. Criminals increasingly use phishing and malicious attachments as delivery channels.
Yes. A Trojan horse is a type of malware. It tricks users into installing it by posing as a safe or useful program, then allows attackers to steal intellectual property, spy, or gain control over a system.
Yes. Microsoft Defender, included in Windows 10 and Windows 11, can detect, quarantine, and remove Trojan malware. It scans for malicious signatures and suspicious behaviors, and can perform offline scans for deeper threats.
In cybersecurity, Trojans are not “made” by a single source. They are created by cybercriminals, hacker groups, or even state-sponsored actors. Attackers design Trojans to look like legitimate programs and distribute them through phishing emails, malicious websites, cracked software, or infected attachments. Unlike commercial software, Trojans are illegal and usually spread anonymously on underground forums or dark web markets.
Get In Touch



