
Who Needs SOC 2 Compliance?
Data is the most valuable currency online, which makes a breach a reputation killer. While regulations like GDPR and HIPAA are mandated by law, SOC 2 is a voluntary commitment that tells customers and business partners: “We take security seriously, and we can prove it.”
That proof matters more than ever as third parties play a growing role in security incidents and related security risks. Recent research shows that breaches involving third parties have doubled to 30%, which is why vendor management and vendor due diligence have become a standard part of risk management.
SOC 2 gives buyers the audit-backed evidence they need to trust your service organization’s controls, not just your promises. Whether you’re an MSP, a fintech innovator, or a healthcare tech provider, demonstrating that your internal controls are verified is how you build a lasting brand and competitive advantage.
Next, let’s look at who really needs SOC 2 and whether you fall in that particular category.
Key Takeaways
- SOC 2 is a voluntary audit report that proves your security controls work
- Buyers use SOC 2 to speed up vendor reviews and cut questionnaires
- SOC 2 matters more now since third-party breaches hit 30%
- SaaS, MSPs, fintech, healthcare, data centers, HR, e-commerce, and AI vendors feel the most pressure
- You need SOC 2 when customers ask for proof and you handle sensitive data
What Is SOC 2 Compliance and Why It Matters for Organizations?
SOC 2 is an independent audit report with a defined audit process that checks whether a SaaS company has effective controls for data processing and protecting customer data, especially when teams manage client data across core system processing workflows. It’s measured against the american institute of certified public accountants (AICPA) selected trust services criteria, often summarized as the five trust services criteria:
- Security
- Availability
- Processing Integrity
- Confidentiality
- Privacy
SOC 2 matters for organizations because enterprise buyers want proof, not promises. SOC 2 is one of the fastest ways security and procurement teams compare vendors and assess security posture.
A SOC 2 report gives auditor-tested evidence and supporting compliance documentation, which can shorten security reviews and cut down on repeated questionnaires.
SOC 2 also reflects modern vendor-risk pressure. The Verizon 2025 DBIR executive summary reports that third-party involvement in breaches increased from 15% to 30%, so buyers increasingly treat SaaS vendors and other service providers as part of the ways attackers can reach their systems and data.
In practical terms, SOC 2 forces teams to define scope, document how work gets done, and produce repeatable evidence across engineering, IT, and support. That builds customer trust and reduces risk as the company grows.
Key Statistics on Why More Buyers Now Expect SOC 2
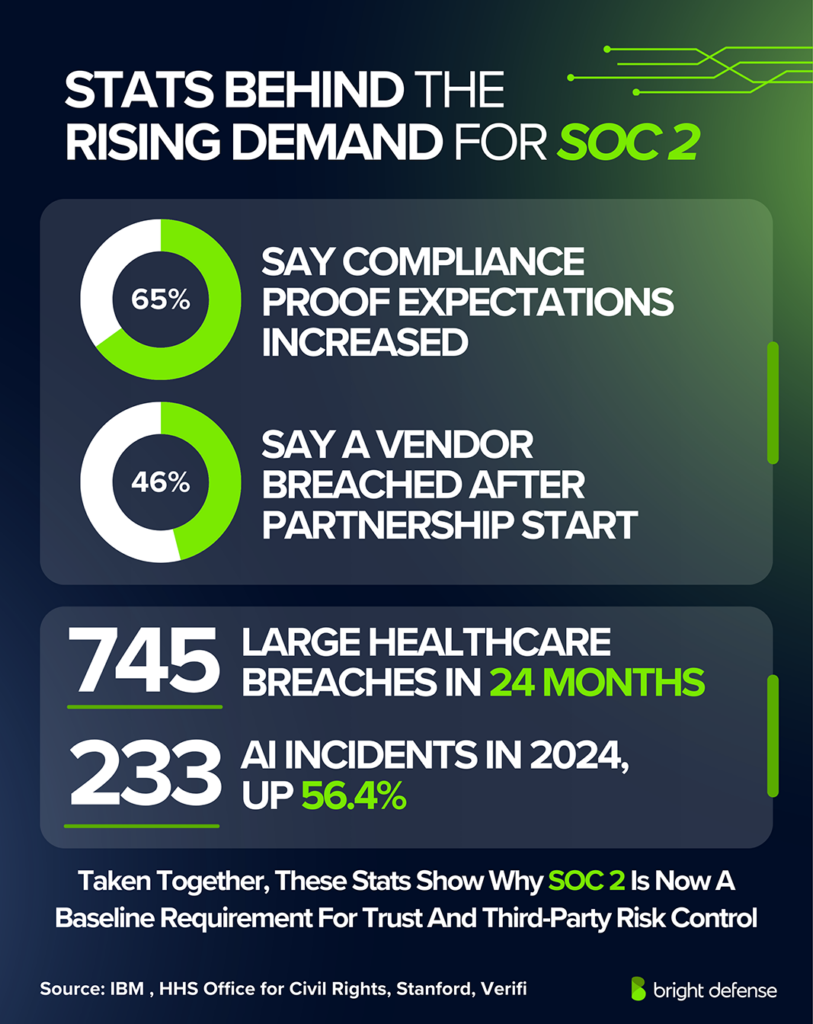
- 65% of business and IT leaders say stakeholders expect more proof of compliance This drives SOC 2 requests during procurement since it offers third-party assurance
- 46% say a vendor had a breach after the partnership began This pushes buyers to demand evidence of mature controls at vendors, not promises
- 47% reported a breach or cyberattack tied to a third party with network access in the past 12 months This puts a spotlight on vendor access controls, monitoring, and incident response
- $6.08M average data breach cost in financial services, 22% above the $4.88M global average Higher impact increases pressure for audited security and data-handling controls
Which Industries and Organizations Need SOC 2 Compliance?
SOC 2 helps organizations prove strong security controls and build trust with customers, partners, and investors.
The industries below face the most pressure to meet SOC 2 requirements, especially during procurement, onboarding, and renewals:

1. SaaS Companies and Cloud Service Providers
65% of business and IT leaders say customers, investors, and suppliers now expect more proof of compliance than in the past, which is why SaaS platforms and cloud providers, including cloud computing companies, face heavier scrutiny across customer data, financial records, and financial data tied to sensitive workflows.
Since buyers treat these products as part of their operating backbone, SOC 2 has become a common vendor requirement in enterprise deals because it gives internal teams third-party assurance they can rely on during procurement and risk reviews.
2. Managed Service Providers (MSPs)
46% of organizations say a vendor experienced a data breach after the partnership began, and that statistic hangs over MSP evaluations from day 1. MSPs often operate with admin-level data access, handle security updates, and keep business-critical systems running across many customers.
With that level of reach, buyers focus heavily on trust and control maturity because a single incident at the provider can ripple through multiple client environments. SOC 2 helps MSPs show that access, change management, incident response plans, and operational oversight follow consistent, disciplined processes.
3. Data Centers and Colocation Providers
55%of data center operators reported an outage in the past 3 years, and 54% said their most recent serious outage cost more than $100,000. With numbers like that, customers expect clear evidence that physical and logical access controls, monitoring, and incident response operate reliably, especially when a facility supports regulated or high-value workloads.
Data center operators host everything from intellectual property to production systems and customer records, so even short disruptions can create real downstream impact. Most of these incidents are also avoidable, with 4 in 5 operators saying their last serious outage could have been prevented with stronger management, tighter process discipline, or better configuration.
4. Financial Services, Fintech, and Payments
Financial services providers process transactions, maintain detailed customer records, and operate across complex ecosystems of vendors, partners, and internal platforms, where even small control gaps can create serious downstream exposure. The financial impact is also significant: financial services organizations in the financial industry average $6.08M per data breach, which is 22% higher than the $4.88M global average.
For that reason, buyers and partners often request SOC 2 during vendor risk reviews since it provides a clear, focused view of security and data-handling controls across the systems used to process and protect customer data, including controls tied to financial reporting.
5. Healthcare Service Providers and Healthtech Vendors
Healthcare organizations and digital health vendors handle highly sensitive information and connect to hospital and insurance ecosystems. The stakes are high, with 745 large healthcare breaches (500+ individuals) reported in the last 24 months that are still under investigation, according to the HHS OCR breach portal.
Even when HIPAA applies, customers still ask for SOC 2 to gain additional assurance about how systems and operational controls work in day-to-day reality, especially for vendors selling into enterprise healthcare.
6. Insurance and Claims Organizations
For insurers, brokers, and claims platforms, third-party exposure is a constant concern because underwriting and claims workflows rely on identity data, financial information, and sometimes health-related details. That risk is not theoretical: 47% of organizations reported a breach or cyberattack in the past 12 months that involved a third party with network access, according.
Insurance operations also depend heavily on claims software, customer portals, and outsourced processing partners, which means the control surface often extends far beyond internal systems. As a result, SOC 2 often becomes a key factor in vendor reviews because it offers a structured view of how security and data-handling controls are governed, including risk mitigation strategies in environments that manage regulated or high-impact data.
7. HR, Payroll, and Benefits Platforms
HRIS, payroll, and benefits vendors handle highly sensitive employee data, including PII, compensation details, and bank information. They also routinely pass that data between interconnected providers, which increases exposure. That risk shows up in real-world reporting: 20,044 “Employment” complaints were filed in 2024.
With attackers increasingly targeting HR and payroll workflows for fraud, buyers want proof that security controls remain consistent, even when multiple systems and third-party vendors connect behind the scenes. SOC 2 helps these organizations demonstrate disciplined access controls, secure data handling, and dependable operational processes that support confidentiality and privacy expectations from both customers and partners.
8. Marketing, AdTech, and Customer Data Platforms
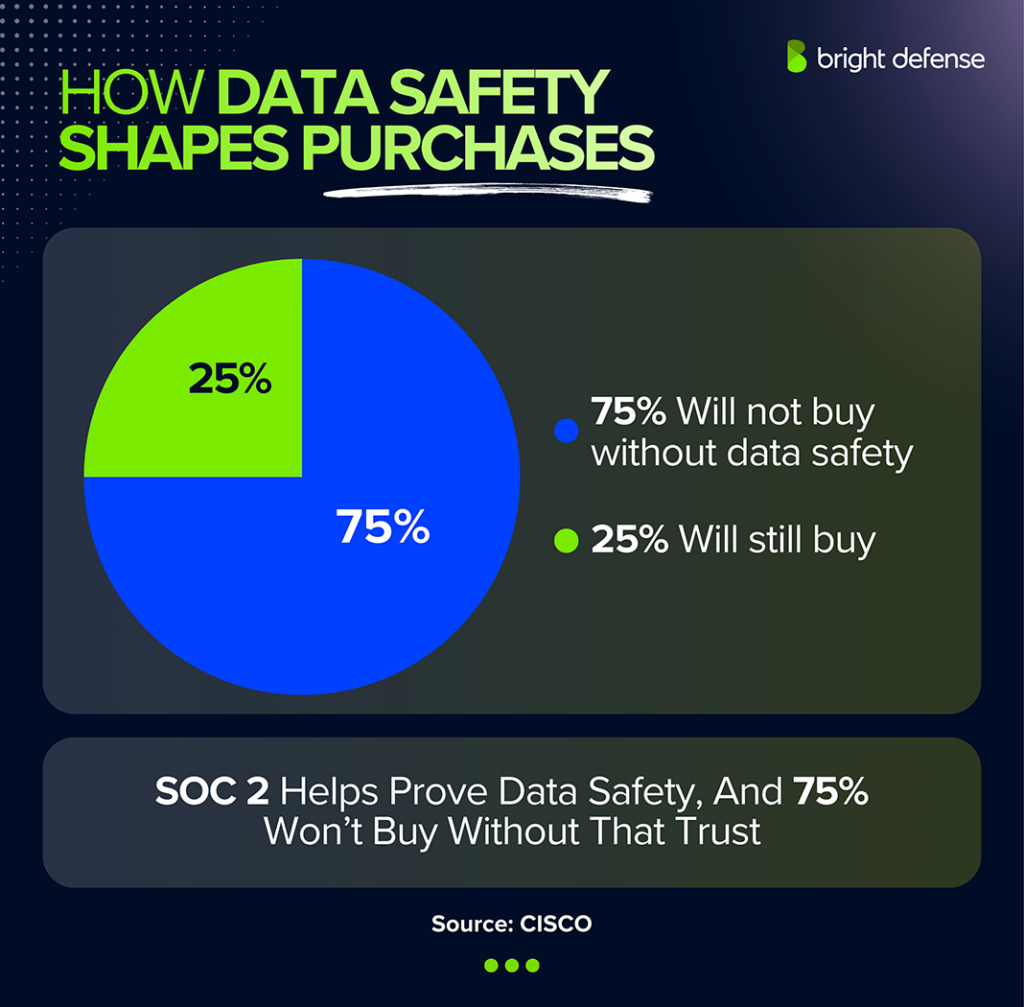
Customer data platforms, analytics tags, and marketing automation tools often collect large volumes of personal data and behavioral signals, and that trust breaks quickly when customers feel their information isn’t protected.
In fact, 75% of consumers say they will not buy from an organization they do not trust with their data. Because these vendors sit in the middle of identity, tracking, segmentation, and data activation workflows, buyers often request SOC 2 to confirm there are clear controls around access, data handling, retention, and incident response when sensitive customer information moves through the system at scale.
9. E-commerce Platforms and Marketplaces
E-commerce and marketplace providers hold customer accounts, order history, returns data, and sometimes payment-related information through integrations. Fraud pressure is constant, and merchants reportedly lose about 3% of annual e-commerce revenue to payment fraud.
SOC 2 helps when enterprise merchants want assurance around access control, change management, uptime practices, and incident response for systems that support revenue operations. (Verifi 2024 survey)
10. AI Platform Providers
Data warehouses, ETL providers, BI platforms, and AI tooling can process customer datasets at scale, sometimes across multiple tenants. Threats are growing fast, and Stanford HAI tracked 233 AI-related incidents in 2024, up 56.4%from 2023. SOC 2 often comes up when customers need proof of access boundaries, auditability, and operational discipline across systems that process their data. (Stanford AI Index Report)
The Real Numbers Behind Growing SOC 2 Pressure
- 745 large healthcare breaches in the last 24 months (500+ people)
High breach volume increases scrutiny for vendors that touch sensitive data - 55% of data centers had an outage in the past 3 years, and 54% of serious outages cost >$100,000
Availability risk makes SOC 2 important for proving reliability and operational discipline - 75% of consumers will not buy if they do not trust data handling
Trust affects revenue, so vendors use SOC 2 to reduce sales friction
Signs Your Organization Needs SOC 2 Compliance
If customers, partners, or regulators are asking for formal proof that your security and data handling practices maintain compliance with recognized standards, it is a strong sign you need SOC 2.
Below is a detailed list of indicators that suggest your organization should pursue SOC 2 compliance:

1. Customers Start Asking For A SOC 2 Report During Procurement
If deals increasingly include security reviews, SOC 2 usually becomes the fastest way to answer “show me proof” questions. 2,500 business and IT leaders, 65% said customers, investors, and suppliers require more proof of compliance than before, which explains why SOC 2 often shows up early in procurement.
Many teams share third-party audit reports and also complete security questionnaires as part of due diligence, so a SOC 2 report can reduce back-and-forth during these requests.
2. You Handle Sensitive Customer Data Or Personal Information
SOC 2 fits organizations that store or process customer data, especially when that data includes personal information or confidential information you must protect data from improper access or disclosure. IBM reports 46% of breaches involved customer personal data, which is why buyers care about how data is collected, stored, accessed, and logged.
The Trust Services Criteria cover confidentiality and privacy alongside security and operational controls, so SOC 2 becomes a natural expectation once your product or service acts as a system of record for customers.
3. Your Service Is Critical to Customer Operations
When customers depend on your uptime, accurate processing, or consistent outcomes, SOC 2 becomes more than a checkbox. Availability and processing integrity are part of what a SOC 2 report can address, which makes it relevant for SaaS platforms, cloud services, payment flows, and managed operations that sit inside customer business operations.
This also connects to incident reality: IBM’s 2024 Cost of a Data Breach Report puts the global average breach cost at $4.88M, with a mean time to detect and contain of 258 days, which is difficult to manage with informal SOC 2 controls.
4. Third-Party Risk Is Becoming Part Of Every Customer Conversation
If your product relies on sub-processors, cloud providers, or outside operational support, buyers will look at your vendor oversight as part of their own risk posture. Verizon’s 2025 DBIR release reports that third-party involvement in breaches doubled to 30%, which increases pressure on vendors to show mature control operation and evidence.
That pressure also shows up in buyer behavior: IT decision makers spend 6.5 hours per week on vendor risk review, 46% reported a vendor breach during the relationship, and 62% said third-party breaches harm reputation. (Business Wire) (Verizon)
5. Security Questionnaires Keep Piling Up
If your team spends a lot of time answering questionnaires or RFP security sections, SOC 2 can help standardize the story and provide auditor-tested evidence as part of ongoing compliance efforts.
Customers save 35 hours per month on security questionnaires once they have a formal trust package, which is a practical signal that this work becomes a serious operational tax without SOC 2-style artifacts.
Vanta’s 2024 survey also found teams spend 11 weeks per year on manual security compliance tasks, reinforcing how quickly ad hoc work can consume bandwidth. (Business Wire) (Secureframe)
6. You Are Moving Upmarket Into Enterprise Accounts
Enterprise buyers tend to expect formal assurance artifacts. SOC 2 is often requested as a standard trust document, and vendors commonly pursue it to support larger accounts and more demanding security reviews with enterprise clients.

How to Prepare for a SOC 2 Audit
SOC 2 prep starts with understanding what auditors will evaluate across security, availability, processing integrity, confidentiality, and privacy.
Below are the core steps that help teams get audit-ready without confusion:

1. Pick The Right Report Type and Timeline Early
Start with Type 1 if you need a point-in-time report on control design. Plan for Type 2 when customers want proof that controls operated effectively over time.
A SOC 2 Type 2 timeline commonly requires at least a 3-month observation window, with longer timelines possible depending on scope.
2. Define The Audit Scope and The “System”
SOC 2 applies to a clearly defined system, not your entire company. Start by documenting exactly what sits in scope, including the product, supporting infrastructure, key internal tools, the processes that support delivery, and the people responsible for operating and maintaining them.
Getting scope right early matters because it determines which controls you need, how much evidence you must collect, and how much time and effort the audit will take. A well-defined scope also helps prevent surprises later, such as auditors requesting evidence for systems or teams you did not intend to include.
3. Choose the Trust Services Criteria That Match Customer Expectations
Security is the baseline for most SaaS SOC 2 audits, and the other criteria depend on what you promise customers. The AICPA describes SOC 2 as covering controls relevant to security, availability, processing integrity, confidentiality, or privacy.
Select criteria that match real product commitments, contract language, and buyer concerns, including core security criteria, or you risk extra work with little sales value.
4. Run A Readiness Assessment, Then A Gap Analysis
A readiness assessment gives you a reality check before the audit starts. It helps confirm which Trust Services Criteria (TSC) apply, then moves into a gap analysis that compares your current controls to those criteria and clarifies what needs to change.
Treat this as a planning phase that ends with a concrete remediation plan, clear owners, and target dates for closing control gaps or implementing missing controls, backed by documented compliance processes.
5. Put Evidence on a Schedule That Matches the Audit Window
Type 2 success depends on repeatable evidence. If a control runs weekly or monthly, evidence needs coverage for each week or month in the Type 2 window, and quarterly controls need updated evidence each quarter.
This is where teams stumble: controls exist, but the proof is missing or inconsistent. Set a calendar for evidence production and reviews, then keep artifacts organized in a single place.
6. Get the Auditor’s Data Request List and Map It to Owners
Most auditors provide a data request list that spells out the evidence and documentation they expect for the SOC framework and scope. It functions as a detailed checklist for the evidence, documentation, and data needed to complete the assessment.
Map each request to an internal owner early, then track progress weekly so nothing piles up at the end, including tickets, logs, and security policies.
7. Prep Your Team for Walkthroughs and Sampling
Auditors will validate how controls work in practice, not just on paper. Once you provide the requested information, the auditor reviews evidence for each in-scope control, verifies details, schedules walkthroughs, and then produces the final report.
Prep control owners for walkthroughs, keep narratives consistent with evidence, and confirm the same story shows up across tickets, logs, and policy references.
8. Keep Controls Operating Through the Entire Period
SOC 2 is not a one-time push. Ongoing control monitoring and maintenance needs to remain a core part of the program, not something you revisit only during audit season. If controls become “audit-only work,” the evidence trail breaks and Type 2 gets painful fast.
The fix is treating security as daily operations, backed by a consistent framework, continuous monitoring, and baseline safeguards such as multi factor authentication, data encryption, and employee training. These foundations support day-to-day information security practices and long-term operational effectiveness.
Final Thoughts
Ultimately, SOC 2 compliance is more than just a technical hurdle or a “check-the-box” requirement for your legal department. It serves as a foundational seal of trust in an increasingly data-conscious market.
While the process requires an investment of time and resources, the return is a strengthened security posture and a significant competitive advantage. For any organization handling data in the cloud, SOC 2 isn’t just about proving you are secure. It’s about proving you are a reliable partner worthy of your customers’ most sensitive information.
Bright Defense Offers SOC 2 Services
Bright Defense helps organizations prepare for SOC 2 audits with a clear, audit focused approach. We support SOC 2 readiness assessments, gap analysis, and control design across security, availability, and confidentiality.
Our team helps document policies, implement controls, and build strong audit evidence so the engagement stays practical and focused. Whether you are targeting SOC 2 Type I or Type II, Bright Defense helps reduce audit friction and improve confidence ahead of assessment timelines.
FAQ
Service organizations that store, process, or support customer data for other businesses commonly need SOC 2 because the report is designed to give users detailed assurance about controls tied to those services and systems.
No. SaaS companies are a common group, but SOC 2 can also apply to cloud providers, managed service providers, data processors, and other service organizations that support customer systems or information.
Probably not in most cases. Companies that do not provide outsourced services to other organizations and do not face customer assurance requests often have less need for a SOC 2 report.
Clients, prospects, procurement teams, and vendor risk reviewers commonly ask for SOC 2 reports when they need proof that a vendor’s controls were reviewed by an independent auditor.
No. SOC 2 scope depends on the services provided and the criteria selected, although the framework covers security, availability, processing integrity, confidentiality, and privacy.
It depends on your customers. If enterprise prospects are asking for security reviews or a SOC 2 report during sales, it becomes a practical requirement much earlier, even for a small team.
Start with scope and readiness planning, then confirm whether the customer can accept a timeline, a Type I report first, or other interim evidence while you work toward a full report. Only a CPA firm can issue the final SOC 2 audit report.
Ask for it when the vendor will handle sensitive data, support critical systems, or provide an outsourced service that creates operational or data risk for your organization. SOC reports are used to help assess risks tied to outsourcing services.
No company is universally required by law to have SOC 2. In practice, SOC 2 is mainly expected for service organizations that store, process, or transmit customer data, especially when customers or partners ask for a SOC 2 report during vendor reviews.
No, SOC 2 is generally not a legal requirement. It is commonly a contractual or customer requirement, especially for SaaS, cloud, and other data-handling vendors.
The five SOC 2 Trust Services Criteria are Security, Availability, Processing Integrity, Confidentiality, and Privacy.
Get In Touch



