
200+ Phishing Statistics for 2026
The Bright Defense team has gathered 187 up-to-date phishing statistics for 2025. This article brings together the most recent data on how phishing continues to shape cybersecurity incidents across industries and regions.
Drawing from trusted sources such as the FBI, Homeland Security, Verizon, BlackBerry, Sophos, Arctic Wolf, and Check Point Research, the dataset reflects the most current and credible findings available.
You’ll find information covering:
- Global phishing trends and yearly changes
- Sector-specific phishing activity
- Financial and operational impact of phishing attacks
- Methods and success rates of phishing campaigns
- Regional data across North America, Europe, Asia, Africa, Australia, and South America
Let’s examine the key numbers.
General Phishing Statistics

- Phishing was the most reported cybercrime in 2024, with 193,407 complaints representing 22.5% of all internet crimes and $70 million in losses. (FBI IC3 2024)
- Phishing losses quadrupled compared with 2023. (FBI IC3 2024)
- Phishing attacks increased 13% year over year and remained the most common initial attack vector in 2024. (Check Point Research)
- 36% of organizations experienced at least one successful phishing attack. (Check Point Research)
- 72% of organizations experienced at least one phishing attack in 2024. (Cybersecurity Foundation & Gruppo Tim)
- 49% of companies faced at least one cyberattack in the past year, with phishing among the top causes. (Cisco Cybersecurity Readiness Index)
- 68% of breaches involved a human element that includes phishing, stolen credentials, or social engineering. (Verizon DBIR 2025)
- 32% of all breaches included a phishing component. (Verizon DBIR 2025)
- The average organizational cost per phishing incident reached 1.14 million dollars. (Check Point Research)
- The average breach cost for phishing-driven incidents was 1.29 million dollars, up 12% from 2023. (Verizon DBIR 2025)
- Employee awareness training reduced phishing simulation click-through rates 32% compared with untrained staff. (Check Point Research)
- Click rates on phishing simulations were 38% lower among trained employees. (Verizon DBIR 2025)
- The average phishing email click rate was 2.7%. Median time to click was 21 seconds. Median time to report was 28 minutes. (Verizon DBIR 2025)
- 82% of organizations increased email security budgets or training to counter phishing. (Check Point Research)
- 29% of organizations did not track phishing metrics despite having email protection tools. (Verizon DBIR 2025)
- 56.56% of November 2024 phishing was spearphishing. (OpenText Cybersecurity Threat Report)
- 3,938 phishing cases involved cryptocurrency schemes, causing $28.5 million in losses. (FBI IC3 2024)
- Total phishing websites detected: >80,000 (up 22% from previous year) (Group IB)
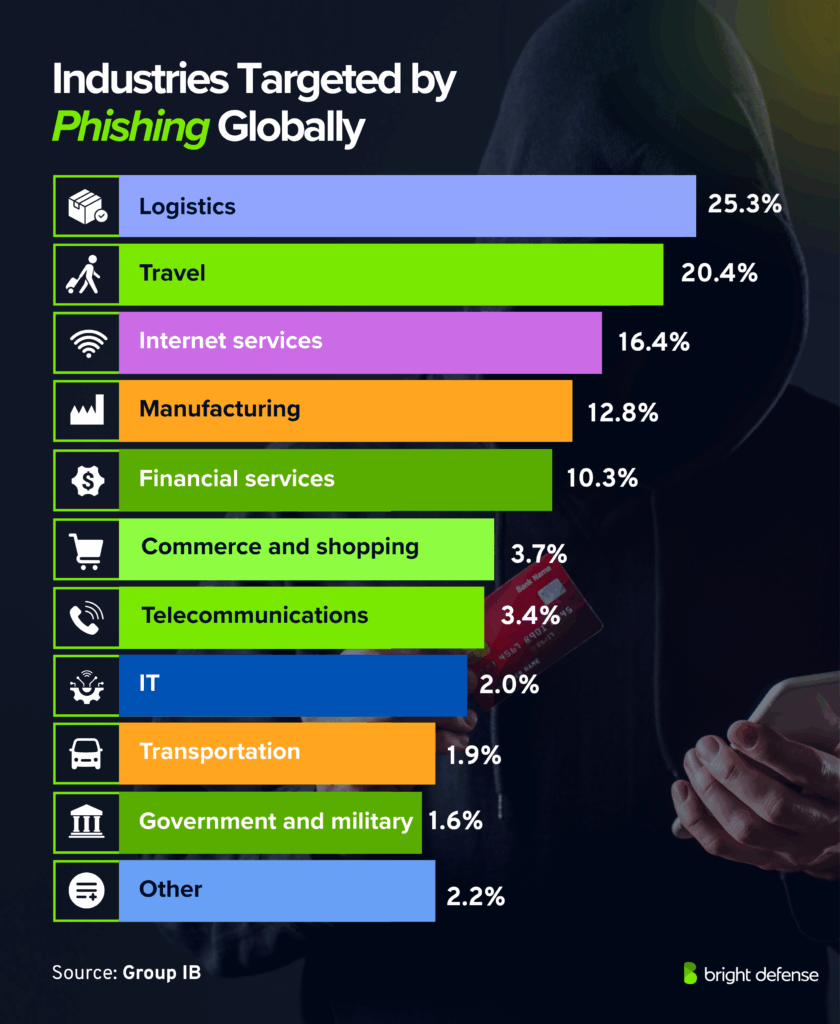
- Top industries targeted globally:
- Logistics 25.3%
- Travel 20.4%
- Internet services 16.4%
- Manufacturing 12.8%
- Financial services 10.3%
- Commerce and shopping 3.7%
- Telecommunications 3.4%
- IT 2.0%
- Transportation 1.9%
- Government and military 1.6% (Group IB)
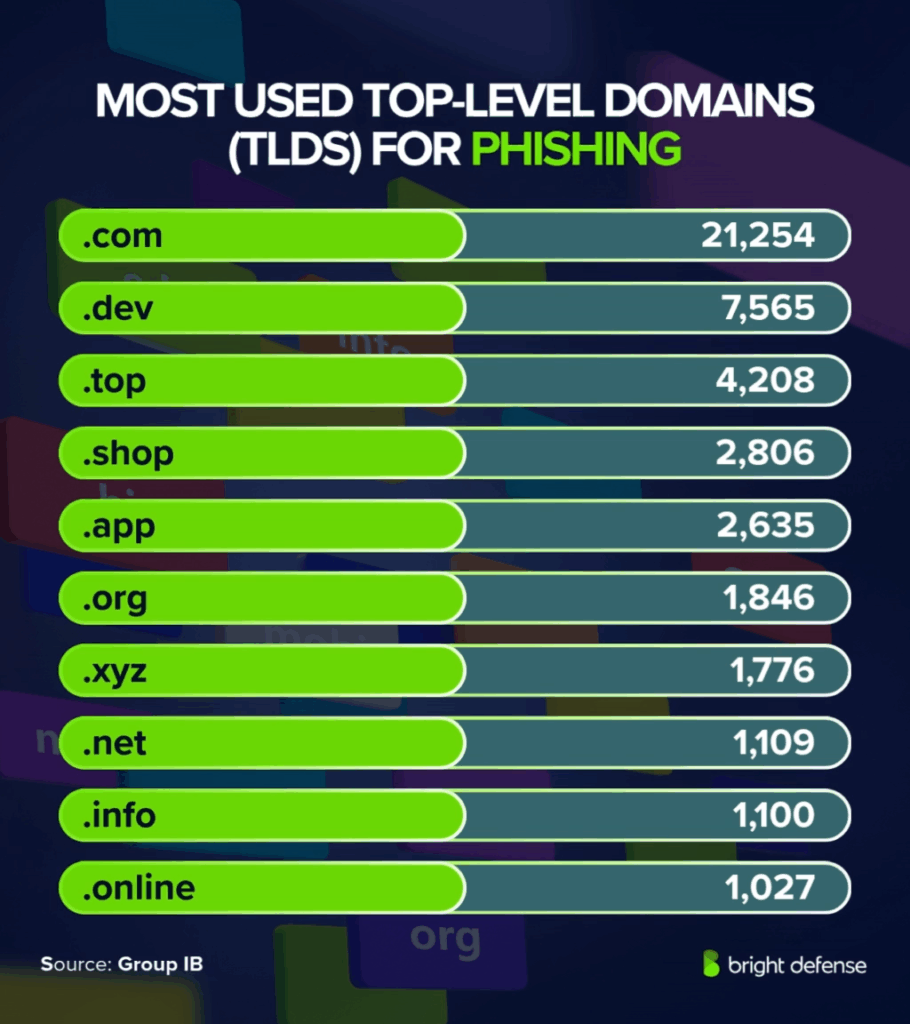
- Most used top-level domains (TLDs) for phishing:
- .com 21,254
- .dev 7,565
- .top 4,208
- .shop 2,806
- .app 2,635
- .org 1,846
- .xyz 1,776
- .net 1,109
- .info 1,100
- .online 1,027 (Group IB)
- Phishing (T1566) ranked among the most used attack techniques in 2024:
- Spearphishing Attachment 20.5%
- General Phishing 19.4%
- Spearphishing Link 14.5% (Group IB)
- Phishing activity has risen 49% since 2021, largely due to the use of AI-generated phishing messages. (Vipre)
- Phishing accounted for 22% of all spam emails detected during the quarter, maintaining its position as one of the top categories of email-based threats. (Vipre)
- The most spoofed brand remained Microsoft, appearing in nearly 900 phishing incidents. Apple ranked second, followed by DocuSign, marking the same top three as in 2023. Financial institutions such as PayPal, HSBC, and BankID also appeared frequently. (Vipre)
- VIPRE, a global email security provider, scanned 1.8 billion emails in Q2 2024, detecting 226.45 million spam messages, which accounted for 13% of total email traffic. (Vipre)
- The United States was the top phishing target in Q2 2024, receiving 46% of all attempts, followed by Great Britain (16%), Sweden (13%), Canada (10%), Iceland (7%), Denmark (4%), and Ireland (3%). (Vipre)
- The most used top-level domains for phishing were .com, .org, and .uk. (Vipre)
- 86% of malicious spam (malspam) emails used links instead of attachments, a reversal from the prior quarter’s 78% attachment rate. (Vipre)
- The most common malicious attachment types were ZIP (62%), DOCM/DOCX (16%), HTML (12%), and XLSX (10%). (Vipre)
- 68.6% of recorded intrusions resulted in data breaches that were later leaked or sold on criminal forums. (Enisa Threat Landscape 2025)
- 2.8% of advertised breaches were explicitly presented as the direct outcome of a ransomware attack. (Enisa Threat Landscape 2025)
- Data-exfiltration outcomes broke down as 8.9% credential theft and 21.3% strategic data collection, together accounting for 30.2% of recorded intrusions. (Enisa Threat Landscape 2025)
Want to learn about other types of cybercrimes? Explore our verified list of 256 updated Cybercrime Stats for a clear overview of various cybercrimes.

AI-Driven Phishing Trends

- AI-generated phishing accelerated in 2025, with election-themed spear phishing noted as a key threat. (Homeland Threat Assessment 2025)
- 40% of Business Email Compromise (BEC) emails in Q2 were AI-generated, as confirmed by multiple AI text detection tools. (Vipre)
- The use of AI has improved the sophistication of phishing and BEC messages, reducing grammatical and structural cues that traditionally signaled fraud. (Vipre)
- AI-generated phishing rose significantly, producing more authentic language and evading traditional spam filters. (Check Point Research)
- Generative AI phishing content increased 22%. (Verizon DBIR 2025)
- AI-generated phishing emails increased 24%. (Cybersecurity Foundation & Gruppo Tim)
- 86% of organizations reported at least one AI-related incident that included AI-powered phishing or social engineering. (Cisco Cybersecurity Readiness Index)
- AI-aided social engineering incidents impacted 42 % of organizations. (Cisco Cybersecurity Readiness Index)
- Only 48% of employees understand how threat actors use AI for phishing. (Cisco Cybersecurity Readiness Index)
- Identity-based attacks were 60 % of phishing incidents, many linked to AI-powered phishing. (Cisco Cybersecurity Readiness Index)
- AI-powered phishing and deepfakes listed as the main identity threat vector in 2025. (Cisco Cybersecurity Readiness Index)
- Thousands of emails in early 2025 showed a sharp rise in AI-assisted message construction, with stronger brand impersonation and realism. (Red Canary Threat Detection Report)
- Threat actors used AI to generate large-scale, more convincing lures. (Flashpoint Global Threat Intelligence Report)
Advanced Phishing Tactics and Tooling
- Nearly one in four campaigns used QR codes or malicious links disguised as MFA prompts. (Check Point Research)
- A surge in PDF-based phishing was linked to Microsoft’s macro-blocking policy, with all observed PDFs containing QR phishing (quishing) attempts. (Vipre)
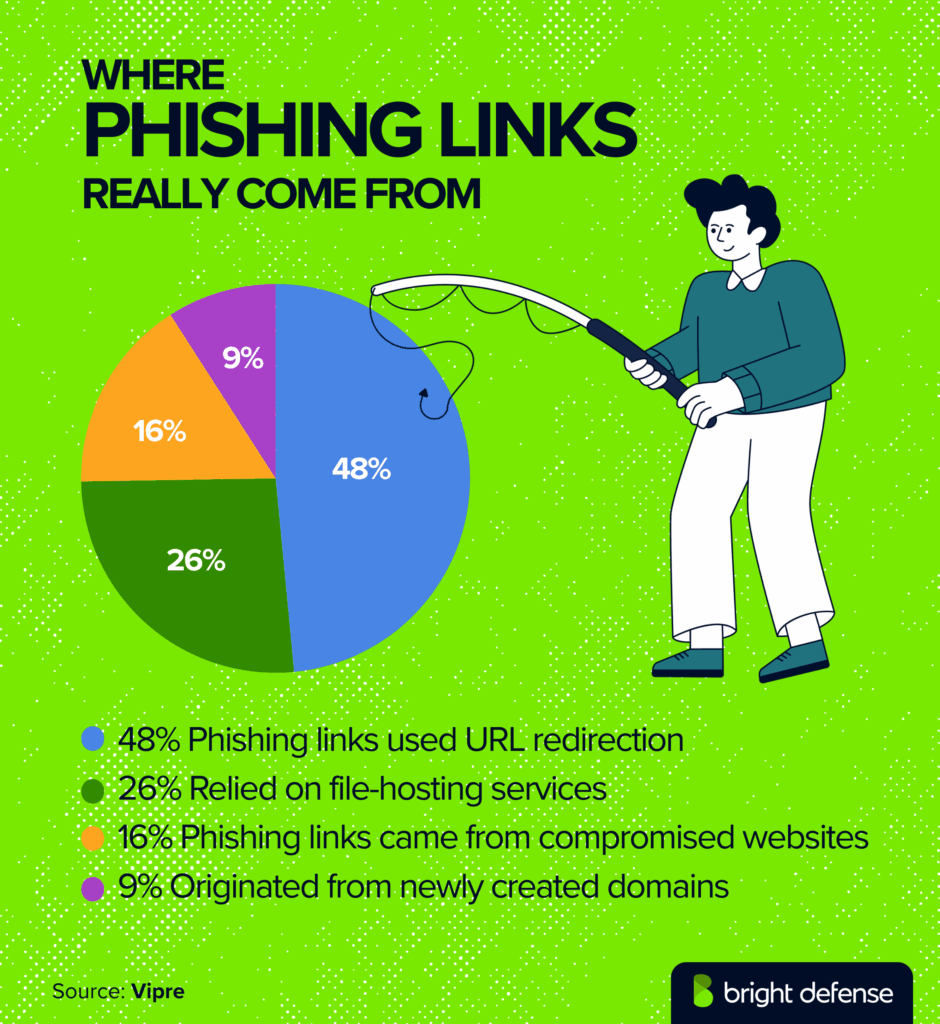
- URL Redirection was the most common tactic, used in 48% of phishing links (up from 39% a year earlier). (Vipre)
- File-hosting services were used in 26% of phishing links, a sharp rise from just 6% in the previous quarter. (Vipre)
- Compromised websites accounted for 16%, while newly created domains represented 9% of all phishing URLs. (Vipre)
- MFA phishing kits appeared in 15% of credential-harvesting cases. (Verizon DBIR 2025)
- 43% of campaigns used legitimate cloud service links to bypass filters. (Verizon DBIR 2025)
- Attackers hid malicious URLs behind Google Translate’s domain rewrite and used URL shorteners or trusted hosts for open-redirect credential harvesting. (Red Canary Threat Detection Report)
- Paste-and-run fake CAPTCHA lures and malicious copy-and-paste attacks grew quickly. (Red Canary Threat Detection Report)
- PhaaS (Phishing-as-a-Service) platforms grew 21%, lowering the bar for large-scale phishing. (Cybersecurity Foundation & Gruppo Tim)
- AI-driven domain spoofing and automated content generation were key drivers of phishing volume. (BlackBerry Global Threat Intelligence Report)
- Abuse of List-Manage Mailchimp, Canva, Cloudflare IPFS, and Google Docs with 2+ million occurrences. (OpenText Cybersecurity Threat Report)
- Multilingual lures mixing English and non-English to slip past language filters. (Red Canary Threat Detection Report)
- Deepfake phishing and voice cloning in 7% of incidents. (BlackBerry Global Threat Intelligence Report)
Phishing Detection, Exposure, and Outlook
- Email gateway filtering accuracy improved 14 %, yet zero-day phishing URLs bypassed in 11% of cases. (Check Point Research)
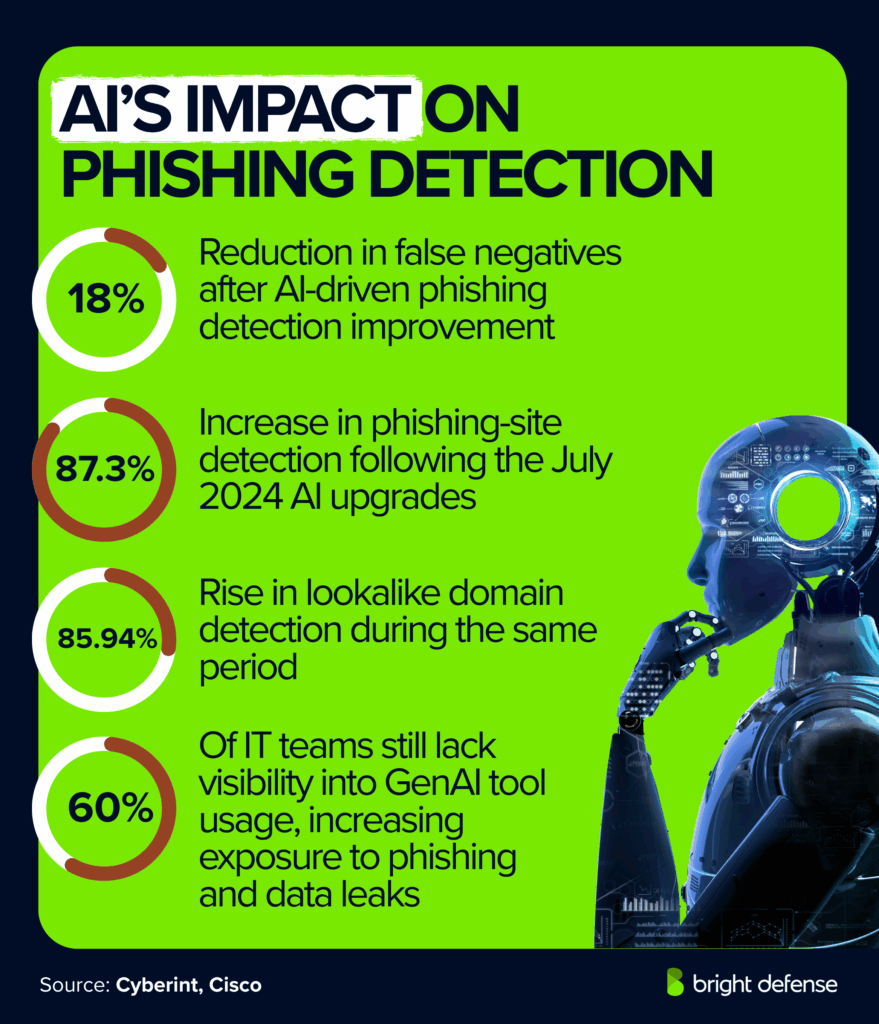
- AI-driven phishing detection cut false negatives 18 %, though 9 %of malicious messages still slipped through. (Verizon DBIR 2025)
- Enterprises increasingly used AI and machine learning to spot phishing-related identity anomalies. (Red Canary Threat Detection Report)
- 60% of IT teams lack visibility into GenAI tool use, which raises exposure to phishing and data leaks. (Cisco Cybersecurity Readiness Index)
- 71% expect a business-disrupting cyber incident within 12 to 24 months, with phishing and AI-driven threats cited as major factors. (Cisco Cybersecurity Readiness Index)
- Average phishing site lifespan is under 12 hours. (BlackBerry Global Threat Intelligence Report)
- Post-July 2024 AI upgrades raised phishing-site detection 87.3% and lookalike domain detection 85.94%. (Cyberint – Europe Threat Landscape 2024–2025)
Business Email Compromise (BEC) Through Phishing

- 72.9% of BEC incidents were initiated through phishing. (Arctic Wolf Threat Report)
- 18.9% of BEC cases involved previously compromised credentials, often harvested from earlier phishing campaigns. (Arctic Wolf Threat Report)
- 4.3% of BEC incidents involved misconfiguration or exploited API access that enabled unauthorized mailbox control. (Arctic Wolf Threat Report)
- 0.8% of BEC cases were linked to malicious insiders. (Arctic Wolf Threat Report)
- 26.5% of BEC cases targeted finance and insurance, 13.3% legal and government, and 11.4% manufacturing. (Arctic Wolf Threat Report)
- 76% of organizations affected by phishing-related BEC had not implemented phishing-resistant MFA. (Arctic Wolf Threat Report)
- 30% reduction in successful BEC compromises occurred among trained employees. (Arctic Wolf Threat Report)
- 58% of financially motivated phishing attacks were BEC-related. (Verizon DBIR 2025)
- 27% of all investigated incidents were classified as BEC. (Arctic Wolf Threat Report)
- Average initial loss in phishing-based BEC incidents exceeded $160,000 before recovery. (Arctic Wolf Threat Report)
- Total BEC losses linked to phishing reached $2.9 billion across 21,489 cases. (Check Point Research)
- Email compromise losses attributed to phishing totaled approximately $2.6 billion. (Verizon DBIR 2025)
- Credential phishing made up 73.9% of BEC; 18.9% used previously compromised creds; 4.3% involved misconfig or abused API access; 0.8% involved malicious insiders. (Arctic Wolf Threat Report)
Credential Theft and Breach Vectors
- 61% of reported phishing incidents named credential phishing as the most common breach vector. (Check Point Research)
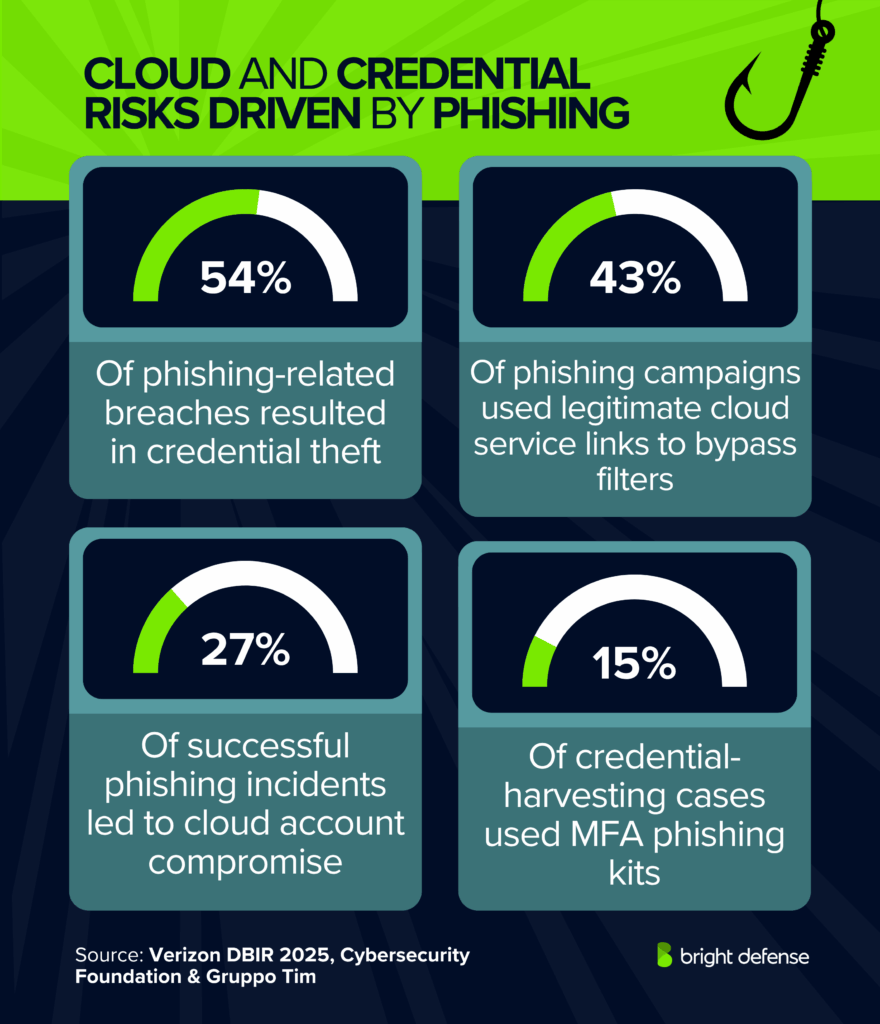
- 54% of phishing-related breaches resulted in credential theft. (Verizon DBIR 2025)
- 27% of successful phishing incidents led to cloud account compromise. (Cybersecurity Foundation & Gruppo Tim)
- 15% of credential-harvesting cases used MFA phishing kits. (Verizon DBIR 2025)
- 16% of cases saw secondary compromises due to password reuse after phishing. (Verizon DBIR 2025)
- 43% of phishing campaigns used legitimate cloud service links to bypass filters. (Verizon DBIR 2025)
- 19% of breaches originated from smishing or vishing channels. (Verizon DBIR 2025)
- 73% of breaches were attributed to unauthorized access, often tied to phishing and credential theft. (Flashpoint Global Threat Intelligence Report)
- Of the confirmed phishing emails:
- 43% were credential phishing
- 6% contained malicious attachments
- 51% were generic social engineering attempts (Red Canary Threat Detection Report)
- 53% of malicious attachments were .zip; growth tied to macro removal and user familiarity, often password protected. (OpenText Cybersecurity Threat Report)
Insider Threats and Human Error Contributing to Phishing

- 55% of insider-related security incidents were triggered through phishing or social engineering. (Ponemon Insider Threat Report)
- 31% of insider incidents began with employees clicking phishing emails or opening malicious attachments. (Ponemon Insider Threat Report)
- Average cost of a phishing-related insider incident reached $804,997, up 14% from 2023. (Ponemon Insider Threat Report)
- Mean time to contain phishing-related insider breaches was 77 days vs 63 days for other insider types. (Ponemon Insider Threat Report)
- 64% of organizations said phishing often involves credential misuse that leads to insider data exposure. (Ponemon Insider Threat Report)
- 41% reported AI-generated phishing increased insider-driven credential theft. (Ponemon Insider Threat Report)
- 67% cited phishing awareness and email security training as the most effective insider risk measure. (Ponemon Insider Threat Report)
- 38% said phishing simulations helped pinpoint employees most likely to fall for social engineering. (Ponemon Insider Threat Report)
- 72% of insider incidents tied to phishing occurred because employees failed to verify sender authenticity. (Ponemon Insider Threat Report)
- 46% of phishing incidents within the insider category resulted in data exfiltration or unauthorized file sharing. (Ponemon Insider Threat Report)
- 53% increased behavioral monitoring of email activity after major phishing events. (Ponemon Insider Threat Report)
- 58% said AI-enabled phishing is the fastest-growing insider threat vector. (Ponemon Insider Threat Report)
- 49% of insider incidents linked to phishing were unintentional/negligent, 51% involved malicious insiders with external collaborators. (Ponemon Insider Threat Report)
- Real-time activity monitoring correlated with a 37% reduction in phishing-related insider costs. (Ponemon Insider Threat Report)
- Financial services saw the highest phishing-related insider losses, averaging $1.2M per incident. (Ponemon Insider Threat Report)
- 62% said phishing emails increasingly bypass traditional DLP through cloud-based channels. (Ponemon Insider Threat Report)
- 44% of phishing-triggered insider incidents led to unauthorized use of privileged accounts. (Ponemon Insider Threat Report)
- 48% expect phishing-related insider risks to grow with GenAI and automation tools. (Ponemon Insider Threat Report)
- 69% now consider phishing-driven credential misuse the top insider threat category for 2025. (Ponemon Insider Threat Report)
- 68% of breaches involved a human element that includes phishing, stolen credentials, or social engineering. (Verizon DBIR 2025)
Phishing Delivery and Techniques
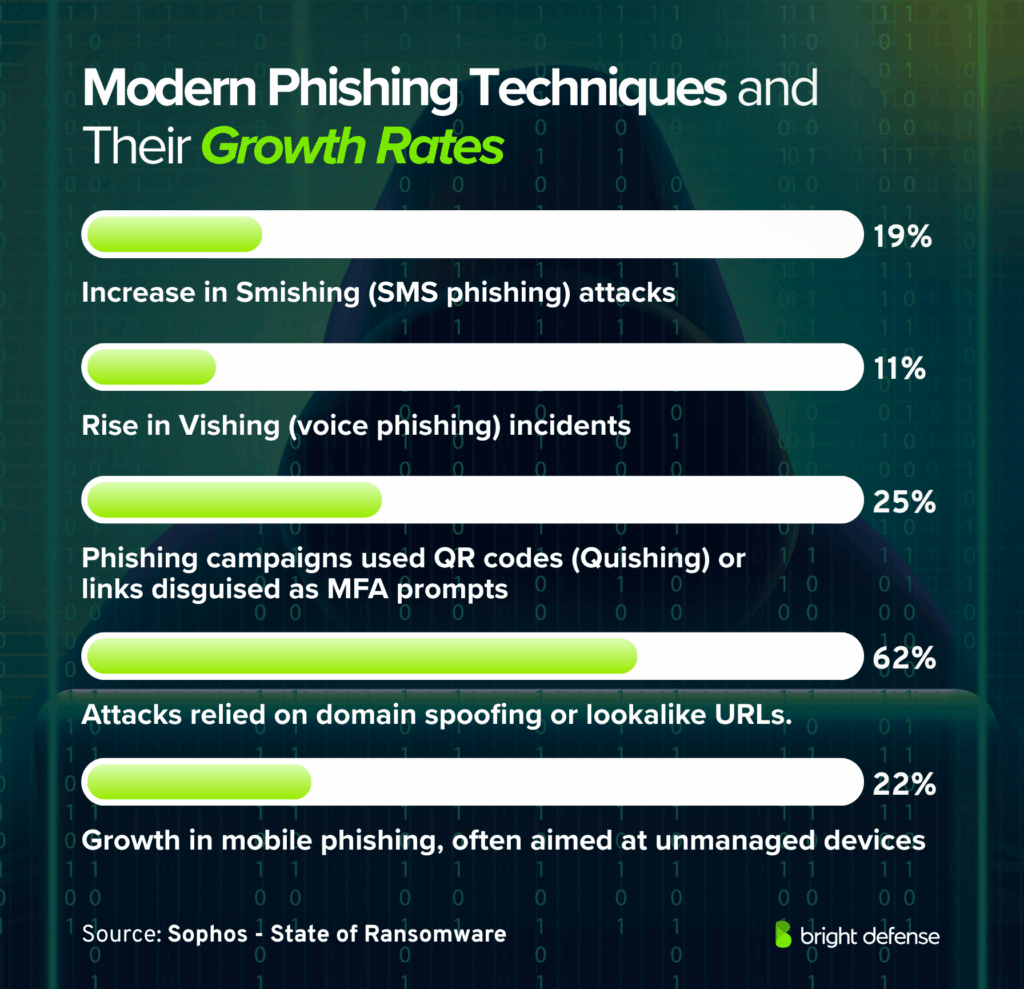
- 19% smishing growth and 11% vishing growth. (Check Point Research)
- ~25% of campaigns used QR codes or links disguised as MFA prompts. (Check Point Research)
- 11% of zero-day phishing URLs evaded email gateways despite a 14% accuracy gain. (Check Point Research)
- Links inside PDF/HTML attachments rose 8% vs 2023. (Check Point Research)
- File-type mix in phishing attachments: .exe 54%, .dll 11%, .pdf 6%, .jar 5%. (Check Point – 2024 State of Cybersecurity)
- 27% of phishing emails carried malicious links and 18% had weaponized attachments. (Verizon DBIR 2025)
- MFA-phishing kits appeared in 15% of credential-harvesting cases. (Verizon DBIR 2025)
- Quishing grew 11% year over year. (Verizon DBIR 2025)
- 43% of campaigns used legitimate cloud service links to bypass filters. (Verizon DBIR 2025)
- Generative-AI phishing content increased 22%. (Verizon DBIR 2025)
- 53% of malicious email attachments were .zip; .htm 20%, .pdf 7.5%, .doc/.rar 5.6%. (OpenText Cybersecurity Threat Report)
- AWS abuse rose 22.5%; Google APIs named top abused service. (OpenText Cybersecurity Threat Report)
- Tactic set expanded to quishing, TOAD, and use of legitimate cloud hosting. (OpenText Cybersecurity Threat Report)
- Confirmed phish split: credential 43%, malicious attachments 6%, generic social engineering 51%. (Red Canary Threat Detection Report)
- Notable techniques: Google Translate domain rewrite, URL shorteners with open redirects, multilingual lures, fake-CAPTCHA “paste-and-run,” malicious copy-and-paste (T1204.004). (Red Canary Threat Detection Report)
- PhaaS accounted for 21% of campaigns. (BlackBerry Global Threat Intelligence Report)
- Quishing made up 9.5% of campaigns late 2024. (BlackBerry Global Threat Intelligence Report)
- Mobile phishing rose 22%, often targeting unmanaged devices. (BlackBerry Global Threat Intelligence Report)
- 62% of attacks used domain spoofing or lookalike URLs. ((Cybersecurity Foundation & Gruppo Tim)
- 31% used fake Microsoft or Google login pages. (Cybersecurity Foundation & Gruppo Tim)
- 26% included links to fake login portals and 18% contained malicious attachments. (Cybersecurity Foundation & Gruppo Tim)
- PhaaS (Phishing-as-a-Service) platforms grew 21%.(Cybersecurity Foundation & Gruppo Tim)
- 235 million malware-attachment emails quarantined in 2024; email-malware share ranged from 0.42% to peaks of 2.50% and 1.92%.(OpenText Cybersecurity Threat Report)
- Google Translate domain rewrite abuse; URL shorteners and trusted hosts for open-redirect credential theft. (Red Canary Threat Detection Report)
- Paste-and-run fake CAPTCHA lures and malicious copy-and-paste technique growth. (Red Canary Threat Detection Report)
- Social media impersonation reached 938 cases in 2024; unofficial apps with malicious SDKs exposed data and credentials. (Cyberint – Europe Threat Landscape 2024–2025)
Cyber threats are growing fast and the numbers prove it. Check out 200+ cybersecurity stats that show how the threat scene keeps changing.
Industry-specific Impact
- The financial sector accounted for the largest share of phishing incidents, representing 24% of all cases. Healthcare followed with 17%, while education reported 11%.(Verizon DBIR 2025)
- Business Email Compromise (BEC) by sector:
- Finance & insurance 26.5%
- Legal & government 13.3%
- Manufacturing 11.4% (Arctic Wolf Threat Report)
- Financial services had the highest phishing exposure rate, followed by healthcare and education. (Check Point Research)
- Finance, healthcare, and government were the most targeted by phishing campaigns. (BlackBerry Global Threat Intelligence Report)
- Manufacturing and public administration saw a double-digit increase in phishing-driven intrusions. (Verizon DBIR 2025)
- Financial services incurred the highest phishing-related insider losses, averaging $1.2M per incident. (Ponemon Insider Threat Report)
- Small orgs vs large: 40% of small organizations cited phishing as their most frequent breach vector vs 27% of large enterprises. (Verizon DBIR 2025)
- Finance departments/executives were targeted in 43% of phishing emails with payment-related lures.(Cybersecurity Foundation & Gruppo Tim)
- In Europe, IT, education, and healthcare were the most phished sectors. (Cyberint – Europe Threat Landscape 2024–2025)
- Healthcare hit 67% in 2024; mean recovery cost 2.57 million dollars; Change Healthcare and Synnovis incidents noted. (CyberProof Global Threat Intelligence Report)
- During US election week, 6 billion malicious DDoS requests blocked; supply-chain breach growth and major cases summarized.(CyberProof Global Threat Intelligence Report)
Regional Breakdown of Phishing Attacks
Phishing remains a key entry point for ransomware, though its impact differs by region. The data below shows how phishing-driven attacks vary across countries.
Phishing in the Asia-Pacific Region
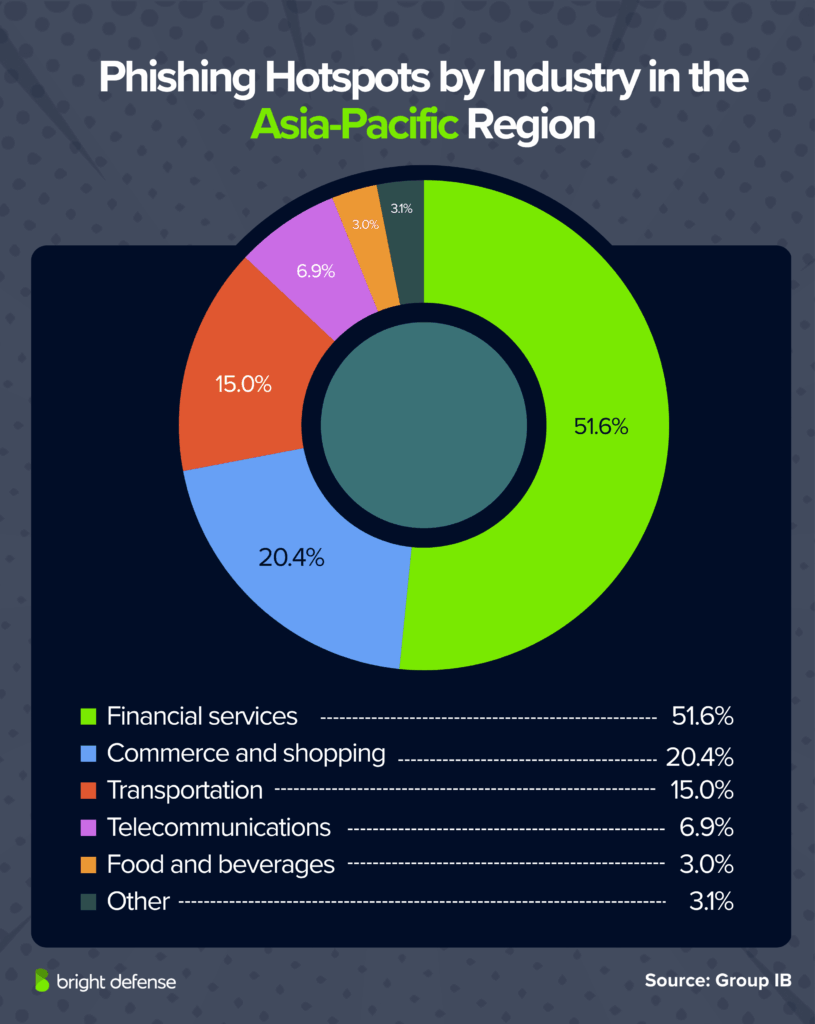
- In the Asia-Pacific region, phishing activity concentrated heavily on financial institutions, which accounted for 51.6% of all detected phishing attempts. Here’s a breakdown of different industries which has been impacted by phishing:
- Financial services 51.6%
- Commerce and shopping 20.4%
- Transportation 15.0%
- Telecommunications 6.9%
- Food and beverages 3.0% (Group IB)
Australia
- Phishing caused 24% of ransomware attacks.
- Exploited vulnerabilities led with 28%, phishing followed at 24%, and compromised credentials at 21%.
- Data theft occurred in 35% of encrypted attacks, higher than 2024.
India
- Malicious emails responsible for 21% of ransomware attacks.
- Down from about 34% in 2024.
- Vulnerabilities 29%, credentials 22%.
- Data stolen in 31% of encrypted incidents.
Japan
- Phishing initiated 22% of ransomware attacks, down from 26% in 2024.
- Vulnerabilities and credentials each 26%.
- Data encryption rate 34%, down from 76% in 2024.
Singapore
- Phishing responsible for 36% of ransomware incidents.
- Malicious emails triggered 29% of attacks.
Source: Sophos State of Ransomware
State of Phishing in Europe
- Phishing incidents across Europe show distinct concentration patterns across industries. Here is the breakdown:
- Travel 57.6%
- Logistics 27.5%
- Government and military 8.2%
- Financial services 3.6%
- Transportation 1.6%
- Crypto Drainer Campaign “Declaration Trap” — impersonated European tax authorities, mainly targeting Dutch residents. (Group IB)
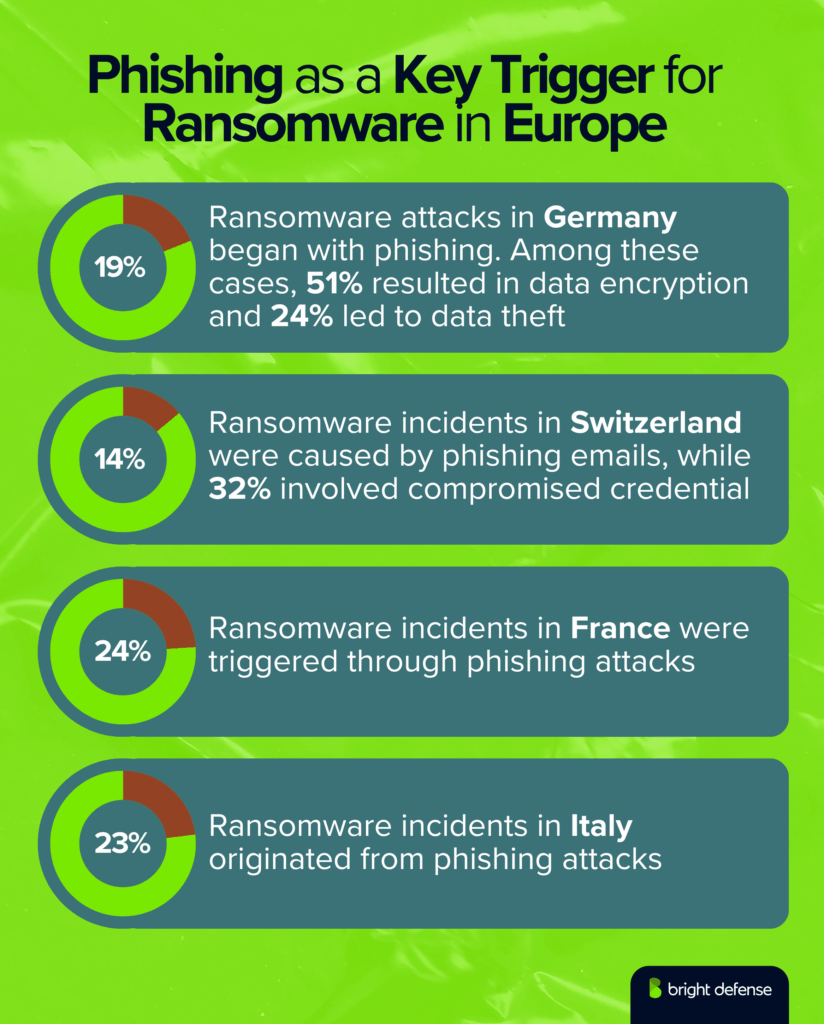
- In Germany, phishing was responsible for 19% of ransomware attacks, a drop from 30% in 2024. Vulnerability exploitation remained the main entry point at 42%. Once attackers gained access, 51% of cases resulted in data encryption, and 24% led to data theft. (Sophos State of Ransomware)
- In Switzerland, phishing emails caused 14% of ransomware incidents, down from 29% the year before. Around 32% of cases involved compromised credentials, while 31% exploited known vulnerabilities. (Sophos State of Ransomware)
- Data theft was seen in 10% of encrypted cases, compared to 29% last year, showing a notable decline in Switzerland. (Sophos State of Ransomware)
- In France, 24% of ransomware incidents began with phishing, and 23% involved stolen credentials used to escalate access. (Sophos State of Ransomware)
- In Italy, 23% of ransomware incidents originated from phishing, with 16% tied to credentials stolen in earlier phishing campaigns. (Sophos State of Ransomware)
- In Spain, 17% of ransomware incidents were triggered by phishing, and 21% involved credentials compromised through phishing activity. (Sophos State of Ransomware)
State of Phishing in Middle East & Africa
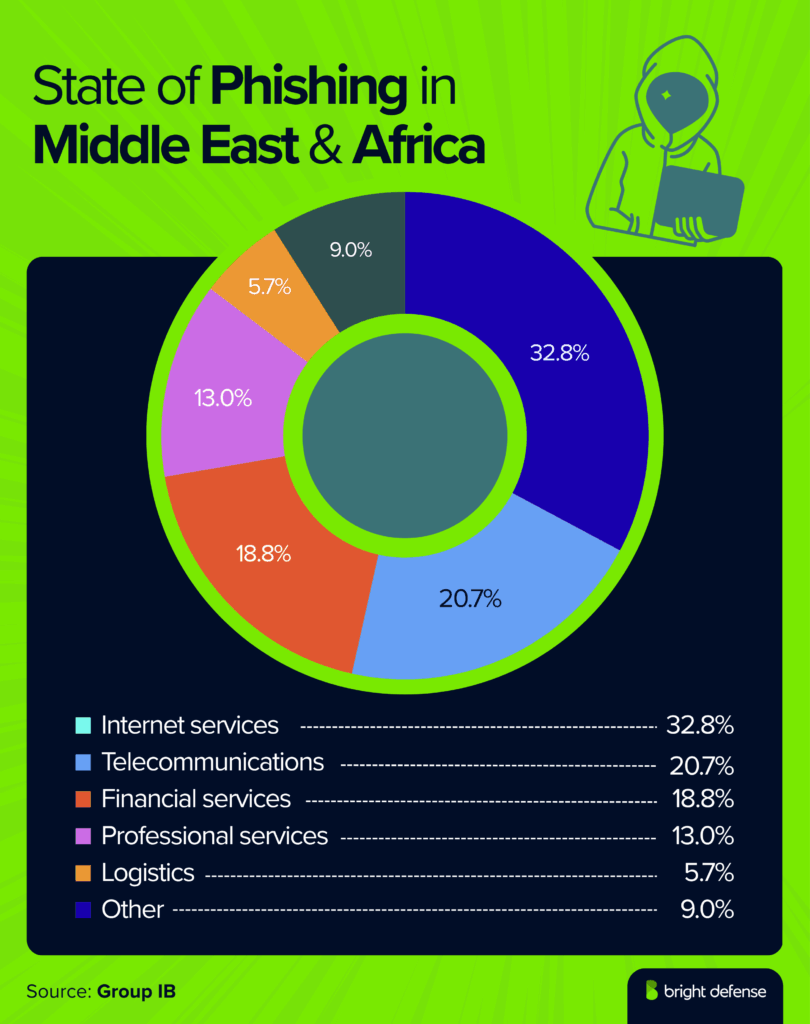
- Phishing activity across the Middle East and Africa shows a clear tilt toward digital infrastructure and financial platforms. Here are how different industries are being targeted by phishing:
- Internet services 32.8%
- Telecommunications 20.7%
- Financial services 18.8%
- Professional services 13.0%
- Logistics 5.7% (Group IB)
United Arab Emirates (UAE)
- Phishing initiated 23% of ransomware attacks. (Sophos State of Ransomware)
- In the United Arab Emirates (UAE), phishing initiated 23% of ransomware attacks. (Sophos State of Ransomware)
- Exploited vulnerabilities were the leading cause in the UAE, responsible for 42% of incidents, followed by 18% linked to credential theft. (Sophos State of Ransomware)
- Data theft affected 43% of encrypted attacks in the UAE, exceeding the global average of 28%. (Sophos State of Ransomware)
- Overall, 43% of organizations in the UAE chose to pay the ransom. (Sophos State of Ransomware)
South Africa
- Phishing emails triggered 22% of ransomware attacks.
- 34% resulted from credential theft tied to phishing.
Source: Sophos State of Ransomware
Phishing in North America
- In North America, phishing concentration remains heavily skewed toward the tech ecosystem. Internet services dominate with 79.8%. Here’s detailed breakdown:
- Internet services 79.8%
- IT 14.5%
- Financial services 3.6% (Group IB)
United States
- In the United States, phishing emails were behind 26% of ransomware incidents, dropping slightly from around 30% in 2024. (Sophos State of Ransomware)
- Vulnerability exploitation contributed to another 27% of attacks.(Sophos State of Ransomware)
- Across U.S. organizations, 51% of ransomware incidents led to data encryption, while 29% resulted in data theft. (Sophos State of Ransomware)
- More than half of affected U.S. organizations — about 53% — ultimately paid the ransom. (Sophos State of Ransomware)
Canada
- Phishing remains the most common initial access method used by both cybercriminals and state-sponsored threat actors.
- Phishing emails and SMS (smishing) are the leading cause of credential theft in Canada.
- Over 70% of ransomware infections in Canada begin with phishing emails.
- Spearphishing is a favored technique for state-aligned espionage groups targeting Canadian government and critical infrastructure.
- Phishing impersonation of Canadian financial institutions and logistics companies accounted for nearly half of observed phishing campaigns in 2024.
- AI-enabled phishing content is expected to drive a notable rise in social engineering attacks through 2026.
- Foreign interference campaigns used phishing to compromise election officials and exfiltrate voter registration data.
- Phishing kits on dark web markets include AI-written templates and realistic clone domains.
- Credential-stealing phishing emails targeting Canadian organizations increased 27% from 2023 to 2024.
- Multi-channel phishing that combines email, SMS, and social media is rising as attackers adapt to hybrid communication.
Source: Canadian Cyber Centre Threat Assessment
Phishing in Latin America
- Across Latin America, cyber incidents are spread across consumer-facing and financial sectors.
- Travel 40.9%
- Financial services 36.2%
- Commerce and shopping 13.8% (Group IB)
Brazil
- 18% of ransomware incidents originated from phishing.
- 20% from stolen credentials via phishing.
- 44% exploited vulnerabilities after phishing or credential theft.
Chile
- 20% of ransomware attacks began with phishing emails.
- 22% from compromised credentials.
- 46% involved vulnerability exploitation after phishing.
Colombia
- 24% of ransomware incidents started with phishing emails.
- 27% from credential theft.
- 30% exploited vulnerabilities after phishing-based access.
Mexico
- 13% of ransomware infections began with phishing emails.
- 28% linked to credential theft from phishing.
Source: Sophos State of Ransomware
Liked the stat content? Check Out our latest stat articles:
List of Recent Phishing Attacks
Recent phishing incidents have targeted major organizations through social and technical exploits. Below are notable recent attacks and their impact:
1. BNB Chain Recovers X Account After $8,000 Phishing Scam Amid Record Crypto Losses
BNB Chain has regained control of its official X account after a brief phishing attack that lured users with fake reward links. The breach, which involved one phishing contract and ten malicious URLs, led to total losses of about $8,000. One user lost $6,500, the bulk of the damage, after connecting to a fraudulent wallet prompt.
The attacker injected roughly $17,800 through the contract before cashing out meme tokens valued at $22,000. Fortunately, the incident was quickly contained, and no compromise occurred within the BNB network itself. Control of the X account was restored within hours.
This event adds to a growing wave of crypto-related phishing scams. A recent Chainalysis report revealed that phishing attacks surged this year as cyber threats across blockchain ecosystems intensified. Cybercriminals have stolen $2.17 billion so far in 2025, already surpassing last year’s total and marking a 17% rise from 2022. In one separate case, a BNB whale lost $13.5 million to a similar phishing link.
BNB Chain stated it is investigating the cause of the breach and urged users to remain alert against social media reward offers or unfamiliar links. Experts noted that cyber attacks begin with small entry points that can quickly escalate into broader financial losses if not contained. (Coin Tribune)
2. Hackers Use PDFs and Phone Scams to Impersonate Major Brands in Phishing Surge
A widespread phishing campaign is using fake PDFs and phone scams to impersonate trusted companies and steal sensitive data. The attacks, known as Telephone-Oriented Attack Delivery (TOAD), trick victims into calling fraudulent support lines or scanning malicious QR codes embedded in PDFs.
The scams often use Voice over Internet Protocol (VoIP) numbers and mimic real customer service systems to appear legitimate. Attackers have also exploited the Microsoft 365 Direct Send feature to send fake internal emails with credential phishing emails attached, which often lead to malware attacks when opened.

Researchers say some phishing messages were aided by AI tools that unknowingly generated links to unregistered or fake domains. Others involved phishing through injected code that redirected traffic to cloned login portals.
Experts warn that these evolving tactics, combining phone deception, QR phishing, and AI manipulation, are making social engineering attacks more convincing and harder to detect, posing growing security threats for both individuals and global businesses. (The Hacker News)
3. HMRC Phishing Scam Exposes 100,000 Accounts, £47 Million Stolen
A large-scale phishing attack allowed criminals to access about 100,000 taxpayer accounts and steal £47 million through fake rebate claims. HMRC said all affected accounts were secured and reset, assuring taxpayers that no personal funds were lost.

The fraudsters used stolen personal data to create false online tax profiles, many in the names of people unaware the accounts existed. Officials confirmed arrests were made and said efforts are ongoing to strengthen HMRC’s digital defences and expand multi factor authentication to reduce exposure.
The incident, described as organised and adaptive, prompted government plans to improve defences against security breaches and online fraud in the public sector. (BBC)
4. Cyber Attack Disrupts Edinburgh Students’ Exam Revision
An attempted spear-phishing attack on Edinburgh Council’s education department forced a citywide password reset just days before major exams. The precaution cut thousands of students off from online revision tools, prompting schools to reopen so pupils could collect new credentials.
Officials said the attack was detected and contained quickly, with no data compromised and systems expected to return to normal within days. The council provided online help and replacement study materials to minimise disruption.
The incident reflected rising threat reporting rates across the UK education sector and demonstrated how compromised accounts can impact daily operations. (BBC)
5. WhatsApp Deletes 6.8 Million Scam Accounts in Global Crackdown
WhatsApp removed 6.8 million accounts linked to large-scale scam operations during the first half of 2025. Many were tied to organized crime networks in Southeast Asia that use forced labor to run fraudulent schemes.

The platform said it detected and blocked accounts before they could be used for scams, such as fake investment offers and group chat invitations. New safety features now warn users when they’re added by unknown contacts on messaging apps.
Some scams used AI-generated messages to attract victims with false job or investment promises, often ending with payments through crypto platforms. Authorities continue to warn users to stay alert and enable two-step verification or multi factor authentication to prevent hijacking. These preventive actions have reduced the number of reported malicious emails and similar phishing messages. (BBC)
6. UK Police Warn of Rising ‘Courier Fraud’ Targeting Vulnerable Victims
Police across the UK have raised alarms over a surge in courier fraud, a scam where criminals pose as bank staff or police officers and trick victims into handing over their bank cards, cash, or valuables.
In a recent crackdown, 18 arrests were made, with £250,000 and hundreds of bank cards recovered. Authorities say about 80% of victims are over 65, with the oldest known victim aged 101.
The scam typically begins with a fake phone call claiming there is a problem at the victim’s bank. Victims are persuaded to hand over their card or withdraw cash for “safekeeping.” In some cases, scammers have demanded gold or other assets. These criminals use emotional pressure to deceive users into compliance.
Police urge anyone receiving such calls to hang up immediately, wait a minute, and call their bank or the police using verified contact numbers. They stress never to share PINs, hand over bank cards, or make purchases following unsolicited calls. Law enforcement believes these targeted industries will remain under threat unless awareness expands across global email traffic channels. (The Guardian)
Keeping up with cybersecurity compliance is tougher than ever. See 150+ cybersecurity compliance stats that highlight the challenges, progress, and real-world impact.
7. Iran-Linked Hackers Target Israeli Experts in New Phishing Campaign
A state-sponsored group known as APT42 has launched a new wave of phishing attacks against Israeli journalists, cybersecurity experts, and computer science professors. The group, believed to be tied to Iran’s Islamic Revolutionary Guard Corps, posed as cybersecurity firm employees to steal victims’ email credentials and two-factor authentication codes.
The attackers contacted targets through email and WhatsApp, using realistic AI-generated messages to build trust before sending fake Google Meet or Gmail login links. These cyber threats highlight how targeted industries face espionage through cross-platform phishing tactics.

Researchers say the campaign is part of Iran’s ongoing espionage efforts aimed at gathering intelligence from high-profile Israeli figures. Similar attacks have also been reported in Europe, where Iranian hackers recently disrupted public services in Albania.
Security analysts warn that Iran-linked cyber activity is expected to intensify, particularly across global businesses managing sensitive data. (The Record)
What Is Phishing and How Does It Work?
Phishing is a scam where attackers pose as trusted entities to trick people into revealing sensitive data or installing malware. It usually comes through fake emails, texts, calls, or social media messages that look legitimate. These phishing threats continue to evolve as attackers refine their tactics.

The goal is often financial gain, identity theft, or unauthorized access. Phishing can also serve as the entry point for larger attacks that deploy malware or steal company data through multi channel attacks that blend email, SMS, and messaging platforms.
Common methods involve links to counterfeit websites or malicious attachments. Messages use urgency, fear, or rewards to push victims into quick action, sometimes as part of phishing campaigns targeting multiple organizations.
A phishing attack typically follows five stages:
- Preparation: The attacker creates fake websites and messages mimicking real sources.
- Delivery: The fraudulent message is sent through email, SMS, or social media.
- Interaction: The victim clicks a link or opens an attachment, believing it is real.
- Compromise: The attacker captures credentials or gains device access.
- Exploitation: Stolen data is used for theft, fraud, or further intrusion.
Phishing depends on deception and emotional manipulation rather than technical skill. Recognizing these signs helps users defend against such attacks and avoid becoming victims of impersonation scams.
What are the Likely Future Developments In Phishing and Its Defense?
Phishing is continually evolving, with attackers using advanced tools to create convincing scams while defenders race to improve countermeasures. This report focuses on future phishing tactics, detection technology, and the role of AI on both sides, emphasizing technical systems rather than policy or training. The rise in latest phishing statistics highlights how these threats continue to expand across industries.
Emerging Phishing Tactics and Techniques
Attackers are using modern technologies to make phishing more deceptive and scalable. These phishing threats often blend social engineering with automation, creating campaigns that are harder to track.
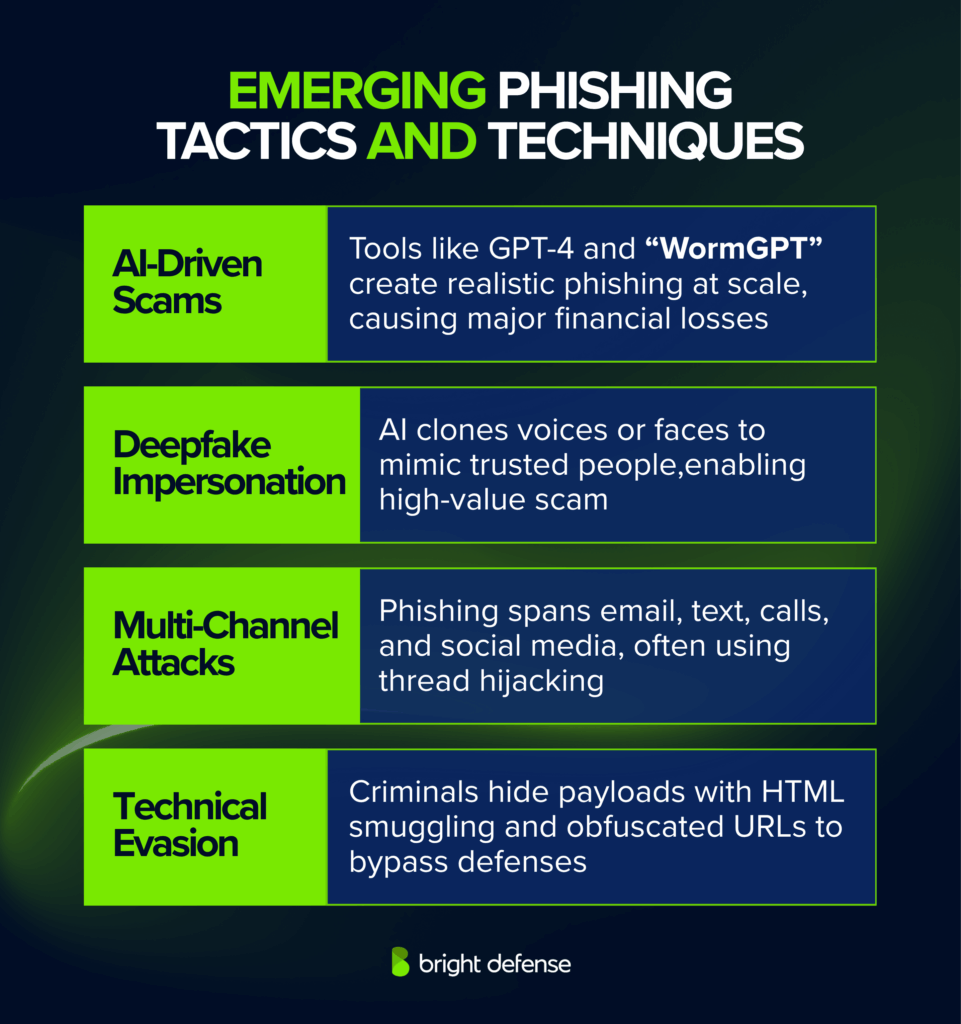
- AI-Driven Personalization and Volume: Generative AI tools like GPT-4 and “WormGPT” automate phishing at scale, using scraped personal data to imitate writing styles. The FBI has reported major financial losses from AI-written scams, with phishing volume rising over 1,200% in 2024. AI lowers the expertise needed to launch professional-looking attacks and contributes to significant concern among security experts.
- Deepfake Voice and Video Impersonation: AI can now clone voices or faces to impersonate executives or relatives in calls or video meetings. Real cases include a 2024 deepfake CFO scam that stole $25 million. These attacks blur authenticity and make deception easier, showing the growing risk of voice phishing in corporate environments.
- Multi-Channel “Social Engineering” Attacks: Phishing extends beyond email into text messages, voice calls, and social media. Attackers use combinations like follow-up calls to add credibility. Thread hijacking—where attackers reply within real email chains—is increasingly common and difficult to detect. Such multi channel attacks demonstrate how modern phishing adapts to user communication habits.
- Technical Evasion and Obfuscation: Criminals use HTML smuggling, padded attachments, and obfuscated URLs to bypass scanners. AI-generated text changes file hashes and hides payloads, producing polymorphic phishing that resists detection. The involvement of anti phishing working group reports shows the need for coordinated data sharing across organizations.
Advances in Phishing Detection Technologies
Detection methods are evolving toward smarter, multi-layered analysis. Current phishing campaigns are being tracked through AI-powered threat intelligence systems that classify and isolate suspicious patterns faster than before.
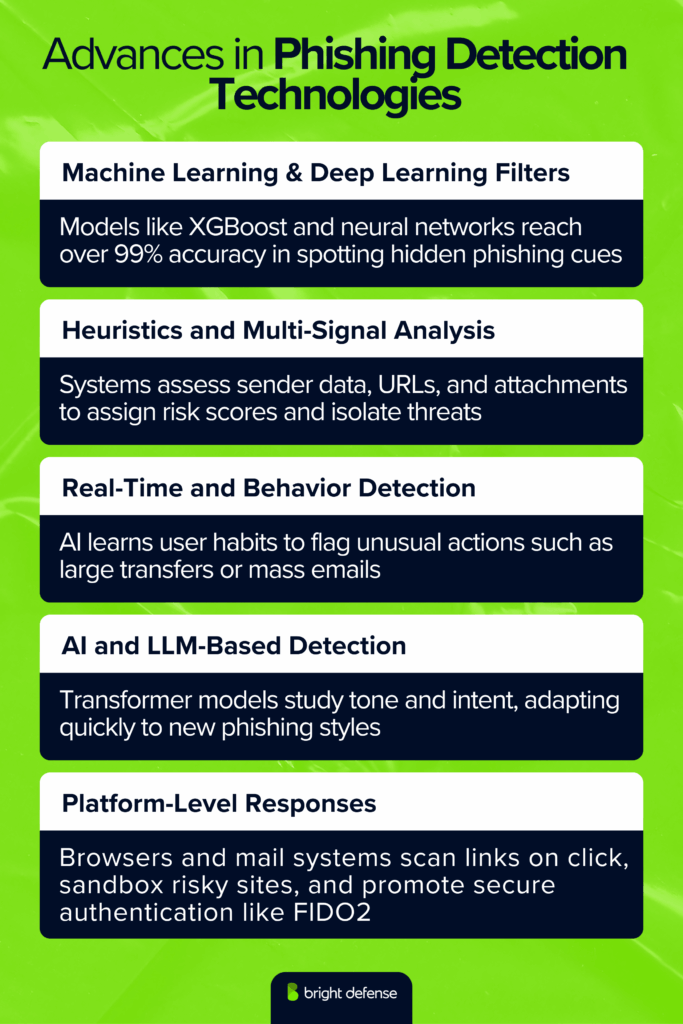
- Machine Learning & Deep Learning Filters: Modern filters use models like XGBoost and neural networks, achieving over 99% accuracy. These detect subtle phishing signals that static systems miss.
- Heuristics and Multi-Signal Analysis: Systems now analyze multiple signals—sender metadata, URLs, reputation, and attachments—to assign risk scores and quarantine threats more accurately.
- Real-Time Monitoring and Behavior Anomaly Detection: AI models learn typical user behavior to spot anomalies such as sudden large transfers or mass emails, flagging possible compromises.
- AI and LLM-Based Detection: Transformer-based models analyze tone and intent, identifying suspicious context and phrasing. They adapt faster to new phishing variants and can explain detection logic.
- Platform-Level Responses: Browsers and email providers now analyze links at click time, sandbox suspicious sites, and promote phishing-resistant authentication like FIDO2. Platforms also use AI to detect deepfake media and verify audio or video requests.
In summary, AI defines the next stage of phishing warfare. Attackers exploit it to multiply deception, while defenders use it to identify threats with greater intelligence and speed. The contest will depend on how quickly defensive AI evolves to counter the creativity of AI-powered phishing.
Why Phishing is a Major Cyberthreat?
Phishing remains a major cyberthreat because it exploits human trust and scales easily. Verizon’s 2025 DBIR links about 60% of breaches to human actions. Business Email Compromise caused $2.77 billion in losses in 2024, while total cybercrime losses reached $16.6 billion. Phishing accounted for 16% of initial breaches, with many credential abuse cases starting the same way, according to key phishing statistics from recent security reports.
Attackers now use adversary-in-the-middle pages to steal session cookies and bypass MFA, a tactic that surged 146% in 2024. Crimeware kits have made phishing cheap and accessible, while qr code phishing attacks and AI-generated messages now make up a growing share of lures. These campaigns also deliver ransomware and enable espionage, affecting victims in 139 countries through phishing breaches that compromise data integrity.
The most effective defenses include phishing-resistant MFA (FIDO2 or WebAuthn), SPF/DKIM/DMARC email authentication, DNS blocking of phishing infrastructure, and regular user training. These measures lower success rates and limit damage when a lure gets through, supported by guidance from the anti phishing working group and security awareness training programs that reinforce user vigilance.
How Do You Prepare for Phishing in 2025?
AI-driven phishing is more convincing than ever, making it a top cause of breaches. Strong awareness, detection, and quick response are key to staying protected.
The following steps outline how to strengthen defenses and reduce the risk of falling victim to modern phishing tactics:
1. Understand the Threat Landscape
Phishing remains the top cybercrime worldwide, responsible for over 22% of all reported internet crimes in 2024 and causing $70 million in losses. It continues to serve as the most common entry point for attacks. In 2025, AI-generated phishing has made threats far more realistic, producing messages that mirror real brands and evade filters. More than 86% of organizations have already encountered at least one AI-related phishing or social engineering incident. These latest phishing statistics demonstrate the ongoing growth of digital deception.
Attackers increasingly use advanced tactics such as QR code phishing (quishing), malicious MFA prompts, and cloud-hosted credential lures. PhaaS (Phishing-as-a-Service) kits have also grown 21%, giving even low-skilled actors the tools to run large-scale campaigns and launch phishing campaigns against targeted sectors.
2. Strengthen Employee Awareness
Humans remain the first line of defense. Verizon’s 2025 DBIR found that 68% of breaches involved a human element—often a phishing email. Organizations that invested in awareness programs saw 38% lower click rates on simulated phishing messages.
Practical steps include:
- Running quarterly phishing simulations.
- Teaching staff to verify sender addresses and URLs.
- Emphasizing rapid user reporting of suspicious messages—ideally within minutes, not hours.
- Highlighting AI-driven phishing examples so employees can recognize synthetic writing patterns.
3. Update Technical Defenses
Email security systems improved filtering accuracy 14% last year, but 11% of zero-day phishing URLs still slipped through. Detection powered by AI reduced false negatives 18%, yet no system catches everything. Combining multiple layers remains critical.
Recommended measures:
- Use phishing-resistant MFA (hardware keys, FIDO2 tokens).
- Implement real-time domain monitoring to spot lookalike or spoofed domains.
- Block open-redirect links and monitor cloud-hosted file shares for malicious messages or uploads.
- Deploy endpoint detection systems that flag “paste-and-run” or copy-and-paste payloads.
4. Address AI and Identity Risks
AI-powered phishing now fuels identity-based attacks in 60% of cases. Deepfake voice calls, cloned faces, and synthetic documents add a new dimension to deception. To counter this:
- Train employees to question unexpected audio or video messages requesting credentials or money, helping prevent impersonation scams.
- Enable anomaly-based login detection and device fingerprinting to catch imposters.
- Limit AI tool permissions inside the organization—60% of IT teams currently lack visibility into their use, increasing exposure.
5. Reinforce Incident Response and Metrics
Phishing readiness requires preparation beyond prevention. Yet 29% of organizations still do not track phishing metrics. Measuring exposure, click rates, and reporting speed reveals weak points early.
To prepare effectively:
- Maintain a rapid containment workflow for suspected phishing incidents.
- Set clear escalation paths for BEC attacks or credential compromise.
- Use forensic tools to trace phishing-driven data access.
- After incidents, review simulation data and refine policies with support from the anti phishing working group.
6. Prepare for Sector-Specific Risks
Phishing affects every industry, but finance, healthcare, and government remain prime targets. Financial firms see the highest losses, averaging $1.2 million per phishing-related insider event. Public-sector institutions face spear-phishing campaigns that exploit election or tax themes, while education and healthcare networks continue to be hit by ransomware triggered through phishing breaches.
7. Maintain a Continuous Defense Posture
Phishing sites now last less than 12 hours, meaning detection speed determines success. Organizations that continuously update filters, rotate credentials, and refresh staff awareness are far less likely to suffer large-scale compromise. Regular security awareness training keeps teams alert and helps identify subtle new threats.
8. Strengthen Sign-In Security
Use phishing-resistant MFA such as passkeys, hardware keys, or authenticator apps. Avoid SMS codes when possible. Decline unexpected prompts and watch for MFA fatigue attacks. Multi-factor solutions should be expanded across departments to reduce multi channel attacks that combine voice, text, and email.
9. Manage Passwords Wisely
Use a password manager to create and store strong, unique passwords for every site. Replace weak or reused ones. Keep recovery codes saved securely and offline. This limits damage from phishing breaches that expose credentials.
10. Think Before You Click
Pause and consider what triggered the message. Unexpected invoices, password resets, or prize alerts are red flags. Verify through a known, trusted channel instead of replying to the same message. Such mindfulness helps prevent incidents tied to recognize phishing attempts campaigns.
11. Check Senders and Links
View full sender addresses and look for misspellings or extra words. Hover or press and hold to preview links before clicking. Avoid shortened or strange URLs that imitate real domains. This small habit can block deceptive links before they cause harm.
12. Treat Attachments Carefully
Do not open unexpected attachments, even from familiar names. Use cloud preview when possible and keep macros disabled. Never open executable files from email, since malicious messages may hide inside compressed folders.
13. Verify Sensitive Requests
Always confirm financial or personal information requests through direct contact with the sender using a known number or channel. Use two-person approval for bank or payment changes, especially during impersonation scams targeting executives.
In 2025, preparing for phishing means accepting that prevention is an ongoing cycle—training, testing, updating, and responding. The goal is not to eliminate every fake message, but to shorten reaction times, reduce risk exposure, and keep attackers from gaining their first foothold.
What are the Different Types of Phishing?
Phishing comes in many forms, each designed to trick people into giving up information, money, or access. While the goal is always deception, the delivery methods vary across email, text, calls, and social media. Below are the most common types seen today and how each one works.
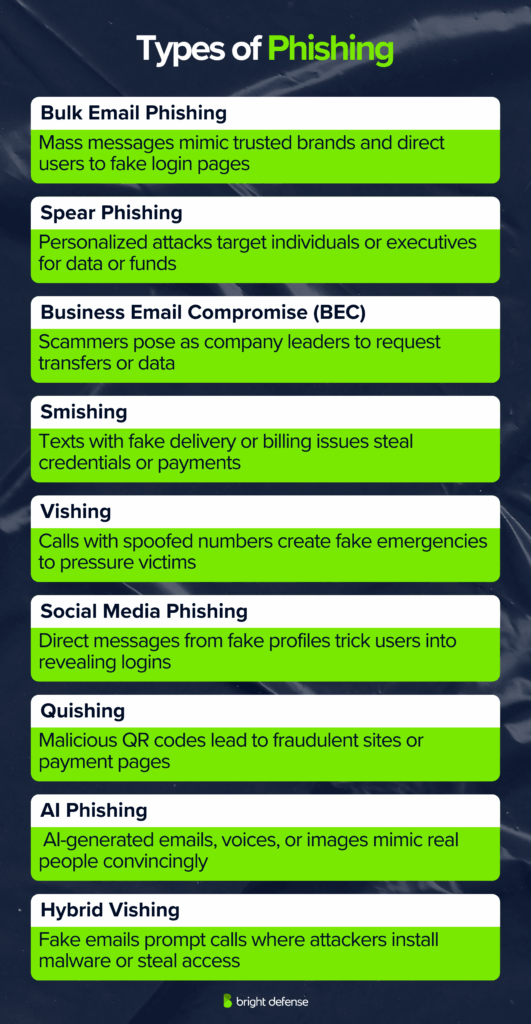
- Bulk email phishing: Scammers send mass emails posing as trusted brands like banks or retailers. Messages use real logos and urgent subjects such as “Payment issue” or “Account update.” Victims are lured to fake sites that steal credentials or install malware.
- Spear phishing: Targeted attacks on specific individuals, often with financial or data access. Attackers research victims online and impersonate someone they trust. When aimed at executives, it’s called whaling.
- Business Email Compromise (BEC): Scammers impersonate or hijack business accounts to request wire transfers or data. Common types include CEO fraud and email account compromise. Losses often reach millions per attack.
- Smishing: Fake texts from carriers or shippers claim billing or delivery issues. Clicking the link exposes victims to credential theft or payment fraud.
- Vishing: Phone scams using spoofed caller IDs to appear legitimate. Calls create panic over fake legal or billing problems. Vishing grew 260% from 2022 to 2023.
- Social media phishing: Scammers use DMs on platforms like Facebook or LinkedIn to pose as friends or support staff. They steal logins or direct users to fake forms and links.
- Quishing: Malicious QR codes in emails, messages, or public places lead to fake payment or login pages. Some replace real codes, such as those on parking meters.
- AI phishing: Generative AI creates flawless, personalized phishing emails in minutes. Scammers also use voice and image cloning to impersonate real people convincingly.
- Hybrid vishing: Attackers send fake emails urging a call to “support.” On the phone, victims are guided to install malware or give access credentials.
How Bright Defense Strengthens Phishing Defense
Bright Defense helps organizations reduce phishing risks through expert-led security training, phishing simulations, and penetration testing. Our hands-on training programs teach employees how to spot suspicious messages, avoid deceptive links, and respond correctly to real-world threats.
Through phishing-focused pen tests, we identify weak points in email systems, employee responses, and security controls before attackers can exploit them.
In addition, Bright Defense guides businesses through compliance frameworks such as SOC 2 and HIPAA, building stronger security practices that limit exposure to phishing-related breaches. With these combined services, organizations create a more informed workforce and a hardened defense against today’s most common attack method.
FAQ
Phishing is still one of the most reported internet crime categories. The FBI said phishing/spoofing was among the top three cyber crimes by complaint count in 2024, and the IC3 report lists 193,407 phishing/spoofing complaints in 2024.
APWG reported 3.8 million phishing attacks in 2025, up slightly from 3.76 million in 2024, and recorded 853,244 phishing attacks in Q4 2025. APWG also lists monthly Q4 totals of 269,558 (October), 287,995 (November), and 295,691 (December).
APWG’s Q4 2025 data shows Social Media and SaaS/Webmail as the most targeted sectors at 20.3% each, followed by Telecom (18.7%) and Financial Institutions (9.3%).
SMS phishing is rising, and URL-based attacks remain dominant. APWG reported steady 30% to 40% quarter-over-quarter growth in SMS-based fraud detections in Q4 2025, while Proofpoint highlights that URLs were used 4x more often than attachments in malicious emails, at least 55% of suspected smishing messages contained malicious URLs, and about 34% of URL-based malware campaigns delivered remote access software.
No, absolutely not. The FBI says not to click anything in an unsolicited email or text, and the FTC says suspicious phishing messages should be reported and deleted instead of opened.
Yes, act immediately. The FTC says to update your security software and run a scan if a harmful file may have downloaded, and to go to IdentityTheft.gov if sensitive information was exposed. The FTC also says to report phishing to APWG and ReportFraud, and the FBI points people to IC3 for phishing reports.
Yes, definitely. The FBI lists two-factor or multi-factor authentication as a key protection step, and Google’s passkey documentation says passkeys are resistant to phishing because they are bound to the website or app identity. Google also states passkeys are more secure against phishing than passwords.
Phishing trends in 2026 point to more AI generated and AI assisted social engineering, more attacks across email, SMS, voice, social platforms, and collaboration tools, and more phishing that abuses trusted login flows instead of only fake password pages. The World Economic Forum notes genAI is making phishing more scalable and more convincing, ENISA says phishing remains a primary initial access method and reports ClickFix fake CAPTCHA scams gaining momentum, and Proofpoint documents growth in Microsoft 365 device code phishing that leads to account takeover and data theft.
The strongest 2026 cybersecurity prediction is that AI will shape both attacks and defense more than any other factor, while fraud, phishing, and third party risk stay major concerns. WEF reports 94% of survey respondents see AI as the most significant driver of change in cybersecurity in the year ahead, and 77% report an increase in cyber enabled fraud and phishing; WEF also reports 65% of large companies cite third party and supply chain vulnerabilities as their top resilience challenge. Microsoft’s 2025 defense report also flags AI automated phishing and faster attack chains as a current pattern going into 2026.
The latest widely cited volume data shows APWG recorded 853,244 phishing attacks in Q4 2025, down 4% from Q3, and about 3.8 million phishing attacks across 2025, slightly above 2024. APWG also recorded 1,003,924 phishing attacks in Q1 2025, which was its largest quarterly total since late 2023, and noted smishing growth and continued QR code abuse trends during 2025. In the FBI IC3 2024 annual report, Phishing/Spoofing had 193,407 complaints and $70,013,036 in reported losses.
Get In Touch



