
Reviewed by:
Published:
October 9, 2023
Updated:
August 16, 2025
Risk-Based Mindset: The Core of Modern Risk Management
According to IBM, the average cost of a data breach in 2024 reached $4.88 million. With stakes this high, can any organization afford to take a reactive approach to risk?
At Bright Defense we strongly believe the key to staying ahead lies in adopting a risk-based mindset. This approach shifts the focus from just simply checking boxes to identifying, evaluating, and prioritizing real threats.
In this blog, we’ll break down what a risk-based mindset looks like and why it’s at the heart of effective, modern risk management.
Let’s jump right in!
What is a Risk-Based Mindset?
A risk-based mindset is a way of thinking that focuses on identifying, assessing, and prioritizing risks before making decisions. Instead of reacting to problems after they happen, this approach anticipates potential threats and weighs them against opportunities. It’s proactive, not reactive.
In security compliance, a risk-based mindset means identifying which systems, data, and processes pose the greatest risk if breached or misused, and focusing security and compliance efforts there first. Instead of applying uniform controls across the board, organizations prioritize based on threat likelihood, potential impact, and regulatory requirements.
This approach allows compliance teams to allocate resources efficiently, address high-risk areas first, and avoid wasting time on low-impact issues. It also helps demonstrate to regulators that the organization is not just checking boxes but actively managing compliance based on real risk exposure.
What is Modern Risk Management? And Why It Is Important?
Modern risk management is a proactive, data-driven approach that identifies, evaluates, and responds to risks in real time. It integrates technology, continuous monitoring, and cross-functional collaboration to address threats across cybersecurity, compliance, operations, and business strategy.
Unlike outdated models that rely on periodic reviews and rigid checklists, modern risk management adapts quickly to change, focusing on business impact and resilience.
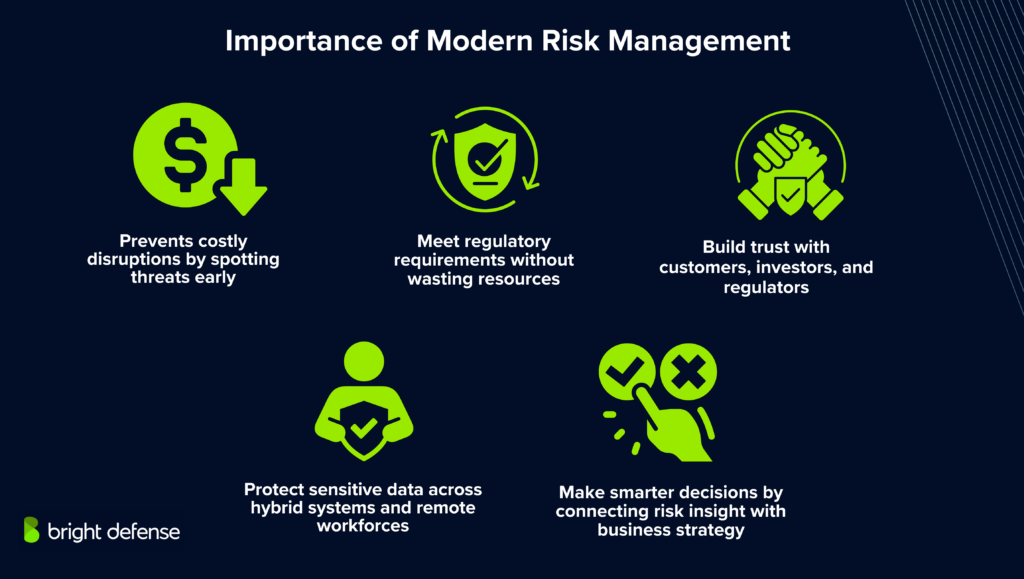
Modern risk management is critical because traditional methods can’t keep up with today’s fast-moving threats. Cyberattacks, regulatory shifts, supply chain disruptions, and reputational risks evolve constantly. A modern approach helps organizations:
- Prevent costly disruptions by spotting threats early
- Meet regulatory requirements without wasting resources
- Protect sensitive data across hybrid systems and remote workforces
- Build trust with customers, investors, and regulators
- Make smarter decisions by aligning risk insight with business strategy
Without modern risk management, organizations leave themselves exposed and reactive. With it, they stay ahead.
Why Adopt a Risk-Based Approach?
Adopting a risk-based approach means focusing on what truly matters and investing efforts where the payoff is highest. It cuts through noise and lets organizations prioritize threats that could destabilize operations or cause costly compliance failures.
Let’s learn more why adopting a risk-based approach matters:
- Efficient Resource Allocation: By focusing on the most significant risks, organizations can allocate their resources more efficiently, ensuring that critical areas receive the attention they deserve.
- Enhanced Decision Making: A risk-based approach provides a clearer picture of potential threats, allowing organizations to make informed decisions and prioritize actions based on potential impact.
- Flexibility and Adaptability: As the business environment changes, so do the risks. A risk-based mindset allows organizations to adapt quickly to new threats, ensuring that they remain compliant and protected.
Changing the Attitude Towards Risk-First
Most teams have been trained to chase feature delivery, speed, and innovation without first considering the consequences. Risk becomes an afterthought, addressed only when deadlines loom or incidents force a response. Shifting to a risk-first mindset demands that risk considerations come before everything else.
1. Bringing Risks Into Early Design Decisions
Rather than tacking on controls late, teams must treat potential security vulnerabilities, system failures, and insecure output as first-class concerns during initial planning.
Especially when building large language model applications, overlooking risks like direct prompt injection or insecure output handling can create gaps that attackers exploit. Stronger security postures form when risk shapes design choices from the beginning.
2. Redefining Success Metrics Around Resilience
A risk-first approach also reframes success. Teams do not measure progress solely by features shipped or deadlines met. Instead, they evaluate how well the work withstands critical security risks such as model denial of service or training data poisoning.
Teams that understand the importance of protecting training datasets, access logs, and backend systems build resilience into every layer of their work.
3. Shared Accountability Across All Teams
Responsibility cannot rest with security teams alone. Engineers, product managers, and data scientists all contribute to preventing data breaches and managing emerging threats. In doing so, they reduce the chances of service model denial attacks and improve overall llm security, without waiting for security flaws to surface during late-stage reviews.
4. Making Risk Management Part of Everyday Operations
Embedding risk-first thinking into everyday decisions creates organizations better prepared to handle the unique security challenges tied to llms and generative AI.
It shifts risk management away from isolated checkpoints and into the DNA of daily operations, preserving trust, protecting personally identifiable information, and supporting more durable innovation.
Implementing a Risk-Based Approach to Compliance
A risk-based approach allows organizations to proactively identify and prioritize their most critical security risks, enabling smarter allocation of resources and stronger overall protection.
Below is a practical breakdown of how to implement this strategy effectively.

1. Identify
Begin by identifying all relevant compliance-related risks within your organization. This includes operational risks, legal and regulatory exposure, and technological threats. You should consider both internal and external sources, ranging from insider threats and market volatility to emerging challenges like training data poisoning and insecure output handling in large language model applications.
2. Analyze
Once risks are identified, analyze each one for its potential likelihood and impact. This allows you to classify them into risk tiers: high, medium, or low. During this step, assess the broader implications, such as how direct prompt injection or insecure plugin design could compromise systems or violate regulatory obligations.
3. Action
Develop and implement targeted actions to mitigate the most critical security risks. This includes designing custom controls like rate limiting, role-based access restrictions, output sanitization, or secure integration protocols. These actions should focus on preventing model denial, data breaches, or the manipulation of model outputs through adversarial user prompts.
4. Monitor
Establish real-time monitoring mechanisms to observe system behavior and evaluate control effectiveness. Use access logs, alerts, and audit trails to track anomalies or attempted exploitation. Continuous monitoring is essential for detecting threats such as insecure output, model denial of service, or backend failures before they escalate.
5. Control
Finally, implement overarching control measures to manage residual risk. These may include regular audits, compliance checklists, periodic training for security teams and data scientists, and system-level safeguards. Controls help enforce policies that keep your organization resilient in the face of evolving threats in LLM application security and web application security.
Challenges and Considerations of a Risk-Based Approach
While a risk-based approach to compliance offers significant advantages, it also presents important challenges and considerations that organizations must address to ensure its effectiveness.
1. Subjectivity in Risk Assessment
One major challenge lies in the subjective nature of evaluating risks. Without clear, standardized criteria, different teams or individuals may assess the same risk differently. This can lead to inconsistent prioritization, uneven application of controls, and confusion across the organization. Establishing a consistent risk evaluation framework is crucial to maintaining objectivity and alignment.
2. Rapid Changes in the Business Environment
The business environment, regulatory landscape, and operational risks can evolve quickly. New threats, regulatory updates, and organizational changes can make earlier risk assessments outdated. Organizations must have processes in place to continuously reassess and update risk evaluations to stay relevant and effective.
3. Resource Constraints
Implementing a risk-based approach often demands dedicated resources—time, skilled personnel, and technology. Smaller teams or organizations with limited budgets may find it difficult to conduct comprehensive risk assessments or implement tailored controls, leading to potential gaps in protection or compliance coverage.
4. Balancing High-Impact, Low-Probability Risks
Risk-based models may sometimes underemphasize rare but catastrophic events. Low-likelihood risks can still cause significant damage if realized. It is critical to ensure that the organization doesn’t solely prioritize based on frequency but also weighs the potential severity of impact when making decisions.
5. Organizational Resistance and Cultural Barriers
Adopting a risk-based approach often requires a shift in mindset across the organization. Departments may resist change if they perceive the process as bureaucratic or if they do not understand the value of prioritizing risk-driven compliance activities. Building a risk-aware culture, with clear communication and leadership support, is essential for success.
Final Thoughts
A risk-based approach helps organizations focus on the most important risks first. It allows teams to allocate resources based on actual threat levels and maintain compliance with regulatory requirements.
Regular risk evaluation keeps compliance strategies current and aligned with business goals. A deliberate and organized risk management process strengthens operational stability, protects critical assets, and improves overall resilience.
Get In Touch



