
SOC 2 Controls List for 2026
Starting a SOC 2 program means creating controls that fit your company’s goals, risks, and systems. These controls will vary depending on how your organization operates, the data you handle, and what your customers expect.
SOC 2 is based on five Trust Services Criteria, each tied to a specific type of risk. Knowing which controls apply helps you prepare for audits, handle vendor reviews, and keep your security practices in order.
This post outlines the main types of SOC 2 controls, how they connect to the criteria, and where to begin when building your list.
Download SOC 2 Controls List PDF
What Are SOC 2 Controls?
SOC 2 controls are the policies, procedures, and technical measures used to protect systems and data. They help reduce the risk of security risks, mistakes, or unauthorized access.

These controls are based on the SOC 2 Trust Services Criteria, which auditors use as a guide when assessing your organization.
Common examples include password rules, multi-factor authentication, logical access security measures, access permissions, and steps for onboarding and offboarding employees.
Each control supports your overall security program and helps meet the expectations of customers and service organizations.

SOC 2 Controls List
The SOC 2 controls framework is built around five Trust Services Criteria (TSC): Security, Availability, Processing Integrity, Confidentiality, and Privacy. These controls guide how a company protects systems and data and form the core of what auditors evaluate during a SOC 2 examination.
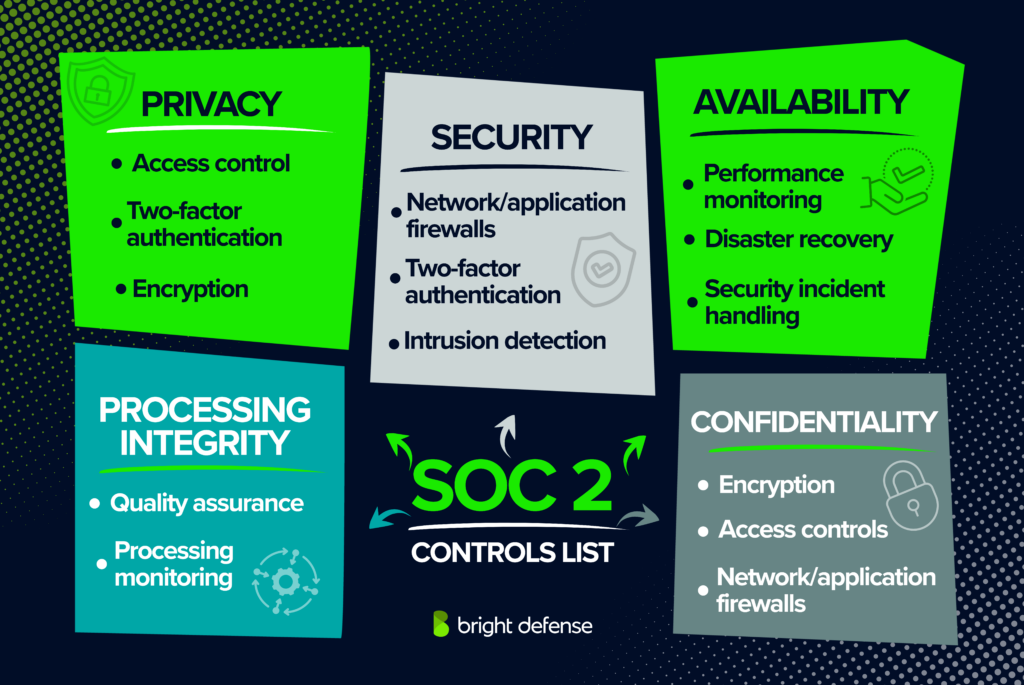
1. Security Controls
Security is the foundation of SOC 2. This category focuses on strong operational practices and defenses against both digital and physical threats. Controls in this section often include multi-factor authentication, web application firewalls, physical and virtual measures, and physical safeguards at server facilities.
Auditors also review indirect controls, such as hiring policies for security roles, to assess whether the organization has established the right environment for protecting confidential information.
Security is the foundation of SOC 2. These controls protect against both digital and physical threats.
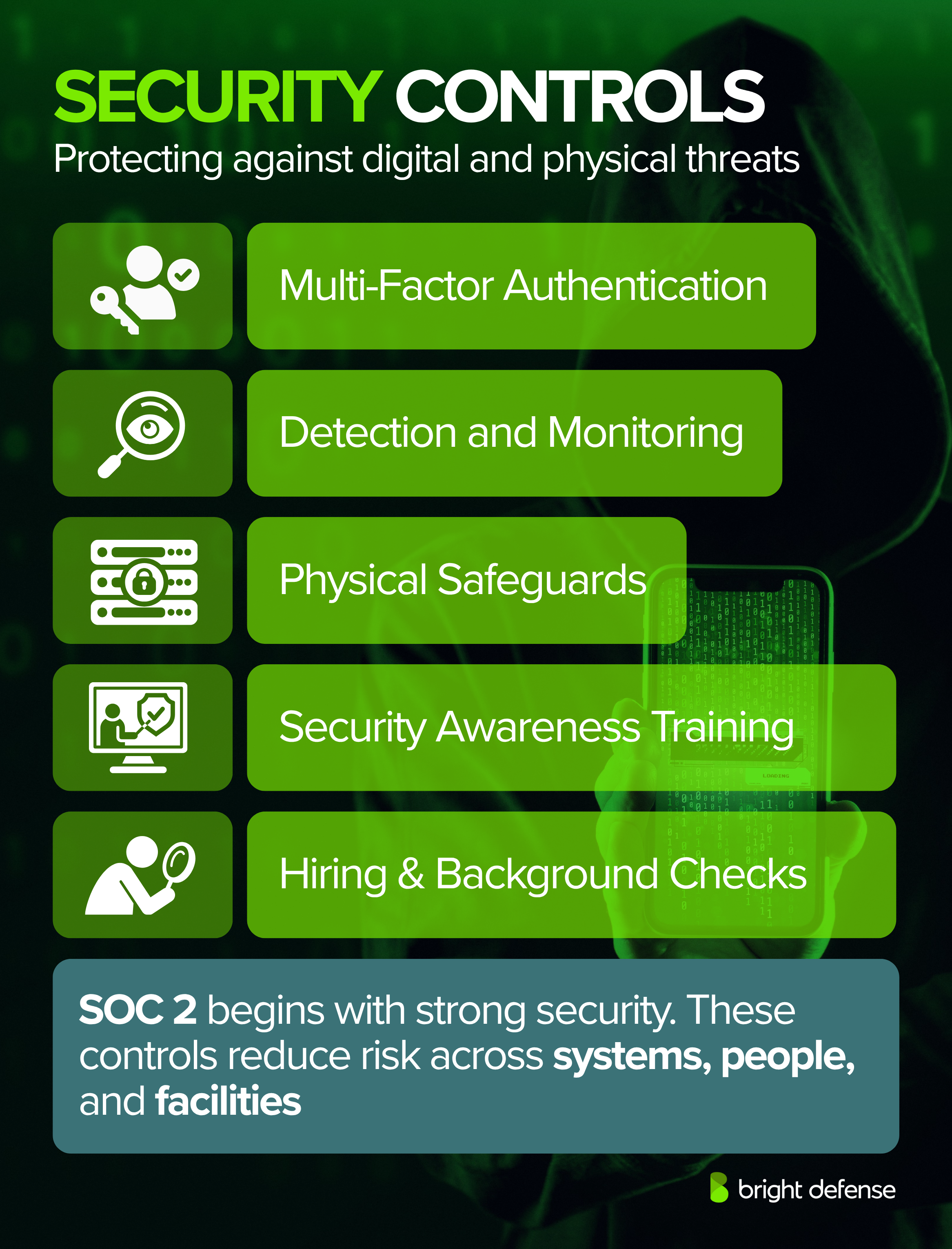
Examples include:
- Multi-factor authentication
- Web application firewalls
- Detection and monitoring procedures for unauthorized activity
- Physical safeguards for server rooms
- Hiring and background checks for staff in sensitive roles
- Security awareness training for all employees
2. Privacy Controls
Privacy controls apply to any customer data a company handles. Organizations must clearly communicate their privacy policies to individuals whose data they store.

These controls typically require organizations to:
- Obtain consent before collecting data
- Limit data collection to what is necessary
- Collect data through lawful methods
- Use data only for the purpose stated
- Dispose of data once it is no longer needed, following internal compliance process requirements
- Maintain documentation as part of internal control responsibilities
3. Confidentiality Controls
Confidential data often needs to be shared with trusted parties, for example, health information shared across hospitals and pharmacies. The goal here is not to block access entirely but to manage secure sharing with vetted business partners.
Controls focus on identifying confidential data, limiting unauthorized access, and securely disposing of it after a defined retention period. These safeguards help maintain trust services principles and support compliance efforts.
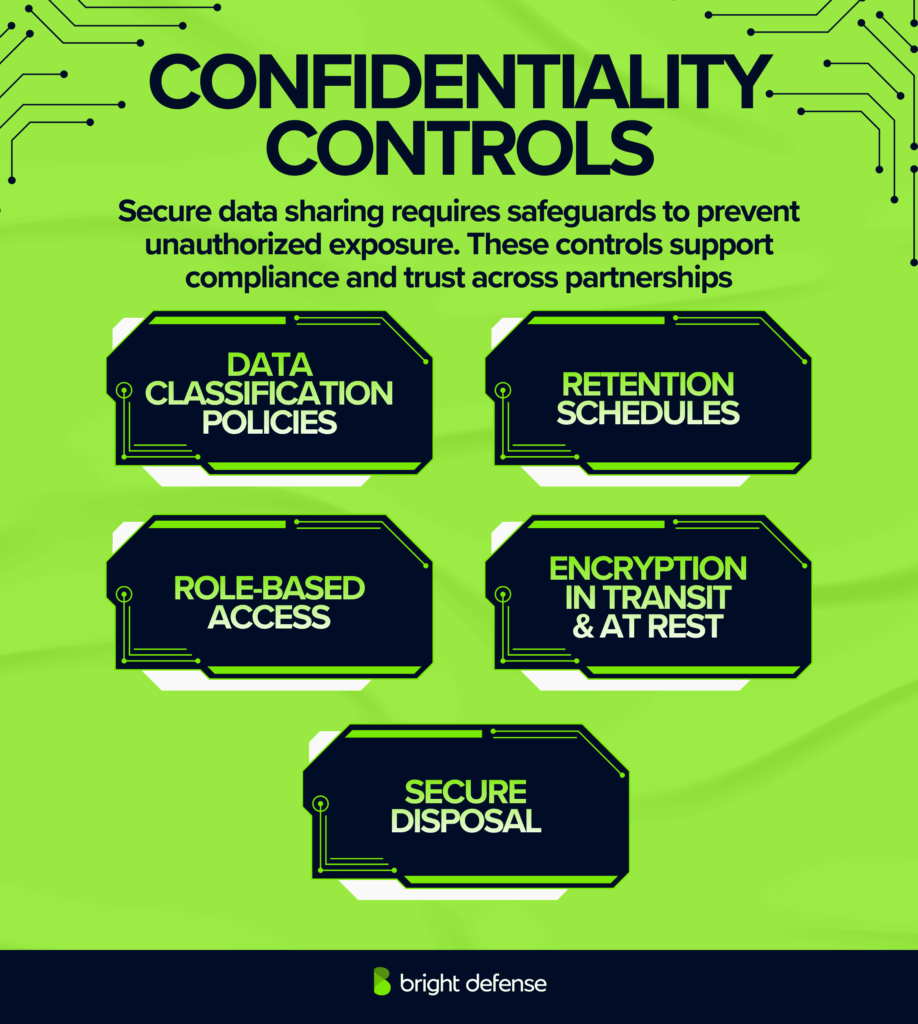
The goal of confidentiality controls is to allow secure sharing without exposing unauthorized users to that data.
Typical controls:
- Data classification policies
- Role-based access permissions
- Use of encryption at rest and in transit
- Secure disposal processes for confidential information
- Retention schedules for confidential data

4. Processing Integrity Controls
These controls address whether systems perform as intended. They focus on the accuracy, completeness, and reliability of system processing, especially when large volumes of data are ingested, processed, and exported. Effective controls help confirm that inputs and outputs align and that no data is lost or altered during processing.
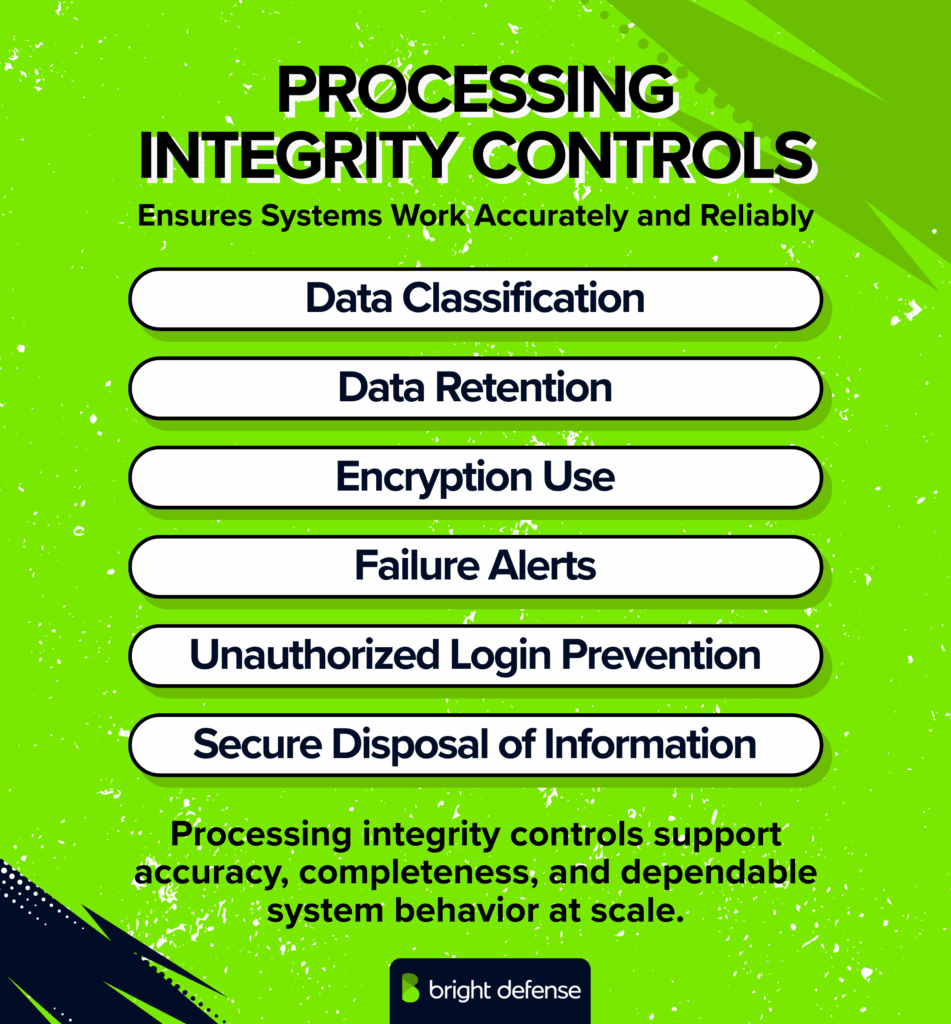
SOC 2 Processing Integrity Controls
Examples include:
- Timely error detection and correction during periods of high processing demand
- Input validation and sanity checks
- Monitoring data pipelines to verify inputs and outputs match expected results
- Reconciling processed data through automated checks and reporting
- Controls that prevent unauthorized system components’ logic changes
- Automated alerts for processing failures
5. Availability Controls
Availability controls aim to reduce downtime and maintain reliable service delivery. These are critical for SaaS platforms and cloud providers. This category also involves input from senior management when defining acceptable recovery objectives and allocating resources.
Typical controls include:
- Secure backup procedures
- Disaster recovery plans
- Business continuity plans
- Environmental risk management assessments
- Predictive capacity planning as part of a formal readiness assessment
Control Categories in SOC 2
SOC 2 controls are also grouped into functional categories that support the five TSCs. These include:
1. Control Environment
- Encourages ethical behavior and integrity
- Involves senior leadership and the board in oversight
- Assigns clear responsibilities for controls
2. Communication and Information (CC2)
- Documents policies and procedures clearly
- Communicates data-handling expectations to staff and third parties
- Ensures timely sharing of incident updates and risk alerts
3. Risk Assessment (CC3)
- Regularly evaluates new risks to security and compliance
- Identifies internal and external threats
- Considers the impact of system changes or new services
4. Monitoring Activities
- Tracks control performance over time
- Flags control failures or policy violations
- Shares findings with stakeholders
5. Logical and Physical Access Controls
- Manages user credentials and system permissions
- Uses strong authentication methods
- Restricts physical access to hardware
6. System and Operations Controls
- Logs security events and monitors for anomalies
- Responds to system incidents
- Maintains change logs and version control
7. Change Management Controls
- Requires documented approvals for all code or system changes
- Tests updates in a staging environment
- Tracks who made changes and when
8. Risk Mitigation Controls
- Supports recovery from business disruptions
- Maintains vendor risk assessment practices
- Includes monitoring and contract terms for third-party vendors
Common Criteria (CC-Series)
The Security category includes nine Common Criteria (CC1–CC9), which apply across all TSCs.
- CC1: Control Environment
- CC2: Communication and Information
- CC3: Risk Assessment
- CC4: Monitoring Activities
- CC5: Control Activities
- CC6: Logical and Physical Access Controls
- CC7: System Operations
- CC8: Change Management
- CC9: Risk Mitigation
Each criterion represents a layer of control maturity and helps shape an auditor’s opinion on whether your environment meets SOC 2 standards.

How Bright Defense Can Help?
Bright Defense helps organizations meet SOC 2 requirements through a complete compliance support system. The team performs readiness assessments to spot gaps, builds detailed security controls, and prepares all documentation needed for the audit. We guide clients through every stage, from defining scope and writing policies to gathering evidence and coordinating with auditors.
With CISSP and CISA certified experts, Bright Defense provides ongoing monitoring, risk reviews, and policy updates so that compliance stays current beyond certification. Their goal is to make SOC 2 achievable and sustainable with practical, clear processes and hands-on support.
FAQs
There is no fixed number. Most audits include 60 to 100 controls depending on which trust services principles you include and how complex your systems are. Security is always required, and adding more criteria increases the number of controls.
Internal controls are the policies, procedures, and systems used to meet SOC 2 requirements. These can include approval processes, access restrictions, and training programs that help protect customer data and support compliance.
SOC 1 addresses controls that impact a client’s financial reporting. SOC 2, on the other hand, covers areas like data security, system availability, confidentiality, privacy, and integrity. This type is more common among technology and cloud service providers that need to show operational effectiveness.
There is no official checklist. The AICPA offers points of focus for each Trust Services Criteria to help organizations decide how to meet each requirement. These are not mandatory but serve as useful guidance during audits.
A common example is reviewing your information security policy annually to confirm it addresses responsibilities, legal requirements, and security objectives. This shows that the policy remains relevant and effective.
Only the Security category is required. The others, Availability, Confidentiality, Processing Integrity, and Privacy, are optional. You select the ones that apply to your service and your customers’ expectations.
If your controls do not meet SOC 2 standards, the auditor may issue a qualified or adverse opinion. This highlights control gaps that need attention and can affect customer trust or delay business agreements.
SOC 2 compliance is not legally required. However, many customers expect it, especially in cloud or B2B environments. A clean SOC 2 report helps show that your systems follow strong security practices.
A SOC 2 Type I audit typically takes 1 to 3 months, depending on how prepared your team is. A Type II audit takes longer—usually between 3 to 12 months, because it covers how controls perform over time, usually across a 3 to 12 month review window.
The SOC 2 framework is based on 5 Trust Services Criteria. These break down into 64 individual criteria that form the basis of the auditor’s evaluation. Most of these criteria are contained within the Security category, also called the Common Criteria (CC1 through CC9).
Costs vary depending on your company size and audit scope. A SOC 2 Type I audit usually costs between $20,000 and $40,000. A Type II audit ranges from $30,000 to over $100,000, especially for larger organizations with multiple TSCs or complex environments.
On average, a SOC 2 audit involves gathering 200 to 300 pieces of evidence. This can include policy documents, system screenshots, logs, onboarding records, access reviews, and more. Auditors use this evidence to test both the design and operating effectively of your controls.
Based on industry trends, more than 70 percent of SOC 2 reports now include controls that address third-party vendor risk. Auditors often look for vendor risk assessments, contract clauses, and monitoring practices to confirm that data shared with vendors remains protected. This typically includes oversight of both physical and virtual measures vendors use to manage data.
Get In Touch



