
SOC 2 vs SOC 3 – What’s the Difference?
You’ve probably come across SOC reports while researching how to show customers or partners that your company takes security seriously. There are a few types: SOC 1, SOC 2, and SOC 3. It can get a little confusing figuring out which one fits your needs. Most organizations focus on SOC 2, but SOC 3 appears in conversations as well. So how do you know when to choose one over the other?
In this post, we will set SOC 1 aside and focus only on SOC 2 and SOC 3. You will see how they differ, what each one covers, and why your business might choose one depending on your goals and audience.
Key Takeaways
- SOC 2 gives technical, private details for customer reviews; SOC 3 is a short public summary.
- Both use the same audit and follow the same five Trust Services Criteria.
- SOC 2 is for due diligence and vendor reviews; SOC 3 is for marketing and public trust.
- SOC 2 costs more due to control testing; SOC 3 adds minimal cost.
- Only licensed CPA firms can issue these reports, and most companies that get SOC 2 also request SOC 3.
SOC 2 and SOC 3 Definitions
SOC 2 and SOC 3 reports follow standards from the American Institute of Certified Public Accountants (AICPA). Both are used to evaluate how a company protects customer data. If your business stores, processes, or handles client information, especially in SaaS, cloud services, or IT, you will likely need one or both reports, particularly if you’re acting as a service organization for clients managing regulated or financial reporting obligations.
Both reports use the same framework, called the AICPA Trust Services Criteria. These include five categories:
- Security
- Availability
- Processing Integrity
- Confidentiality
- Privacy
SOC 2 Overview
Every SOC 2 report includes Security. The others are optional depending on what your customers expect or what your services promise. To complete a SOC 2, an independent auditor reviews your systems and policies to check whether your security controls are working as claimed and aligned with your company’s overall security posture.

SOC 2 reports provide detailed information, including technical descriptions, control testing results, and audit findings. Organizations share these reports privately, typically with customers or prospects under NDA, and do not publish them publicly. Teams use SOC 2 as a final report to prove internal controls during compliance or procurement reviews.
SOC 3 Overview
SOC 3 reports are different. They are based on the same controls as SOC 2 but are much shorter and less technical. You can share a SOC 3 with anyone. Organizations use it publicly and often post it on their websites to show they passed a formal review of their data protection efforts. These reports also serve marketing purposes, helping build trust with a broader audience.

SOC reports are now common across many industries. Many enterprise clients ask for a SOC 2 before moving forward with contracts. AICPA trend data shows consistent growth in SOC 2 audits, especially in cloud and B2B tech sectors.
If your company handles data security responsibilities and works with larger clients, a SOC 2 shows that your internal controls meet industry expectations and support SOC compliance. A SOC 3 gives you a public-facing version to help show credibility without revealing sensitive system details, often reviewed by service organization’s management for external communication.
Similarities and Differences Bteween SOC 2 and SOC 3
Both SOC 2 and SOC 3 reports are based on the AICPA Trust Services Criteria, which include:
- Security
- Availability
- Processing Integrity
- Confidentiality
- Privacy
They use the same audit process. A third-party auditor evaluates whether a company’s systems and controls meet the selected criteria.
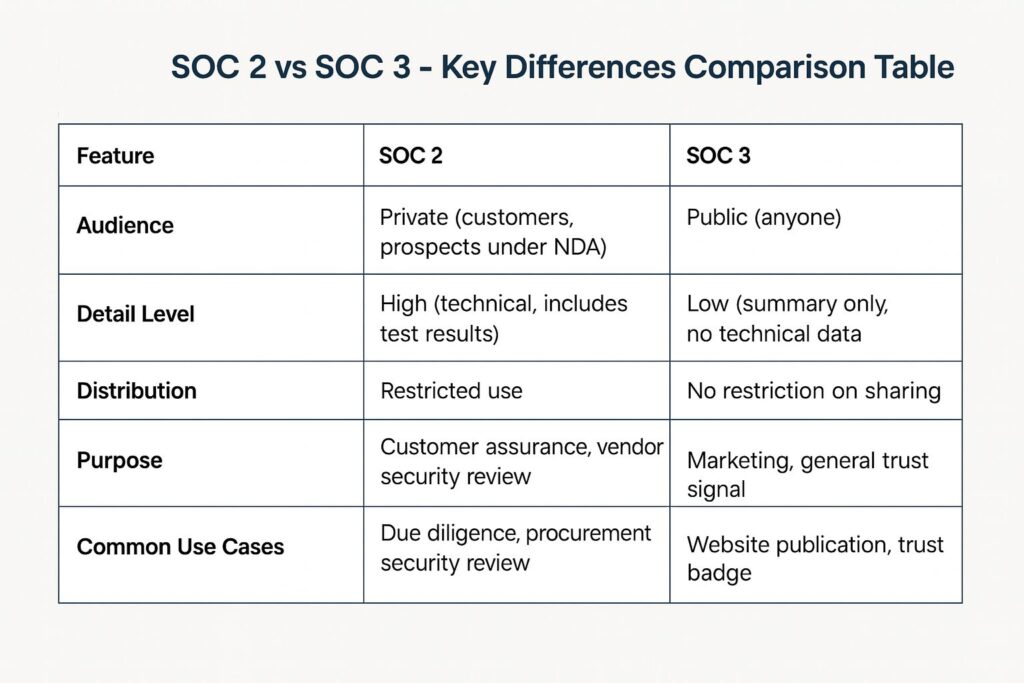
SOC 2 vs SOC 3 – Key Differences Comparison Table
| Aspects | SOC 2 | SOC 2 |
|---|---|---|
| What It Is | Audit report on data security, confidentiality, privacy, processing integrity, availability | Public summary of SOC 2 controls |
| What It Covers | Internal controls that protect customer data | Same SOC 2 controls, but presented in a simplified, non-technical format |
| Who Needs It | Organizations that handle, store, or transmit customer data (e.g., SaaS, cloud providers) | Organizations that want to show proof of security compliance to the general public |
| Who Uses It | Clients, regulators, management (under NDA) | General public |
| Who Requests It | Customers, partners, internal compliance teams | No formal requester — used for marketing or public trust |
| Evaluation Timeline | Type I: At a single point in timeType II: Over a defined period | Always Type II: Based on controls over a defined period |
| When to Get It | When handling customer data and needing to meet vendor or regulatory requirements | When public assurance is needed, without disclosing full control details |
| Reporting | Detailed report (requires NDA) | General-use report (does not require NDA) |
| Reporting |
Practical Example
If a potential customer wants to review your access controls, encryption practices, or how you monitor systems, they will request a SOC 2 report. This report includes those details and shows how they were tested.
If you want to show website visitors or press that your company has passed a third-party audit without disclosing internal systems, you provide a SOC 3. It confirms the result but skips the specifics.
Summary
- SOC 2 is meant for deeper reviews and is shared under strict conditions.
- SOC 3 is meant for public use and acts as a simplified version of the SOC 2.
- Both prove that your controls meet industry standards, but only SOC 2 includes the evidence behind it.
Price Differences Between SOC 2 vs SOC 3
The cost difference between SOC 2 and SOC 3 reports is minimal because both come from the same audit process. SOC 3 is simply a summarized version of SOC 2, meant for public sharing.
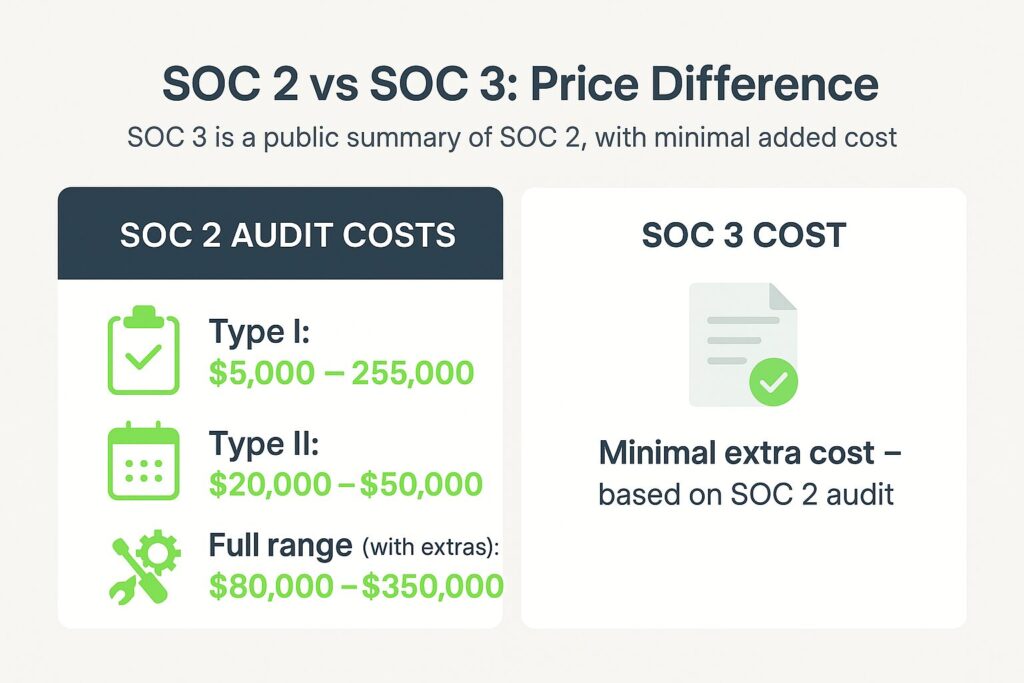
SOC 2 Audit Costs
SOC 2 audits are detailed and can be expensive. The price depends on the size and complexity of the company, the number of systems involved, and how many trust categories are included.
- SOC 2 Type I: Evaluates controls at a specific point in time. Costs typically range from $5,000 to $25,000.
- SOC 2 Type II: Assesses the effectiveness of controls over a period (usually 3 to 12 months). Costs often range from $20,000 to $50,000.
Additional costs may include readiness assessments, remediation, and compliance tools. With all factors included, total expenses can range between $80,000 and $350,000.
SOC 3 Report Costs
A SOC 3 report uses the results of the SOC 2 audit. It does not require a separate audit or testing process. Because of this, the extra cost to produce a SOC 3 is usually small. Some audit firms include it as part of the SOC 2 package, or charge a minor fee for formatting and issuing the public version.
Summary
- SOC 2 is the primary cost driver due to its depth and control testing.
- SOC 3 adds little or no extra cost, since it’s derived from the same audit.
- Most companies that produce SOC 2 reports also request a SOC 3 to serve public audiences without disclosing sensitive information.
Who Can Perform SOC 2 and SOC 3 Reports?
Only independent CPA (Certified Public Accountant) firms or firms authorized by the American Institute of Certified Public Accountants (AICPA) can conduct SOC 2 and SOC 3 audits and issue the official reports.

These firms must follow the AICPA’s Statement on Standards for Attestation Engagements (SSAE 18) guidelines and assess compliance with the AICPA’s Trust Services Criteria.
To issue either a SOC 2 or SOC 3 report, the auditor must:
- Hold an active CPA license
- Be trained in SOC reporting standards and Trust Services Criteria
- Follow AICPA audit methodology and quality control requirements
- Maintain independence from the company being audited
The auditor can work directly for a CPA firm or be part of a cybersecurity-focused advisory group partnered with a licensed CPA firm. These evaluations result in restricted use reports for SOC 2 or general use reports for SOC 3, depending on the report type and distribution intent.
Why Customers Request SOC 2 Reports
SOC 2 reports are designed for customers who need detailed insight into how your company secures its systems and handles data. They request these reports to:

- Evaluate Risk: Security, availability, and confidentiality controls directly affect business risk. A SOC 2 report helps customers decide if your systems are safe to use and supports confidence in your information security practices.
- Meet Internal Compliance: Many organizations have internal or regulatory requirements (such as HIPAA, PCI, or GDPR) that demand proof of vendor controls, especially when handling financial information or regulated workloads.
- Review Specific Controls: SOC 2 includes detailed testing results, control descriptions, and evidence of how your company operates over time. Customers may want to verify practices like access control, encryption, and incident response, especially if you’re dealing with sensitive data.
- Satisfy Procurement Checklists: For enterprise buyers, SOC 2 is often a box to check during security due diligence before contracts are signed. A readiness assessment can also help prepare for these evaluations.
- Avoid Additional Audits: A strong SOC 2 can reduce the need for separate security questionnaires or site visits, saving time for both sides and demonstrating your organization’s ability to maintain strong controls.
Why Customers Request SOC 3 Reports?
SOC 3 reports are requested less often, but they still provide value in certain cases:
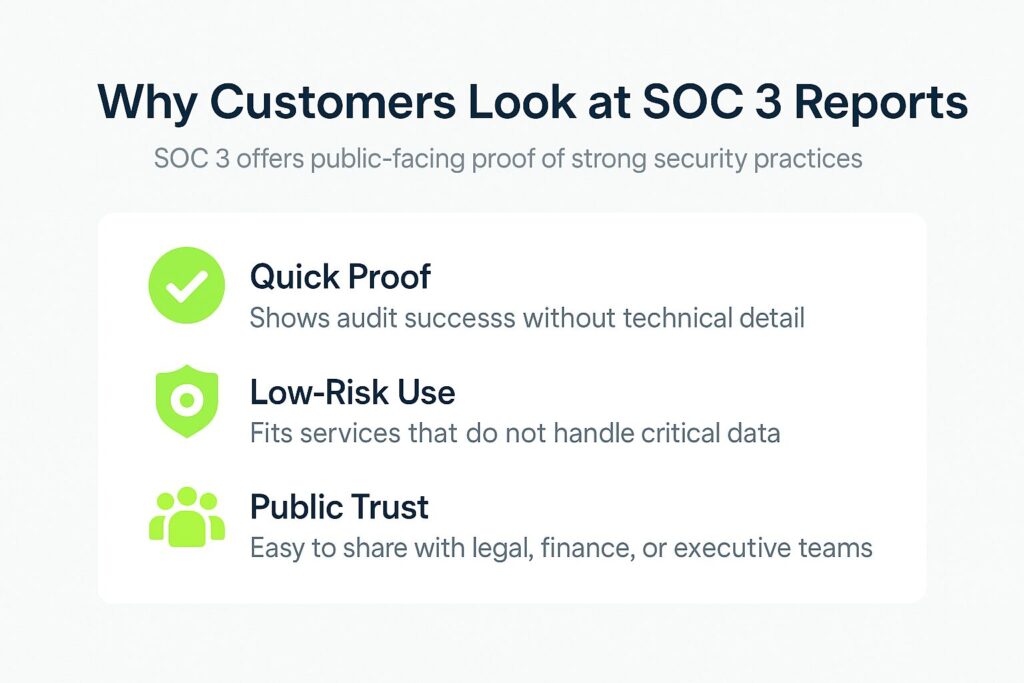
- Quick Assurance: A customer may want fast proof that your company passed a SOC audit without reviewing technical details.
- Low-Risk Partnerships: When the service does not involve critical data or infrastructure, a SOC 3 may be enough. These cases often apply to companies that offer services not tied to regulated systems.
- Public Credibility: Non-technical stakeholders such as legal, finance, or executive teams can review SOC 3 reports to assess a company’s trustworthiness. Companies that focus on transparency in their marketing use SOC 3 as a helpful trust signal.
SOC 2 vs SOC 3: Final Take
SOC 2 and SOC 3 reports serve different purposes. SOC 2 provides detailed, private insights into your security controls. SOC 3 offers a high-level summary you can share publicly. Both help build trust, but they’re used in different ways depending on the audience.
Bright Defense helps you decide which report fits your needs and guides you through the audit process. We connect to your systems, monitor for risks, and help you stay prepared with less manual work. Our process supports both service providers handling sensitive information and organizations preparing reports for the general public.
Ready to get started? Reach out to Bright Defense to begin your compliance automation and SOC reporting.
FAQs
SOC 2 reports provide detailed information about an organization’s controls related to security, availability, processing integrity, confidentiality, and privacy. They are intended for restricted use by stakeholders with a thorough understanding of the system. In contrast, SOC 3 reports offer a high-level summary of the same information and are designed for general public distribution.
SOC 2 reports are meant for specific stakeholders such as customers, partners, and regulators who require detailed insights into an organization’s controls. SOC 3 reports are intended for a broader audience, including potential customers and the general public, providing assurance about the organization’s controls without disclosing sensitive details.
No, a SOC 3 report cannot be issued independently. It is derived from the results of a SOC 2 Type II audit and serves as a summarized version suitable for public distribution.
Both SOC 2 and SOC 3 reports evaluate controls based on the Trust Services Criteria, which include:
- Security
- Availability
- Processing Integrity
- Confidentiality
- Privacy
These criteria assess how well an organization manages and protects data.
Yes, SOC 2 reports are divided into two types:
- Type I: Assesses the design of controls at a specific point in time.
- Type II: Evaluates the operational effectiveness of controls over a defined period, typically ranging from 3 to 12 months.
SOC 3 reports are only available as Type II, reflecting the operational effectiveness over time.
Organizations may obtain both reports to address different stakeholder needs. SOC 2 reports provide detailed information required by customers and regulators, while SOC 3 reports offer a general overview suitable for public sharing, such as on a company’s website.
SOC 2 reports contain detailed descriptions of the organization’s systems, controls, and the results of the auditor’s testing. SOC 3 reports, however, present a summarized version without specific details, focusing on the overall effectiveness of controls.
SOC 2 reports are restricted and typically shared under non-disclosure agreements due to the sensitive information they contain. SOC 3 reports are designed for public distribution and can be freely shared without confidentiality concerns.
Only independent Certified Public Accountant (CPA) firms or firms authorized by the American Institute of Certified Public Accountants (AICPA) can conduct SOC 2 and SOC 3 audits and issue the official reports.
The choice depends on the organization’s objectives and stakeholder requirements. If detailed information is needed for due diligence or regulatory compliance, a SOC 2 report is appropriate. For general assurance to the public without disclosing sensitive details, a SOC 3 report is suitable.
In a SOC 2 Type II audit, auditors use statistical or non-statistical sampling to test the operating effectiveness of controls over a period. For example, instead of examining all 10,000 user access changes in a year, an auditor might select a statistically significant sample of 100 changes. By examining this sample, they can infer the effectiveness of the access control process for the entire population and quantify the potential rate of deviation.
There is no universally defined “acceptable” error rate. The tolerable rate of deviation is determined by the auditor based on professional judgment and factors like the criticality of the control and the overall risk assessment. A single failure in a critical control (e.g., a firewall configuration error) might be significant, whereas a higher number of minor errors in a less critical control (e.g., delayed termination of a non-sensitive account) might be acceptable. Any deviations are analyzed to determine if they represent a control failure.
Auditors collect and analyze a wide range of data as evidence. This includes:
- System logs: Access logs, change logs, security event logs.
- Configuration data: Firewall rules, user access lists, system settings.
- Human resources data: New hire lists, termination lists, training records.
- Documentation: Policies, procedures, incident response plans. This evidence is analyzed to verify that controls are designed appropriately and have operated effectively as described by the organization.
The Processing Integrity Trust Services Criterion is focused on ensuring that data processing is complete, valid, accurate, timely, and authorized. To test this, auditors examine data from input to output. For instance, they might trace a sample of financial transactions through a system, analyzing system calculations, data transformations, and reports to ensure the integrity of the data has been maintained throughout the processing lifecycle.
Yes, auditors increasingly use data analytics to enhance SOC audits. Instead of just sampling, analytics tools can be used to analyze entire populations of data for anomalies or patterns of interest. For example, an auditor could analyze all user access logs for an entire year to identify access outside of normal business hours or repeated failed login attempts, providing a more comprehensive view of control effectiveness than traditional sampling alone.
Get In Touch



