
10 Steps to Prevent Data Exfiltration
The global market for data exfiltration prevention and response reached $69.7 billion in 2021 and is expected to hit $217.5 billion by 2031, with a projected annual growth rate of 12.3%.
That growth reflects how quickly data theft has become a critical issue for organizations of every size. Security teams face daily threats from insiders, external attackers, and compromised tools. Attackers do not need to break systems; they only need to quietly extract sensitive information without setting off alarms.
This blog covers 10 practical steps that help reduce data exfiltration risks without adding unnecessary complexity. Each one focuses on actions that teams can take using existing tools, policy updates, or simple monitoring improvements.
Key Takeaways
- The threat is growing. The data exfiltration prevention market is projected to grow from $69.7B in 2021 to $217.5B by 2031.
- Attacks are often silent. Data is frequently stolen without triggering alerts, using email, cloud apps, or compromised accounts.
- Risks come from many sources. External attackers, insiders, and careless users all contribute to data loss.
- Small changes help. Tools like DLP, stricter permissions, endpoint controls, and better training can block many threats.
- Layered defenses work. No single fix solves it all, but combining monitoring, audits, and access control raises the bar for attackers.
What is Data Exfiltration?
Data exfiltration refers to the unauthorized transfer of data from a computer or network. This activity is typically carried out by a cybercriminal, an insider, or malware that has infiltrated a system. It is often part of a broader security breach and is sometimes referred to as “data theft” or “data leakage.”
Data exfiltration usually happens in two ways:
- Manual Exfiltration: A malicious insider or intruder actively copies data using tools like USB drives, emails, or file transfers.
- Automated Exfiltration: Malware or scripts run in the background, quietly extracting data over time through external channels like FTP, cloud services, or command and control servers.
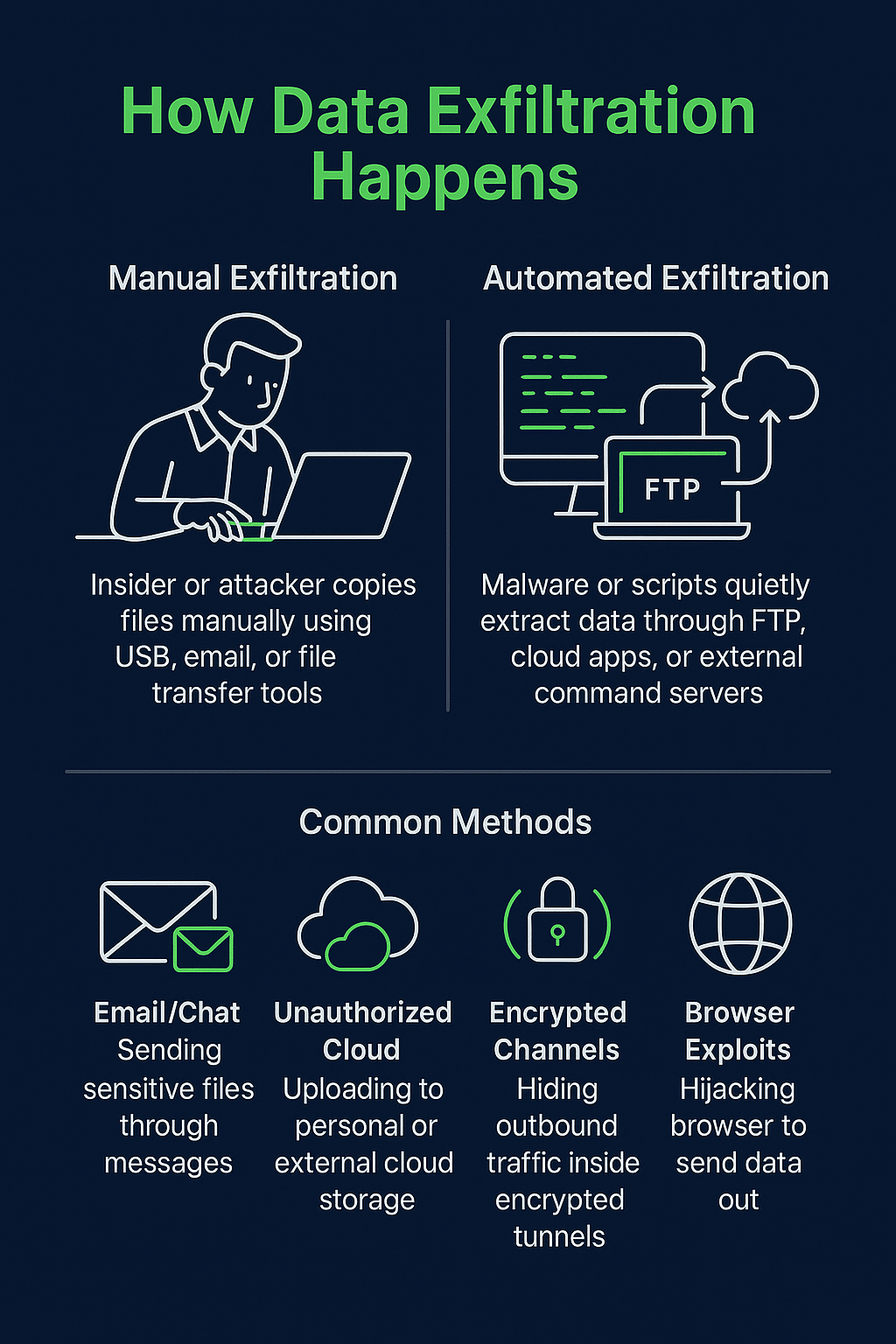
Common methods include:
- Sending files via email or chat apps.
- Uploading files to unauthorized cloud storage.
- Using encrypted channels to hide outgoing data.
- Exploiting browser vulnerabilities to transmit data.
How to Prevent Data Exfiltration
Data exfiltration involves the unauthorized transfer of sensitive data. Preventing it requires targeted steps that block risky actions, detect unusual behavior, and limit who can access critical information. Below are key methods that help reduce this risk:
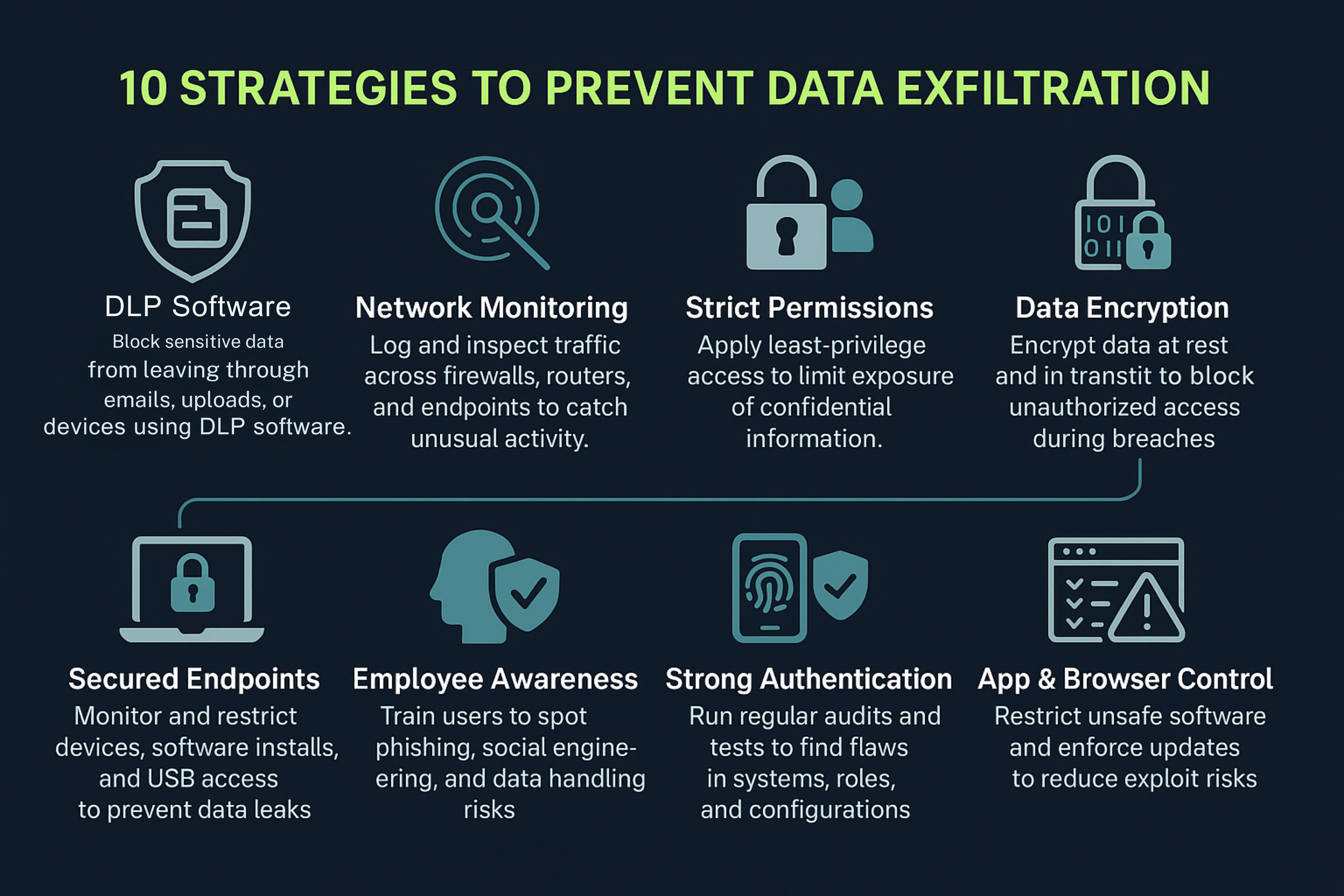
1. Implement Data Loss Prevention (DLP) Solutions
Data Loss Prevention (DLP) involves using software to detect, monitor, and block the movement of sensitive data outside authorized boundaries. It focuses on preventing leaks of personal, financial, and confidential business information, whether through email, cloud apps, or physical devices.
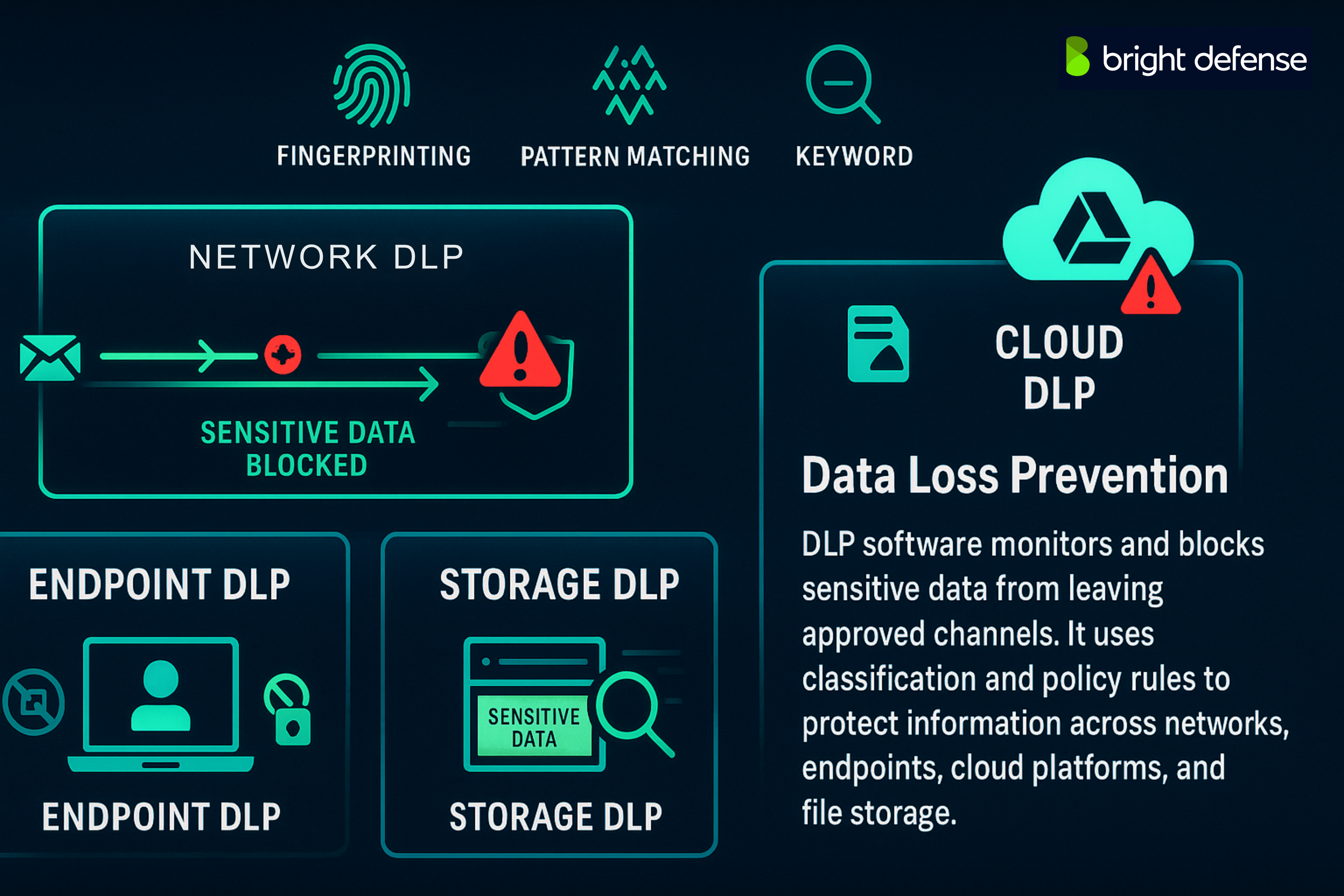
DLP tools classify data using pattern matching, fingerprinting, and keyword rules. Once classified, policies are applied to control how that data is handled. For example, rules can block the sending of credit card numbers via email or prevent uploads to unapproved cloud storage. Logs are generated for every policy action, helping with audits and investigations.
DLPs are of different kinds:
- Network DLP checks data moving through the internet, like emails or websites.
- Endpoint DLP monitors devices, watching for things like USB use or screen captures.
- Cloud DLP connects with services like Google Drive or Dropbox.
- Storage DLP scans servers and shared folders to find exposed data.
2. Strengthen Network Monitoring
Network monitoring means keeping an eye on all data moving through your systems. This helps you catch unusual activity, like someone trying to steal data, access things they shouldn’t, or move through your network unnoticed.
Monitoring begins with logging network activity at multiple points, such as: ‘
- Firewalls
- Routers
- Switches
- Endpoints
Analysts or automated systems review this traffic to identify spikes in volume, connections to unknown IP addresses, or transfers involving sensitive files at odd hours. These patterns often point to suspicious behavior that needs further investigation.
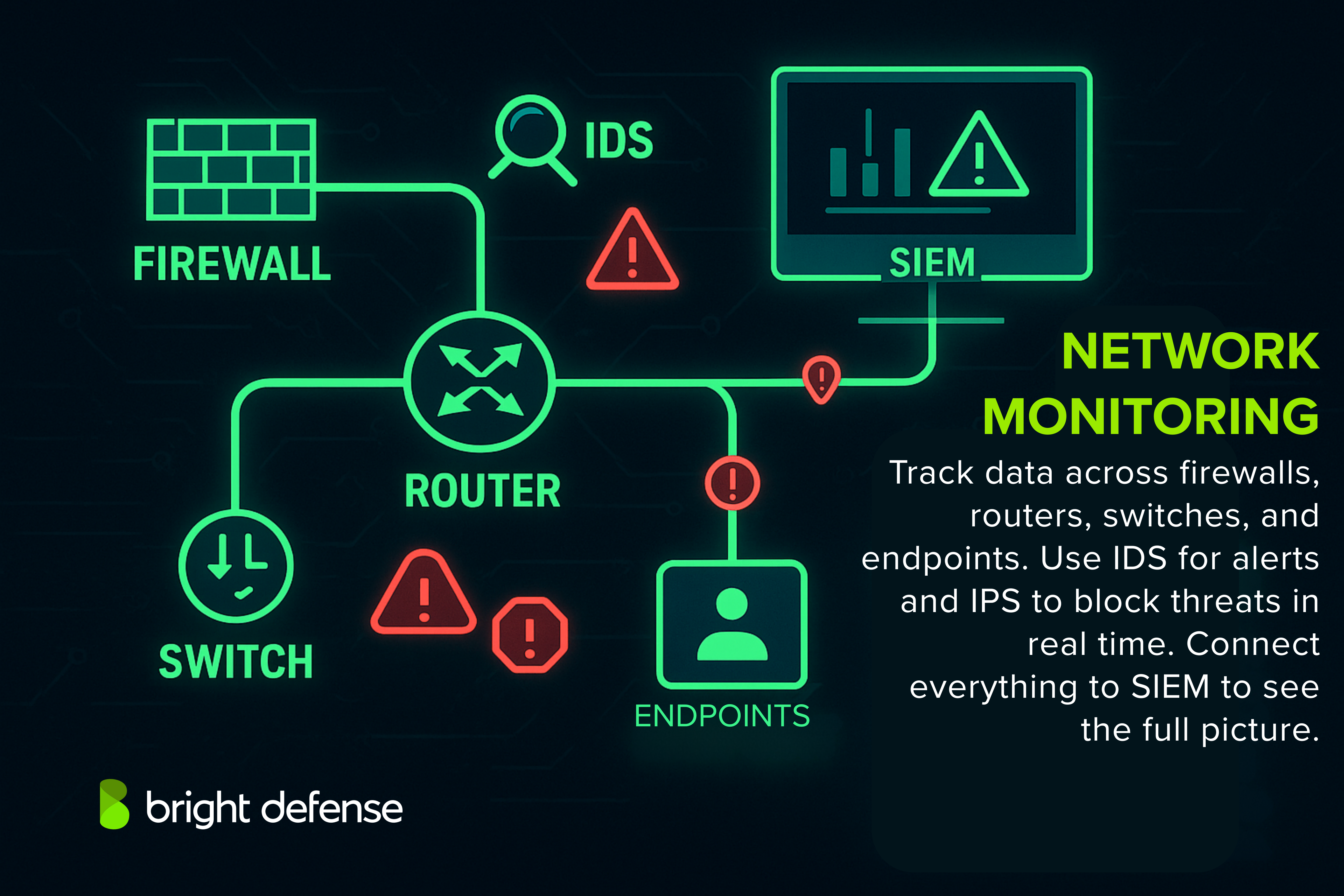
Intrusion Detection Systems (IDS) play a key role by passively analyzing network traffic and alerting when known attack signatures or unusual behaviors are detected.
They work well for identifying reconnaissance attempts, malware activity, or policy violations. Intrusion Prevention Systems (IPS) take it a step further. They operate inline and actively block malicious traffic in real time, such as dropping packets associated with known exploits or halting unauthorized data transfers.
Both IDS and IPS need to be set up with current threat information and adjusted to match your usual network activity. If they’re not tuned well, they might send too many false alerts and overwhelm your team. Connecting them to a SIEM system helps bring all the alerts and logs together, so security teams can see the full picture.
3. Limit Access with Strict Permissions
Limiting access with strict permissions means controlling who can view or interact with sensitive data. This follows the principle of least privilege, where each user, application, or system is given only the minimum access needed to perform its function. Narrowing access reduces the chances of accidental exposure or intentional misuse. Users typically do not need full administrative rights to complete routine tasks, and backend systems should not be open to broad internal traffic unless specifically required.
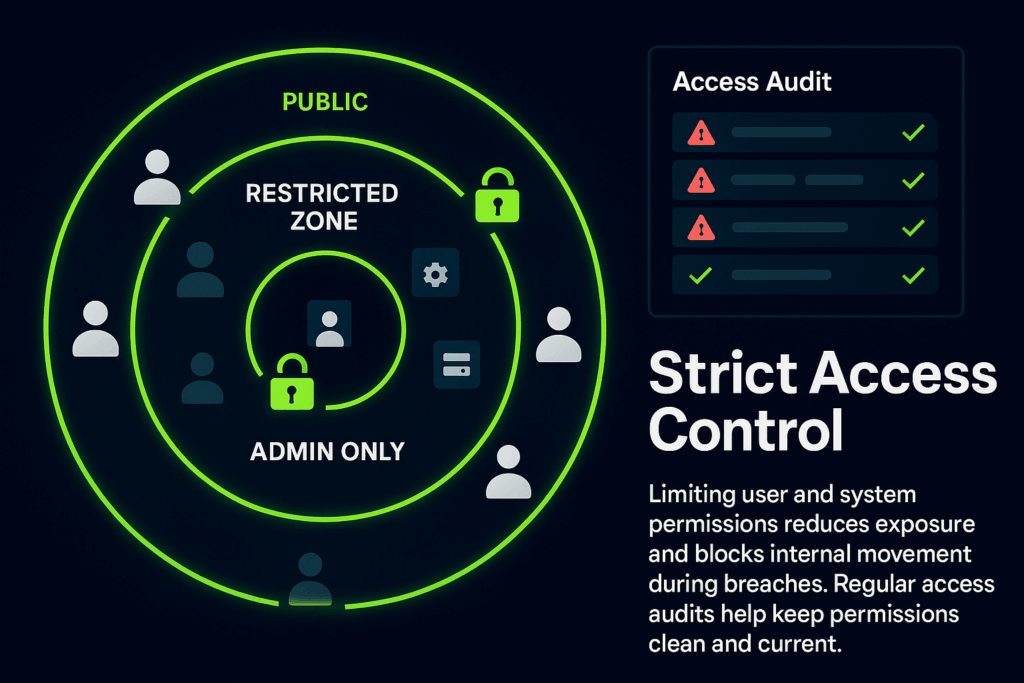
Regular audits of access rights are necessary to keep this standard in place. Over time, users might switch roles or leave the organization, yet their access may remain unchanged without proper review. These audits help reveal accounts with:
- Outdated or excessive privileges
- Misconfigured roles
- ‘’Temporary” access that was never removed
Eliminating these unnecessary permissions reduces the attack surface and limits the internal routes an intruder could take after gaining access.
4. Encrypt Sensitive Data
Encryption protects data from unauthorized access by converting readable information into a scrambled format that only a valid key can decode. This applies to data in two states:
- At rest: Encrypting stored files prevents access if a device or server is stolen.
- In transit: Encrypting data during transfer blocks interception attempts across networks.
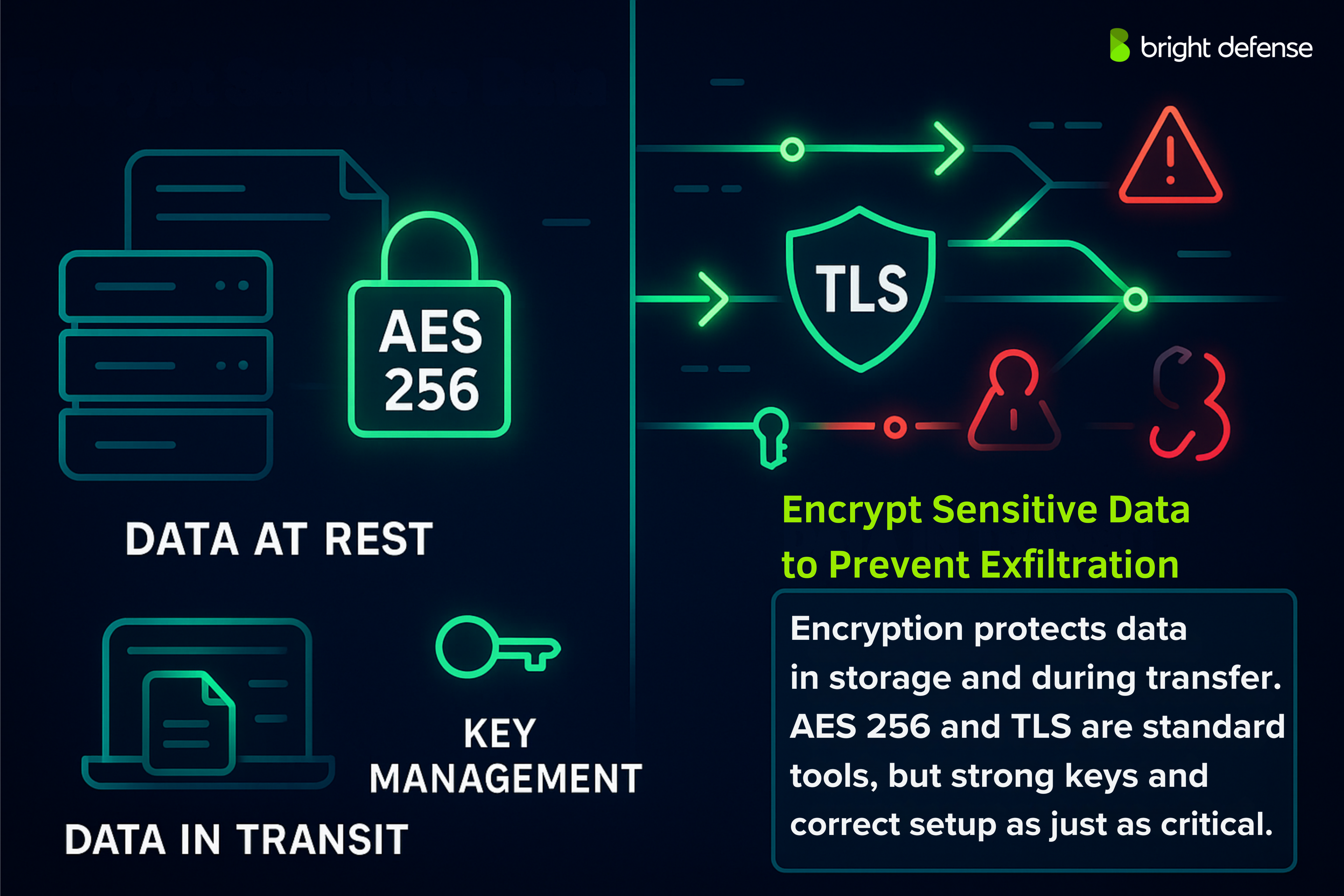
Strong encryption protocols are essential to this protection. AES 256 is widely used for encrypting files and storage systems because of its reliability and speed. For data moving across networks—such as emails, web sessions, or file transfers, Transport Layer Security (TLS) provides a secure communication tunnel between sender and receiver.
Both encryption methods must be set up correctly. Weak configurations or poor key management can lead to exposure of decrypted data even when encryption is in place.
5. Secure Endpoint Devices
Endpoints such as laptops, desktops, phones, and tablets are frequent targets for threats and require close protection. Unauthorized devices like USB drives are often used for manual data exfiltration, so it is important to:
- Restrict or disable USB access where possible
- Allow only approved, encrypted removable storage when necessary
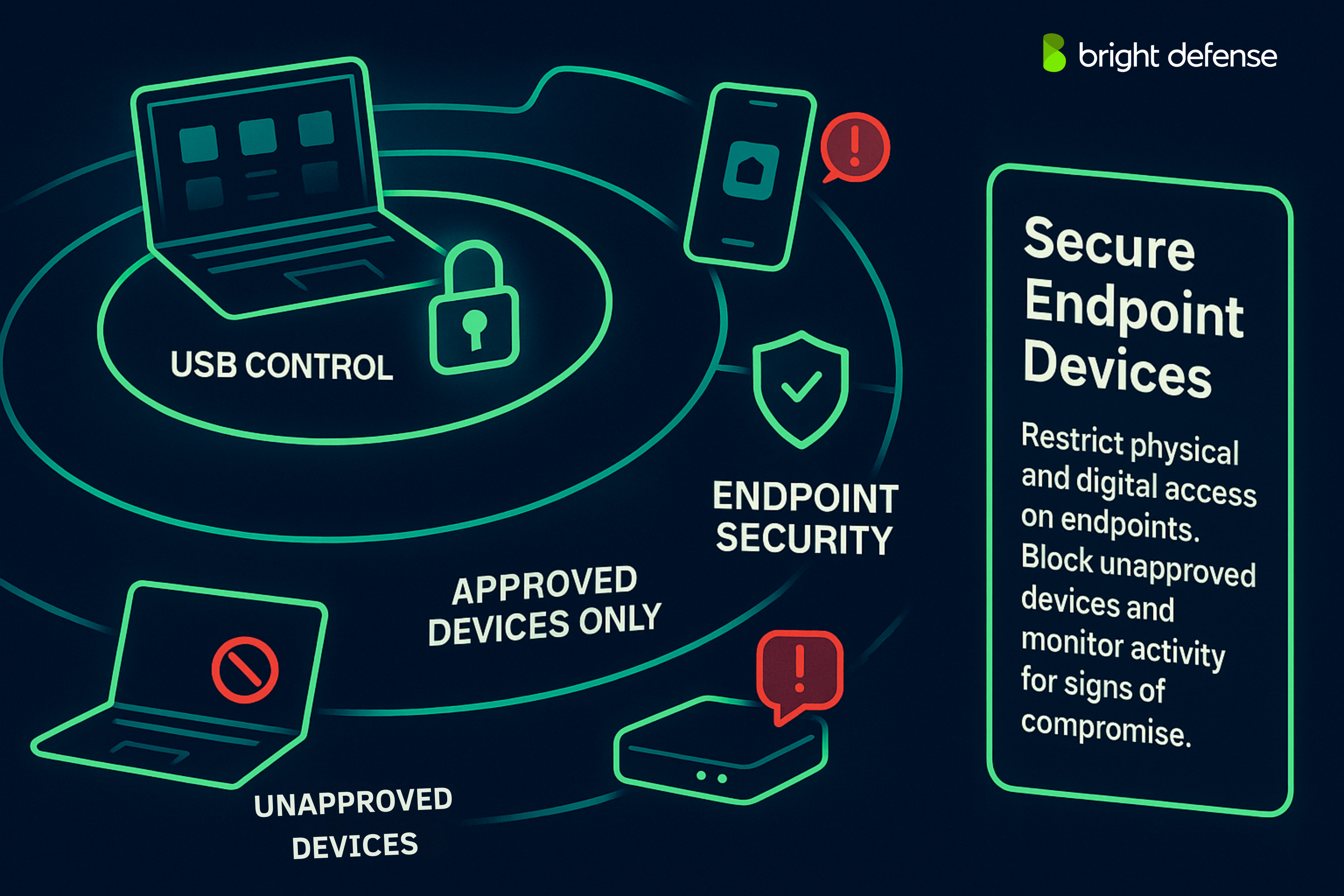
Beyond hardware controls, endpoint security software monitors device activity for signs of compromise. This includes detecting:
- Unauthorized software installations
- Abnormal file access
- Connections to suspicious domains
These tools also help contain threats by isolating compromised endpoints before they affect the broader network. When endpoints are secured properly, the risk of both internal misuse and external attacks through user devices is significantly reduced.
6. Deploy Advanced Threat Detection Tools
Advanced threat detection tools help identify attack patterns that traditional defenses might miss. A key part of this approach is the use of Security Information and Event Management (SIEM) systems. These systems collect and analyze log data from various sources, including:
- Endpoints
- Servers
- Cloud applications
- Security devices
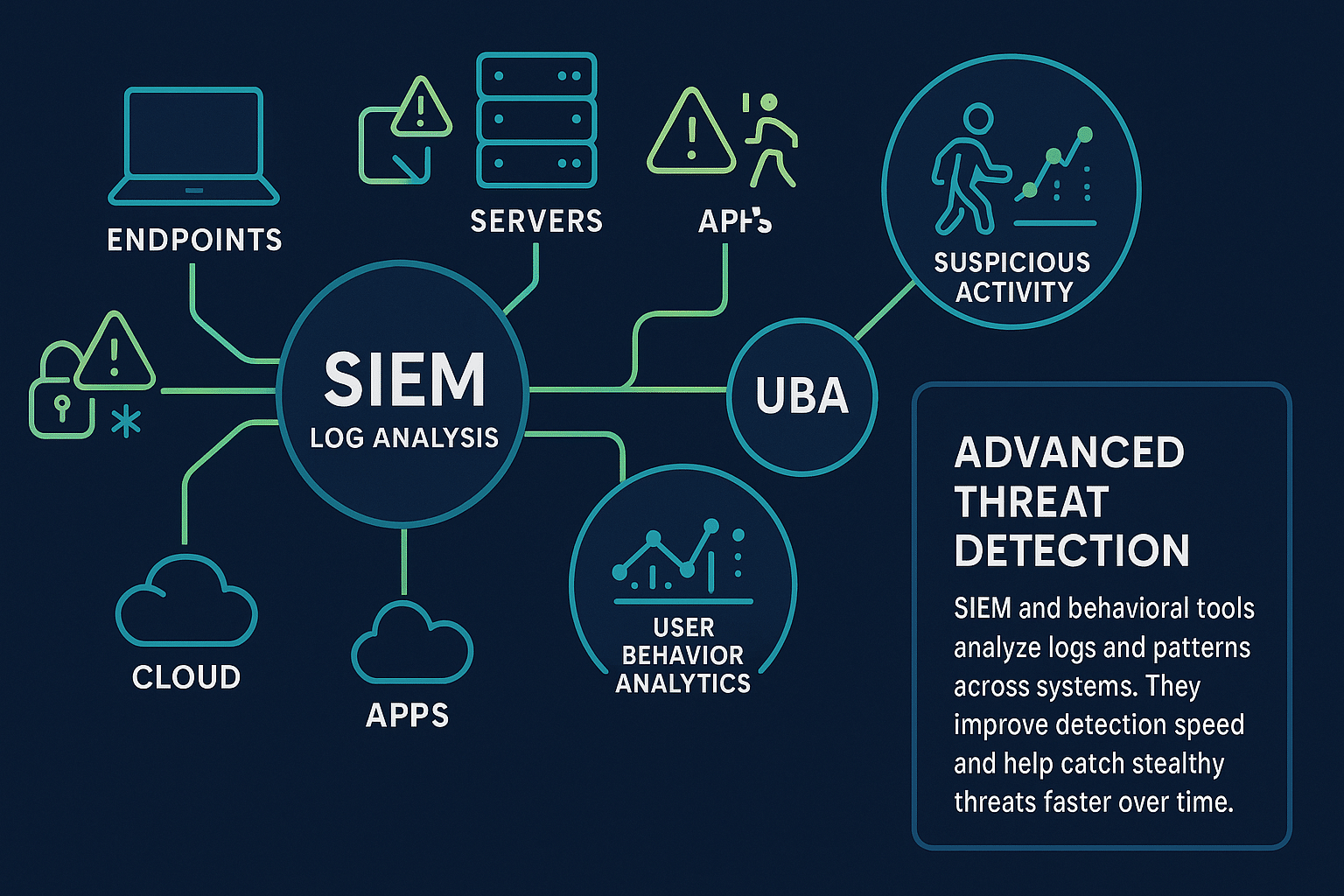
SIEM tools detect suspicious activity by correlating events such as:
- Repeated failed login attempts
- Unusual data transfers
- Unauthorized changes to access rights
Machine learning detection engines go a step further. These tools learn typical behavior patterns across users and systems, then spot anomalies that could indicate malicious intent.
For example, if someone in accounting suddenly starts transferring large volumes of source code to an external server, the system can immediately flag the activity.
As these tools gather more data, they adjust to changes and sharpen their detection accuracy. Together, SIEM and behavioral analytics give security teams quicker, more precise insight into potential data exfiltration attempts.
7. Employee Training and Awareness
Human error remains a leading cause of security breaches, making employee training a critical part of any protection strategy. Regular security awareness sessions help staff understand:
- The importance of protecting sensitive data
- Acceptable use policies
- The consequences of careless or negligent behavior

Training should include how to recognize:
- Phishing emails
- Suspicious links
- Social engineering tactics used to gain unauthorized access or install malware
Employees also need to understand that insider threats can come from both intentional actions, like selling company data, and careless mistakes, like sending confidential information through unsecured channels.
8. Strong Authentication and Identity Management
Authentication and identity controls help stop unauthorized access to sensitive systems and data. One important measure is multi-factor authentication (MFA), which requires users to verify their identity through multiple steps, such as:
- A password
- A time-sensitive code generated on a mobile device
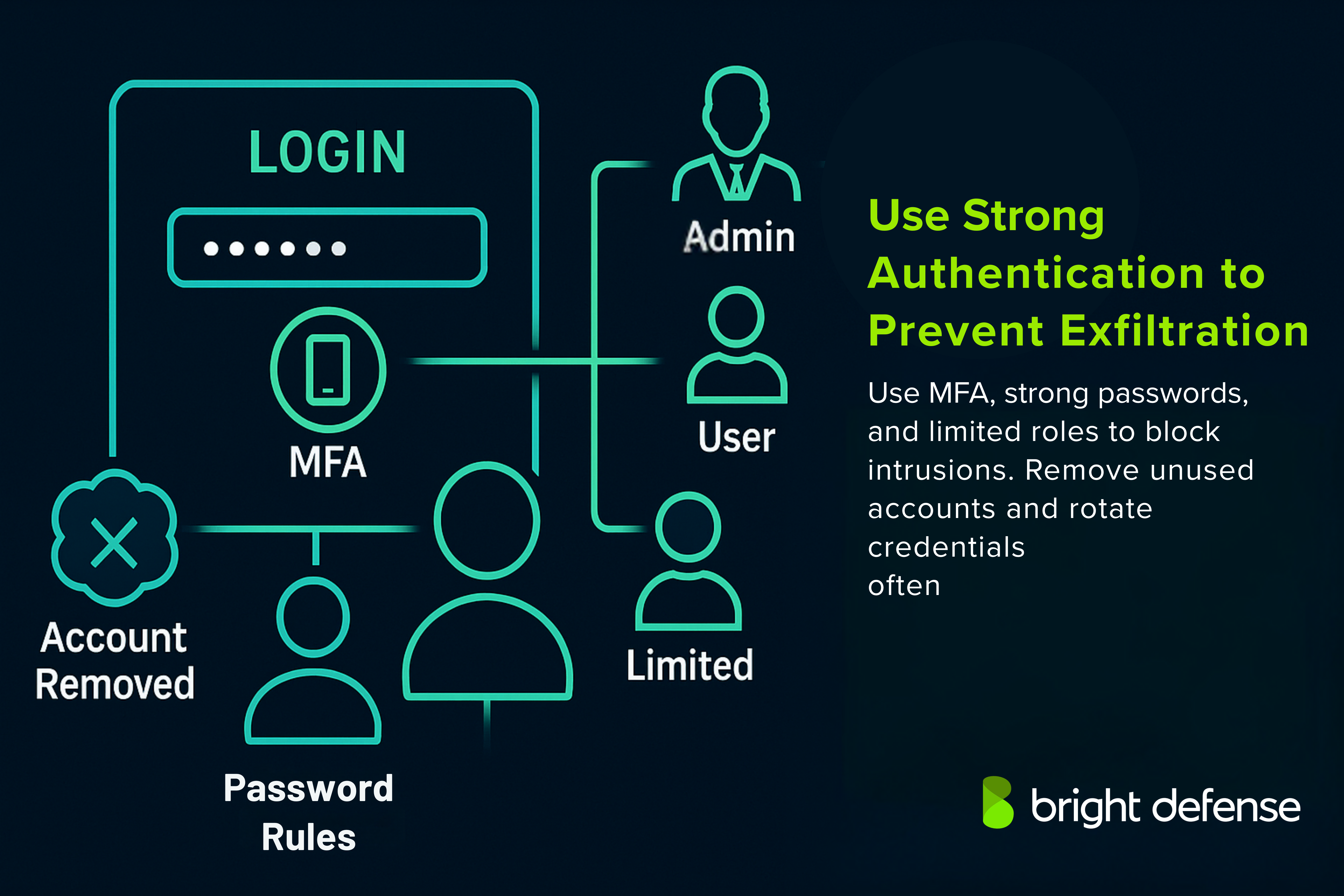
This prevents many attacks that rely on stolen or weak credentials.
Good identity management also includes:
- Regular reviews of user roles and access rights
- Limiting permissions to only what is necessary for each person’s role
- Promptly removing access when it is no longer needed
Password policies should encourage strong complexity, require regular updates, and use secure storage methods. These controls help block unauthorized activity and reduce the risk of compromised accounts being used to extract sensitive data.
9. Regular Security Audits and Vulnerability Assessments
Regular security audits and vulnerability assessments help maintain awareness of weaknesses across systems, networks, and applications. These efforts aim to find flaws before attackers can exploit them. Penetration tests simulate real-world attacks to evaluate how well current defenses perform.
The results highlight both technical security vulnerabilities and procedural gaps that could allow unauthorized access or data breaches.
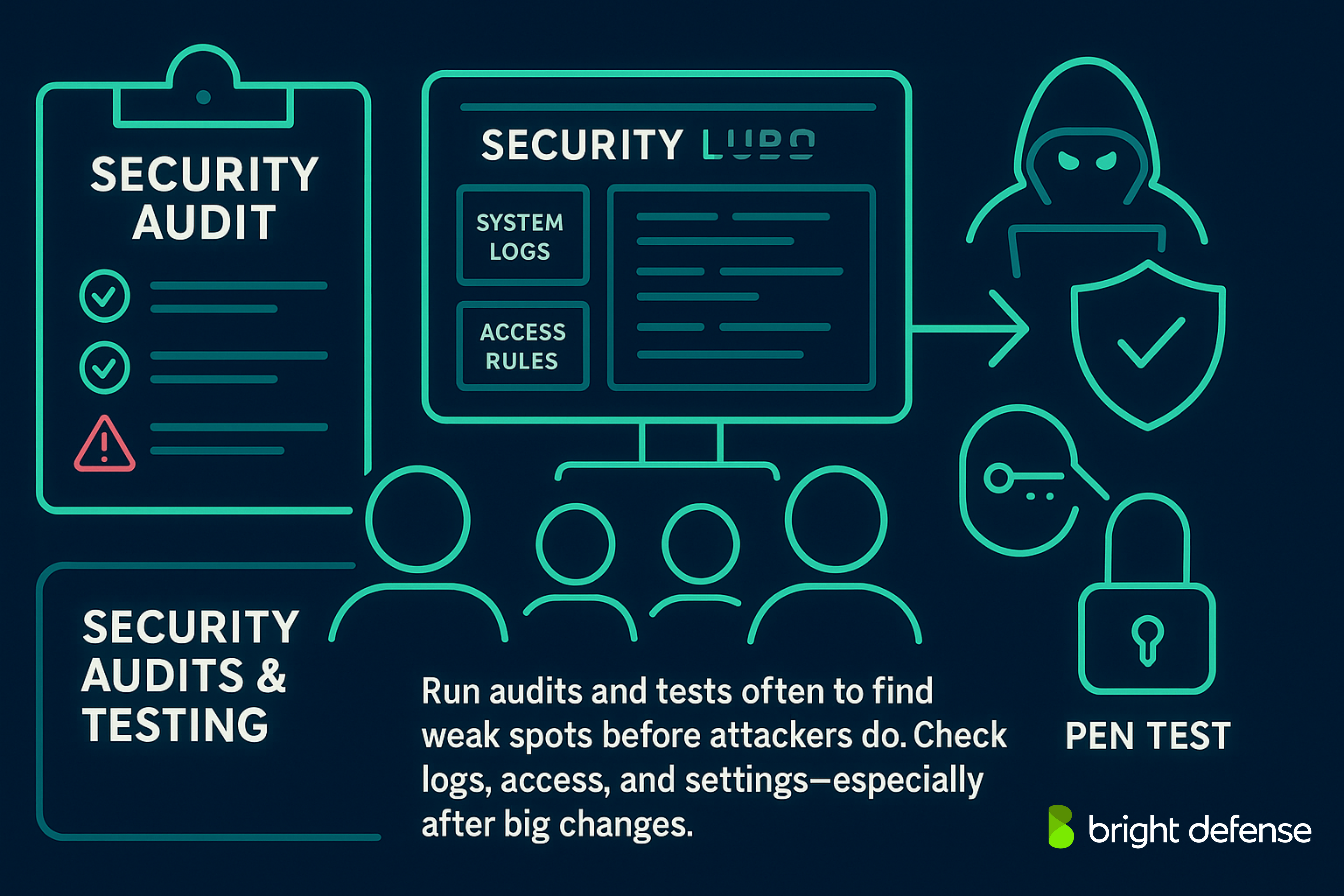
Audits go further than technical tests by examining configurations, access rules, and policy enforcement. This includes:
- Checking whether logging is enabled where needed
- Confirming that user permissions are accurate
- Ensuring sensitive corporate data is not exposed through misconfigured systems
These assessments should be done on a recurring basis or after significant system changes. Each upgrade or shift in infrastructure can introduce new risks. The goal is to keep security solutions current, apply strong access controls, and reduce the chances of missed issues that could lead to common data exfiltration.
10. Control Application and Browser Security
Applications and browsers are frequent targets for data exfiltration, especially when users click malicious links, download harmful files, or access insecure websites.
Securing these areas involves:
- Enforcing strict controls on which software can run
- Limiting which browser extensions are allowed
- Restricting how applications communicate over the network

Keeping browsers, plugins, and applications updated is equally important. Unpatched software frequently contains known vulnerabilities that attackers scan for and exploit. Automated patching, strict version control, and regular review cycles help close these security holes.
- Disabling unused browser features
- Applying sandboxing to limit the impact of compromised components
- Monitoring browser behavior for signs of misuse
Controlling these commonly used tools reduces the number of ways attackers can move data out of your systems.
Where Do Data Exfiltration Threats Come From?
Data exfiltration can originate from both outside attackers and individuals within the organization. Understanding the source is critical to developing targeted defenses that address the full range of risks.

1. External Threat Actors
External threat actors operate outside the organization and attempt to infiltrate systems to steal sensitive information. These include cybercriminals, nation-state groups, and opportunistic hackers. They often use phishing, malware, or software exploits to breach defenses and extract data over time. Because they lack direct access, they rely on stealth and technical exploitation to remain unnoticed while collecting information.
2. Malicious Insiders
Malicious insiders are individuals within the organization who intentionally steal sensitive data or leak information. These may be disgruntled employees, contractors, or anyone with access to sensitive corporate data who acts with harmful intent. They often know exactly where important data resides and how to extract it without raising alarms. Their access gives them a significant advantage, allowing them to bypass many external-facing defenses and exploit technical security vulnerabilities.
Additional protections include implementing strong access controls, monitoring for unusual behavior, and applying tools that can identify suspicious data transfers in real time. These steps help organizations limit the damage that insiders can cause and effectively prevent data exfiltration.
3. Careless or Negligent Insiders
Not all insider threats come from bad intent. Many incidents are caused by employees who mishandle data or ignore basic security practices. This includes emailing sensitive files to personal accounts, falling for phishing attempts, or failing to follow data handling protocols. These mistakes can unintentionally open the door to external attackers or lead to unmonitored data exposure.
4. Infected Devices
Malware turns compromised devices into quiet channels for ongoing data theft. Attackers infect endpoints through unsafe downloads, phishing links, or malicious USB drives and then take control of the system. They use the malware to monitor activity, collect files, and send them to remote servers without the user’s awareness. Without detection tools in place, attackers keep using the device to extract data over long periods.
5. Compromised Accounts
User accounts that have been taken over by attackers represent a significant threat. This usually happens when credentials are stolen through phishing, credential stuffing, or password reuse across platforms. Once inside, attackers can operate under the guise of a legitimate user, making it harder to detect suspicious behavior. These accounts may be used to access email, file storage, or internal systems and quietly transfer data outside the organization.
6. Third-Party and Supply Chain Risks
Vendors, partners, and service providers often have access to internal systems or shared data. If these third parties are compromised, attackers may use that access to steal information indirectly. Weak security practices at one supplier can lead to exposure across connected environments. These risks are especially serious when third-party software includes hidden backdoors or when external teams have broad permissions that are not properly monitored.
What Are the Consequences of Data Exfiltration?
Data exfiltration can have wide-reaching consequences that affect a company’s operations, finances, reputation, and legal standing. The impact often extends beyond the initial breach, especially when sensitive or regulated information is involved.
Below are the key areas where the damage is felt.
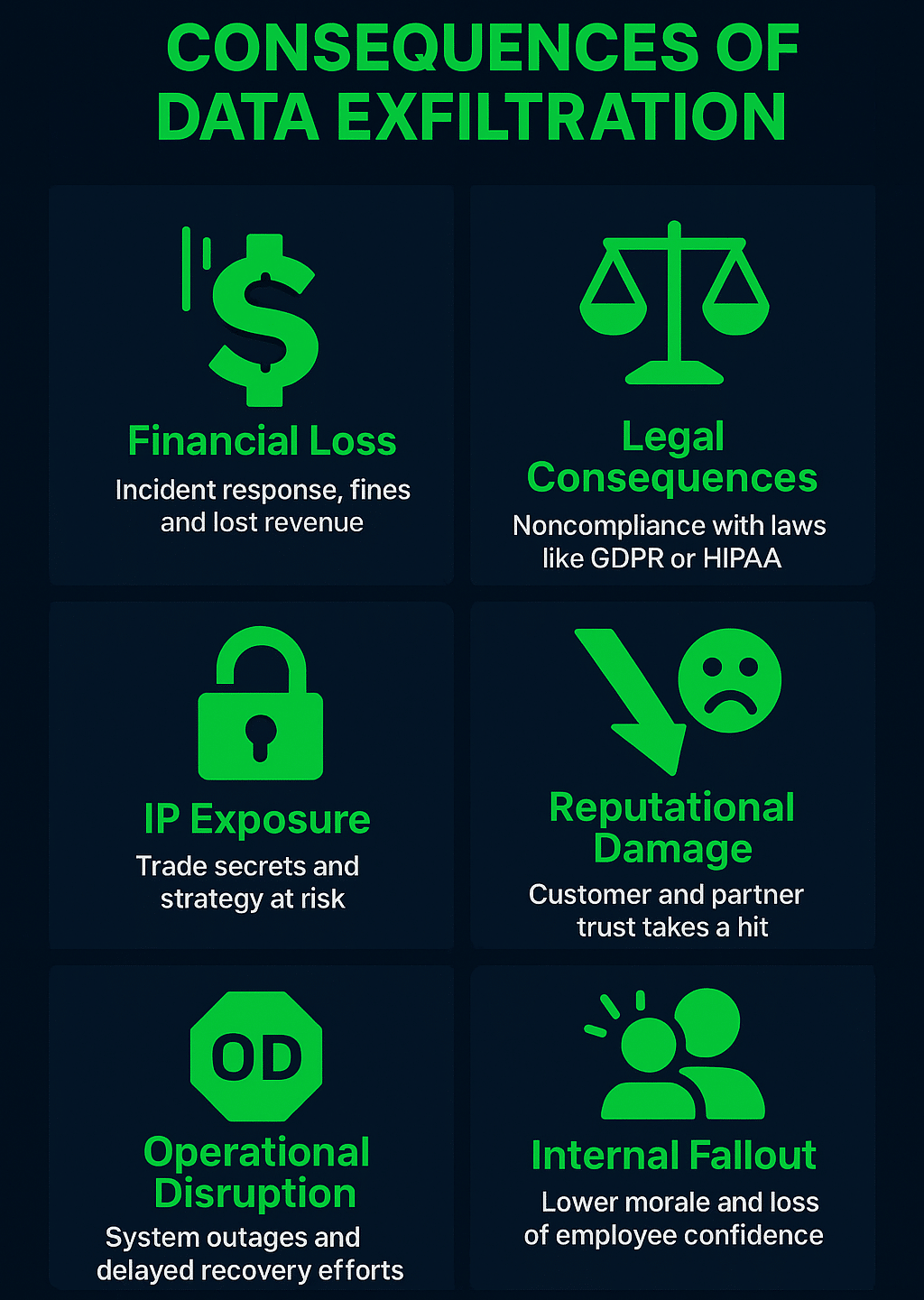
1. Financial Loss
One of the most immediate effects of data exfiltration is financial damage. Companies may face costs related to incident response, forensic investigations, system repairs, legal consultation, and customer notification. In cases involving customer or payment data, fines from regulatory bodies can be severe. Businesses may also suffer revenue losses from service disruptions or lost client contracts following the breach.
2. Regulatory and Legal Consequences
If the exfiltrated data includes personal, financial, or health-related information, companies may be subject to legal action or regulatory penalties. Laws such as GDPR, HIPAA, or CCPA impose strict requirements on data protection and breach reporting. Failing to notify affected individuals or to act within defined timeframes can lead to additional sanctions, lawsuits, or government investigations.
3. Reputational Damage
Once a data exfiltration incident becomes public, customer and partner trust can quickly erode. Clients may hesitate to continue doing business with a company that cannot protect its data. Brand damage can linger for years, especially if the breach was preventable or the response was poorly handled. In competitive industries, loss of trust can directly affect market share and long-term growth.
4. Intellectual Property Exposure
If proprietary information is taken, such as designs, source code, formulas, or strategy documents—it may be used to replicate products, undercut pricing, or sabotage future plans. In industries like manufacturing, biotech, or software, this type of breach can stall innovation and cause lasting competitive disadvantages.
5. Operational Disruption
Some exfiltration events involve malware that also affects system performance, disables services, or corrupts data. The time needed to investigate, isolate, and rebuild affected systems can interrupt business functions. Even in quieter breaches, internal teams must divert time and resources to handle the aftermath, slowing productivity and ongoing projects.
6. Internal Trust and Morale Issues
In cases where insiders are involved or security gaps are exposed, there can be a breakdown in internal trust. Employees may feel uncertain about the company’s ability to protect their data or job-related resources. This can lead to lower morale, increased turnover, or reduced cooperation with security policies.
Each of these consequences can compound the others. A financial hit combined with reputational damage, for example, may lead to customer attrition that takes years to recover from. That’s why data exfiltration is not just an IT problem but a company-wide risk that affects every function and department.
Common Data Exfiltration Techniques
Attackers use a variety of methods to quietly transfer data out of a target environment. These techniques are often designed to blend into regular activity or exploit weak points in system configuration, making detection difficult. Here are the most commonly used methods:
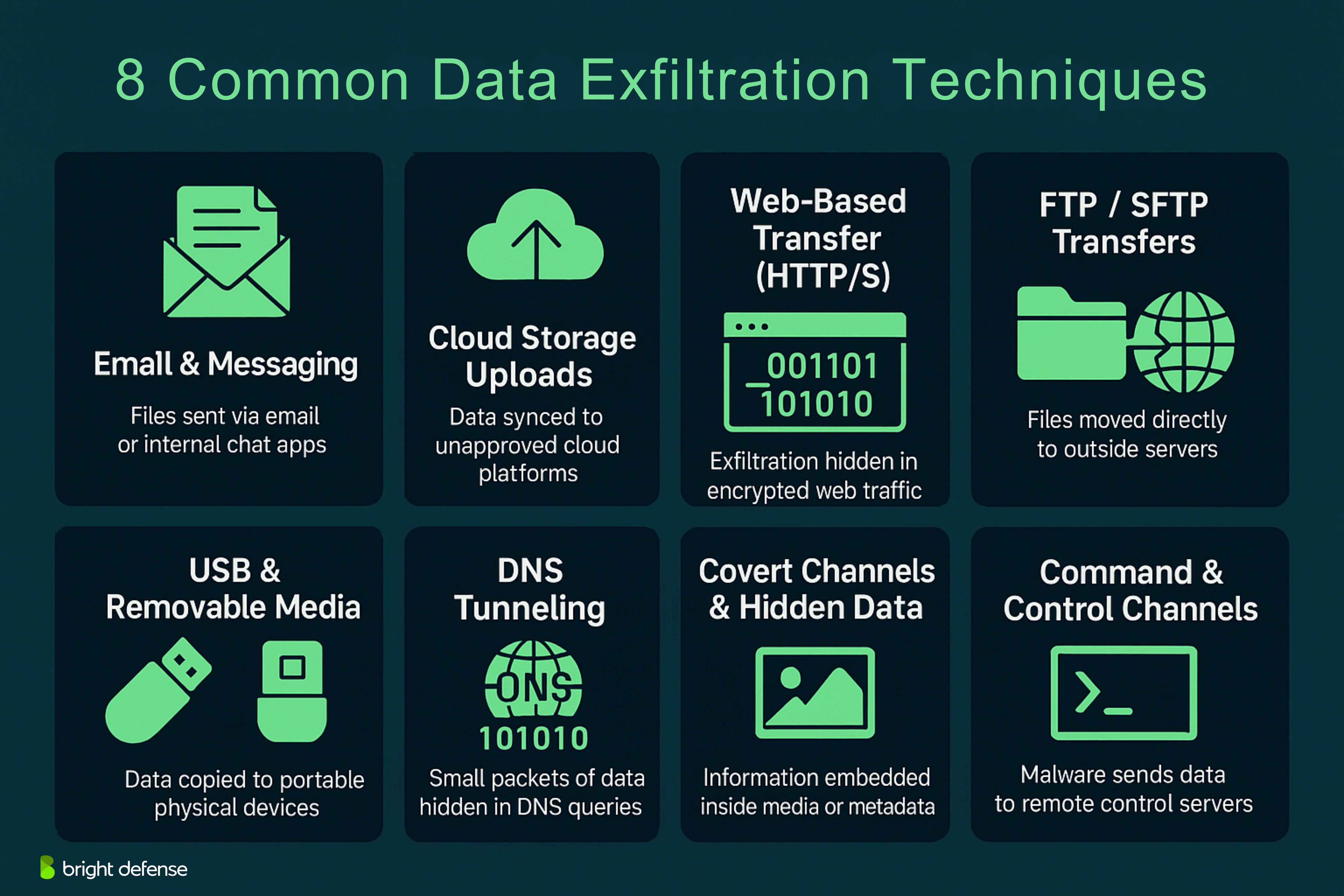
1. Email and Messaging Applications
Sensitive files are often exfiltrated through email, either by sending attachments to external addresses or by forwarding messages from compromised accounts. Attackers may also use internal chat tools or messaging apps linked to outside accounts. Because email traffic is routine and trusted, this method is often overlooked in basic monitoring setups.
2. Cloud Storage and File Sharing Services
Uploading data to unauthorized cloud platforms like personal Google Drive, Dropbox, or OneDrive accounts is another frequent tactic. These services are commonly allowed through firewalls for productivity purposes, which makes them convenient exfiltration channels. Attackers or insiders can sync sensitive files to these accounts with little resistance if restrictions are not in place.
3. Web-Based Data Transfer (HTTP/HTTPS)
Using standard web traffic, attackers can hide stolen data inside outbound HTTP or HTTPS sessions. Encrypted HTTPS connections, in particular, make it harder for traditional security tools to inspect the contents of the traffic. This method allows the transfer of data to external servers under the cover of normal browsing or application behavior.
4. File Transfer Protocol (FTP) and Secure FTP
FTP and SFTP are direct ways to move files to external servers. While less commonly used in modern businesses, these protocols are still exploited in environments that lack strict monitoring. Attackers may deploy scripts that automate regular uploads to remote destinations.
5. Removable Media (USB Drives, External Hard Drives)
Insiders may copy data onto USB drives or external disks and physically remove it from the premises. This is a straightforward method of exfiltration and one of the hardest to track unless endpoint monitoring and device control policies are active. In some environments, attackers may also exploit weak USB access controls to auto-execute malicious code.
6. DNS Tunneling
DNS, a protocol normally used for resolving domain names, can be misused to smuggle data out in small packets. This technique is highly covert because DNS traffic is generally allowed and considered low-risk. Attackers encode the stolen data into DNS queries and responses, creating a hidden communication channel.
7. Covert Channels and Data Hiding
Data can be hidden inside images, videos, or document metadata before being uploaded or sent out through legitimate services. Known as steganography, this method disguises exfiltration by embedding information in formats that appear harmless. Other approaches involve misusing system logs, printer queues, or temporary files as staging areas for collection and transfer.
8. Command and Control (C2) Channels
Some advanced malware establishes communication with remote command servers. Through these C2 channels, attackers receive instructions and transmit collected data over time. These sessions often operate in the background, disguised as routine outbound connections, and are designed to avoid triggering detection systems.
Such covert activity is common in data exfiltration attacks, where the goal is to move stolen information without alerting monitoring tools. In some cases, malware may exploit cloud storage services as a covert channel, blending into regular traffic patterns.
Each of these techniques can function independently or be combined depending on the attacker’s goal and the environment’s defenses. Organizations must monitor across multiple vectors—network, endpoint, cloud, and user behavior, to spot the signs of covert data movement. Visibility into user activity and use of network monitoring tools can help detect these operations before serious damage occurs.
How Can Bright Defense Help?
Bright Defense helps stop data from leaking out through real testing, tight monitoring, and smart controls. Attack simulations expose weak points, and fixes happen fast. System activity is tracked so data access is visible and controlled. For companies working under SOC 2, HIPAA, or similar standards, compliance controls stay current and effective.
We act as your security lead when you need one—writing clear rules, setting up response plans, and helping you understand where your risks lie. If your team is the weak link, we address that too through training that helps people spot phishing, avoid mistakes, and report suspicious activity.
We also configure access controls, file tracking, and alerts to help you catch unusual behavior early. Instead of vague recommendations, we give you direct steps and work with you to implement them. If you’re ready to stop data exfiltration, we’ll help you get there.
4o
FAQs
Data exfiltration is the unauthorized transfer of data from a computer or network. It often involves attackers stealing sensitive corporate data through phishing, malware, or direct extraction using storage devices or cloud apps.
Organizations prevent data exfiltration by monitoring file transfers, blocking unauthorized cloud use, limiting access to sensitive data, detecting suspicious data transfers, and patching system vulnerabilities.
Using data loss prevention (DLP) tools is one effective measure. These tools monitor and block attempts to send or copy sensitive information without authorization.
Critical controls include endpoint monitoring, DLP systems, user behavior tracking, email filtering, strong access rules, encryption, and cloud access security brokers. These help detect data exfiltration and prevent unauthorized transfers
Get In Touch



