What is API Penetration Testing?
If you’re getting started with API Penetration Testing, it’s critical to understand not just how APIs work but also how they break. APIs handle sensitive data, enforce permissions, and link services, which makes them a frequent target for attackers. Testing them the way an attacker would is the only way to find the weak points that typical scans miss.
API Penetration Testing simulates real attacks to find these gaps before someone else does. This blog explains what it is, why it matters, and how it works.
Key Takeaways
- API penetration testing simulates real attacks to uncover flaws in authentication, authorization, data handling, and logic that scanners often miss
- Many API vulnerabilities involve business logic or hidden endpoints that require manual testing to detect
- Testing helps verify token handling, access controls, input validation, and rate limiting across REST, GraphQL, and other API types
- Common issues include broken object-level authorization, token tampering, and exposure of undocumented endpoints
- A qualified security team conducts targeted assessments and delivers clear reports that support remediation and compliance with OWASP, SOC 2, and HIPAA standards
What is API Penetration Testing?
API Penetration Testing is a security assessment that targets application programming interfaces (APIs) to detect vulnerabilities that could be exploited by attackers. It simulates real-world attacks on API endpoints to check how well they can resist unauthorized access, data leaks, and manipulation.
This testing focuses on:
- Authentication and authorization issues
- Data exposure risks
- Input validation flaws
- Rate limiting and abuse prevention gaps
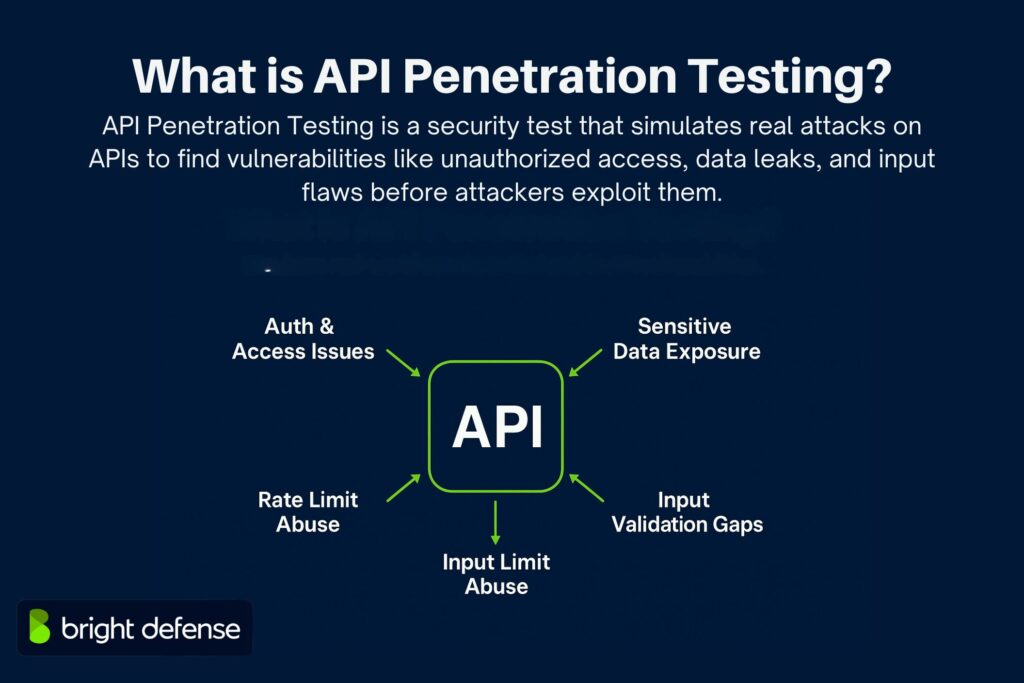
It helps verify whether APIs correctly enforce access controls and protect sensitive information during both typical and malicious use.
Why Is API Pentesting Important?
APIs introduce unique security risks that traditional testing often misses. From hidden endpoints to logic flaws, these issues demand focused attention. Here’s why API penetration testing is essential:

1. APIs Are the New Frontline for Attackers
Attackers increasingly target APIs as the most exposed part of modern application architecture. According to Gartner, by 2025, over 90% of web-enabled applications will have more attack surface in exposed APIs than in the user interface. APIs are responsible for handling authentication, transferring sensitive data, and performing core business functions.
However, they are often treated as internal infrastructure rather than security-critical components. This lack of focus has led to major breaches, such as the T-Mobile API exposure in 2023, which affected over 37 million customers due to an unprotected endpoint.
2. Most API Vulnerabilities Can’t Be Found with Scanners
Automated scanners are useful for detecting surface-level issues, but they consistently miss deeper vulnerabilities in APIs. Common issues such as logic flaws, broken object-level authorization (BOLA), and privilege escalation typically require manual analysis.
The OWASP API Security Top 10 for 2023 ranks BOLA as the most critical API threat. According to Salt Security, 94% of organizations experienced an API-related security incident in the past year, with many of those linked to vulnerabilities that tools failed to detect. Manual testing remains essential for identifying these high-impact weaknesses.
3. APIs Expand Rapidly and Are Often Poorly Documented
As development teams ship new features and integrations, APIs multiply quickly across environments. Over time, this creates a complex network of endpoints, many of which are undocumented, deprecated, or forgotten.
These orphaned APIs often remain accessible in production. Without regular penetration testing, hidden and legacy endpoints become easy targets for attackers looking to exploit forgotten assets.
4. Business Logic and Abuse Cases Are Not Caught Automatically
Many real-world API breaches exploit flaws in business logic rather than technical misconfigurations. Attackers manipulate workflows, bypass intended steps, or tamper with inputs to gain unauthorized access. Examples include skipping payment processes, adjusting booking parameters, or abusing reward systems.
These actions typically appear valid at the network level, allowing them to bypass automated defenses. Manual API penetration testing can simulate these abuse scenarios with context that automated tools cannot model, helping uncover vulnerabilities that directly affect application integrity and business operations.
5. Compliance and Risk Management Depend on Thorough Testing
Security and compliance standards such as SOC 2, ISO 27001, PCI-DSS, and HIPAA increasingly require API-level testing as part of their audit criteria. Auditors and stakeholders expect organizations to present API-specific risk assessments and test results.
In the absence of formal API testing, organizations face delayed certifications, increased regulatory scrutiny, and potential reputational damage. Conducting regular API penetration testing supports both risk reduction and compliance, providing assurance to partners, customers, and regulators that the API surface is actively monitored and maintained.
API Pentesting Process
Effective API penetration testing follows a structured process designed to simulate real-world attack behavior while maintaining control, documentation, and repeatability. Let’s find out more about the process in detail:
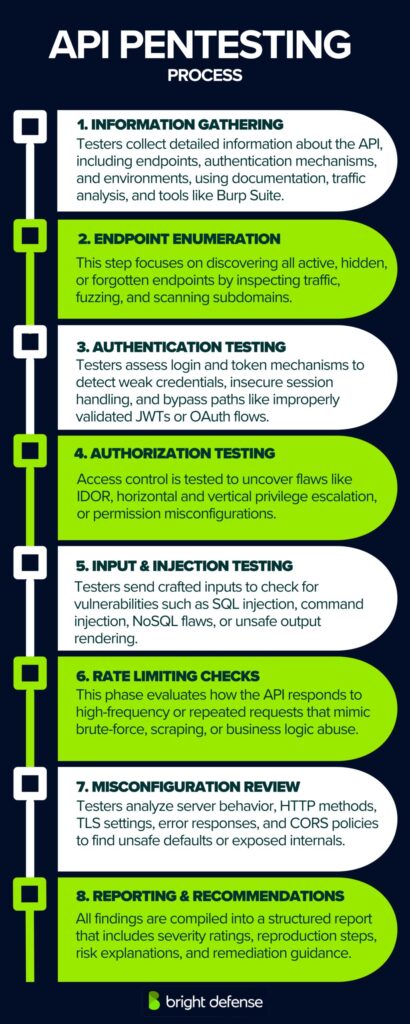
Step 1. Information Gathering
This initial phase focuses on collecting all available data about the target API. Testers examine documentation, review API specifications (such as OpenAPI/Swagger files), analyze client-side code, and capture live traffic using tools like Burp Suite or Postman.
Key objectives include:
- Mapping all endpoints and methods (GET, POST, PUT, DELETE)
- Identifying required headers, parameters, and authentication types
- Extracting token formats and session behavior
- Listing available environments (production, staging, development)
Step 2. Endpoint Enumeration
The next step is identifying known, hidden, or undocumented API endpoints. This is critical because attackers often exploit forgotten or misconfigured routes. Enumeration is performed using:
- Network traffic inspection
- Wordlist-based fuzzing with tools like ffuf or dirsearch
- JavaScript file analysis in web applications
- Subdomain scanning to uncover environment-specific APIs (e.g., api-dev.example.com)
This phase helps build a complete picture of the API’s exposed surface.
Step 3. Authentication Testing
Authentication mechanisms are tested for weaknesses such as:
- Weak or guessable credentials
- Insecure token handling (e.g., expired tokens still accepted)
- Missing multi-factor enforcement
- Bypass through improper validation of JWTs, OAuth flows, or API keys
Tools such as jwt_tool, Burp Suite extensions, and custom scripts are commonly used here. Manual analysis is key, especially when assessing custom token formats or login flows.
Step 4. Authorization Testing
Once authenticated, testers verify if access controls are correctly enforced. This involves:
- Testing for Insecure Direct Object References (IDOR)
- Attempting horizontal privilege escalation by accessing other users’ resources
- Trying vertical escalation by accessing administrative functions
- Modifying user roles or permissions in tokens or requests
Improper access control remains one of the most exploited weaknesses in APIs.
Step 5. Input Validation and Injection Testing
This step targets how the API handles input across parameters, body content, headers, and cookies. Testers attempt:
- SQL Injection using tools like sqlmap
- NoSQL Injection through crafted JSON queries
- Command Injection to execute system-level instructions
- Cross-site Scripting (XSS) if APIs return rendered content
Input fields are fuzzed with payloads to observe abnormal behavior, server errors, or data leaks.
Step 6. Rate Limiting and Abuse Testing
Testers simulate high-frequency API calls to assess whether protections exist against:
- Brute-force login attempts
- Mass data extraction
- Resource exhaustion (DoS)
- Abuse of business logic (e.g., reusing coupon codes or reward points)
Testing is done with throttled automation, replayed sessions, and manipulation of timestamps or rate counters.
Step 7. Security Misconfigurations and Transport Testing
During this stage, configurations and transport layers are reviewed. This includes:
- Testing HTTP methods (e.g., is PUT or DELETE unnecessarily enabled?)
- Inspecting TLS implementation and certificate handling
- Checking for verbose error messages or debug headers
- Verifying CORS settings and allowed origins
- Detecting exposed internal infrastructure via SSRF or open redirects
These flaws often reveal internal systems or create attack chains.
Step 8. Reporting and Recommendations
Once testing concludes, all findings are documented in a structured report. This includes:
- A list of discovered vulnerabilities, categorized by severity
- Technical details, reproduction steps, and screenshots
- Risk descriptions mapped to CVSS or OWASP standards
- Fix guidance and remediation advice
- Optional retesting timelines and evidence of patch verification
Reports are written for both technical teams and business stakeholders, supporting remediation and decision-making.
Best API Penetration Testing Tools
Choosing the right tools is key to conducting effective API penetration testing. These are the tools that stand out in terms of capability, flexibility, and practical use during real-world API assessments:
- Insomnia: A modern API client that provides strong support for scripting and environment variables. Ideal for manually crafting requests or testing edge cases during exploratory assessments.
- SoapUI: Still the go-to option when dealing with legacy SOAP APIs. SoapUI supports complex XML structures, custom headers, and detailed test scenarios that are hard to reproduce elsewhere.
- FFUF: Used primarily for brute-forcing endpoints and parameter names. FFUF is fast and effective when testing for hidden API routes or sending fuzzed input to uncover unexpected behavior.
- Amass: More reconnaissance-focused, Amass helps in discovering subdomains where APIs are hosted. It’s a common starting point for pentesters mapping out where APIs live within large environments.
- sqlmap: Highly effective when an API interacts with a SQL backend. sqlmap can automate detection and exploitation of SQL injection flaws, even through JSON or URL-encoded payloads.
- JWT Tool: Specialized in analyzing and manipulating JSON Web Tokens. Useful for tampering with token payloads, checking for weak signing keys, or testing signature validation logic.
- Hydra: Valuable for brute-force attacks against login endpoints. Hydra supports HTTP-based forms, allowing testers to evaluate how well an API defends against credential stuffing or weak passwords.
- Burp Suite: One of the most essential tools for API pentesters. It allows full control over request and response flow, making it ideal for intercepting API calls, modifying headers or tokens, and replaying requests. Its extensions cover everything from JWT decoding to active scanning.
- OWASP ZAP: A solid open-source alternative for scanning and fuzzing APIs. ZAP supports automated discovery of endpoints and can simulate common attack patterns. With support for both REST and SOAP, it fits well into CI pipelines for continuous API testing.
- Postman: While built for developers, Postman is highly useful for manual API security testing. It allows testers to construct requests, manage sessions, inject custom headers, and test authentication flows like OAuth and JWT. It’s also a great way to replay and sequence requests during logic testing.
Different Types of API Attacks
In this section, you’ll learn about common types of API attacks used during penetration testing. Each method helps expose flaws in authentication, authorization, data validation, and more.
1. Fuzzing Attacks
Fuzzing sends unexpected or malformed input, such as extra long numbers, special characters, or known exploit strings, to an API to see how it reacts. The purpose is to uncover crashes, errors, or strange behavior that reveals weaknesses in how the API handles input.
Example:
If an API expects a user ID, you might try:
- A very large number
- Another user’s ID
- SQL-like input such as 1 OR 1=1
Tools Used:
- ffuf
- SecLists (public wordlists)
2. API Discovery Attacks
These attacks focus on finding forgotten, hidden, or undocumented API endpoints that developers may have left exposed. They often appear in test environments, old projects, or mobile apps and can be used as backdoors if overlooked.
How it’s done:
- Reviewing front end JavaScript or decompiling mobile apps
- Capturing and analyzing network traffic
- Scanning for common subdomains such as api.example.com or dev-api.example.com
Tools Used:
- amass
- subfinder
- Burp Suite, OWASP ZAP
3. Authorization Attacks
Authorization attacks attempt to access data or perform actions beyond the user’s allowed role. These include modifying requests to view another user’s data or elevate privileges.
Types:
- Horizontal access: Accessing data of other users at the same level
- Vertical access: Pretending to be a higher privilege user
- IDOR (Insecure Direct Object Reference): Changing resource IDs in requests to retrieve unauthorized data
Example:
Changing GET /orders/123 to GET /orders/124 may return another user’s order if the API lacks proper checks.
4. Authentication Attacks
These attacks try to bypass or break the process that verifies user identity. They often involve guessing login credentials, manipulating tokens, or exploiting weak validation logic.
Types:
- Brute Force: Trying many password combinations
- Token Tampering: Modifying JWTs or other session tokens
- Improper Token Handling: Using expired or malformed tokens if the API doesn’t reject them
Tools Used:
- Burp Suite Intruder
- jwt_tool
- hydra
5. Injection Attacks
Attackers inject malicious code into API inputs, targeting the backend database or operating system. The goal is to extract data, bypass login flows, or execute commands.
Types:
- SQL Injection: Modify database queries
- NoSQL Injection: Alter logic in NoSQL databases
- Command Injection: Run system commands on the server
Example (NoSQL):
This might bypass login if the server uses MongoDB and doesn’t validate inputs properly.
Tool Used:
- sqlmap
6. SSRF (Server Side Request Forgery)
SSRF tricks the API server into sending requests to internal or restricted services, often using its elevated access. It allows attackers to reach otherwise unreachable areas of a network.
Example:
If the server fetches the page, the attacker may gain access to internal panels.
Tool Used:
- Burp Collaborator
How Can Bright Defense Help You With API Penetration Tests?
Bright Defense helps secure your APIs by detecting broken authentication, improper access controls, and injection flaws across REST, GraphQL, and other interfaces. We evaluate real-world risks in how APIs handle data, sessions, permissions, and third-party integrations.
Why Choose Bright Defense for API Pen Testing?
- Clear Outcomes: Reports highlight technical and business risks, with remediation steps tailored to your API logic.
- Purpose-Built Packages: Select from Core (basic auth and data validation), Scale (complex API flows), or Apex (multi-environment + compliance-driven).
- Attack-Led Testing: We simulate adversaries, not just fuzzers, to uncover abuse paths through real API misuse.
- Compliance Ready: Testing supports OWASP API Top 10, SOC 2, HIPAA, ISO 27001, and PCI-DSS controls.
FAQs
It simulates real-world attacks on APIs—whether REST, SOAP, GraphQL—to find vulnerabilities in authentication, access control, injection flaws, data exposure, and rate limiting.
APIs often expose backend services; testing ensures these endpoints can’t be misused or leaked, helping prevent data breaches and compliance failures.
Frequent issues include broken authentication or authorization, injection flaws (SQL, NoSQL), excessive data exposure, misconfigured CORS, and business logic abuse.
Process includes reconnaissance (mapping endpoints), enumeration (discovering parameters), vulnerability analysis, exploitation (injecting or bypassing controls), and reporting.
Tools like Postman, Burp Suite, OWASP ZAP, SoapUI, and cURL help testers send requests, inspect responses, automate fuzzing, and probe for weaknesses.
Testers try bypassing tokens or session handling, brute-forcing credentials, manipulating roles or permissions, and using improper scopes or expired tokens.
Validating inputs prevents injections, XSS, command execution, and other abuses by ensuring only expected data is processed by the API.
Weak rate controls can allow brute-forcing, flooding, or DoS attacks; testing confirms if APIs enforce limits and handle abuse gracefully.
Attackers exploit flawed logic (e.g., pricing controls, workflows) to gain unauthorized actions, escalate privileges, or bypass restrictions, not necessarily via technical bugs.
At least once a year, and whenever you add new endpoints, change authentication flows, or integrate third-party APIs to maintain security posture.
Get In Touch



