
10 Types of Penetration Testing Every Organization Should Know
Penetration testing plays a critical role in assessing an organization’s ability to withstand cyberattacks. Security teams use it to simulate real-world threats, find weak points, and assess how well defenses hold up under pressure.
However, not all penetration tests follow the same approach. Different types serve different goals, whether it’s testing external infrastructure, employee behavior, or application security.
This blog breaks down the main types of penetration testing and explains when and why each one is used.
Types of Penetration Testing
Penetration testing comes in many forms, each targeting different parts of your environment. The following 10 types simulate real-world attacks to reveal security gaps and help reduce risk:
Penetration Testing Types Comparison Table
| Penetration Testing Type | Purpose | Targets | Key Vulnerabilities | Tools | When to Test |
|---|---|---|---|---|---|
| Network Penetration Testing | Evaluate internal and external network infrastructure for exploitable weaknesses. | Servers, firewalls, routers, switches, printers, wireless access points, workstations. | Open ports, misconfigured devices, outdated software, insecure remote access. | Nmap, OpenVAS, Metasploit, Nessus, Aircrack-ng. | Annually, after infrastructure changes, for compliance (e.g., PCI DSS, ISO 27001). |
| Web Application Penetration Testing | Test web apps for security flaws in logic, input handling, and access control. | Web portals, dashboards, APIs, authentication systems. | SQLi, XSS, CSRF, broken authentication, security misconfigurations. | OWASP ZAP, Burp Suite, Acunetix, Wapiti, Nikto. | Before launch, after major updates, quarterly, or for compliance. |
| Client-Side Penetration Testing | Find vulnerabilities in desktop applications used by end-users. | Browsers, email clients, Office apps, communication tools. | HTML injection, clickjacking, CORS misconfigurations, file execution risks. | BeEF, Burp Suite, Exploit DB, MITMf. | During assessments, software rollouts, or endpoint audits. |
| Wireless Penetration Testing | Test the security of Wi-Fi networks and connected devices. | Access points, routers, IoT devices, mobile devices. | Weak encryption, rogue APs, reused passphrases, signal leakage. | Aircrack-ng, Kismet, Wireshark, WiFi Pineapple, Bettercap. | During assessments, after deployments, office moves, or security incidents. |
| Social Engineering Testing | Evaluate employee response to phishing, impersonation, and manipulation. | Employees, helpdesk, executives. | Phishing, tailgating, pretexting, impersonation, dumpster diving. | Phishing Frenzy, Evilginx, KnowBe4, Gophish. | Quarterly, post-onboarding, after incidents, or as part of awareness training. |
| Physical Penetration Testing | Assess physical security of facilities and asset protection measures. | Buildings, server rooms, badge systems, surveillance tools. | Propped doors, poor surveillance, badge cloning, unattended devices. | Proxmark3, USB drops, lockpicks, hidden cameras. | After office changes, during red team ops, or annually. |
| API Penetration Testing | Check API endpoints for improper access, data leaks, and logic flaws. | Public/internal REST/SOAP/GraphQL APIs. | IDOR, broken auth, rate limiting, injection flaws. | OWASP ZAP, Postman, Insomnia, Burp Suite, APISec. | During development, after updates, new integrations, or regularly. |
| Mobile Application Penetration Testing | Test security of Android/iOS apps and their interactions. | Mobile apps, backend APIs, local storage. | Insecure storage, weak auth, traffic interception, reverse engineering. | MobSF, Frida, Drozer, Veracode, Checkmarx. | Pre-launch, post-update, or for compliance (HIPAA, PCI DSS). |
| Cloud Penetration Testing | Evaluate cloud configurations, access controls, and exposure. | AWS, Azure, GCP setups, storage, IAM, APIs. | Open buckets, weak IAM roles, exposed admin panels. | Prowler, ScoutSuite, CloudMapper, Prisma Cloud. | After migrations, infra changes, or for annual compliance. |
| IoT Penetration Testing | Test security of embedded devices and communication layers. | Sensors, smart devices, industrial controllers. | Hardcoded creds, insecure firmware, unprotected APIs. | Firmadyne, Binwalk, Ghidra, UART tools, OWASP IoT Guide. | Before launch, in regulated deployments, or during security cert processes. |
1. Network Penetration Testing
Network penetration testing is one of the most critical assessments for identifying weaknesses in an organization’s network infrastructure. It evaluates how vulnerable the network is to external and internal threats, helping to expose potential entry points that attackers might exploit.
Penetration testers assess a wide range of devices, including servers, firewalls, routers, switches, printers, wireless access points, and workstations. The test simulates real-world attack scenarios to understand how a breach could occur and what impact it might have.
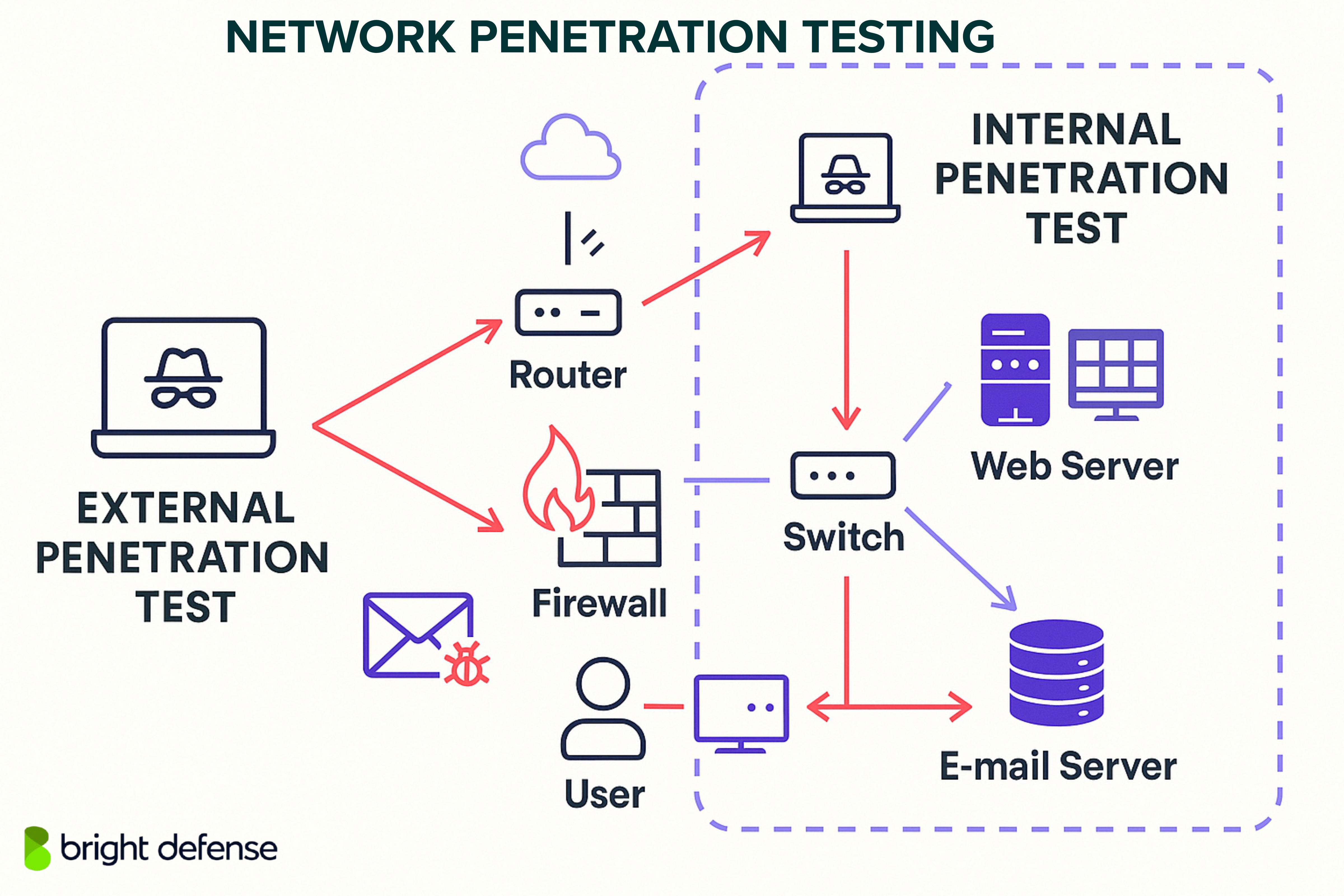
Network pen testing can be divided into two parts: external network penetration testing and internal network penetration testing.
External testing targets internet-facing systems such as VPN gateways, public web servers, and mail servers. The objective is to determine how an outsider with no internal access could breach the perimeter.
Internal testing assumes the attacker has already gained access to the network, perhaps through phishing, stolen credentials, or social engineering. The test then explores how easily an attacker can escalate privileges, move laterally, or access sensitive data from within the network.
Check out our blog on
Wireless Network Considerations
Wireless testing is often included in the scope of network penetration testing. It focuses on the security of Wi-Fi infrastructure and devices such as laptops, phones, and IoT hardware. Testers look for weak encryption, rogue access points, default settings, and potential misconfigurations that could be exploited from within signal range or via remote devices like WiFi Pineapples.
Common Vulnerabilities Explored
- Misconfigured firewalls or routers
- Open and unnecessary ports
- Weak encryption protocols
- Insecure remote access tools (SSH, FTP, RDP)
- DNS exposures (e.g., zone transfers)
- Lack of network segmentation
- Outdated software or unpatched systems
- Man-in-the-Middle attack vectors
These vulnerabilities can allow attackers to gain access, maintain persistence, or pivot to high-value systems within the network.
Tools Commonly Used
Open-source tools:
- Nmap (port scanning and discovery)
- OpenVAS (vulnerability assessment)
- Metasploit Framework (exploitation)
- Aircrack-ng (wireless testing)
Commercial tools:
- Nessus Professional
- Burp Suite Professional (when web interfaces are involved)
These tools help testers perform reconnaissance, probe defenses, validate findings, and generate reports.
When to Perform the Test
Network penetration testing should be scheduled at least annually. Additional testing is recommended after significant infrastructure changes or deployment of new services. Many regulatory standards (e.g., PCI DSS, ISO 27001) require regular testing as part of maintaining compliance.
Organizations often begin with external testing since it targets the most exposed and accessible assets. Internal testing adds deeper insight and is especially important if there’s concern about insider threats or gaps in internal segmentation.
2. Web Application Penetration Testing
Web application penetration testing focuses on evaluating the security of websites, portals, dashboards, and web-based services. These applications often handle sensitive business and user data, making them high-value targets for attackers. This type of testing simulates attacks on front-end and back-end components to find flaws in authentication, session management, input validation, logic, and more.

Testers aim to detect vulnerabilities such as SQL injection, cross site scripting attacks (XSS), file inclusion, insecure direct object references, and broken access controls. Since web applications change often, testing must keep pace with development cycles to catch new security issues and avoid regressions.
Common Vulnerabilities and Targets
A web application test checks for weaknesses across both static and dynamic elements. The scope often includes:
- Web interfaces (login forms, search fields, file uploads)
- Front-end components (scripts, plugins, embedded code)
- APIs (RESTful or SOAP)
- Back-end logic and database interaction
- Review of source code in white box scenarios
Typical vulnerabilities discovered during testing include:
- SQL injection
- Cross-site scripting (XSS)
- Broken authentication or session management
- Insecure direct object references
- Server-side request forgery (SSRF)
- Cross-site request forgery (CSRF)
- Misconfigured security headers
These flaws can result in data theft, unauthorized access, defacement, denial of service, or the ability to access sensitive data beyond intended boundaries.
Tools Commonly Used
Open-source tools:
Commercial tools:
These tools support both automated scanning and manual techniques, helping testers uncover security vulnerabilities and verify the impact of their findings.
When to Perform the Test
Web application penetration testing should be conducted:
- Before launching any new application
- After significant updates or code changes
- As part of a routine security program (e.g., quarterly or annually)
- To meet compliance requirements such as PCI DSS or ISO 27001
Organizations with continuous deployment pipelines or agile development cycles often include testing within their sprints or supplement it with bug bounty programs for added coverage.
Why It Matters
Web applications serve as public-facing access points and often interact with databases, user accounts, and core business logic. A single weakness can trigger a data breach or compromise business operations. Regular testing helps reveal issues early and supports safer application development.
3. Client-Side Penetration Testing
Client-side penetration testing focuses on identifying vulnerabilities in desktop applications and user-side software. These are the programs that run on individual endpoints, such as employee workstations or personal laptops, and can include browsers, email clients, document editors, and custom business tools.
Unlike network or web application testing, which evaluates infrastructure or server-side logic, client-side tests look at how applications respond to malicious input or scripts when executed locally. This helps uncover weaknesses that attackers might exploit through phishing, file delivery, or browser-based attacks.
What It Targets
Client-side applications often form the first line of contact between users and external content. Common targets for testing include:
- Web browsers (Chrome, Firefox, Safari)
- Email clients (Outlook, Thunderbird)
- Productivity suites (Microsoft Office, Adobe Acrobat)
- Communication tools (Slack, Zoom)
- Custom desktop software
- Supporting frameworks (Flash, Silverlight, Java applets)
Many attacks target these interfaces by tricking users into interacting with malicious documents, links, or scripts.
Common Vulnerabilities
Client-side penetration testing identifies weaknesses that allow attackers to run malicious code or manipulate application behavior. Typical issues include:
- Cross-site scripting (XSS)
- Clickjacking
- HTML injection
- Cross-Origin Resource Sharing (CORS) misconfigurations
- Open redirection
- Form hijacking
- Local file inclusion
- Weak sandboxing or input validation
- Malware execution via document macros or file uploads
Exploitation often begins with user interaction, such as opening an email attachment or clicking a crafted URL.
Tools Commonly Used
- BeEF (Browser Exploitation Framework)
- Burp Suite (with appropriate extensions)
- MITMf (Man-in-the-Middle Framework)
- Exploit DB for known client-side CVEs
- Custom scripts for payload testing
Testers also use sandbox environments to safely run and monitor application behavior under simulated attacks.
Why and When to Test
Client-side applications are common attack entry points, especially in phishing and targeted malware campaigns. Testing is recommended:
- During regular security assessments, especially in organizations with many endpoints
- When deploying new desktop software
- After major updates to email, browser, or document-processing tools
- As part of a security awareness program tied to user behavior
These tests are often conducted alongside social engineering simulations or endpoint protection audits to create a full picture of the organization’s exposure.
4. Wireless Penetration Testing
Wireless penetration testing focuses on identifying vulnerabilities in an organization’s wireless infrastructure. These tests assess how securely devices connect to Wi-Fi networks and how well the network protects sensitive data from interception, tampering, or unauthorized access.
Wireless networks are particularly attractive to attackers because they can be accessed without physically entering a building. If not properly secured, wireless access points can become entry doors to the internal network, allowing attackers to bypass perimeter defenses.
Scope of Testing
Wireless penetration tests typically examine:
- Wi-Fi access points (APs)
- Wireless routers and controllers
- Laptops, smartphones, tablets, and IoT devices on the network
- Wireless encryption protocols (e.g., WPA2, WPA3)
- Authentication methods (e.g., PSK, 802.1X)
- Signal leakage beyond secure boundaries
- Guest Wi-Fi networks and network segmentation
Testers may also analyze the radio frequencies used, look for rogue access points, and determine whether attackers could exploit misconfigured settings to join or eavesdrop on the network.
Common Weaknesses Detected
Some of the most frequent findings in wireless penetration tests include:
- Use of outdated encryption standards (e.g., WEP or weak WPA)
- Unsecured or misconfigured guest networks
- Rogue access points added without authorization
- Weak or reused passphrases
- MAC address spoofing vulnerabilities
- Inadequate access controls between wireless and internal systems
- Signal coverage extending beyond physical boundaries, allowing outside access
Attackers can exploit these flaws using tools that allow passive monitoring, fake AP setups, or direct brute force attempts against handshakes and credentials.
Tools Commonly Used
Open-source tools:
- Aircrack-ng: Captures packets and performs WPA/WPA2 cracking
- Kismet: Wireless packet sniffer and network detector
- Wireshark: Analyzes captured traffic
- Bettercap: Conducts MITM attacks on wireless networks
- Wifite: Automates attack sequences against encrypted Wi-Fi networks
Hardware:
- WiFi Pineapple: Used to create rogue APs or intercept wireless traffic
- USB Wi-Fi adapters with monitor mode capability
- NUC (Next Unit of Computing) for remote deployment scenarios
These tools allow testers to simulate real-world attacks, including signal jamming, credential capture, and network spoofing.
When to Perform the Test
Wireless penetration testing is recommended:
- During annual security assessments
- After deploying new access points or wireless configurations
- When moving into new office locations
- As part of post-compromise investigations or incident response drills
Testing is typically done on-site, but remote setups can be arranged by placing pre-configured hardware at the target location.
Why It Matters
Wireless networks serve as invisible extensions of the corporate environment. If attackers can access the network without being noticed, they can bypass firewalls, monitoring tools, and other controls. A successful wireless penetration test helps ensure that all endpoints communicate securely and that weak links are discovered before they’re exploited.
5. Social Engineering Testing
Social engineering penetration testing focuses on the human element of security. Instead of targeting devices, applications, or network infrastructure, these tests assess how susceptible employees are to deception and manipulation. The goal is to evaluate how attackers might exploit trust, curiosity, or fear to bypass technical safeguards and gain access to sensitive data or systems.
Social engineering is responsible for the vast majority of successful breaches. According to industry reports, over 90% of cyber attacks begin with some form of social engineering, making this one of the most important penetration testing types.
Common Attack Methods
A typical gray box penetration testing approach is often used here, where the tester knows limited internal details but not everything, mimicking a partially informed attacker.
These simulations include:
- Phishing: Deceptive emails that prompt users to click malicious links, download files, or submit credentials on fake websites.
- Vishing: Voice calls from fake support agents or authority figures attempting to extract sensitive data.
- Smishing: Phishing delivered through text messages, often using fake delivery alerts or urgent login requests.
- Tailgating: Following authorized personnel into restricted areas without proper access credentials, closely related to internal penetration testing where access is simulated from inside the organization.
- Pretexting: Using fabricated identities or scenarios to build trust and gather confidential data.
- Impersonation: Pretending to be a vendor, colleague, or IT support member to gain access.
- Dumpster diving: Retrieving discarded documents or media that might contain passwords, usernames, or confidential information.
Each tactic helps identify security vulnerabilities in human behavior, showing where attackers might succeed without needing to breach code or systems.
Testing Tools and Platforms
Open-source and commercial tools include:
- Modlishka: Reverse proxy tool for phishing simulations
- Evilginx: Man-in-the-middle attack platform used for advanced phishing
- KnowBe4: Commercial training and testing platform for phishing awareness
- Gophish: Lightweight open-source phishing framework
These platforms help security professionals build simulations, track outcomes, and tailor training to address specific gaps.
When to Perform the Test
Social engineering tests are recommended:
- As part of employee security awareness programs
- After onboarding new staff
- On a recurring basis (e.g., quarterly or biannually) to track improvements
- Following major phishing incidents or changes in company structure
Some organizations conduct these tests without notice, while others inform staff in advance. Both approaches serve different goals and can be part of broader cyber security strategies.
Why It Matters
Even the most secure operating systems and tools can fail if an attacker convinces an employee to click a malicious link, share credentials, or open a door. Social engineering penetration testing helps identify security vulnerabilities that no firewall or software patch can fix. The results guide policy updates, focused training, and stronger connections between teams and security staff.
6. Physical Penetration Testing
Physical penetration testing evaluates how well an organization can prevent unauthorized access to its buildings, hardware, and other physical assets. Unlike other forms of testing that target digital systems, this method focuses on real-world security, door locks, security guards, access cards, surveillance systems, and employee procedures.
This type of test simulates how a determined intruder might bypass physical defenses to steal equipment, access sensitive data, or install rogue devices like keyloggers or wireless sniffers.
What It Involves
A physical pen test often begins with surveillance. Testers observe facility layouts, employee routines, badge protocols, and entry points. The test may include:
- Attempting to gain access by tailgating employees
- Cloning access cards or using lockpicking tools
- Impersonating delivery staff, contractors, or maintenance workers
- Placing rogue devices inside server rooms or network closets
- Extracting equipment or documents from unattended areas
- Checking for unattended workstations, unsecured backups, or exposed whiteboards
The goal is not just to bypass security, but to determine how easily an intruder could reach high-value assets without being challenged or detected.
Key Weaknesses Uncovered
Physical tests often reveal flaws that are overlooked in traditional audits, such as:
- Propped-open doors or unattended entrances
- Inactive or poorly placed surveillance cameras
- Lack of visitor screening or sign-in processes
- Insufficient access control segmentation between sensitive and general areas
- No clear response plan when unauthorized individuals are noticed
Misplaced devices containing sensitive data (e.g., USB drives, laptops)
Many organizations invest heavily in cybersecurity while neglecting physical entry points that can bypass digital protections entirely.
Tools Commonly Used
- RFID cloning tools (e.g., Proxmark3)
- Lockpick sets or bump keys
- USB drop devices
- Hidden cameras or microphones
- Covert wireless access devices
- Surveillance gear for reconnaissance
Testers use these tools to simulate realistic intrusion methods that a motivated attacker could attempt.
When to Conduct a Physical Penetration Test
Physical penetration testing is particularly valuable:
- After office relocations or renovations
- When sensitive systems are located in shared buildings
- During mergers or expansion into new regions
- When physical access policies have recently changed
- As part of a broader red team engagement
Testing should be done periodically to account for changing staff, processes, and building layouts.
Why It Matters
If an attacker can enter a server room, plug in a malicious device, or walk away with an unencrypted laptop, then no amount of digital security will stop them. Physical penetration testing reveals gaps in building access controls, employee procedures, and emergency response, areas that often fall outside the scope of traditional IT security but can lead to serious breaches.
7. API Penetration Testing
API penetration testing focuses on identifying security weaknesses in application programming interfaces (APIs), which act as communication channels between different software systems. APIs often handle sensitive data and system commands, making them a prime target for attackers.
Poorly secured APIs can expose user information, business logic, or backend systems, even if the rest of the application appears secure.
As organizations continue to adopt microservices, cloud integrations, and mobile apps, the number of exposed APIs has increased significantl, raising the overall attack surface.
What It Targets
An API penetration test evaluates both public and internal APIs. These may be:
- REST or SOAP APIs used by mobile and web apps
- APIs supporting third-party integrations
- Backend APIs used for internal services
- GraphQL endpoints
The test reviews endpoints for improper input handling, misconfigured authentication, excessive permissions, and logic flaws. It also examines how error messages, response codes, and headers behave when manipulated.
Common Vulnerabilities
Some of the most common API issues include:
- Broken authentication (e.g., missing token validation)
- Insecure direct object references (IDOR)
- Improper rate limiting or lack of throttling
- Excessive data exposure in response payloads
- Injection flaws (e.g., SQL or command injection via API parameters)
- Improper authorization between user roles
- Replay attacks using reused or predictable tokens
- Weak cryptographic controls over data transmission
These flaws allow attackers to impersonate users, extract unauthorized data, or take actions on behalf of others.
Tools Commonly Used
Open-source tools:
- OWASP ZAP: For intercepting and fuzzing API requests
- Postman: For manual request crafting and validation
- Insomnia: A REST client for testing API endpoints
- Swagger/OpenAPI tools: For static analysis of API specifications
Commercial tools:
- Burp Suite Professional: Widely used for manipulating requests and analyzing API responses
- APISec: Automated testing focused on security coverage of APIs
- NoName Security: For API visibility and vulnerability detection
These tools allow testers to test known endpoints, manipulate payloads, and simulate unauthorized access attempts.
When to Perform API Testing
API testing should be performed:
- During the development of new services or integrations
- After changes to authentication, rate limiting, or data handling logic
- When exposing internal services to external partners
- As part of a scheduled security program alongside web app testing
Organizations deploying APIs in mobile, web, or SaaS applications should include this in their security process.
Why It Matters
APIs often sit directly between users and critical backend systems. If not properly secured, they become one of the most efficient entry points for attackers. Testing helps confirm that APIs enforce proper access controls, minimize data exposure, and handle unexpected input safely. Given how APIs now support core business operations, their security cannot be left to assumptions.
8. Mobile Application Penetration Testing
Mobile application penetration testing focuses on evaluating the security of mobile apps developed for platforms like Android and iOS. These applications often process sensitive data such as login credentials, personal information, financial transactions, and location history, making them high-value targets for attackers.
This type of testing aims to identify vulnerabilities within both the client-side application and its communication with backend services, APIs, and data storage layers.
What It Involves
A mobile app test typically includes:
- Reviewing how the app handles data storage on the device
- Inspecting how it communicates with servers over the network
- Checking how it manages authentication and authorization
- Testing embedded components such as third-party SDKs or plugins
- Analyzing the binary for reverse engineering or tampering risks
Both rooted (Android) or jailbroken (iOS) environments are often used in testing to simulate how attackers might bypass built-in OS restrictions.
Common Vulnerabilities
Common security flaws uncovered during mobile penetration testing include:
- Insecure data storage: Sensitive information saved in plain text or without access control
- Weak server-side controls: Poor input validation or exposed backend APIs
- Unencrypted or poorly encrypted communication: Allowing traffic to be intercepted
- Hardcoded credentials or tokens: Embedded in the app binary
- Improper authentication and session handling: Allowing session hijacking or replay attacks
- Data leakage through logs, caches, or background processes
- Reverse engineering risks: Due to lack of code obfuscation or signing checks
These flaws can lead to account takeovers, data exposure, or full compromise of the user experience.
Tools Commonly Used
Open-source tools:
- MobSF (Mobile Security Framework): For static and dynamic analysis
- Frida: For runtime instrumentation and API hooking
- Drozer: For Android app testing and exploitation
- APKTool and JADX: For decompiling Android APKs
- Objection: Used for runtime exploration of iOS and Android apps
Commercial tools:
These tools help testers analyze how the app behaves, whether data is handled securely, and how resistant it is to tampering or reverse engineering.
When to Test
Mobile penetration testing is essential:
- Before launching a new app
- After major updates or refactoring
- When adding payment, location, or biometric features
- During compliance reviews (e.g., HIPAA, PCI DSS)
- As part of a broader secure development lifecycle
Security must be tested regularly as mobile platforms, OS versions, and app features evolve.
Why It Matters
Mobile apps often act as gateways to user accounts, private data, and connected services. A security flaw in a mobile application can lead to stolen credentials, unauthorized actions, or exposure of sensitive information. Penetration testing ensures these apps are resilient to attacks and that data remains protected across every interaction point.
9. Cloud Penetration Testing
Cloud penetration testing evaluates the security of services, applications, and infrastructure deployed in cloud environments. As businesses continue shifting to cloud platforms like AWS, Azure, and Google Cloud, understanding and securing those environments has become essential.
The purpose of cloud testing is to uncover misconfigurations, exposed assets, and insecure interfaces that could allow attackers to compromise cloud-based resources.

Unlike traditional systems, cloud environments operate under a shared responsibility model, the cloud provider secures the infrastructure, while the customer is responsible for their configurations, user access, and data.
Cloud penetration testing focuses on different areas depending on the service model: IaaS, PaaS, or SaaS.
In IaaS, customers manage the OS, applications, and network settings. Testing targets access controls, unpatched virtual machines, public storage exposure, firewall rules, and unauthorized access in activity logs.
In PaaS, developers handle the code but not the infrastructure. Testing looks at API and app logic security, exposed environment variables, data flow between the app and platform, and use of platform authentication and storage features.
In SaaS, users have limited control. Testing checks role-based access, tenant data separation, input validation, authentication, and encryption. It focuses on user-facing behavior and configuration.
Common Vulnerabilities
Cloud penetration testing frequently reveals:
- Misconfigured storage (e.g., open S3 buckets, public blobs)
- Overly permissive IAM roles and policies
- Weak MFA enforcement or password policies
- Exposed admin panels or APIs
- Insecure container configurations
- Default credentials or unprotected instances
- Lack of logging or alerting on sensitive actions
These issues can allow attackers to access cloud consoles, extract sensitive data, or escalate privileges.
Tools Commonly Used
Open-source tools:
- Prowler: For auditing AWS environments
- ScoutSuite: Multi-cloud configuration analysis
- CloudMapper: Visualizes and audits AWS setups
- PacBot: Policy-as-code enforcement and compliance tracking
Commercial tools:
These tools provide visibility into configurations, assets, and identity usage patterns within cloud environments.
When to Perform the Test
Cloud penetration testing should be conducted:
- After migrating workloads to the cloud
- Following major infrastructure changes
- When deploying new APIs or cloud-native applications
- As part of routine annual assessments or compliance efforts
It’s important to follow cloud provider rules, some vendors require prior approval before conducting active testing, especially on production services.
Why It Matters
Cloud services offer flexibility, scalability, and convenience, but they also introduce complexity. A single exposed bucket or misconfigured policy can lead to massive data leaks or compromised infrastructure. Cloud penetration testing provides the visibility and assurance needed to operate securely in these environments and confirms that configurations match the organization’s intent.
10. IoT Penetration Testing
IoT (Internet of Things) penetration testing focuses on evaluating the security of connected devices that interact with networks, software, and users. These devices can range from sensors and wearables to smart appliances and industrial controllers.
Many IoT devices are embedded in business operations, healthcare systems, and home networks, often without the same level of security scrutiny applied to traditional IT assets.
IoT testing examines not just the device itself, but the entire ecosystem surrounding it, including mobile applications, cloud penetration testing, and communication channels. In some cases, external penetration testing may also apply, especially when devices communicate over public networks.
What It Covers
IoT penetration testing includes analysis across several layers:
- Device layer: Firmware, hardware interfaces (e.g., UART, JTAG), and physical penetration testing for hardware access points
- Network layer: Communication protocols like Wi-Fi, Bluetooth, Zigbee, MQTT, and cellular connections; this ties into network penetration testing and wireless networks
- Application layer: Mobile or web applications used to manage or monitor devices; may include mobile application penetration testing
- Cloud/backend: APIs and cloud services used to store or retrieve device data; penetration testing services sometimes include testing these cloud APIs
A complete test examines how these layers interact, how data is transmitted and stored, and whether security controls or encryption are consistently applied.
Common Vulnerabilities
IoT devices often ship with minimal protections, resulting in widespread issues such as:
Hardcoded credentials
- Insecure firmware updates
- Lack of encryption in data transmission
- Unauthenticated communication with backend servers
- Unprotected debug interfaces
- Local storage of sensitive data without access control
- Mobile application flaws (e.g., reverse engineering, weak authentication)
These weaknesses can be used to gain access, hijack devices, or pivot into internal network segments. Depending on the approach, white box penetration testing may uncover issues in source code, while black box penetration testing simulates an outsider probing for vulnerabilities without internal access.
Tools Commonly Used
- Firmadyne: For firmware analysis and emulation
- Binwalk: Unpacks and analyzes firmware images
- Ghidra: Reverse engineering tool for binaries
- Wireshark: Network traffic analysis
- Shodan: For finding exposed IoT devices on the internet
- OWASP IoT Testing Guide: Reference for OWASP best practices and testing checklists
Hardware tools such as UART adapters, JTAG debuggers, and logic analyzers are also used for deeper security testing of physical components.
When to Perform the Test
IoT penetration testing should be conducted:
- During product development and before release
- When deploying devices in sensitive or regulated environments
- After updates to firmware or mobile applications
- As part of security certification efforts for industries like healthcare, automotive, or industrial controls
Ethical hackers are typically engaged for such testing, and testing may include gray box testing depending on the target’s complexity and available information.
Why It Matters
IoT devices are often overlooked during security assessments, yet they can serve as entry points to critical systems. An insecure smart thermostat, surveillance camera, or industrial controller can give attackers a foothold in an otherwise secure environment. Penetration testing helps identify weak links across the device ecosystem and supports safer deployment of connected technologies. Some firms also conduct penetration testing methods like social engineering tests in parallel to evaluate how attackers might exploit both human and technical vectors.
Methods of Penetration Testing
Below are the four main methods of penetration testing , Black Box, White Box, Grey Box, and Hybrid, each designed to simulate specific threat scenarios and provide distinct insights into system vulnerabilities.
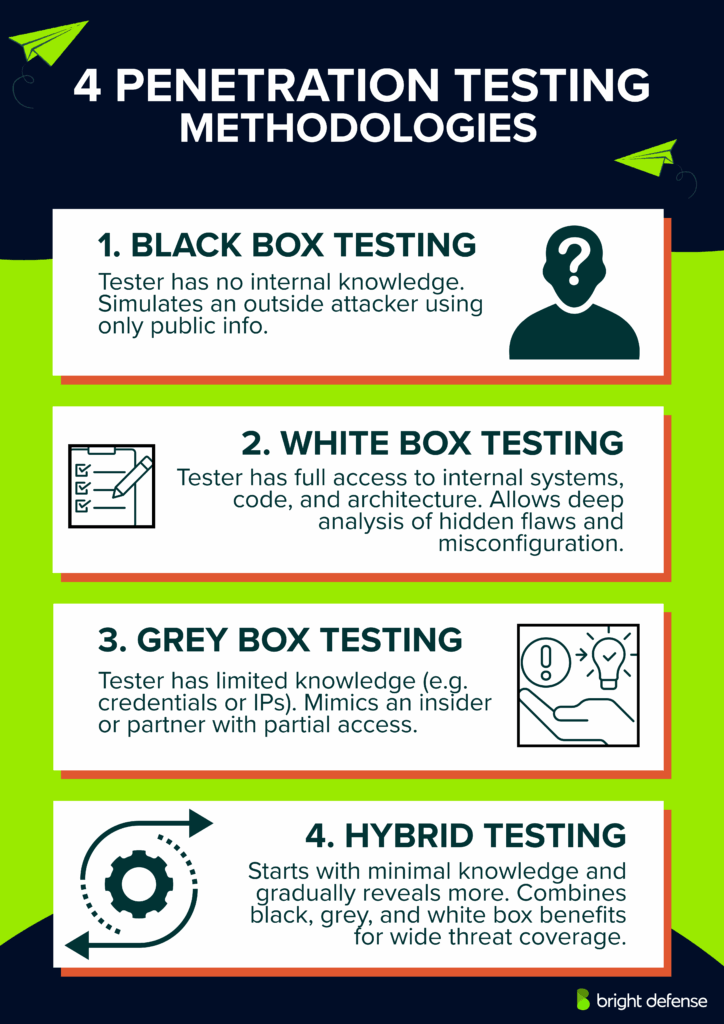
1. Black Box Testing
Black box penetration testing involves simulating an attack from an outsider’s point of view. Testers have no prior access to the organization’s internal systems, source code, or infrastructure documentation. They rely on external reconnaissance methods, including open-source intelligence (OSINT), domain name system (DNS) enumeration, network scanning, and public vulnerability databases.
The objective centers on evaluating perimeter defenses, uncovering publicly exposed assets, and identifying entry points. Common targets include firewalls, load balancers, web servers, APIs, and external portals. Techniques such as phishing, exploitation of exposed services, and web application attacks (e.g., SQL injection, cross-site scripting) are commonly used.
Black box testing provides an accurate depiction of how a real-world attacker without privileged access would attempt to breach the environment, offering valuable insight into how effective external defenses truly are.
2. White Box Testing
In white box penetration testing, testers receive full disclosure of the organization’s technical environment. This includes access to architecture diagrams, source code repositories, system configurations, network topology, and administrative credentials. White box testing eliminates guesswork, enabling a deep and thorough analysis of the environment.
Testers scrutinize application logic flaws, insecure coding practices, misconfigurations, and privilege escalation paths. Techniques like static code analysis, configuration review, and manual code inspection play a central role.
Because testers understand the internal workings, white box testing often reveals hidden vulnerabilities that external attacks could not expose, such as backdoors, poor cryptographic implementations, and logic errors. It helps organizations assess risks posed by insider threats and ensures that security controls are correctly applied across systems and applications.
3. Grey Box Testing
Grey box penetration testing blends aspects of both black box and white box approaches. Testers are provided limited information, such as user accounts with specific roles, selected network ranges, or application endpoints, simulating the conditions of an attacker with partial knowledge, such as a disgruntled employee or a contractor.
This method allows for focused testing on systems where the attacker would not have complete ignorance but also lacks privileged access. Grey box testing highlights flaws in authentication mechanisms, access control policies, and session management. It helps organizations understand what damage a malicious actor could cause if they obtained some, but not full, information.
By targeting privilege escalation paths and misused permissions, grey box testing uncovers vulnerabilities that attackers could exploit after gaining an initial foothold, making it a practical option for real-world threat modeling.
4. Hybrid Testing
Hybrid penetration testing merges the techniques and goals of black box, white box, and grey box testing into a unified process. Testing begins from an outsider’s perspective with no prior information and gradually incorporates internal access and documentation. This staged approach reflects the evolving tactics of real attackers, who often start blind and escalate their access over time.
Hybrid testing covers a full spectrum of potential threats: external attacks targeting public assets, internal threats exploiting configuration errors, and mid-level threats based on partial knowledge. It involves dynamic adjustment of tactics based on findings at each phase.
The benefit lies in its ability to present a broader view of the security posture, combining surface-level exposure assessments with deep internal audits. Hybrid testing identifies vulnerabilities across all tiers, from external-facing systems to backend infrastructure, and provides organizations with prioritized, realistic threat assessments based on different levels of attack
How Can Bright Defense Help You With Different Types of Penetration Testing?
At Bright Defense, we help you find and fix security weaknesses before attackers can exploit them. Our penetration testing services cover every layer of your organization, using real-world techniques to assess your defenses.
We perform network penetration testing to reveal gaps in your internal and external infrastructure, closing off the routes threat actors often use to gain access.
Through web application testing, we simulate attacks on your websites and APIs to detect issues like injection flaws, broken access controls, and insecure authentication.
For mobile application testing, we analyze your Android and iOS apps to uncover vulnerabilities in code, data storage, and communication channels.
Our wireless testing identifies risks in your Wi-Fi setup, including weak encryption, rogue access points, and insecure configurations.
With social engineering assessments, we test how your team responds to phishing, phone scams, and impersonation attempts that target human behavior.
In physical penetration testing, we attempt to bypass your facility’s physical barriers to show where unauthorized access might be possible.
Each engagement ends with a clear, actionable report. We don’t just point out problems, we help you fix them, step by step, so your security gets stronger where it matters most.
What is Red Teaming? What is the Difference Between Red Teaming and Penetration Testing?
Red Teaming is a security exercise where a group simulates real-world attacks to test how well an organization can detect and respond to threats. It often includes cyber, physical, and social engineering attacks to reflect what a real attacker might do.
The main difference from penetration testing is that pen testing focuses on finding technical vulnerabilities in a specific system, while red teaming tests the organization as a whole, including its people and processes. Pen tests are usually more controlled and visible, whereas red teaming is stealthy and mimics real adversaries more closely.
Pen tests run for days or weeks. Red team work takes longer and stays quiet to feel real. This makes red teaming better suited for testing an organization’s security posture over time.
Pen testers use known tools and methods to break in. Red teams change tactics, write their own tools, and use anything from phishing to physical penetration testing simulates how an intruder might breach facilities and gain unauthorized access.
Pen test reports list flaws and fixes. Red team reports tell how the attack happened, what they reached, and if anyone noticed. These findings often help security professionals evaluate how well systems and staff hold up under real-world threats.
Pen tests suit audits or system checks. Red teaming fits when the goal is to perform penetration tests that mirror persistent threats and uncover deeper blind spots across people, processes, and infrastructure.
Penetration Testing vs Red Teaming
| Feature | Penetration Testing | Red Teaming |
|---|---|---|
| Goal | Find vulnerabilities | Test detection & response |
| Scope | Narrow and predefined | Broad, organization-wide |
| Visibility | Known to defenders | Covert |
| Duration | Short term (days to weeks) | Long term (weeks to months) |
| Methodology | Technical and automated | Adaptive and realistic |
| Output | Vulnerability report | Attack narrative and response insights |
| Blue Team Role | Informed and involved | Uninformed and reactive |
FAQs
Penetration testing includes black box, white box, and gray box methods. Black box testing simulates an external attack with no system knowledge. White box testing gives full access to source code and system details for a deep security audit. Gray box testing uses limited info, simulating an insider threat.
The stages are pre-engagement, reconnaissance, discovery, vulnerability analysis, exploitation, reporting, and remediation. Testers use OSINT in reconnaissance, find systems in discovery, scan for flaws in analysis, test attacks during exploitation, then write a penetration test report and verify fixes through a retest.
The five phases are reconnaissance, scanning, vulnerability assessment, exploitation, and reporting. Tools like Nmap and Nessus help identify open ports and flaws. Exploitation tests real-world risk. The report covers findings and mitigation steps.
Network penetration testing is the most common. It checks firewalls, routers, and servers for vulnerabilities attackers could exploit. This helps assess exposure to external threats and improve overall network security.
Get In Touch



