What is Cloud Penetration Testing?
As more companies move to the cloud, keeping those environments secure becomes a priority.
Cloud penetration testing is a way to simulate real-world attacks and spot weaknesses in cloud setups like misconfigured storage, exposed APIs, or overly broad permissions.
It focuses on the areas you control, since cloud providers and users share responsibility for security. Testing helps reduce risk before someone else finds the gaps.
Keep reading to learn how cloud penetration testing works, why it matters, and what to watch out for during the process.
Key Takeaways
- Cloud penetration testing simulates real attacks on cloud environments to detect misconfigurations, exposed APIs, and weak access controls
- Unlike traditional testing, it targets areas under customer control, such as IAM policies, storage settings, and workload permissions
- Common test types include external, internal, black box, white box, and gray box, each revealing different layers of risk
- The process identifies privilege issues, lateral movement paths, insecure serverless functions, and storage exposure across AWS, Azure, and GCP
- Professional testing teams provide clear reports and practical fixes that support both remediation and compliance with SOC 2, PCI-DSS, and ISO 27001
What is Cloud Penetration Testing?
Cloud penetration testing is the process of simulating attacks on cloud environments to find security gaps before real attackers do. It targets issues like misconfigured storage, exposed endpoints, and weak access controls.

Since cloud security is a shared responsibility between the provider and the customer, these tests focus on what the organization manages, things like identity, network settings, and workload configurations.
How Does Cloud Penetration Testing Differ from Standard Penetration Testing?
Cloud penetration testing focuses on the parts of the environment managed by the customer, like IAM roles, storage, and APIs, while avoiding areas controlled by the provider. Traditional testing usually covers full systems without those limits. Cloud tests look for misconfigurations and privilege issues in dynamic environments, using cloud-specific tools. They often require provider approval, unlike standard tests, which are more static and under full control of the organization.
Types of Cloud Penetration Testing
Cloud penetration testing helps simulate real-world attacks to reveal these hidden issues before they lead to a breach. Below are the major types and methods used to test the security of cloud-based infrastructure:
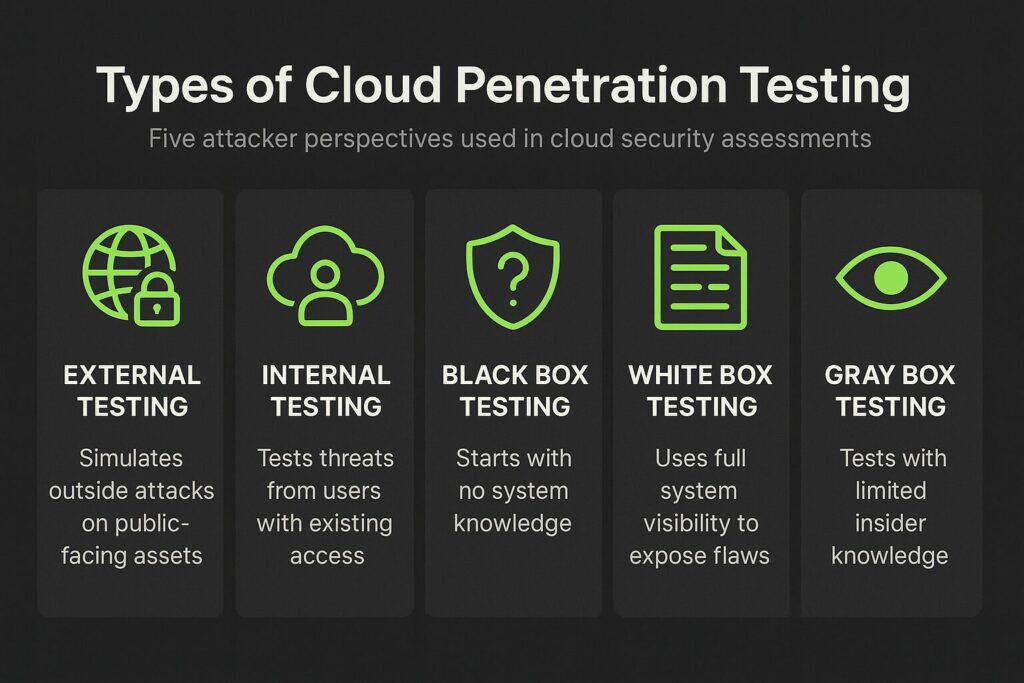
- External testing targets cloud assets that are accessible from the public internet. These can include cloud-hosted websites, APIs, DNS records, or storage services like AWS S3. The purpose of this testing is to simulate an attacker who has no internal access and is trying to breach the environment from the outside.
- Internal testing assumes the attacker already has some level of access, like a user account or access to a private network within the cloud environment. This type is used to find what damage a rogue employee or compromised insider could cause through privilege escalation or lateral movement.
- Black box testing provides no prior information to the tester. The tester doesn’t know the cloud provider, services, architecture, or credentials. This method closely mimics an external attacker starting from zero.
- White box testing gives the tester full knowledge of the cloud infrastructure. They may receive documentation, source code, credentials, and architectural diagrams. This allows a very targeted approach to finding weaknesses that might be missed otherwise.
- Gray box testing offers limited insight, such as a standard user account or some documentation, while keeping other parts of the environment hidden. It represents the situation where an attacker has some but not full access, like a compromised user account.
Stages in Cloud Penetration Testing
Here is a breakdown of the key stages involved in cloud penetration testing, outlining the process from planning to reporting. Each stage targets a specific aspect of cloud security.

Step 1. Planning and Scoping
This is the foundation of the engagement. The testing team defines the scope with the client, specifying:
- Cloud platforms (e.g., AWS, Azure, GCP)
- Services under assessment (e.g., storage buckets, IAM, serverless functions)
- Testing type (external, internal, black box, white box)
- Compliance or legal requirements
This phase avoids unauthorized access and clarifies responsibilities.
Step 2. Reconnaissance
The team collects publicly accessible data to understand the target’s cloud environment:
- Subdomain enumeration
- Discovery of public S3 buckets or blob storage
- DNS records, metadata endpoints
- Leak hunting through GitHub, paste sites, or exposed configuration files
This helps identify misconfigurations or weak exposure points before active engagement begins.
Step 3. Threat Modeling
The testers analyze the gathered data to map potential attack paths. This includes:
- Evaluating IAM policies and roles
- Pinpointing data exposure vectors
- Spotting overly permissive access (e.g., public read/write access)
- Reviewing trust relationships between services or accounts
This sets up the attack strategy.
Step 4. Exploitation
This step tests real-world vulnerabilities and misconfigurations. Examples include:
- Gaining access through misconfigured IAM roles or credentials
- Exploiting serverless code logic flaws (e.g., Lambda or Cloud Functions)
- Accessing unsecured cloud storage or databases
- Abusing default configurations or escalation paths (e.g., privilege escalation)
The goal is to simulate actual attacks and observe the resulting access or impact.
Step 5. Post-Exploitation
Once access is achieved, the focus shifts to exploring further risk:
- Lateral movement across cloud services
- Access to sensitive resources (e.g., backups, customer data, secrets)
- Persistence mechanisms (e.g., rogue roles, scheduled functions)
- Use of internal APIs or services
This determines how much damage could occur in a real breach.
Step 6. Cleanup
The testers remove any temporary resources or credentials they created. This avoids leaving behind active artifacts or permissions that could pose a risk.
Step 7. Reporting
The findings are documented in a structured report with:
- Technical details of vulnerabilities
- Proof-of-concept examples
- Potential impact per issue
- Recommended actions
How Much Does Cloud Pentesting Cost?
In 2025, cloud penetration testing typically ranges from $10,000 to $50,000, with basic tests starting near $8,000 and complex, compliance-heavy engagements exceeding $50,000. Costs depend on scope, test type, manual vs. automated effort, and add-ons like compliance reporting or retesting. Most small to mid-sized setups fall between $10k and $25k.
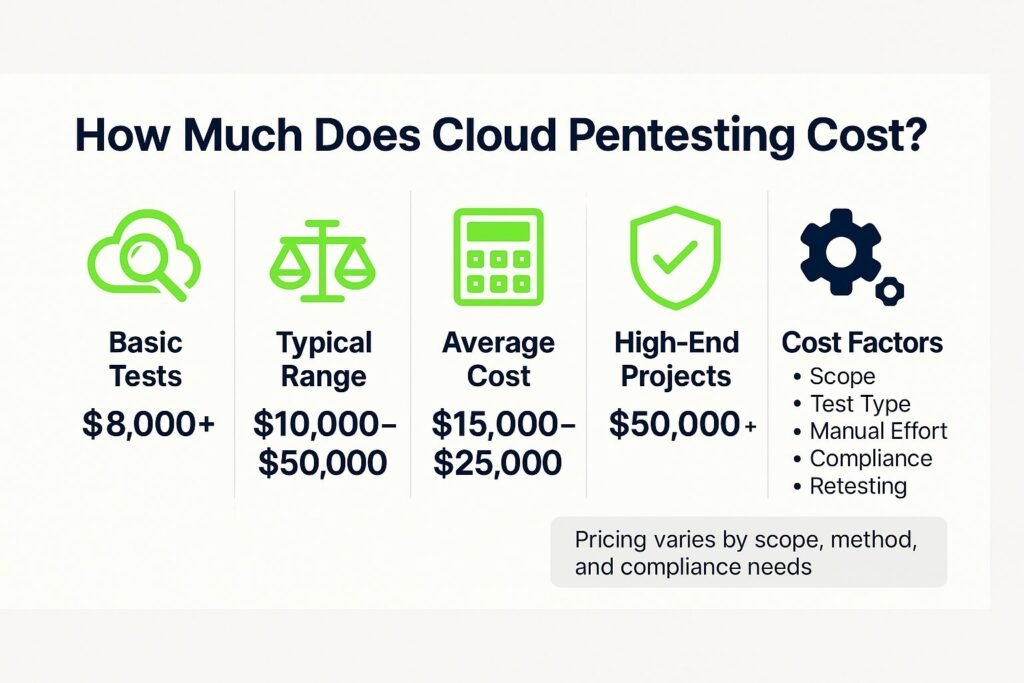
Cloud penetration testing in 2025 typically costs between $10,000 and $50,000, with averages falling around $15,000 to $25,000, though simpler tests might start closer to $8,000 and extremely complex, compliance-heavy or black-box engagements can exceed $50,000.
Price varies based on scope (number of cloud services, environments, IAM setups), test type (black‑box, gray‑box, white‑box), depth of manual effort versus automated scanning, and added needs like compliance documentation, retesting, and remediation support
Entry-level packages aimed at small to mid‑sized setups often range from $10k to $25k, while broader, cross‑platform engagements or those with compliance obligations (e.g. PCI-DSS, HIPAA) can push total cost above $40k–$50k.
Benefits of Cloud Pentesting for Your Company
Cloud penetration testing helps your company find and fix security gaps in cloud setups, access controls, and configurations. Here are the main benefits:

1. Exposure Detection Across Cloud Assets
Cloud penetration testing uncovers vulnerable misconfigurations, exposed services, and weak access controls across cloud service providers like AWS, Azure, and GCP. This includes overlooked elements such as:
- Unrestricted S3 buckets or blob containers
- Over-permissive IAM roles and policies
- Inactive but exposed services (e.g. abandoned EC2 instances or VMs)
Unlike traditional scans, these tests replicate real-world tactics used to access these gaps.
2. Reduced Risk of Breach or Data Loss
Simulating attacks against your cloud infrastructure allows your security team to understand the potential impact of a successful compromise. It highlights:
- Where unauthorized data extraction could occur
- Whether lateral movement is possible between environments
- How privilege escalation might be achieved from misconfigured permissions
This gives decision-makers evidence to support remediation actions before real attackers exploit those paths.
3. Testing Identity and Access Management (IAM)
Cloud penetration tests stress-test IAM configurations. That includes:
- Verifying MFA requirements for privileged accounts
- Detecting privilege creep from nested roles or outdated permissions
- Checking for unused or unmonitored access keys
This is vital for organizations with federated access models or multiple cloud tenants.
4. Verification of Compliance and Internal Policies
Cloud pen testing supports compliance efforts under frameworks like:
- ISO 27001
- SOC 2
- HIPAA
- PCI DSS
It provides audit-ready evidence that cloud environments are reviewed under real-world conditions, not just policy checklists. This helps your company maintain both internal and regulatory confidence.
5. Visibility Into Cloud-Specific Attack Paths
These assessments reveal attack surfaces unique to cloud environments, such as:
- Serverless functions accepting unvalidated inputs
- Over-reliance on token-based trust without proper revocation
- Excessive reliance on third-party services with weak integrations
Simulating how attackers can pivot or chain these weaknesses, you get a clearer view of systemic exposure.
Cloud Penetration Testing Best Practices
Cloud pentesting requires awareness of provider policies, an understanding of ephemeral services, and a deep focus on identity-driven access.
The following practices help guide effective and safe testing efforts across cloud environments:
- Define clear test boundaries covering specific cloud assets, environments, and objectives.
- Obtain written authorization detailing allowed actions, timeframes, and emergency contacts.
- Respect cloud provider restrictions and follow their acceptable use and test notification rules.
- Test IAM roles for excessive privileges, misconfigurations, and privilege escalation paths.
- Check cloud storage for public access, weak ACLs, and metadata exposure.
- Analyze network security groups, firewalls, and routing rules for segmentation flaws.
- Inspect serverless and container setups for insecure defaults, exposed secrets, and event risks.
- Use native logging tools to verify visibility into test actions and anomalies.
- Trigger detectable events to assess security team monitoring and alerting capability.
- Search for hardcoded secrets, plaintext credentials, and exposed API tokens.
- Confirm MFA enforcement and key policies limit access based on roles and scopes.
- Deliver a clear report with technical details, impact, and actionable remediation steps.
- Re-test critical issues to validate proper fixes and avoid reintroducing misconfigurations.
- Exclude tests that risk service interruption, such as denial-of-service or destructive exploits.
- Collect and securely store test evidence to support incident response and auditing.
How Can Bright Defense Help You With Cloud Penetration Tests?
Bright Defense helps secure your cloud environments by exposing weak access controls, misconfigurations, and cloud-specific attack paths across AWS, Azure, and GCP. We assess real threats, from IAM risks to unsecured storage and serverless flaws.
Why Choose Bright Defense for Cloud Pen Testing?
- Clear Outcomes: Reports focus on real impact, with remediation steps mapped to your cloud stack.
- Purpose-Built Packages: Choose from Core (essentials), Scale (multi-cloud setups), or Apex (compliance-focused + deep testing).
- Attack-Led Testing: We mimic real adversaries—not just scanners—to show how breaches unfold.
- Compliance Ready: Tests support SOC 2, ISO 27001, HIPAA, and PCI-DSS validation.
FAQs
It’s a security assessment that simulates attacks on cloud infrastructure (e.g., AWS, Azure, GCP) to find misconfigurations, weak access controls, and exposed services.
AWS penetration testing targets services like EC2, S3, IAM, and Lambda to find flaws, while following AWS’s acceptable use policies.
Yes, basic scripting or programming helps in writing exploits, automation, and understanding how applications behave under attack.
A standard pen test evaluates external/internal systems using a defined scope and methods to find and validate security weaknesses.
ISO/IEC 27001 doesn’t mandate pen testing but references it as a control; ISO/IEC 27002 and 27005 provide more guidance.
In cybersecurity, “STP test” isn’t standard; it may refer to a specific organization’s internal process or a misused term.
Cloud pen tests focus on dynamic services like IAM, storage, APIs, and serverless functions, while traditional tests often target fixed infrastructure like on-prem servers and networks.
Yes, testing cloud environments like AWS or Azure usually requires advance notice and approval to comply with provider policies.
Typical targets include misconfigured storage (e.g., public S3 buckets), exposed credentials, overly permissive IAM roles, and vulnerable APIs.
At minimum, once a year or after major changes; high-risk setups may benefit from quarterly or continuous testing.
Get In Touch



