
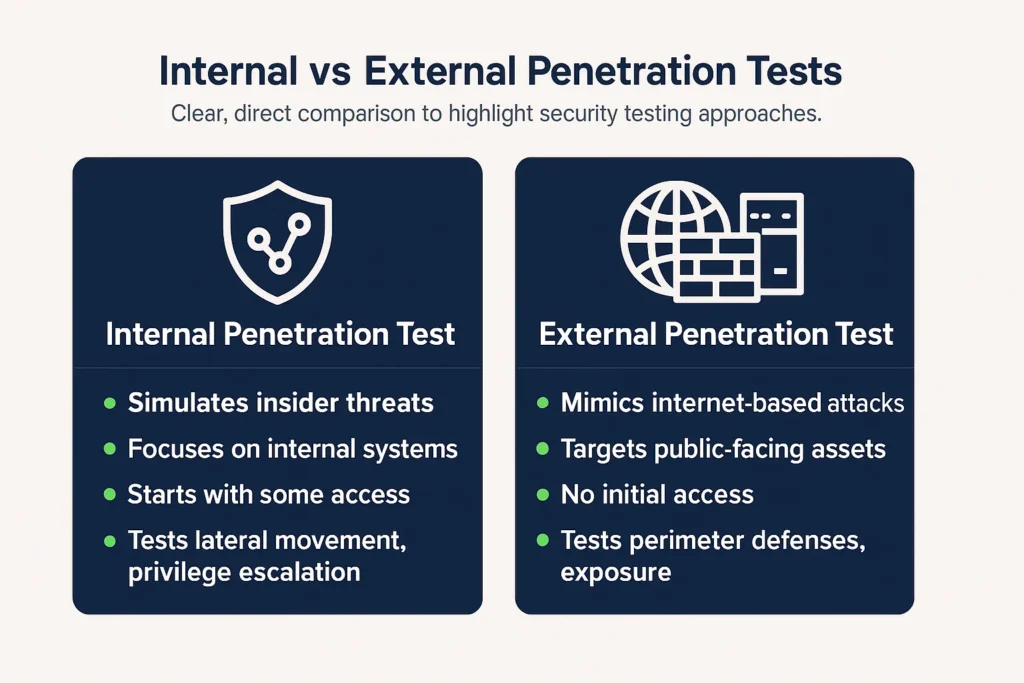
Internal vs External Penetration Testing – Key Differences
Internal and external penetration tests serve different purposes in assessing an organization’s security. One focuses on threats from within the network, such as a compromised device or insider access.
The other looks at how attackers might exploit systems exposed to the internet. Both tests are important, but they target different risks and require different approaches.
This blog explains how they differ, when to use them, and why both matter for building a strong security program.
Key Takeaways
- Internal penetration tests simulate insider threats or compromised devices to find risks like privilege escalation, lateral movement, and sensitive data access.
- External penetration tests simulate internet-based attacks on public-facing assets like web servers, VPNs, and cloud services.
- Internal tests focus on insider access and internal weaknesses, while external tests target perimeter defenses and exposed services.
- Both are recommended annually and after major changes, breaches, or compliance requirements (PCI DSS, SOC 2, ISO 27001).
- Using both gives a full view of risk, covering perimeter security and post-breach impact.
What Is An Internal Penetration Test?
Internal Penetration Testing is a security assessment conducted from within an organization’s network. It simulates an attack that could come from a malicious employee, a contractor, or an attacker who has already bypassed the external defenses.
The aim of a internal pen test is to figure out what kind of access and damage an insider or compromised device could cause. This includes threats like privilege escalation, lateral movement across systems, and unauthorized access to sensitive data.
Typical Scenarios
- A rogue employee trying to gain access to restricted resources
- A visitor plugging in a malicious USB or device into the internal network
- Malware that infected one machine and is attempting to spread
- An attacker who breached external defenses and now has internal access
Key Focus Areas
- Misconfigured permissions and excessive privileges
- Vulnerable internal applications or services
- Insecure file shares or databases
- Unpatched systems and poor segmentation
- Credential reuse or weak passwords
When to Perform an Internal Penetration Test?
An internal penetration test is useful when there are concerns about insider threats, weak internal controls, or lateral movement risks. It should be considered after major changes to the network, such as segmentation, domain migration, or new security tools.
Testing is also recommended following security incidents involving internal access or when new users gain elevated privileges.
Mergers, acquisitions, and compliance requirements like ISO 27001 or PCI DSS also justify this assessment. At a minimum, internal tests should be done annually. High-risk environments or organizations handling sensitive personal data, financial information, or intellectual property should conduct tests more frequently, such as every six months or after any significant infrastructure updates.
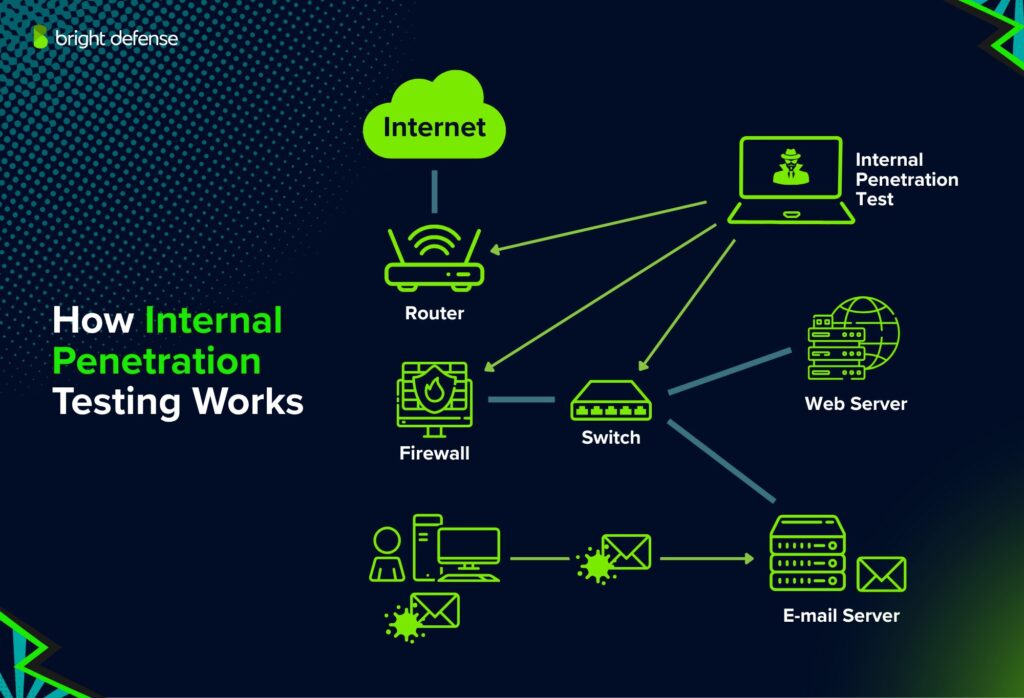
Internal Penetration Testing Methods
Below are common tactics used during internal tests:
- Network Scanning: Identify live hosts, open ports, and exposed services using tools like Nmap or Advanced IP Scanner.
- Service Enumeration: Gather information about running services, versions, and configurations for potential weaknesses.
- Vulnerability Exploitation: Exploit outdated software, default settings, or weak configurations to gain access.
- Password Attacks: Use techniques like password spraying, brute force, and credential dumping to test authentication strength.
- Privilege Escalation: Attempt to move from user to admin using misconfigurations, token impersonation, or reused credentials.
- Lateral Movement: Navigate between systems to simulate how far an attacker could spread once inside.
- Active Directory Mapping: Use tools like BloodHound to analyze relationships, permissions, and trust paths within AD.
- File Share Analysis: Check shared drives for sensitive files, exposed credentials, or misconfigured access controls.
- Persistence Techniques: Test methods for maintaining access, such as creating new users or backdoors (if allowed in scope).
What Is an External Penetration Test?
External Penetration Testing refers to a simulated cyberattack against an organization’s externally accessible systems to find vulnerabilities that an attacker could exploit from outside the network perimeter.

These systems typically include:
- Web servers
- Email servers
- DNS servers
- VPN gateways
- Cloud infrastructure
- Public-facing applications
The purpose of external penetration test is to test what a real attacker could access without any internal credentials or access. This helps organizations understand their exposure from the outside and prevent unauthorized access before it happens.
Key Focus Areas
- Open ports and exposed services
- Misconfigurations in firewalls or routers
- Weak authentication mechanisms
- Vulnerable web applications or APIs
- Data leaks through public sources or metadata
When to Perform an External Penetration Test?
Run an external penetration test whenever you launch new public-facing infrastructure, such as web apps, VPNs, or cloud services. These tests focus on anything exposed to the internet and fall under external network penetration testing.
Also perform a test after:
- System or application updates
- Firewall rule changes
- DNS modifications
These changes can introduce misconfigurations or affect session management, giving attackers an opening.
Schedule tests at least once a year. High-risk industries or fast-moving teams should test more often. Manual vulnerability testing helps catch issues that automated tools might miss.
Run tests before audits like PCI DSS or SOC 2. Also test after any breach or suspicious malicious activities from outside your network. These checks help uncover vulnerabilities detected during scanning and ethical hacking, before attackers find them first.
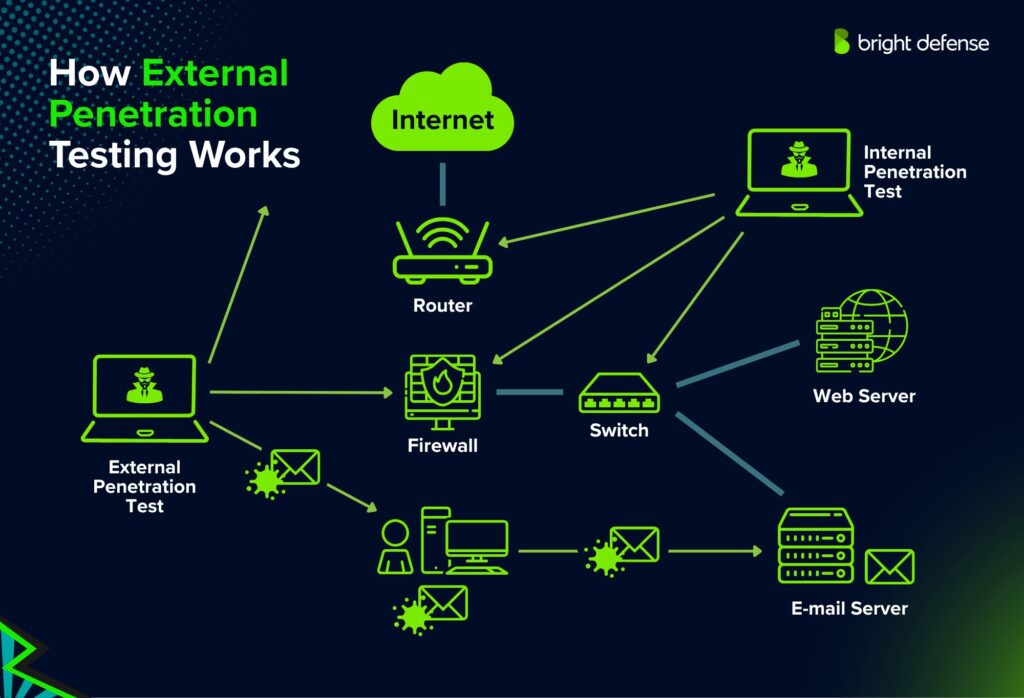
External Penetration Testing Methods
External penetration testing uses a range of methods to identify vulnerabilities and safely exploit weaknesses in internet facing assets. Common techniques include:
- Reconnaissance: Gather public information using WHOIS, DNS lookups, and tools like Shodan or Amass. These steps help map external network exposure and detect early security weaknesses.
- Port Scanning: Detect open ports and active services using tools like Nmap or Masscan. This helps penetration testers evaluate attack surfaces.
- Service Fingerprinting: Identify technologies and versions to find potential security vulnerabilities from unpatched or outdated software.
- Vulnerability Scanning: Use automated tools like Nessus or OpenVAS to flag known flaws. These scans contribute to regular penetration testing routines.
- Web Application Testing: Examine applications for SQL injection, XSS, CSRF, and authentication flaws—key targets in penetration testing services.
- Brute Force Attacks: Test exposed login systems using common or leaked credentials, simulating behavior of a malicious attacker.
- SSL/TLS Inspection: Review encryption settings for weaknesses that could compromise network security.
- Exploitation: Exploit verified flaws safely to confirm actual risk and validate findings.
- Man-in-the-Middle Simulations: If allowed, test for transmission vulnerabilities, adding depth beyond basic manual testing.
Differences Between External and Internal Penetration Tests
External and internal penetration tests both assess an organization’s security posture, but they target different threat scenarios, use different techniques, and yield different insights. Understanding how they differ helps teams prioritize resources and address security risks more effectively.
Let’s find out the key differences between the two options:
External vs Internal Pen Test Comparison Table
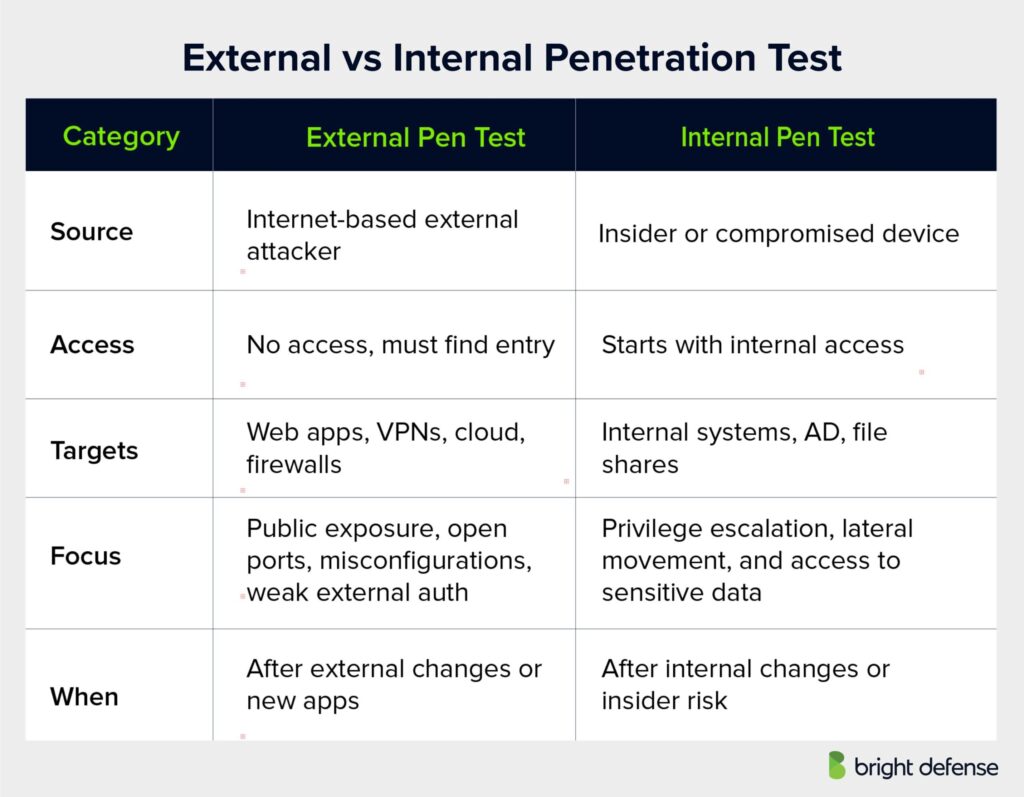
1. Source of Attack
The most obvious distinction lies in the attacker’s position. Internal penetration tests simulate threats that originate from within the organization, either by a malicious employee or through a compromised internal device. External penetration tests replicate attacks launched from outside the network, such as those conducted by cyber attacks scanning the internet for vulnerable systems. These simulations often focus on internet facing assets.
2. Target Systems
Internal pen tests focus on internal infrastructure: employee workstations, internal servers, domain controllers, and network segmentation. The goal is to evaluate how much damage can be done after gaining initial access. In contrast, external pen test engagements target public-facing assets like web servers, cloud environments, email systems, VPN portals, and firewalls to assess perimeter security controls.
3. Access Level
Internal testers typically begin with some level of access, such as a standard user or a connected endpoint, reflecting an attacker who has already breached the perimeter. External testers operate with no prior access, imitating real-world attackers who must first find an entry point, sometimes via ftp servers or overlooked external ips.
4. Threat Focus
Internal tests emphasize lateral movement, privilege escalation, credential theft, and access to sensitive data. They explore how an attacker could expand control inside the network. External tests focus on exposure to the public internet, such as unpatched services, security flaws, open ports, insecure web applications, and weak remote authentication.
5. Risk Coverage
Internal testing reveals critical vulnerabilities that may remain hidden to outsiders but are devastating if the attacker reaches the internal network. External testing is vital for reducing exposure to widespread automated threats and external threats, especially those that take advantage of network penetration testing weaknesses.
6. Value in a Security Program
Both tests are necessary. External efforts help reduce public risk and protect against outside attacks. Internal tests highlight what could happen if attackers gain access to internal layers. When paired, these penetration testing services deliver broader visibility into where manual testing identified vulnerabilities and help validate defenses against both gray box testing and black box testing scenarios.
How Can Bright Defense Help You With Internal and External Pen Tests?
At Bright Defense, we help strengthen your security posture through focused internal and external penetration testing.
Internal Testing: We simulate insider threats such as compromised devices or rogue users to expose misconfigurations, excessive privileges, and overlooked weaknesses within your network.
External Testing: Our team targets your public-facing assets including web applications, VPNs, and cloud infrastructure to surface the same vulnerabilities that real-world attackers pursue.
We combine ethical hacking techniques, manual analysis, and automated testing to reveal the security flaws that matter most. Whether you are preparing for a compliance check, responding to a breach, or conducting routine testing, we deliver clear and actionable results to keep your environment secure inside and out.
Frequently Asked Questions Regarding Internal and External Pen Tests
1. What is penetration testing and how does it differ from a vulnerability assessment?
Penetration testing (or “pen testing”) is an authorized, simulated cyberattack conducted to evaluate system security by actively exploiting vulnerabilities, whereas a vulnerability assessment simply identifies potential weaknesses without exploitation.
2. What is external penetration testing?
External penetration testing simulates attacks from outside the organization’s network (e.g. via internet‑facing services like websites, mail servers, VPNs), with no prior access, to find vulnerabilities in perimeter defenses like misconfigured VPNs, DNS, firewalls, and exposed ports.
3. What is internal penetration testing?
Internal penetration testing simulates an attacker who already has internal network access—such as an insider or compromised user account and attempts lateral movement, privilege escalation, and access to sensitive systems within the internal network.
4. What are the primary objectives of internal vs external penetration testing?
- External testing aims to determine whether an outsider can gain initial access and exploit internet‑exposed services.
- Internal testing evaluates how deeply an attacker with internal access could move, what permissions can be escalated, and how much damage they could cause from inside.
5. Which systems and assets are targeted by internal vs external tests?
- External tests focus on public-facing assets such as web applications, DNS, email servers, VPN endpoints, and firewalls.
- Internal tests target internal servers, Active Directory, endpoints, file shares, intranet applications, printers, IoT devices, and employee workstations.
6. What common vulnerabilities are uncovered by each type of test?
- External testing reveals misconfigurations, open ports, outdated software, weak authentication, web‑app flaws, and DNS issues.
- Internal testing uncovers weak passwords, excessive user privileges, poor segmentation, unpatched systems, lateral movement paths, and weaknesses in access control.
7. When should an organization choose external testing vs internal testing?
- External testing is especially important before launching public services or when regulatory requirements demand it.
- Internal testing is recommended after a breach, when onboarding vendors or new employees, after major infrastructure changes, or to assess insider threat resilience and segmentation schemes.
8. Are both internal and external penetration tests necessary?
Yes. They complement each other: external tests verify perimeter defenses, and internal tests assess post‑breach impact. Together they form a comprehensive view of risk exposure and offer the best strategy for compliance and security resilience.
9. How often should internal and external penetration tests be conducted?
Industry best practices recommend conducting both types at least annually or more frequently (e.g. quarterly) for organizations with dynamic environments, high-value data, or strict compliance needs.
10. What are the challenges and limitations of internal and external penetration testing?
- External testing may miss internal misconfigurations or insider risks that only become evident once you’re inside.
- Internal testing requires safe authorization and coordination to avoid disrupting business operations, clear scope definitions, and potentially complex rules of engagement.
11. How do internal and external penetration tests differ in terms of attack surface?
External tests focus on internet-facing assets such as websites, APIs, VPN endpoints, and firewalls, simulating attacks from outside. Internal tests assume an attacker already has access, assessing endpoints, servers, Active Directory, privilege escalation, and lateral movement. Exact attack surface percentages like 20–30 percent external vs 70–80 percent internal are not supported by public data.
12. What are the most common vulnerabilities detected in internal vs external tests?
External tests often find misconfigured firewalls, open ports, weak encryption, and web flaws such as SQL injection and XSS. Internal tests reveal weak passwords, privilege escalation paths, poor segmentation, and insecure internal services. Internal networks often have more exploitable vulnerabilities—sometimes nearly three times more—but exact percentages like 60 percent external and 75 percent internal are not published.
13. How does testing duration vary between internal and external assessments?
External penetration tests usually last three to seven days, depending on scope. Internal tests often take seven to fourteen days because they cover more systems and movement paths. While internal testing generally requires more effort, no standard benchmark confirms a fixed 40–60 percent increase in hours.
14. What is the cost difference between internal and external penetration testing?
External penetration tests commonly cost $5,000 to $20,000, averaging around $10,000. Internal tests are more expensive, often $7,500 to $30,000, with complex multi‑system or cloud assessments reaching $50,000. Claims that organizations allocate 0.5 to 1 percent of IT security budgets for these services are not industry‑verified.
15. What percentage of breaches could each type of test help prevent?
Penetration testing is linked to stronger security, with one survey showing 72 percent of organizations believed it prevented a breach. External tests reduce risk from internet-facing vulnerabilities, while internal tests help stop lateral movement and privilege abuse. Exact prevention figures like 30 percent, 60 percent, or a combined 45 percent reduction are not supported by research.
16. What is the purpose of a network penetration test?
A network penetration test evaluates the security of an organization’s systems and infrastructure by simulating real-world attacks. Its goal is to find vulnerabilities before malicious actors exploit them, assess how an attacker might gain unauthorized access, and determine the potential impact of those attacks. This testing helps improve security posture and may support compliance requirements such as PCI DSS or HIPAA.
17. Can an internal pen test be performed remotely?
Yes, internal penetration tests can be performed remotely when appropriate access is granted. Testers often use secure VPN or remote access solutions to simulate an internal threat, such as an insider or compromised endpoint, without physically being on-site.
18. How are pen test findings reported?
Penetration test findings are documented in a formal report. The report typically includes:
- An executive summary for non-technical stakeholders
- A detailed scope and methodology section describing what was tested and how
- A list of vulnerabilities with severity ratings, supporting evidence, and potential impact
- A risk analysis showing how exploitation could affect the business
- Recommended remediation steps prioritized by risk
- Supporting technical evidence, such as screenshots and logs, for validation
19. What is the difference between internal pen testing and external pen testing?
Internal penetration testing simulates attacks from within the organization’s network, focusing on insider threats or scenarios where an attacker already has access. It targets internal systems like workstations, file shares, and Active Directory.
External penetration testing simulates attacks from outside the network, focusing on internet-facing systems such as websites, email servers, and VPN endpoints. It identifies vulnerabilities that external attackers could exploit to gain initial access.
20. What information is required to scope a network penetration test?
Scoping a network penetration test requires:
- Clear objectives for the test (e.g., external perimeter, internal threats, specific assets)
- An asset inventory including IP ranges, servers, applications, and cloud resources
- Defined access level (black-box, grey-box, or white-box)
- Rules of engagement covering allowed testing methods and timeframes
- Risk tolerance regarding potential disruptions and exploit depth
- Regulatory or compliance requirements that influence testing depth and reporting format
- Network environment details, such as firewalls, segmentation, and access methods
Get In Touch



