
What Is Penetration Testing? Everything You Need to Know
Cyberattacks are increasing in both scale and severity, placing immense pressure on organizations to strengthen their cybersecurity posture. In 2024 alone, over 16.8 billion records were compromised in 6,670 publicly reported data breaches.
Of those, 63% affected organizations based in the United States. These incidents now come with a steep financial toll. The average cost per breach has risen to $4.88 million, marking a 10% jump from the previous year.
To respond effectively, organizations are turning to penetration testing as a critical safeguard. This blog post breaks down what penetration testing involves, explains its core techniques, and shows how it helps organizations expose and fix vulnerabilities before they can be exploited.
What is Penetration Testing?
Penetration testing is a security practice used to evaluate the defenses of a computer system, network, or application. It involves authorized simulated attacks to find vulnerabilities that malicious actors could exploit. The process mimics real-world threats to test how systems respond under attack. Penetration tests may target web applications, networks, wireless setups, or employee behavior.
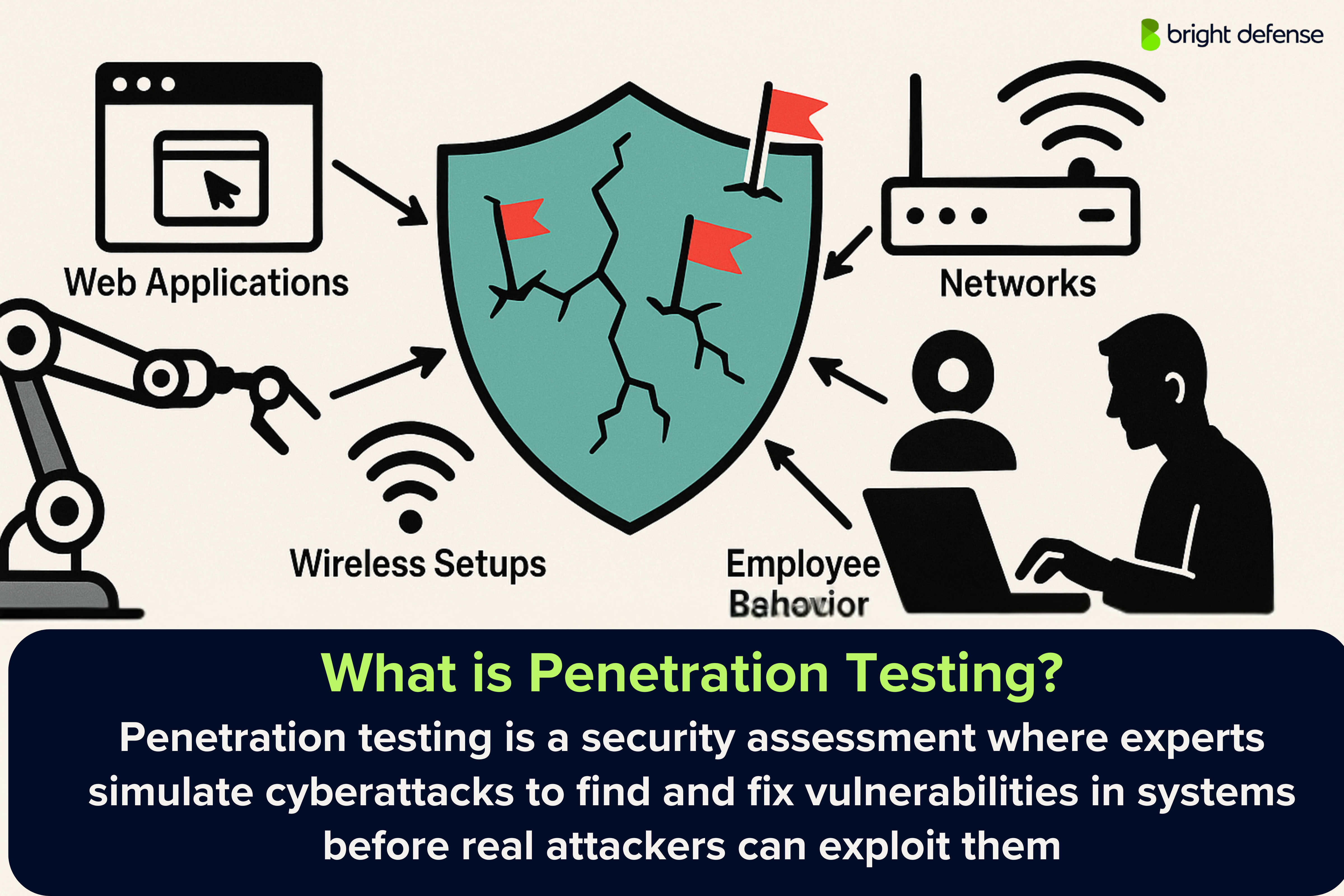
They are usually conducted using a mix of automated tools and manual techniques. The goal is to uncover security gaps, determine their severity, and provide recommendations for fixing them. Pen testing plays a key role in strengthening an organization’s overall cybersecurity posture.
Penetration Testing Methodologies
Penetration testing methodologies define the extent of knowledge provided to the tester about the target systems, influencing testing depth and scope.
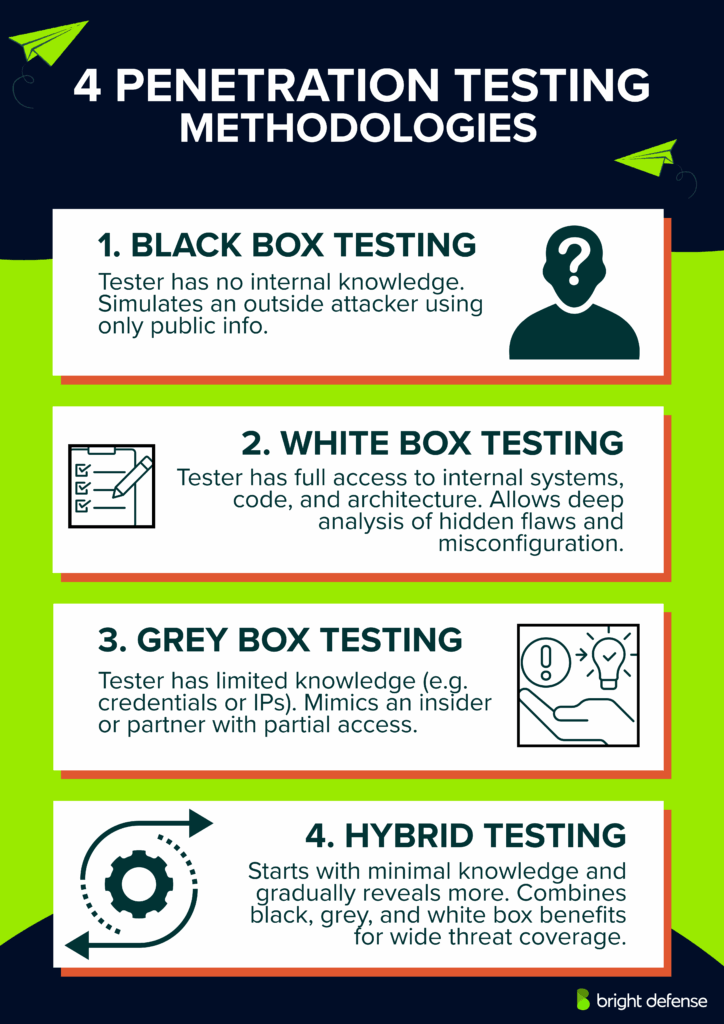
1. Black Box Testing
In black box penetration testing, testers have no prior knowledge about the organization’s internal systems. This method closely replicates an external attacker’s perspective.
Testers rely on open-source intelligence gathering and external scanning to detect vulnerabilities. It assesses an organization’s external security defenses, such as firewalls, websites, and public-facing applications, effectively simulating a real-world cyberattack scenario.
2. White Box Testing
White box penetration testing grants testers complete knowledge about the system, including network architecture, source code, credentials, and infrastructure details. This method thoroughly evaluates internal systems, identifying vulnerabilities that internal threats or informed attackers might exploit.
White box testing enables testers to perform detailed and precise assessments, identifying intricate vulnerabilities and configuration weaknesses that external methods might overlook.
3. Grey Box Testing
Grey box testing provides testers partial knowledge, typically limited to basic information such as credentials, IP addresses, or specific system details.
This method balances black and white box approaches, simulating scenarios where attackers possess limited information, similar to insiders or individuals with partial access.
Grey box testing efficiently identifies vulnerabilities, particularly focusing on user privilege escalation, authentication issues, and specific components requiring targeted attention.
4. Hybrid Testing
Hybrid penetration testing combines elements from black, white, and grey box methodologies. It begins with minimal external knowledge, progressively providing additional internal information to testers. Hybrid methods adapt dynamically, allowing testers to comprehensively assess both external and internal vulnerabilities in a single engagement.
This approach effectively evaluates overall cybersecurity resilience, identifying a wide range of threats and vulnerabilities through diverse testing perspectives, and providing a thorough understanding of an organization’s security posture.
Benefits of Penetration Testing
Penetration testing offers significant value for organizations seeking to strengthen their cybersecurity. Below are key benefits associated with performing regular penetration tests:

1. Improved Security Posture
Regular penetration testing identifies vulnerabilities within systems, networks, and applications. Organizations receive detailed insights about weak points in their security infrastructure. This visibility allows them to prioritize and remediate critical vulnerabilities promptly.
Penetration testing provides practical insights, leading directly to stronger overall security measures. Organizations that integrate penetration tests into their cybersecurity practices significantly reduce their susceptibility to cyber threats and data breaches.
2. Prevention of Security Breaches
Cybersecurity threats continuously evolve, placing organizations at risk of unauthorized access, data loss, and business disruption. Penetration testing proactively uncovers vulnerabilities before attackers exploit them. Simulating real-world attacks, security teams understand how attackers could compromise their systems.
This insight allows organizations to address vulnerabilities in advance, substantially lowering the likelihood of successful cyber-attacks. Regular testing helps organizations remain vigilant, minimizing security incidents and associated disruptions.
3. Meeting Regulatory Requirements
Many industries require organizations to adhere to regulatory standards for data protection and cybersecurity. Regulations such as GDPR, PCI DSS, and HIPAA mandate regular penetration testing as part of compliance. Conducting penetration tests demonstrates to regulatory bodies that an organization actively manages cybersecurity risks.
This helps avoid regulatory penalties and preserves organizational reputation. Furthermore, penetration testing provides documented evidence of compliance, enabling smoother regulatory audits and demonstrating a commitment to cybersecurity best practices.
4. Comprehensive Analysis of IT Infrastructure
Penetration testing thoroughly examines an organization’s IT infrastructure from the perspective of an attacker. This comprehensive approach uncovers hidden vulnerabilities and insecure practices that routine security audits might overlook.
Simulating real-world attack methods, pen testers identify weaknesses in configurations, outdated software, poor access controls, and inadequate security policies.
Organizations can then refine their infrastructure security based on precise, actionable information. Regular testing promotes continuous improvement in infrastructure security, significantly reducing exploitable vulnerabilities.
5. Protection from Financial Damage
Cyber-attacks often cause large financial losses. These can come from business outages, recovery costs, legal bills, fines, and harm to a company’s name. Penetration testing lowers the chance of these losses.
It finds and fixes weak spots before attackers can use them. Catching problems early makes attacks less likely and less harmful. Companies that test their systems often can avoid big risks. This helps protect their money, customer data, and reputation.
How to Perform Penetration Testing – Phases of a Penetration Test
Penetration testing is an essential method for assessing the security of a system by simulating cyber-attacks. Below are the key phases involved in conducting an effective penetration test:
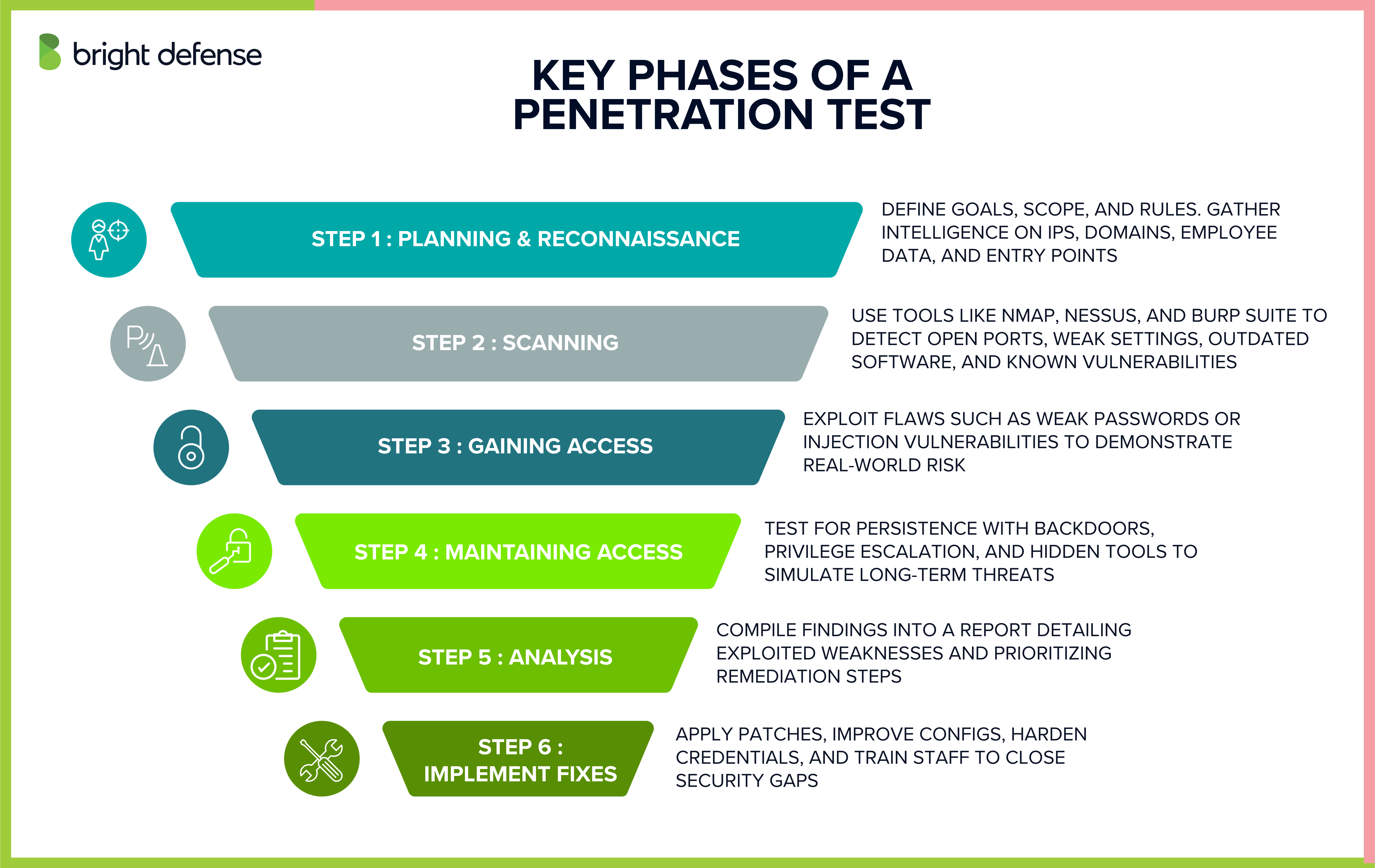
Step 1: Planning and Reconnaissance
The first step is to set clear goals, define what will be tested, and agree on the rules. Security testers collect basic information about the target using public sources.
This may include IP addresses, domain names, employee info, email addresses, and ways to get into the system. Good planning helps the test stay on track, meet the company’s goals, and follow the law.
Step 2: Scanning
In this step, testers check the target systems to find weak spots. They use tools like Nmap for network scans, Nessus for finding known issues, and Burp Suite for testing web apps.
The goal is to find open ports, running services, old software, weak settings, and common flaws that hackers could use. These scans give useful details about the system’s security.
Step 3: Gaining Access
In this key step, testers try to break into the system using the weak spots they found. They may use weak passwords, flaws in software, or attacks like SQL injection and XSS.
If they get in, it shows how serious the risks are. Testers record everything they do to show how the system was exposed and what damage could happen.
Step 4: Maintaining Access
After gaining initial entry, testers aim to maintain persistent access to the target systems. This phase highlights risks associated with prolonged unauthorized access, illustrating how attackers could maintain a foothold within compromised environments.
Techniques include creating backdoors, escalating privileges, and deploying persistent scripts or tools. Understanding persistence mechanisms helps organizations recognize indicators of compromise and implement defenses to prevent ongoing intrusions.
Step 5: Analysis
In this phase, penetration testers compile and analyze their findings into a detailed report. This report outlines vulnerabilities discovered, methods employed, exploited weaknesses, and recommendations for remediation.
The analysis prioritizes risks based on severity, exploitability, and potential impact on the organization. Effective reporting enables management and IT security teams to address vulnerabilities systematically, thereby strengthening overall cybersecurity defenses and reducing the risk of successful cyber-attacks.
Step 6: Implement Penetration Testing Findings
The final step involves implementing recommendations provided in the penetration testing report.
Organizations must prioritize and address vulnerabilities through corrective actions such as patching software vulnerabilities, updating configurations, strengthening passwords, enhancing firewall rules, and conducting regular security awareness training for employees.
Implementing these findings significantly reduces the likelihood of successful cyber-attacks and strengthens the organization’s overall security posture.
Types of Penetration Testing
Penetration testing can be conducted in several ways, depending on the systems being tested and the goals of the assessment. Each type focuses on different aspects of an organization’s technology environment.
Below are the main types of penetration testing used to identify and mitigate security risks.
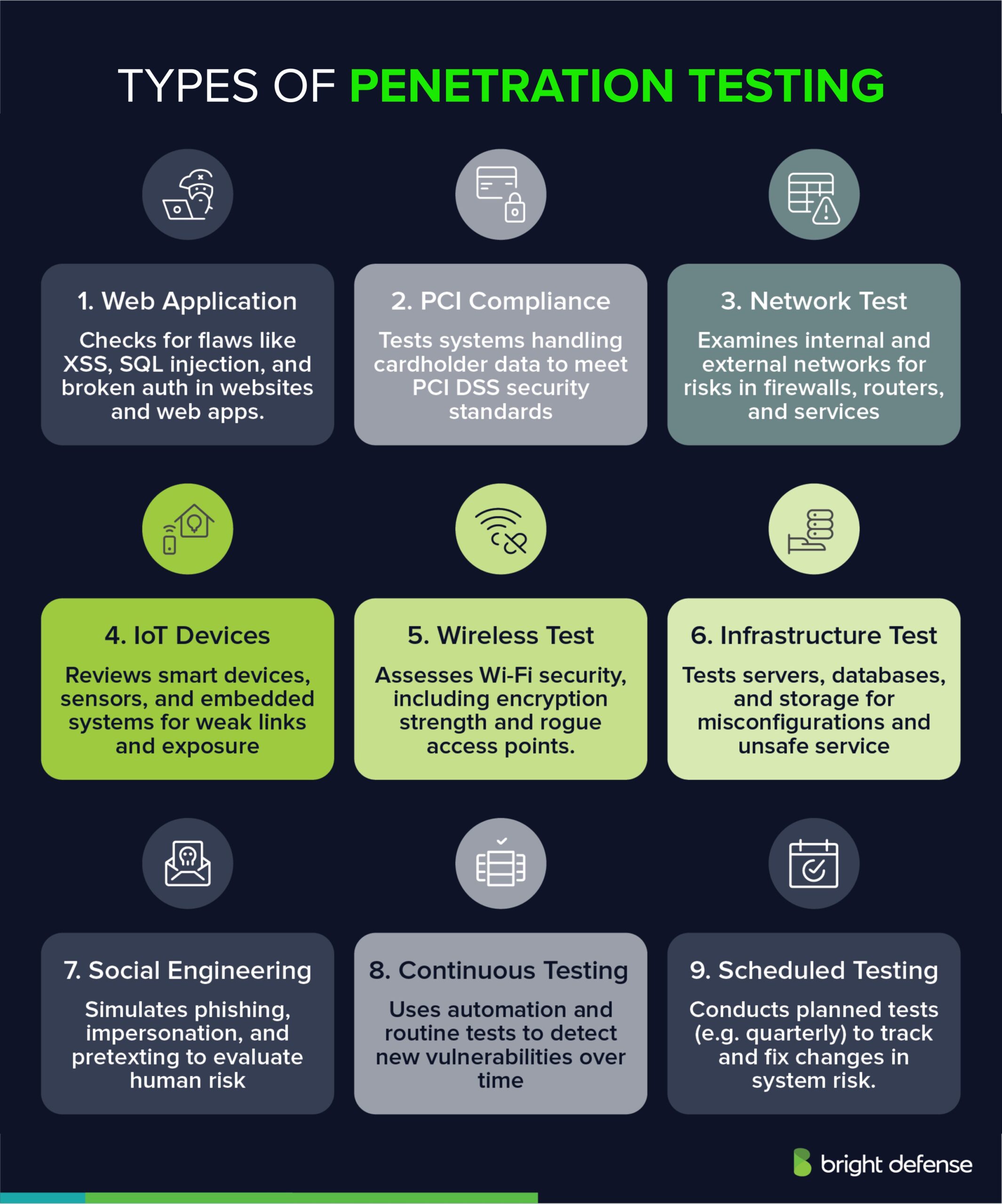
1. Web Application Penetration Test
Web app testing focuses on vulnerabilities within web-based applications. It identifies flaws such as SQL injection, cross-site scripting (XSS), and weak authentication mechanisms. Test cases often simulate attack techniques like stealing credentials or exploiting known vulnerabilities to expose weak spots in application defenses.
The penetration testing team uses tools and techniques similar to those used in real-world attacks. Regular testing of web applications, including vulnerability assessment, protects against threats targeting sensitive data accessed or stored via web interfaces.
2. PCI Penetration Test
PCI (Payment Card Industry) penetration tests assess compliance with PCI DSS standards. Organizations handling credit card transactions must regularly conduct these tests to meet regulatory requirements and reduce risks associated with payment card processing.
Security professionals conduct both internal and external tests to evaluate the security features of systems handling payment data. These assessments check for potential vulnerabilities, security issues, and help the external team gain assurance that adequate security controls and security measures are in place.
3. Network Penetration Test
Network penetration testing examines internal and external networks, discovering vulnerabilities in network infrastructure such as firewalls, routers, and switches. It evaluates the system’s defenses against unauthorized access, denial-of-service (DoS) attacks, and exploitation attempts. T
he testing team focuses on the attack surface and network traffic, attempting to gain remote access using the same tools as real adversaries. An internal test may be conducted from within the organization’s internal network to detect security flaws overlooked during external scanning.
4. IoT Penetration Test
IoT (Internet of Things) penetration tests evaluate vulnerabilities within interconnected devices such as sensors, wearables, and smart home appliances. Security testing involves analyzing mobile devices, wireless networks, and embedded software.
Ethical hacking techniques are used to expose flaws in system components and assess the resilience of the IT system.
The assessment helps penetration testers and security experts identify security weaknesses and conduct a proper security assessment. In some cases, reviewing source code helps uncover hidden issues, especially in scenarios where prior knowledge of the system is limited.
5. Wireless Security Test
Wireless penetration testing assesses the security of Wi-Fi networks and related wireless infrastructure. It identifies vulnerabilities like weak encryption protocols, insecure configurations, unauthorized access points, and susceptibility to eavesdropping attacks. Effective wireless testing protects against unauthorized access and data interception.
6. Infrastructure Penetration Test
Infrastructure penetration tests evaluate the security of critical IT infrastructure components, including servers, databases, storage, and virtualization environments.
This testing identifies misconfigurations, weak passwords, insecure services, and other infrastructure-related vulnerabilities, allowing organizations to secure essential operational assets.
7. Social Engineering Penetration Test
Social engineering tests assess susceptibility to manipulation tactics used by attackers to gain unauthorized access. Techniques tested include phishing emails, pretexting, and impersonation.
Organizations use these tests to measure employee awareness and strengthen defenses against human-centered attacks.
8. Continuous Penetration Testing
Continuous penetration testing integrates regular, automated assessments into cybersecurity practices. It provides ongoing vulnerability detection through automated scanning and periodic manual testing, allowing quicker identification and correction of emerging weaknesses.
9. Regular Penetration Testing
Regular penetration testing involves periodic assessments scheduled at defined intervals, such as quarterly or annually. This approach maintains an updated view of an organization’s cybersecurity posture and addresses new vulnerabilities resulting from system updates or infrastructure changes.
We have a separate blog that covers the different types of penetration testing. Take a look to learn more about each type in greater detail.
How Much Does Penetration Testing Cost?
Penetration testing usually ranges from $5,000 to $50,000, depending on the size of the environment, testing depth, and compliance needs. Factors like how many web apps, IPs, or cloud assets are in scope play a major role in shaping the final price.
At Bright Defense, we offer three flexible plans to match different needs and budgets. Whether you’re looking for focused testing on a single app or a full-scale assessment across multiple environments, our Ignite, Elevate, and Summit plans provide clear options, starting at just $2,750.
For more guidance, check out our full Pentest Pricing Guide to help you choose the right approach for your organization.
How Bright Defense Can Help?
Penetration testing plays a key role in uncovering and addressing security gaps before they turn into real incidents. Bright Defense delivers targeted penetration testing services backed by expert analysis and real-world tactics.
Our team evaluates networks, applications, and cloud environments to identify critical vulnerabilities and guide effective remediation. With a clear focus on actionable results, Bright Defense helps organizations reduce risk and build stronger security foundations.
Ready to strengthen your defenses?
Contact Bright Defense to schedule your penetration test or speak with a security expert today.
FAQs
Penetration testing attempts to breach in-scope systems in controlled conditions to confirm what an attacker could realistically do, not just what weaknesses exist
No. Vulnerability scanning focuses on finding and ranking weaknesses, while penetration testing focuses on exploiting weaknesses to circumvent or defeat security features
Yes. A penetration test is designed to show how vulnerabilities can be exploited and what impact that exploitation can have
A black-box test starts with little or no internal system information, a white-box test starts with full details, and a grey-box test starts with partial details
A penetration test typically ends with a written report that explains verified issues, exploitation paths, and the related risk to the organization
It depends. Tests use a defined scope and rules of engagement that set constraints, schedules, and contacts to reduce operational risk during testing
PCI guidance calls for penetration testing at least annually and after significant changes, and many organizations adopt a similar cadence for high-risk systems even outside PCI scope
Yes. A rules-of-engagement document typically defines target systems, scope, constraints, and notifications before any testing begins
– Planning and reconnaissance
– Scanning
– Gaining access
– Maintaining access
– Analysis (reporting results)
– Network security
– Information security
– Endpoint security
– Cloud security
– Application security
– Operational security (OpSec)
– Disaster recovery and business continuity planning
VA (vulnerability assessment) is a systematic examination to evaluate security measures and find security deficiencies, while PT (penetration testing) attempts exploitation to confirm whether those weaknesses can lead to compromise.
Get In Touch



