
What is Mobile Application Penetration Testing?
Mobile applications are frequent targets for attackers who seek out security flaws to exploit sensitive user data, compromise device integrity, or gain unauthorized access. Mobile application penetration testing focuses on finding these weaknesses before real attackers do.
This blog introduces mobile application penetration testing. You’ll get a clear understanding of how this testing works, what it covers, and why it plays a critical role in protecting user data and business systems.
Key Takeaways
- Mobile application penetration testing simulates real-world attacks on iOS and Android apps to find flaws in data handling, authentication, and device-level security
- Testing covers both static code analysis and dynamic runtime behavior, revealing issues like insecure storage, weak encryption, and flawed session handling
- Assessments verify whether apps align with standards such as OWASP MASVS, HIPAA, and PCI DSS
- Common vulnerabilities include hardcoded credentials, improper platform API use, code tampering, and data exposure through third-party SDKs
- Skilled testers evaluate the app in real scenarios, delivering reports with technical findings and clear fixes to strengthen mobile app security
What is Mobile Application Penetration Testing?
Mobile Application Penetration Testing is a security assessment process that simulates real-world attacks on mobile apps to find vulnerabilities before they can be exploited.
It focuses on identifying flaws in areas such as insecure data storage, weak authentication, poor encryption practices, improper session handling, and vulnerable API connections.
This type of testing covers both the mobile app’s local environment (on the device) and its communication with backend servers. It typically includes static analysis of the app’s code and dynamic testing of the app while it runs, helping security teams understand how well the app can resist common and advanced attack techniques.
The goal is to reduce risk, protect sensitive user data, and help teams fix security issues early in the development cycle.
Why is Mobile Application Penetration Testing Important?
Mobile app pentesting is crucial for the following reasons:

1. Expose Vulnerabilities Before Exploitation
Mobile app penetration testing aims to simulate real-world attacks on iOS and Android applications. This helps uncover flaws in authentication, data storage, communication, and device integration mechanisms before malicious actors can take advantage of them.
2. Assess Data Protection Mechanisms
It evaluates how well sensitive data is stored and transmitted. This includes checking for improper encryption, insecure APIs, and data leakage through logs, caches, or third-party libraries.
3. Verify Secure Implementation of Business Logic
Penetration testing confirms whether custom logic such as payment flows, user permissions, and session handling is implemented securely. It looks for bypasses or misuse scenarios that could compromise the app or its users.
4. Evaluate App Behavior on Compromised Devices
A key objective is to examine how the app behaves on rooted or jailbroken devices. Testing in such environments helps determine if attackers can gain escalated access or tamper with runtime logic.
5. Measure Compliance with Security Standards
Testing often validates whether the app aligns with OWASP MASVS (Mobile Application Security Verification Standard), PCI DSS, HIPAA, or other regulatory or industry-specific benchmarks.
How Much Does Mobile Application Penetration Testing Cost?
The cost of mobile application penetration testing typically falls between $5,000 and $30,000 or more. Several variables influence the final price:
| Testing Scope | Typical Range |
| Basic (1 platform) | $5,000 – $10,000 |
| Moderate (2 platforms, some manual work) | $10,000 – $20,000 |
| Advanced (full manual test, 2 platforms, deep logic) | $20,000 – $30,000+ |
The following factors can impact the cost of mobile application penetration testing:
- Simple apps with minimal features or single-platform deployment often cost less due to reduced testing scope.
- Complex applications with intricate user roles, backend integrations, or dynamic content typically require more effort and cost more.
- Testing only one platform (iOS or Android) is generally cheaper than testing both.
- Testing both iOS and Android increases the cost because of separate testing workflows and platform-specific issues.
- Basic vulnerability assessments or automated scans fall on the lower end of the pricing scale.
- Full manual penetration testing involving reverse engineering, authentication bypass, and local storage analysis increases the cost.
How to Prepare for a Mobile Application Penetration Test?
Proper preparation for mobile app penetration testing helps reduce delays and improve test results.
The steps below outline what to do before testing begins:
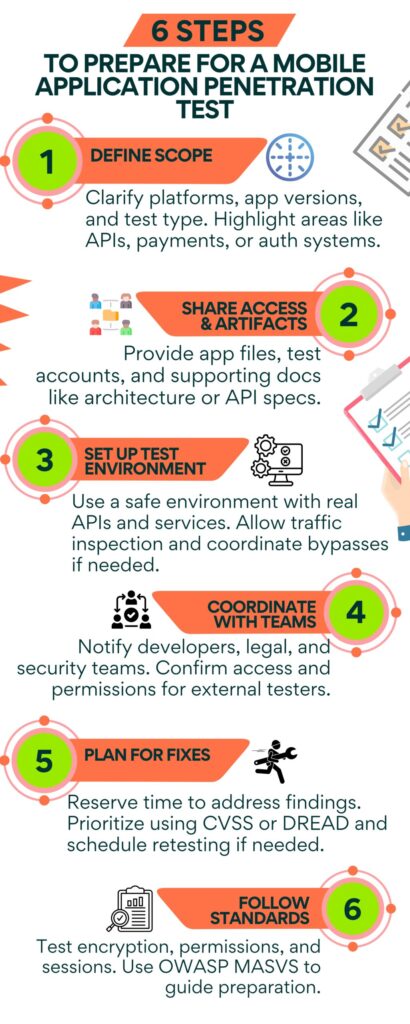
1. Define the Testing Scope Clearly
Start by outlining the platforms and environments involved. Specify whether the testing will cover Android, iOS, or both, and identify the version of the app to be tested.
It is also important to state the type of testing, whether it is black box, gray box, or white box, so expectations are clear. Make a note of key components such as APIs, third party SDKs, authentication systems, or payment modules that need special focus during testing.
2. Gather Required Artifacts and Access
Provide the latest APK or IPA files so testers can install and evaluate the mobile app directly. If the test involves gray box or white box analysis, share parts of the source code or debugging symbols to help with deeper analysis.
Create and deliver test user accounts that cover all necessary roles, including admin, standard users, and restricted accounts. Include documentation like architecture diagrams, threat models, and API references to give testers insight into how the app is structured and where the risk areas lie.
3. Set Up the Testing Environment
Use a staging environment that closely mirrors production to minimize risks. This should include all backend components, API endpoints, and third party integrations.
If the app includes protections like root detection, certificate pinning, or region based access controls, coordinate in advance so testers can bypass these restrictions safely. Make sure network settings allow for traffic interception tools, and whitelist tester IPs if firewall rules or WAFs are in place.
4. Align with Internal Stakeholders
Notify the development team in advance so they are available to answer questions or assist with setup issues during the test.
If third party testers are involved, check with legal and compliance teams to clear any formalities, such as NDAs or authorization letters. Let internal security teams or SOC staff know when the testing is scheduled, so legitimate test activity is not flagged as a real attack.
5. Prepare for Post Test Remediation
Block out time in the development cycle for addressing security issues that come out of the test. Decide whether a follow up test will be required to validate the fixes.
Use a risk based model such as CVSS or DREAD to help prioritize vulnerabilities and apply patches based on their severity and likelihood of exploitation.
6. Additional Tips
Include non functional aspects of the app in your test plan, such as permission handling, session expiration, or encryption. Follow OWASP MASVS to keep preparation aligned with well established mobile security benchmarks.
This helps both internal and external teams follow the same expectations for what secure design and implementation should look like.
10 Common Vulnerabilities in Mobile Applications
Mobile apps often face security issues that expose user data, weaken authentication, or allow attackers to exploit business logic.
Here are some of the most common vulnerabilities found in mobile applications:
1. Insecure Data Storage
Sensitive data stored on the device, such as credentials, tokens, or personal information, may be saved in plain text or in unprotected locations like shared preferences or external storage. This data becomes accessible if the device is compromised.
2. Insecure Communication
Apps that do not use proper encryption for data in transit can leak sensitive information through unsecured HTTP, weak SSL configurations, or missing certificate validation. Attackers can intercept traffic using man in the middle techniques.
3. Inadequate Authentication and Authorization
Improper session handling, weak password policies, and missing reauthentication for sensitive actions can allow attackers to gain or escalate access. Hardcoded credentials or tokens in the app binary are another common issue.
4. Reverse Engineering Exposure
Attackers can decompile mobile apps to access source code, uncover hardcoded keys, or understand app logic. Lack of obfuscation makes it easier to extract sensitive information or find entry points for tampering.
5. Code Tampering
If an app does not verify its integrity, attackers can modify the app binary to alter behavior or inject malicious code. Modified versions may bypass security checks or capture user data.
6. Insecure Use of Platform APIs
Incorrect implementation of biometric features, intent handling, or clipboard access can open paths to privilege abuse or data leaks. Apps may unintentionally expose components to other apps or allow unintended interactions.
7. Weak Cryptographic Practices
Using outdated or broken encryption algorithms, weak key lengths, or storing encryption keys inside the app code can compromise data confidentiality. Sometimes developers use custom encryption schemes that are easy to break.
8. Insufficient Jailbreak or Root Detection
Apps may fail to detect if they are running on rooted or jailbroken devices. This gives attackers more control and access to internal app files and APIs that are usually restricted.
9. Poor Session Management
Sessions that do not expire properly, lack idle timeout, or rely solely on stored tokens without server side checks can be reused by attackers even after logout or app restart.
10. Exposure Through Third-Party Libraries
Vulnerable or outdated third party SDKs used for ads, analytics, or social login can introduce security flaws. Apps inherit the weaknesses of any embedded libraries they rely on.
OWASP Methodologies in Mobile App Penetration Testing
OWASP provides structured resources that guide security assessments for mobile applications. Two key resources are the OWASP Mobile Top 10 and the Mobile Application Security Verification Standard (MASVS). These are widely used in mobile app penetration testing to define risk areas and testing depth.
The OWASP Mobile Top 10 lists the most common mobile security risks. This includes issues such as improper platform usage, insecure data storage, insecure communication, and insufficient cryptography.
Testers use this list to guide initial assessments and prioritize attack vectors based on known mobile-specific weaknesses.
The MASVS serves as a security baseline for development and testing. It offers different levels of verification, from basic security hygiene to defense against advanced threats.
MASVS covers areas like local data storage, authentication, cryptography, code quality, and interaction with the mobile OS. It also pairs with the Mobile Security Testing Guide (MSTG), which explains how to test each MASVS requirement in practice.
Together, these OWASP resources help standardize mobile app testing efforts, improve coverage, and support consistent reporting.
Most professional testing teams use these methodologies as their primary reference throughout an assessment.
How Can Bright Defense Help You With Mobile Application Pen Tests?
Bright Defense helps secure your mobile apps by finding and fixing security gaps across iOS and Android. Our testing covers local storage, APIs, authentication, and real-world attack paths.
Why Choose Bright Defense for Mobile App Pen Testing?
- Flexible Plans: Choose from Ignite (core features), Elevate (API-heavy apps), or Summit (complex mobile ecosystems).
- Realistic Testing: We simulate real-world mobile threats using proven tools and methods.
- Compliance Support: Our tests align with OWASP MASVS, SOC 2, HIPAA, and more.
- Actionable Reports: Clear findings and remediation steps for developers and risk teams.
FAQs
It helps protect user data, prevent unauthorized access, and avoid financial or reputational harm caused by security breaches.
Typical issues include insecure data storage, weak encryption, poor session handling, hardcoded credentials, and flawed authentication.
Android apps run on a wide range of devices with varying hardware and OS versions, while iOS testing usually deals with fewer devices but stricter platform rules.
Tools like Burp Suite, OWASP ZAP, MobSF, and Frida help test mobile apps for security flaws and runtime behavior.
Functional testing checks if the app works as intended, while security testing focuses on finding and fixing risks that attackers could exploit.
Mobile application pentesting is a security test that checks mobile apps for flaws that attackers could use to steal data, gain control, or cause damage.
Application penetration testing simulates real-world attacks on software to find security weaknesses before attackers can use them.
The five steps are planning, scanning, gaining access, maintaining access, and cleaning up with a report.
Get In Touch



