What is Social Engineering Penetration Testing?
Social Engineering Penetration Testing is a social engineering assessment that evaluates how vulnerable an organization’s personnel are to manipulation.
Instead of targeting a computer system or software, this form of security testing focuses on people, examining how easily attackers could exploit human behaviour to gain access to confidential information or secure areas.
According to the 2024 Verizon Data Breach Investigations Report, 74% of breaches involved the human element, including social engineering attacks. Furthermore, phishing remains one of the top attack vectors, accounting for 36% of breaches.
Through such testing, organizations can assess their security posture and uncover potential weaknesses that may otherwise lead to data breaches or compromise of sensitive data. A study by Proofpoint found that over 83% of organizations experienced at least one successful phishing attack in the past year, highlighting the need for regular human-centric security assessments.
Let’s find out more about social engineering penetration testing.
Key Takeaways
- Social engineering penetration testing simulates real attacks that exploit human behavior instead of technical systems
- Common tactics include phishing, vishing, baiting, and impersonation to test how employees respond under pressure
- These tests reveal whether awareness training is effective and highlight security gaps not visible through technical audits
- Findings help reduce risks related to human error, support compliance with standards like ISO 27001 and HIPAA, and improve incident response
- A qualified security team delivers targeted simulations, clear reports, and actionable steps to strengthen employee defenses and reduce overall exposure
Why Should You Perform a Social Engineering Test?
Below are some of the reasons organizations conduct these tests. They highlight how Social Engineering Tests help reveal hidden risks tied to human behavior and show where improvements are needed beyond:

1. Measure Human Risk
Technical defenses may block many attacks, but human behavior often presents a much larger risk. Employees can be tricked into disclosing passwords, opening malicious attachments, or providing sensitive information. A Social Engineering Test evaluates the likelihood of human error under real conditions.
2. Evaluate Security Awareness Training
Training programs are meant to teach employees how to recognize and respond to threats. However, the only way to confirm their effectiveness is through actual testing. Social Engineering Tests reveal whether employees understand and apply what they have learned when faced with a deceptive situation.
3. Identify Gaps Beyond Technical Controls
Firewalls, antivirus software, and encryption can protect against certain attacks. Yet, none of these tools can prevent an employee from unknowingly giving away access. Social Engineering Tests uncover vulnerabilities that technical audits miss, focusing on the human element instead.
4. Test Incident Response
A key aspect of security is how quickly and effectively an organization can respond to an attack. Social Engineering Tests help evaluate whether employees report suspicious activities and how well security teams handle these reports. These exercises show if the incident response plan is practical in real-world conditions.
5. Protect Reputation and Finances
Successful social engineering attacks can lead to financial loss, theft of intellectual property, or damage to the organization’s reputation. Testing helps prevent these consequences by strengthening defenses where they are weakest, the people.
6. Meet Compliance and Regulatory Requirements
Many standards such as ISO 27001, PCI DSS, and HIPAA emphasize the importance of user awareness and risk assessment. Performing Social Engineering Tests can support compliance efforts, showing auditors that the organization actively tests its security measures beyond technical controls.
7. Reduce Overall Attack Surface
Attackers look for the easiest entry point. If employees are less susceptible to manipulation, it forces attackers to take more complex and risky paths. Reducing this human risk decreases the overall probability of a successful breach.
8. Build a Security-First Culture
Routine testing promotes a mindset where employees treat security as a shared responsibility. It encourages vigilance and fosters better communication about potential threats within the organization, without needing formal training sessions every time.
Types of Social Engineering Penetration Tests
Organizations perform different types of social engineering penetration testing to measure the resilience of their personnel against attacks. These tests vary depending on the setting and the tactics used.
1. On-Site Testing
In on-site tests, a pen tester physically visits the organization’s premises. The goal is to evaluate physical security controls and assess how easily someone could gain access to secure areas without proper authorization.
Common techniques include usb drops, where devices loaded with simulated malware are left in open areas, and attempts to bypass security guards by impersonating trusted personnel. On-site assessments help identify vulnerabilities that stem from the human element within physical environments.
2. Off-Site Testing
Off site tests focus on remote social engineering tactics such as phishing, vishing phone calls, and pretexting. These are conducted without physical presence and test how employees react to social engineering attempts via email, phone, or digital communication.

Social engineering pen testing in an off-site setting often includes the use of passive reconnaissance and open source intelligence to gather information about the target. This approach evaluates how well the organization’s personnel can defend against threat actors operating remotely.
What Are Social Engineering Attacks?
Social Engineering Attacks are methods used to manipulate individuals into revealing confidential information, providing access, or performing actions that compromise security.
These attacks rely more on psychological manipulation than technical hacking techniques.
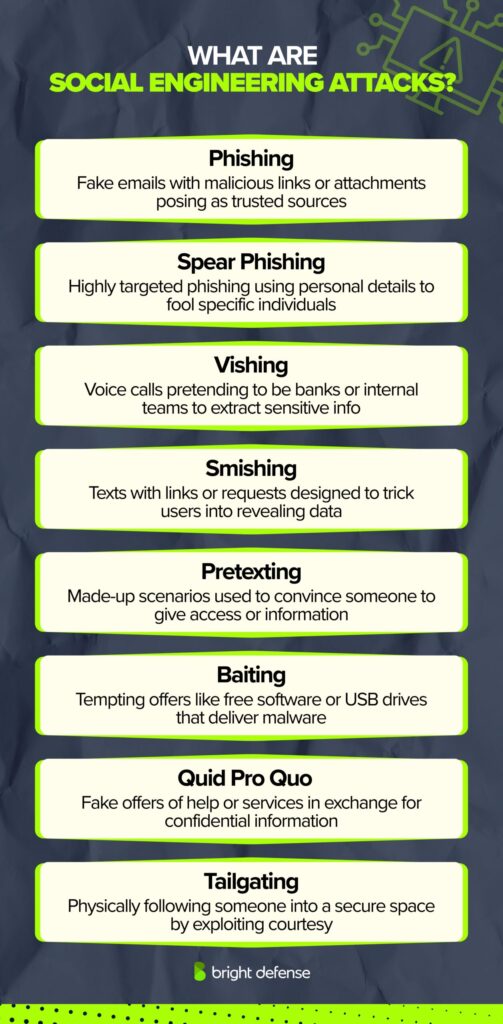
1. Phishing
Phishing involves sending fraudulent communications, usually emails, that appear to come from reputable sources. These messages often contain links to malicious websites or attachments designed to steal credentials or install malware.
2. Spear Phishing
Unlike general phishing attacks, spear phishing targets specific individuals or organizations. Attackers gather personal details about the target to make the message more convincing and harder to detect.
3. Vishing (Voice Phishing)
In vishing attacks, attackers use phone calls instead of emails. They impersonate trusted entities, like banks or internal departments, to extract sensitive information.
4. Smishing (SMS Phishing)
Smishing delivers deceptive messages through text messaging. Victims are urged to click links or reply with personal information.
5. Pretexting
Pretexting involves creating a fabricated story or scenario to convince the victim to provide access or information. For example, an attacker might pretend to be from technical support asking for login credentials to resolve a fake issue.
6. Baiting
Attackers lure victims by offering something enticing, such as free software or physical media (like a USB drive) left in a public place. Once interacted with, the bait deploys malware or leads to a scam.
7. Quid Pro Quo
In a quid pro quo attack, the attacker promises a service or benefit in exchange for information. A common example involves posing as IT support offering help in return for login credentials.
8. Tailgating
Tailgating, or “piggybacking,” involves an attacker physically following an authorized person into a restricted area. The attacker may rely on politeness or social norms, such as holding a door open for someone carrying packages.
Social Engineering Penetration Test Process
Below are some of the key steps involved in conducting a Social Engineering Penetration Test. Each step focuses on simulating real-world conditions to examine how individuals respond to deception and where defenses may fall short.
1. Planning and Scoping
The process starts with defining the purpose, scope, and rules of engagement. Leadership must approve the test, and clear boundaries are set to avoid legal or ethical concerns.
The team decides which departments or employees to target and what types of attacks will be simulated, such as phishing emails or physical intrusions. Careful planning prevents misunderstandings and protects business operations from disruptions.
To achieve accurate results, testers often use social engineering testing strategies and later produce a detailed report highlighting the findings. Regular practice of regular security assessments supports continuous improvement in organizational defenses.
2. Information Gathering (Reconnaissance)
Once the scope is set, information about the target organization and its personnel is collected. Testers research company websites, social media profiles, press releases, and other public sources.
They gather employee names, roles, contact information, and details about internal operations. Thorough reconnaissance helps create believable attack scenarios, increasing the likelihood of successful simulations.
3. Attack Vector Selection
With enough information, the team selects the method for the attack. Common choices include phishing emails designed to trick employees, vishing phone calls that imitate trusted figures, and pretexting scenarios where testers fabricate convincing identities.
Some tests may involve physical attempts to access restricted areas. The attack vector must fit the organization’s risk profile and simulate a realistic threat.
4. Payload Development
For attacks that require technical elements, such as phishing or baiting, testers create payloads like fake login pages or malicious email attachments.
These are crafted to appear legitimate and convincing while remaining controlled and safe to prevent actual harm to systems or data.
5. Execution
The planned attacks are carried out against selected employees or departments. During this phase, testers carefully monitor their actions, documenting every step.
All interactions are controlled to avoid causing harm or panic, and testers maintain detailed records of how targets respond. The execution phase reveals how vulnerable the organization is to manipulation.
6. Monitoring and Data Collection
While the attack unfolds, testers collect data on employee behavior and response times. They track who falls for the attacks, who reports suspicious activity, and how quickly security teams respond.
These observations form the basis for the final analysis, showing where human weaknesses exist and how the organization reacts to social engineering threats.
7. Reporting
After the test concludes, a report is compiled. It covers the methods used, outcomes, and key findings, such as the number of successful and unsuccessful attempts.
The report also includes recommendations for reducing vulnerabilities. Clear reporting focuses on improvement without assigning personal blame.
8. Debrief and Awareness Training
The final step involves sharing the results with the organization. A debrief session explains what was learned and discusses common mistakes.
Focused training sessions follow to address the specific gaps uncovered. These discussions reinforce good security practices and encourage employees to stay alert against future attempts.
How Bright Defense Can Help You With Social Engineering Penetration Testing
At Bright Defense, we approach social engineering threats with the precision they demand. Our team replicates real-world manipulation techniques to expose weak points in human defenses—from phishing emails to phone-based attacks. We do more than point out vulnerabilities; we provide clear, practical actions to reduce risks.
Our social engineering penetration testing examines more than just employee responses. We assess phishing resistance, physical security breaches, pretexting vulnerabilities, and susceptibility to information leaks. We also test how well employees recognize and respond to suspicious behavior, both digitally and in person.
Whether you have a small team or a large workforce spread across offices, we give you a detailed view of where your people are prepared and where more support is needed.
Bright Defense helps you strengthen the human element of your security. No guessing. Just tested defenses, clear gaps, and steps to build resilience.
FAQs
Social engineering penetration testing is a controlled test that tries to trick staff into revealing information or taking actions that could help an attacker, such as sharing credentials or approving a payment.
Common tactics include email phishing, SMS phishing (smishing), and phone-based phishing (vishing), and the test can also cover other pretexting scenarios depending on scope.
A technical penetration test focuses on systems and vulnerabilities, while a social engineering test focuses on human interaction and process gaps that can lead to access or fraud.
Written authorization and a signed rules of engagement document are required, and they should define scope, allowed techniques, contacts, escalation paths, and stop conditions.
Common deliverables include a final report plus metrics such as click rates and reporting behavior, and CISA’s Phishing Campaign Assessment materials describe weekly click-rate summaries and a final report review.
Yes. CISA guidance recommends prompt reporting of phishing activity and treating reporting as a protective control, so running the simulation through the same reporting path gives a realistic view of response performance.
The response should include password changes for affected accounts, session review, and incident-handling steps aligned with your incident response process, since NIST incident handling guidance emphasizes structured response activities and NIST phishing guidance highlights immediate password changes for affected accounts.
A practical approach is running it on a recurring schedule and after major changes such as new payment workflows, new helpdesk processes, or major onboarding waves, and CISA’s phishing campaign assessment model is structured as a time-boxed program that produces periodic metrics and a final report.
Network security, information security, endpoint security, cloud security, application security, operational security (OpSec), and disaster recovery and business continuity planning
– Phishing
– Smishing (SMS phishing)
– Vishing (voice phishing)
– Pretexting
– Baiting
– Tailgating or piggybacking (physical access trick)
– Quid pro quo (offering help or a benefit in exchange for credentials or sensitive data)
The two common types are external penetration testing (tests internet-facing perimeter security) and internal penetration testing (tests what an attacker can do after gaining internal access).
Social engineering is the broader category of attacks that manipulate people to take actions an attacker wants, while phishing is a specific form of social engineering that uses deceptive messages or sites to trick targets into giving up sensitive information or taking unsafe actions.
Get In Touch



