What is Physical Penetration Testing?
Physical penetration testing exposes weaknesses that digital security measures often miss. This article explains what physical penetration testers examine, why these tests are essential, and how to apply the findings effectively. Updates will follow as new tactics and standards develop.
Strong firewalls and cybersecurity tools do not protect against a weak door lock or an unsecured badge system. Many organizations overlook physical threats, which can lead to revenue loss, customer distrust, and major operational disruptions after a breach.
IT defenses alone do not guarantee full security. Physical security gaps allow attackers to bypass digital protections and gain direct access to sensitive areas.
Regular physical penetration testing, handled by trained security personnel, reveals flaws digital audits overlook. It adds a critical layer of protection to your overall security plan.
This guide will help you find and fix these vulnerabilities without guesswork or outdated advice.
Key Takeaways
- Physical penetration testing reveals gaps in locks, badge systems, staff behavior, and access controls that digital tools can’t detect
- Common tactics include tailgating, lock picking, badge cloning, and impersonation to simulate real-world intrusions
- These tests validate physical controls, test employee awareness, and help reduce risks tied to unauthorized facility access
- Regular assessments support compliance with standards like PCI DSS and ISO 27001 and help prevent theft, sabotage, or data breaches
- A professional testing team delivers clear findings, documented breaches, and practical steps to strengthen physical security across sites
What is Physical Penetration Testing?
Physical penetration testing refers to the practice of simulating real world scenarios against physical security weaknesses at a facility, organization, or restricted location. The goal is to determine how vulnerable physical security controls are to unauthorized access, theft, or sabotage.
Rather than focusing on digital systems, this type of assessment targets the physical barriers and protocols intended to protect sensitive information, personnel, and assets. Physical pen testers attempt to bypass security practices and systems like locked doors, access control systems, surveillance cameras, and even security guards.
Attackers may also use social engineering techniques to manipulate staff or carry out social engineering attacks. These tests help reveal hidden security vulnerabilities that standard audits might miss.
Why is Physical Penetration Testing Important?
Physical penetration testing evaluates how well an organization’s physical security controls withstand real-world attacks. Below are the main reasons physical penetration testing is important and the risks it helps address:

1. Protection of Sensitive Assets
Organizations house valuable assets, including intellectual property, financial records, and sensitive data. A breach through physical means can result in stolen documents, tampered hardware, or compromised servers. Testing assesses how well facilities defend against such risks and helps prevent data theft or sabotage through unauthorised access to critical areas.
2. Validation of Security Controls
Security investments like card readers, biometrics, alarms, and surveillance systems are only useful if properly implemented and maintained. Physical penetration testing verifies that these systems function as intended under real-world attack scenarios, not just during compliance checks.
3. Employee Awareness Testing
Employees are often the last line of defense. Testing measures their vigilance in recognizing and reacting to security threats. It evaluates:
- Whether staff challenge unknown individuals
- How well procedures are followed
- The likelihood of insider threats exploiting familiarity or negligence
Findings often show that even the best policies fail without consistent employee participation. Gaps around access points and unmonitored wireless networks increase exposure.
4. Risk Reduction
Physical breaches can lead to financial losses, legal penalties, and reputational damage. Testing uncovers vulnerabilities early, allowing organizations to address risks before actual attackers exploit them. Preventative action saves costs associated with recovery and regulatory fines.
5. Support for Compliance Requirements
Many regulations and security standards (e.g., PCI DSS, ISO 27001) require organizations to protect physical access to critical systems. Physical penetration testing provides documented evidence of due diligence in protecting these assets, supporting audit and certification efforts. Teams in the IT department often work closely with physical security experts to coordinate testing activities as part of overall pen testing strategies.
How Much Does Physical Penetration Testing Cost?
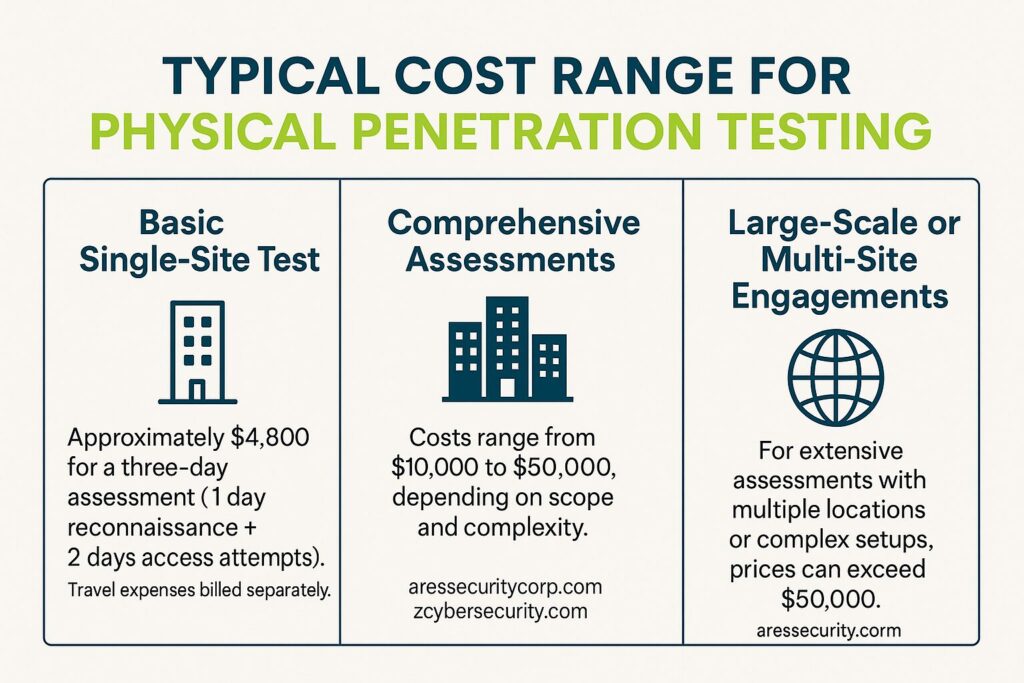
Physical penetration testing typically costs between $4,800 and $50,000, depending on the number of sites, testing duration, and complexity of security measures. Costs increase with more locations, extended testing hours, and advanced security setups. Travel and reporting expenses are usually billed separately.
Here’s a detailed breakdown of a typical physical penetration testing cost range:
Typical Cost Range
- Basic Single-Site Test: Approximately $4,800 for a three-day assessment, which includes one day for reconnaissance and two days for attempting physical access. This estimate excludes travel expenses, which are billed separately. (triaxiomsecurity.com)
- Comprehensive Assessments: Costs can range from $10,000 to $50,000, depending on the scope and complexity of the test. (aressecuritycorp.com)
- Large-Scale or Multi-Site Engagements: For extensive assessments involving multiple locations or complex environments, prices can exceed $50,000. (aressecuritycorp.com)
Factors Influencing Cost
- Number of Sites: Each additional location requires separate reconnaissance and testing efforts, increasing the overall cost.
- Testing Duration: Longer assessments, especially those conducted during specific time windows or requiring extended observation, can raise costs.
- Travel Expenses: Costs associated with travel, lodging, and per diem for the testing team are typically billed separately and can vary based on the location of the sites.
- Complexity of Security Measures: Facilities with advanced security systems, multiple access controls, and surveillance require more intricate testing methodologies, impacting the price.
- Customization and Reporting: Tailored testing approaches and detailed reporting requirements can add to the overall expense.
It’s advisable to consult with specialized security firms to obtain a detailed quote tailored to your organization’s specific needs and to understand the full scope of services included in the testing.
How Can a Criminal Cause Harm Once Inside a Building
Gaining physical access to a building gives a criminal several ways to cause serious damage in a short amount of time. What may seem like a minor breach can quickly escalate into major security incidents, financial, and operational problems. Here are the most common risks:
- Theft of Sensitive Information: Stealing documents, laptops, or storage devices containing confidential data from restricted areas.
- Installation of Malicious Devices: Planting keyloggers, network sniffers, or rogue access points to compromise systems during the reconnaissance phase.
- Sabotage of Infrastructure: Damaging servers, cutting network cables, or interfering with operational equipment, often through tampering with locking mechanisms.
- Social Engineering: Impersonating staff or contractors to gather intelligence or prepare future attacks, using tactics aimed at gaining entry without raising suspicion.
- Physical Violence or Threats: Endangering employee safety through intimidation, sabotage, or hostage situations.
How to Perform a Physical Penetration Test
Below is a step-by-step guide to assessing and exposing weaknesses in a facility’s physical security through authorized simulation techniques.
Step 1: Pre-Engagement Planning
Define what areas and methods are allowed. Agree on restrictions to avoid damage or disruption. Gather building layouts, staff routines, and public details for the targeted physical location.
Step 2: Reconnaissance
Visit the site to observe security operations, monitor entry points, and note guard schedules. Study cameras, locks, badge readers, and weak spots, paying close attention to server room protections.
Step 3: Attack Simulation
- Social Engineering: Attempt to trick staff into granting access by posing as employees or vendors.
- Badge Cloning: Use scanners to copy RFID badges without physical contact.
- Lock Picking: Open secured doors using lock-picking tools quietly and quickly.
- Device Planting: Hide small devices like network implants or keyloggers inside the building.
Step 4: Documentation
Capture photos, videos, and timestamps during breaches. List entry points exploited and describe how security was bypassed without causing harm. Document any security incidents that occur during testing for thorough analysis.
Step 5: Debrief and Recommendations
Review the test with company leadership. Provide a report showing vulnerabilities and suggest improvements like stricter badge policies, employee training, or better surveillance.
Common Physical Penetration Techniques
Physical penetration testing involves tactics that mirror real-world intrusions. Here are the most common techniques used to bypass physical security measures:
- Tailgating: Following an authorized person through a secured entrance without presenting credentials.
- Lock Picking and Bypassing: Opening locks using traditional picking tools or exploiting design flaws without leaving visible damage.
- Badge Cloning: Copying RFID or NFC access cards by capturing the signal and duplicating the credentials.
- Social Engineering: Posing as staff, delivery personnel, or contractors to trick employees into granting access.
- Dumpster Diving: Searching trash bins for documents, badges, or other sensitive materials that can assist in breaching security.
- Forced Entry: Using tools or brute force to break doors, windows, or barriers when stealth is not a priority.
- Piggybacking with Equipment: Carrying large objects to appear legitimate and reduce scrutiny from guards or employees.
- Evading Surveillance: Identifying camera blind spots or timing movements to avoid detection.
These techniques are often used in combination to increase success. Testing with these methods exposes weaknesses that criminals could easily exploit.
Physical Penetration Testing Tools
Here is a list of common tools used during a physical pen test, each serving a specific purpose for bypassing controls or gathering information:
- Lock Picks and Bypass Tools: Open doors and cabinets without leaving damage in sensitive areas.
- RFID Cloners: Copy access badges to bypass entry systems, helping identify vulnerabilities in access control.
- Portable Scanners: Detect badge frequencies and network signals during the early stages of a security assessment.
- Covert Cameras: Secretly capture photos and videos of access points for later review of security incidents.
- Network Implant Devices: Plant small hardware for remote access and monitor network activity discreetly.
- USB Drop Devices: Deliver malicious payloads through USB ports to expose weaknesses.
- Disguise Materials: Blend in using fake badges and uniforms to bypass guards unnoticed.
- Drones: Perform aerial surveillance to spot security gaps and areas missed by security teams.
How Can Bright Defense Help You With Physical Penetration Tests?
Bright Defense helps assess the real-world resilience of your physical security by testing facility entry controls, badge systems, staff response, and access to sensitive areas. Our team simulates unauthorized access attempts using tactics like tailgating, lock bypass, and impersonation to reveal practical exposure.
Why Choose Bright Defense for Physical Pen Testing?
- Real-World Testing: We simulate intrusions using actual adversary tactics, not theory or checklists.
- Clear Deliverables: Reports detail access gained, methods used, and specific fixes for physical gaps.
- Adaptable Scenarios: Choose from Office (workspace access), Data Center (restricted zones), or Hybrid (multi-site + asset risks).
- Policy-Aware: Tests follow safety, HR, and legal guidelines—results support SOC 2, ISO 27001, and HIPAA safeguards.
FAQs
A security assessment where experts attempt to breach physical controls like doors, locks, cameras, and access systems to reveal real-world vulnerabilities.
Techniques include tailgating, lock picking, badge cloning, impersonation, dumpster diving, and bypassing physical barriers.
It identifies weaknesses that digital security can’t catch such as unlocked doors, careless staff behavior, or unmonitored entry points.
There are black box (no prior information), white box (full knowledge), gray box (partial info), covert (unannounced), and overt (with notice) testing.
Typically two to six weeks depending on facility size, access permissions, and depth of testing involved.
Yes, written authorization, clear scope, and legal agreements are mandatory to ensure ethical and lawful testing.
Weak doors, unsecured sensitive areas, poor camera coverage, credential cloning, and staff being easily social engineered.
Detailed descriptions of breach scenarios, evidence (photos or logs), risk levels, and practical recommendations for remediation.
At least annually or after major changes like facility renovations, security upgrades, or new policy rollouts.
Costs range from around $5,000 for standard assessments to over $20,000 for complex multi-site evaluations.
Get In Touch



