August 7, 2025
Continuous Compliance – The Ultimate Guide
Continuous compliance is rapidly becoming standard practice for cybersecurity. 91% of organizations plan to implement continuous compliance in the next five years, according to Drata. Continuous compliance ensures businesses perpetually align with security and regulatory standards, lowering the risk of a security breach and eliminating the scramble to prepare for traditional annual audits.
In this blog, we will:
- Define continuous compliance and outline its benefits.
- Contrast continuous compliance with the traditional compliance model.
- Review the key components of a successful continuous compliance strategy.
- Discuss how you can implement continuous compliance in your organization and how Bright Defense can help.
Let’s get started!
What is Continuous Compliance?
Continuous compliance refers to the ongoing process of monitoring and maintaining adherence to regulatory, legal, and internal security requirements. Rather than relying on periodic assessments or annual audits, it integrates automated checks, real-time monitoring, and regular reporting into daily operations. This approach allows organizations to quickly detect and address compliance gaps before they become critical issues.
Some of the benefits of using continuous compliance include:
Reduces the risk of compliance failures and fines.
Saves time and resources compared to manual compliance checks.
Helps security teams maintain visibility and control over compliance posture.
Improves overall security by detecting policy violations early.

Benefits of Continuous Compliance
Continuous compliance transforms compliance from a reactive process into an ongoing security advantage. Instead of waiting for audits or scrambling to collect evidence, it gives organizations control and clarity over their security posture every day.
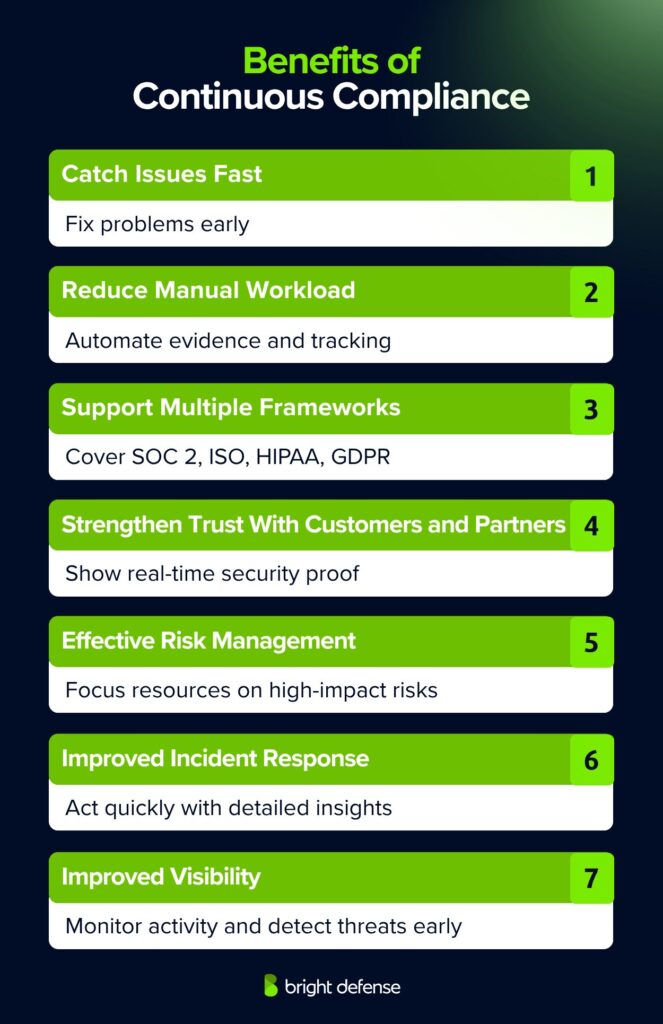
1. Catch Problems Early
Traditional compliance can leave gaps unnoticed until the next audit. Continuous compliance surfaces issues like expired access permissions or incomplete vendor assessments in real time. This allows teams to resolve problems while they are small, preventing last-minute surprises and potential audit findings.
2. Reduce Manual Workload
Manually collecting evidence, tracking policies, and mapping controls consumes valuable time. Automated continuous compliance lightens that burden, freeing risk managers, compliance leads, and IT security teams to focus on strategic initiatives rather than repetitive tasks.
3. Support Multiple Frameworks
Most organizations must comply with more than one standard or regulation. Continuous compliance simplifies this by mapping shared controls across frameworks such as SOC 2, ISO 27001, HIPAA, and GDPR. This approach avoids duplication and supports consistent security practices across all obligations.
4. Strengthen Trust With Customers and Partners
Clients and partners are increasingly cautious about data handling practices. Continuous compliance allows organizations to demonstrate readiness at any moment, proving their security commitment with real-time evidence. This transparency builds confidence and supports long-term business growth.
5. More Effective Risk Management
With continuous compliance, organizations can identify and prioritize security risks based on severity and impact. This allows resources to be allocated effectively and improves the efficiency of overall risk management efforts.
6. Improved Incident Response
Continuous monitoring delivers detailed insights into security events, including their source, nature, and scope. With this level of information, response teams can act quickly and contain incidents before they cause significant harm.
7. Imrpoved Visibility
Continuous compliance provides a clear view of network activity, user behavior, and system logs. This ongoing visibility makes it easier to detect unusual patterns or potential security threats early, enabling faster and more effective corrective action.
Key Areas of Continuous Compliance
Continuous compliance depends on monitoring and maintaining multiple interconnected areas. These areas must operate as a cohesive framework, often supported with automation, clear policies, and team training.
Below is a deeper look at each component and how it contributes to a strong, continuous compliance program:

1. Policy Management
Policies act as the foundation of compliance. They define how employees interact with systems, handle data, and respond to security incidents. Effective policy management involves:
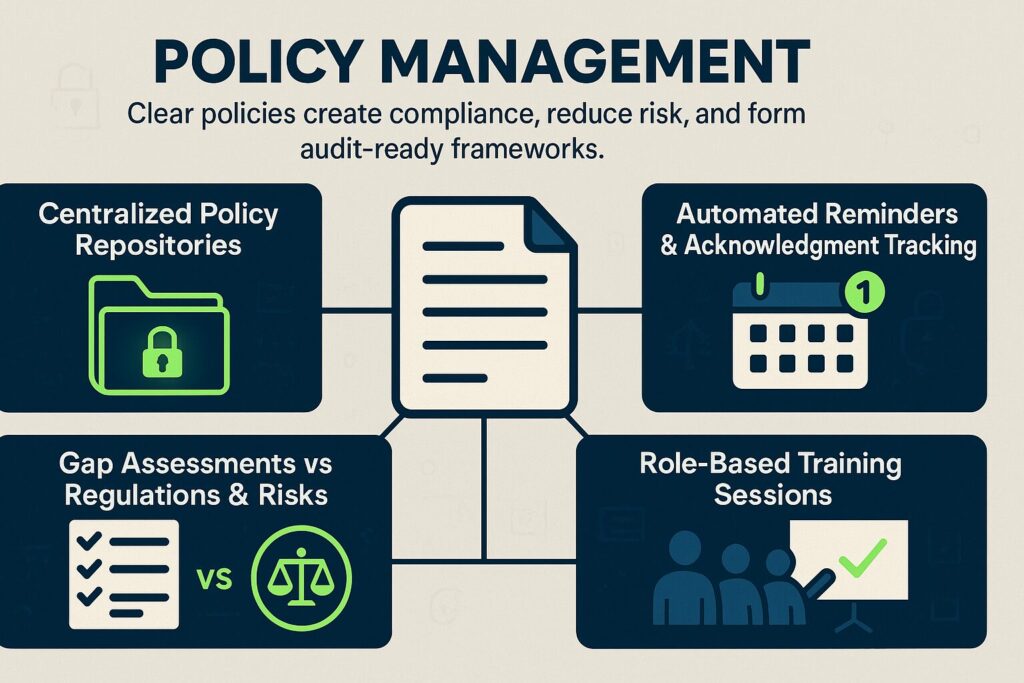
- Centralized policy repositories so employees always reference the most current version of policies.
- Automated reminders and acknowledgment tracking to confirm employees review and accept policy changes.
- Regular gap assessments comparing existing policies to new regulations or evolving risks, then updating accordingly.
- Targeted training sessions for different roles to reinforce critical policies, such as password handling, acceptable use, and access control procedures.
When managed well, policy frameworks create clear expectations, reduce accidental violations, and form the baseline for audit evidence.
2. Vendor Management
Third-party vendors often have access to sensitive systems or data, which creates new risk points. An effective vendor management program includes:
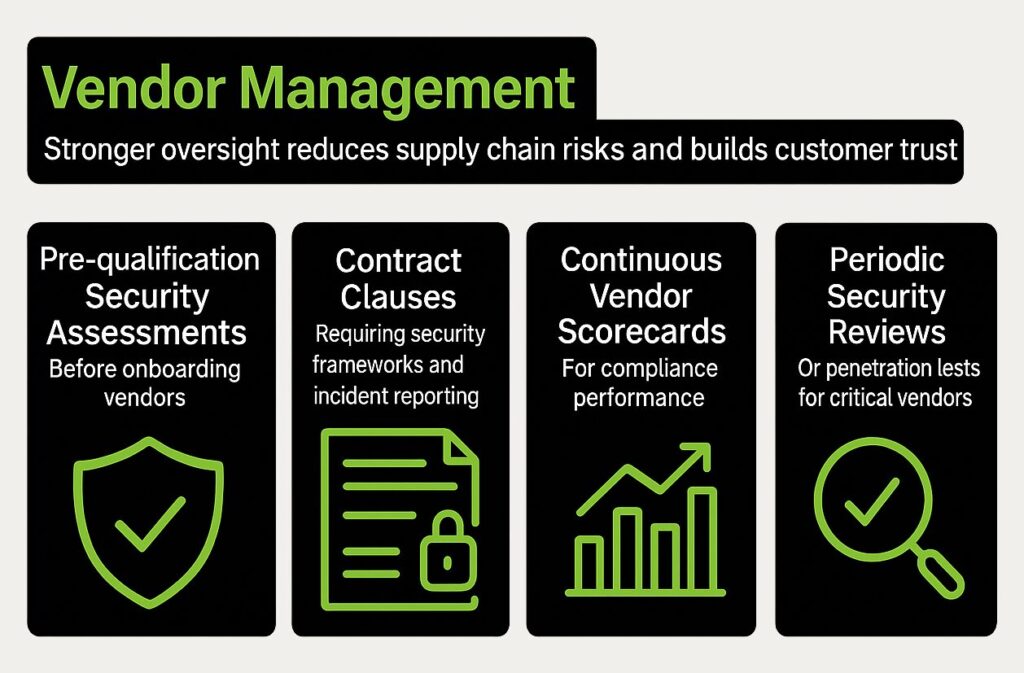
- Pre-qualification security assessments before onboarding vendors, focusing on data protection practices and regulatory certifications.
- Contract clauses that require adherence to security frameworks (like SOC 2 or ISO 27001) and ongoing reporting of any incidents.
- Continuous vendor scorecards that measure compliance performance, updated whenever risk assessments or audits occur.
- Periodic security reviews or penetration tests for critical vendors, ensuring external parties uphold agreed security levels.
This level of vendor oversight reduces exposure from supply chain attacks and strengthens trust with customers who rely on your vendor relationships.
3. Vulnerability Management
Vulnerability management identifies and addresses weaknesses in systems before attackers can exploit them. A strong program involves:
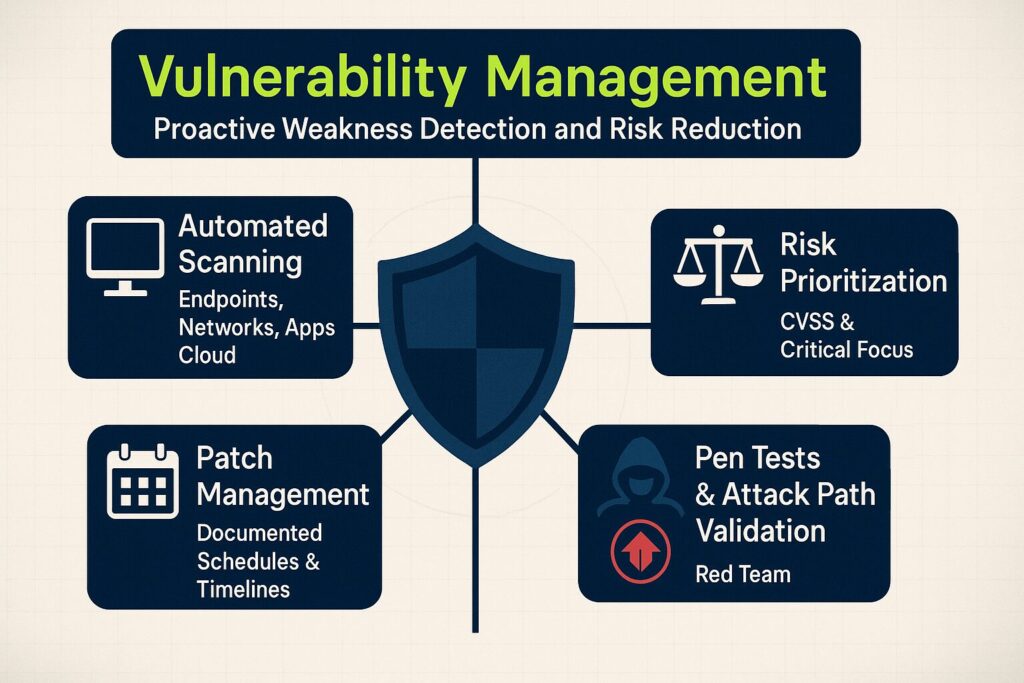
- Automated scanning tools to continuously identify vulnerabilities across endpoints, networks, applications, and cloud infrastructure.
- Risk-based prioritization frameworks (for example, CVSS scoring) to focus on critical vulnerabilities that pose the greatest risk.
- Documented patch management schedules with clear timelines for addressing known weaknesses.
- Red team exercises and penetration testing to validate remediation processes and discover complex attack paths that scanners might miss.
Proactive vulnerability management helps prevent system compromises, ransomware incidents, and compliance violations.
4. Incident Management
No security program is perfect, which makes incident detection and response essential. Key elements include:
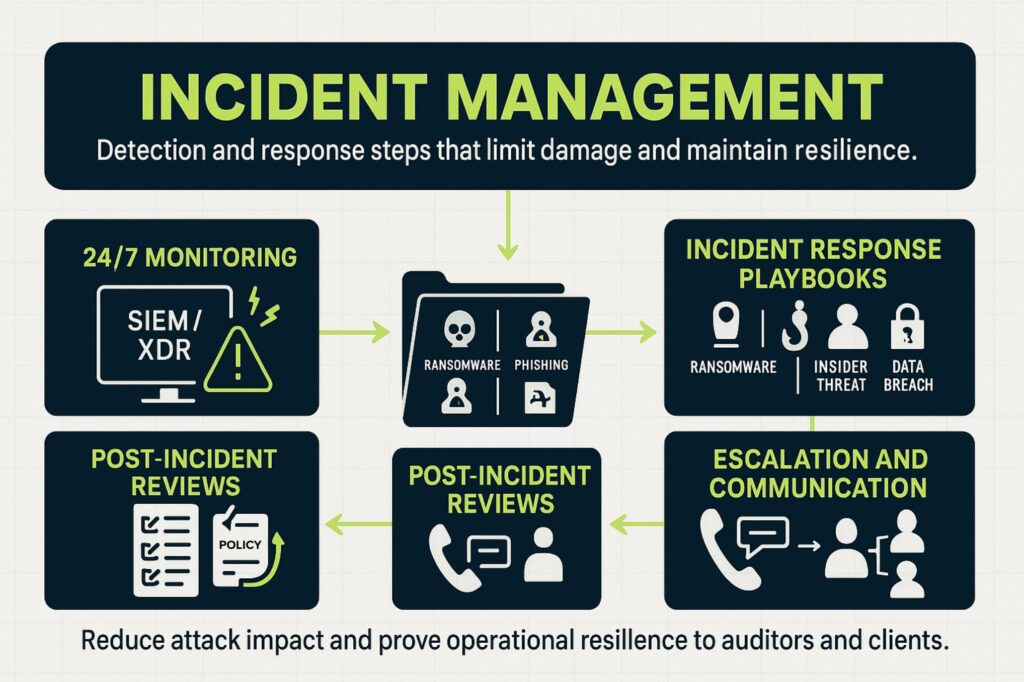
- 24/7 monitoring through SIEM or XDR platforms for real-time threat detection and alerting.
- Defined incident response playbooks covering ransomware, phishing, insider threats, and data breaches.
- Clear escalation procedures and communication plans so critical personnel are notified and response steps begin immediately.
- Post-incident reviews (lessons learned) that identify gaps, adjust policies, and prevent future recurrences.
An effective incident management program reduces damage from attacks and demonstrates operational resilience to auditors and clients.
5. Data Management
Data is the lifeblood of modern businesses and a prime target for attackers. Compliance programs need structured data governance, including:

- Data classification and labeling systems that define what information is sensitive and how it should be protected.
- Access controls and encryption to protect data at rest and in transit.
- Retention and deletion policies to prevent storing unnecessary sensitive information.
- Regular audits of data repositories to verify accuracy, remove redundant data, and confirm compliance with privacy regulations like GDPR or HIPAA.
Managing data correctly limits exposure, reduces compliance risk, and builds trust with customers.
6. Risk Management
Risk management identifies potential threats and prioritizes how to address them. Continuous compliance incorporates:
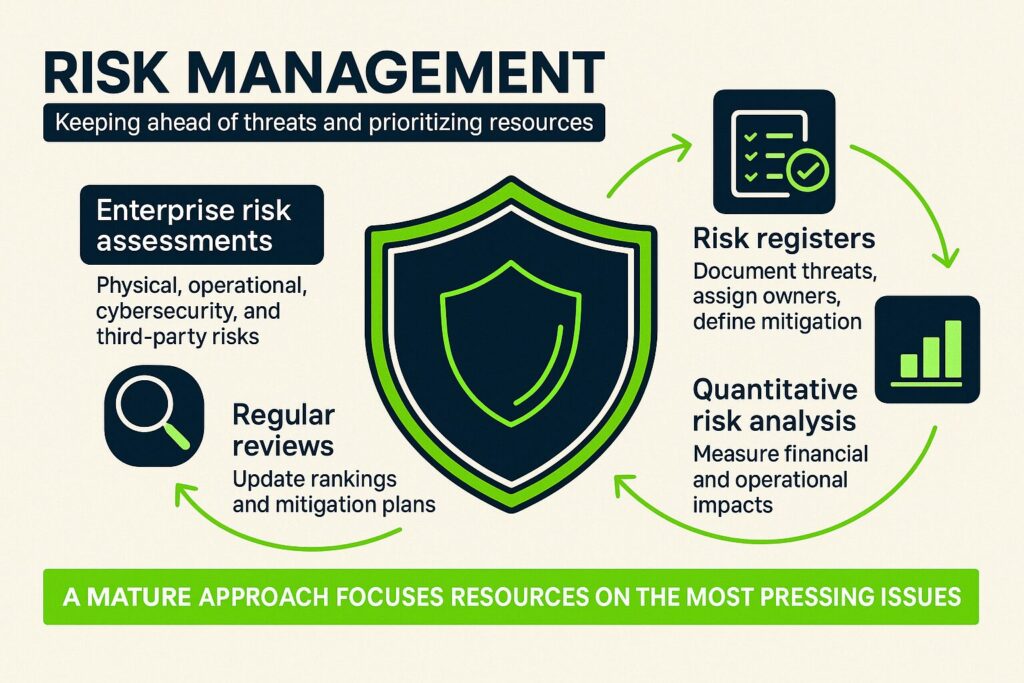
- Enterprise risk assessments to uncover physical, operational, cybersecurity, and third-party risks.
- Risk registers that document threats, assign risk owners, and define mitigation actions.
- Quantitative risk analysis to measure financial and operational impacts if specific risks materialize.
- Regular reviews and updates to ensure risk rankings and mitigation plans reflect changing business conditions and technology stacks.
A mature risk management approach keeps organizations ahead of emerging threats and ensures resources focus on the most pressing issues.
7. Business Continuity Management (BCM)
BCM focuses on resilience and the ability to operate through disruptions. Core elements include:

- Business impact analysis (BIA) to identify critical processes and systems that need immediate restoration during downtime.
- Disaster recovery plans for key IT systems and data stores, including offsite backups and failover mechanisms.
- Tabletop exercises and live drills to practice recovery procedures and identify operational bottlenecks.
- Ongoing monitoring of critical vendors and infrastructure that support continuity efforts, such as cloud providers or backup services.
Strong BCM practices limit downtime, minimize revenue loss, and maintain customer confidence during disruptions.
8. HR Management
Human resources are often overlooked in compliance but play a major role. Continuous compliance requires HR teams to:
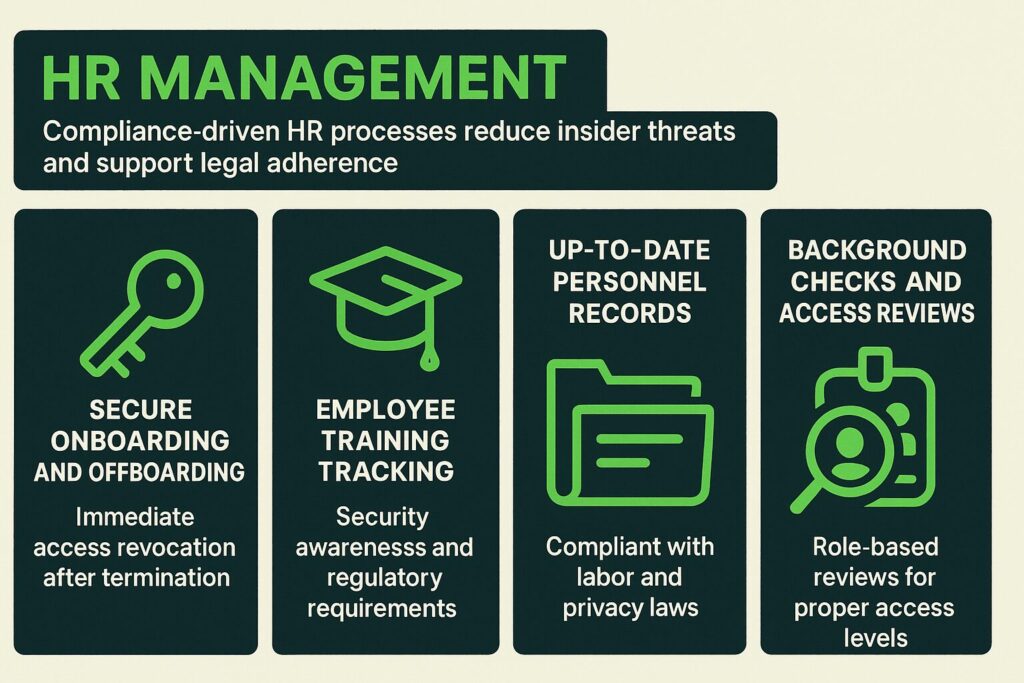
- Enforce secure onboarding and offboarding processes (e.g., immediate revocation of access upon termination).
- Track employee training completion for security awareness, privacy policies, and regulatory requirements.
- Maintain up-to-date personnel records that comply with labor laws and privacy standards.
- Conduct regular background checks and role-based access reviews to ensure employees have appropriate levels of access.
HR compliance helps create a safe workplace culture and supports legal adherence while reducing insider threat risks.
Continuous Compliance vs Periodic Compliance
Organizations approach regulatory and security requirements through different compliance methods. Two common approaches are continuous compliance, which emphasizes real-time or frequent automated checks, and periodic compliance, which relies on scheduled reviews.
Let’s find out more about their differences:
Continuous Compliance vs Periodic Compliance Comparison Table
| Aspect | Continuous Compliance | Periodic Compliance |
| Monitoring Frequency | Real time or near real time | At scheduled intervals |
| Technology Involvement | High (automation and integration) | Low to moderate |
| Risk Detection | Immediate, proactive | Delayed, reactive |
| Reporting | Ongoing dashboards, live data | Point-in-time reports |
| Suitability | Cloud, dynamic IT, agile operations | Stable, traditional IT setups |
Continuous Compliance
Continuous compliance, as stated previously, refers to an approach where compliance checks and monitoring occur in real time or at frequent, automated intervals. It focuses on maintaining an ongoing state of adherence to regulatory or internal security standards.
Characteristics of Continuous Compliance
- Automation: Uses automated tools to monitor controls, configurations, and processes continuously.
- Real-Time Alerts: Provides immediate notifications of deviations or policy violations.
- Integration with Security Operations: Often integrated with security systems, such as SIEM (Security Information and Event Management) and cloud security posture management.
- Proactive Posture: Detects and addresses issues before they become larger compliance failures.
Advantages Continuous Compliance
- Faster detection and remediation of compliance gaps
- Reduced risk of audit surprises
- Easier reporting due to continuous data collection
- Suitable for dynamic environments like cloud infrastructure and DevOps pipelines
Periodic Compliance
Periodic compliance involves scheduled assessments at defined intervals, such as quarterly, semiannual, or annual reviews. It is traditional and often tied to regulatory reporting cycles.
Characteristics
- Manual Assessments: Relies on checklists, interviews, and point-in-time scans.
- Static Reporting: Produces compliance reports valid only for the time of assessment.
- Lower Resource Requirements Between Audits: Monitoring is limited to set audit periods.
- Reactive Posture: Issues often surface during scheduled audits rather than in real time.
Advantages
- Simpler for small, static environments
- Less costly to implement initially
- Well understood by auditors and regulators
How to Achieve Continuous Compliance
1. Adopt a Framework as the Foundation
Select a recognized compliance framework that suits your operational and regulatory needs. Examples include SOC 2, ISO 27001, HIPAA, and PCI DSS. This framework serves as the baseline for security, availability, and confidentiality requirements.
2. Map Controls to Business Processes
Connect compliance controls to existing workflows. This approach creates visibility into how security and privacy measures influence day-to-day operations. It also makes it easier to evaluate changes in processes or technology without disrupting compliance efforts.
3. Automate Evidence Collection
Use compliance monitoring tools that can track configuration changes, log access activities, and monitor security posture in real time. Automation reduces manual audit preparation work and provides auditable records for each control.
4. Establish Continuous Monitoring
Implement security information and event management (SIEM) tools, endpoint detection, and vulnerability scanning to detect non-compliance issues quickly. Pair these with alerting mechanisms for critical deviations.
5. Maintain Policy Version Control
Document every policy and procedure with revision history. Each update should include ownership, approval, and a review cycle to maintain consistency with regulatory requirements.
6. Train Staff Regularly
Compliance success depends on employee awareness. Schedule training sessions on security best practices, data handling, and reporting responsibilities. Refresh training when regulations or policies change.
7. Schedule Internal Audits
Conduct routine internal audits that replicate external auditor expectations. These audits help identify gaps early and reduce the risk of last-minute corrective action before an external assessment.
8. Monitor Regulatory Changes
Compliance rules evolve. Assign responsibility to track changes in relevant regulations. Incorporate these updates into your framework and adjust controls as required.
9. Establish an Incident Response Process
A documented and tested incident response plan helps handle breaches or non-compliance events. Include a communication protocol, evidence preservation steps, and remediation activities.
10. Use a Compliance Dashboard
A central dashboard gives visibility into the status of each control and evidence record. It supports executive oversight and simplifies preparation for external reporting.
Final Thoguhts
In today’s compliance landscape, relying solely on periodic checks for compliance can leave organizations vulnerable and ill-prepared. Continuous compliance emerges as a proactive, adaptive, and robust approach. It ensures that businesses remain ahead of potential threats and always align with regulatory standards.
By shifting from a reactive to a proactive mindset, companies safeguard their operations and instill greater confidence among partners, stakeholders, and customers. Embracing continuous compliance means investing in technology, training, and culture — but the returns, both in security and reputation, are invaluable. As regulations continue to evolve and the digital realm becomes even more intricate, the importance of a steadfast commitment to continuous compliance will only grow.
Bright Defense is Your Continuous Cybersecurity Compliance Partner
Are you ready to achieve continuous compliance? Bright Defense can help. Our mission is to defend the world from cybersecurity threats through continuous compliance. We help you improve your security posture to help mitigate the risk of a data breach.
With our monthly service offering, our CISSP and CISA-certified security experts will develop and execute a cybersecurity plan to meet compliance standards, including SOC 2, CMMC, HIPAA, ISO 27001, and NIST. Our service includes:
- Gap analysis
- Risk assessment and risk management
- Generation and implementation of security policies
- Business continuity planning
- Certification assistance
We also include our managed compliance automation platform, security awareness training, phishing testing, and vCISO services.
Get started today with Bright Defense!
FAQ: Continuous Compliance Explained
1. What is the difference between the compliance process in periodic and continuous approaches?
Periodic audits typically focus on reviewing and maintaining compliance with standards at specified intervals, such as an annual audit. In contrast, continuous compliance is an ongoing process where businesses continuously monitor and maintain compliance, addressing any compliance issues in real-time.
2. How can continuous compliance help identify security gaps?
Continuous compliance offers real-time visibility into security practices and controls. This proactive approach allows for immediate risk detection, ensuring that security gaps are identified and addressed promptly, rather than waiting for scheduled internal audits or third-party compliance audits.
3. Does continuous compliance replace my annual audit?
No, continuous compliance complements annual or periodic audits. While you’ll still undergo compliance audits, the process becomes smoother as potential issues have already been addressed. This often results in fewer surprises during the audit, thanks to the ongoing compliance efforts.
4. How does continuous compliance fit into a cloud infrastructure?
Cloud infrastructures often house data across multiple frameworks and regions. Continuous compliance ensures that all areas of the cloud infrastructure adhere to internal policies and compliance standards consistently, providing an added layer of security controls.
5. What are the key benefits of continuous compliance?
The benefits of continuous compliance include rapid risk detection, reduced chances of non-compliance penalties, and maintaining a competitive advantage for business in today’s dynamic business environment. Additionally, it fosters trust among third-party vendors and stakeholders, as they recognize the business’s commitment to stringent security practices.
6. How can businesses manage achieving compliance across different regulatory standards?
Continuous compliance management tools often support multiple frameworks, allowing businesses to seamlessly align with various standards. This ensures that even if a business operates under multiple regulations, it can maintain compliance effectively and efficiently.
7. How does continuous compliance support internal rules?
Beyond aligning with external regulations, businesses often have internal rules to uphold their standards. Continuous compliance ensures that these internal rules are consistently met, further enhancing the security and integrity of the organization.
8. Is it a challenge to implement continuous compliance in established businesses?
While introducing any new system can have its challenges, the long-term benefits outweigh initial setup efforts. Businesses can close compliance gaps by integrating continuous monitoring tools, training staff, and adopting a proactive approach to compliance, making it an integral part of daily operations.
9. How do third-party vendors fit into the continuous compliance picture?
Third-party vendors can introduce potential risks. Continuous compliance helps monitor and ensure that these vendors also adhere to the necessary compliance standards, reducing potential vulnerabilities.
10. How much time can continuous compliance save compared to traditional audits?
Continuous compliance can reduce manual compliance work by 30 to 50 percent, according to industry benchmarks. Traditional compliance audits often require 3–6 months of preparation, while automated continuous compliance solutions can cut preparation time to a few weeks or even days by maintaining an always-audit-ready state.
11. What is the financial impact of adopting continuous compliance?
Organizations implementing continuous compliance solutions report average cost savings of 25–40 percent on audit and compliance-related expenses. For example, a mid-sized enterprise spending $500,000 annually on compliance audits could save between $125,000 and $200,000 each year after automation.
12. How does continuous compliance affect security incident rates?
Companies leveraging continuous compliance and automated security controls experience 40–60 percent fewer compliance-related security incidents. One study showed that enterprises with automated compliance monitoring had an average of 1.7 incidents per year compared to 4.5 incidents in organizations using manual processes.
13. What adoption trends exist for continuous compliance tools?
The market for continuous compliance platforms is projected to grow at a compound annual growth rate (CAGR) of 14.3 percent, reaching $3.5 billion by 2027. Currently, around 45 percent of enterprises in regulated industries (finance, healthcare, SaaS) use at least one continuous compliance automation solution.
14. How many compliance frameworks can be supported simultaneously?
Modern continuous compliance tools can map and monitor 10 to 20+ compliance frameworks simultaneously (e.g., SOC 2, ISO 27001, HIPAA, PCI-DSS). This can reduce duplicate control testing by up to 60 percent, significantly improving efficiency for companies with multi-regulatory obligations.
15. What core components make up a continuous compliance program?
Effective programs combine real‑time monitoring, automated control testing, audit‑ready reporting, dynamic risk registers, vendor and asset compliance checks, policy lifecycle workflows, and centralized dashboards to unify data and evidence across the organization
16. What step‑by‑step approach can be used to implement continuous compliance?
Typical steps include: assessing existing compliance posture; conducting gap analysis; mapping controls to relevant standards; developing policies and processes; implementing automation tools; training employees; and continuously reviewing evidence and performance.
17. What features should you look for in continuous compliance tools or platforms?
Seek platforms offering automated control testing, real‑time dashboards, audit‑ready evidence mapping, framework coverage (e.g. ISO, SOC, NIST), policy versioning and attestations, risk and asset management, and vendor compliance tracking.
18. How does automation support continuous compliance and what cost savings can it deliver?
Automation enables daily or real‑time compliance checks, alerts on drift, and streamlined reporting—reducing manual effort, lowering breach-related costs (e.g. savings averaging ~$1.9 million per breach), and creating predictable resource demands scrut.io.
19. How can organizations embed compliance into daily workflows to ensure sustainability?
Embedding compliance means integrating controls into DevOps pipelines, access management, onboarding/offboarding, HR processes, vendor management, and change control procedures so that compliance activities happen naturally as work is done.
20. What cultural and organizational change is needed to sustain continuous compliance over time?
Sustainable compliance requires leadership buy‑in and tone‑at‑the‑top, a dedicated compliance owner, clear incentives and accountability, collaboration between compliance and operations teams, and ongoing training so teams understand their roles in maintaining compliance daily.
Get In Touch