
What is Whaling in Cybersecurity?
Whaling is a targeted phishing method that focuses on high-ranking executives to steal sensitive information or authorize fraudulent actions. These attacks are dangerous because they often bypass typical red flags and rely on trust, authority, and familiarity to succeed.
In this blog, we’ll break down what whaling is, how it works, and why it poses a serious threat to organizations. We’ll also cover how to recognize whaling attempts, real-world examples, and practical steps to prevent them. Whether you’re part of the security team or an executive yourself, this guide will help you understand the risks and reduce your chances of falling victim.
Key Takeaways
- Whaling targets high-level executives using personalized, deceptive messages that mimic trusted contacts and appear legitimate.
- Attackers build trust through social engineering, often referencing real-life details to increase believability before requesting sensitive data or payments.
- Common victims include CEOs, CFOs, HR, finance, and IT staff—anyone with access to financial systems or confidential information.
- Consequences include data leaks, financial fraud, operational disruptions, and long-term damage to reputation and trust.
- Preventing whaling requires a mix of executive training, anti-impersonation tools, email authentication, and multi-layered phishing defenses.
What is Whaling?
Whaling is a type of phishing attack that targets senior executives, board members, or individuals with control over sensitive systems, finances, or decision-making authority. These attacks use highly personalized messages to trick the victim into approving fraudulent payments, revealing confidential data, or granting access to internal systems.

Whaling attacks have increased 131% in recent years, and 59% of organizations report that at least one executive has been targeted (Hoxhunt). Although they make up less than 0.5% of all phishing attempts, nearly 60% of spear phishing campaigns which include whaling are successful (Fraud.Net).
How Whaling Attacks / Whaling Phishing Works
Whaling attacks typically start through familiar channels such as email or internal messaging platforms. The attacker impersonates someone the target trusts, often a colleague, vendor, or executive, using a spoofed or lookalike email address.
In the next sections, we’ll walk through the steps attackers follow, from the first message to the final request, and why these tactics are so effective against executives.
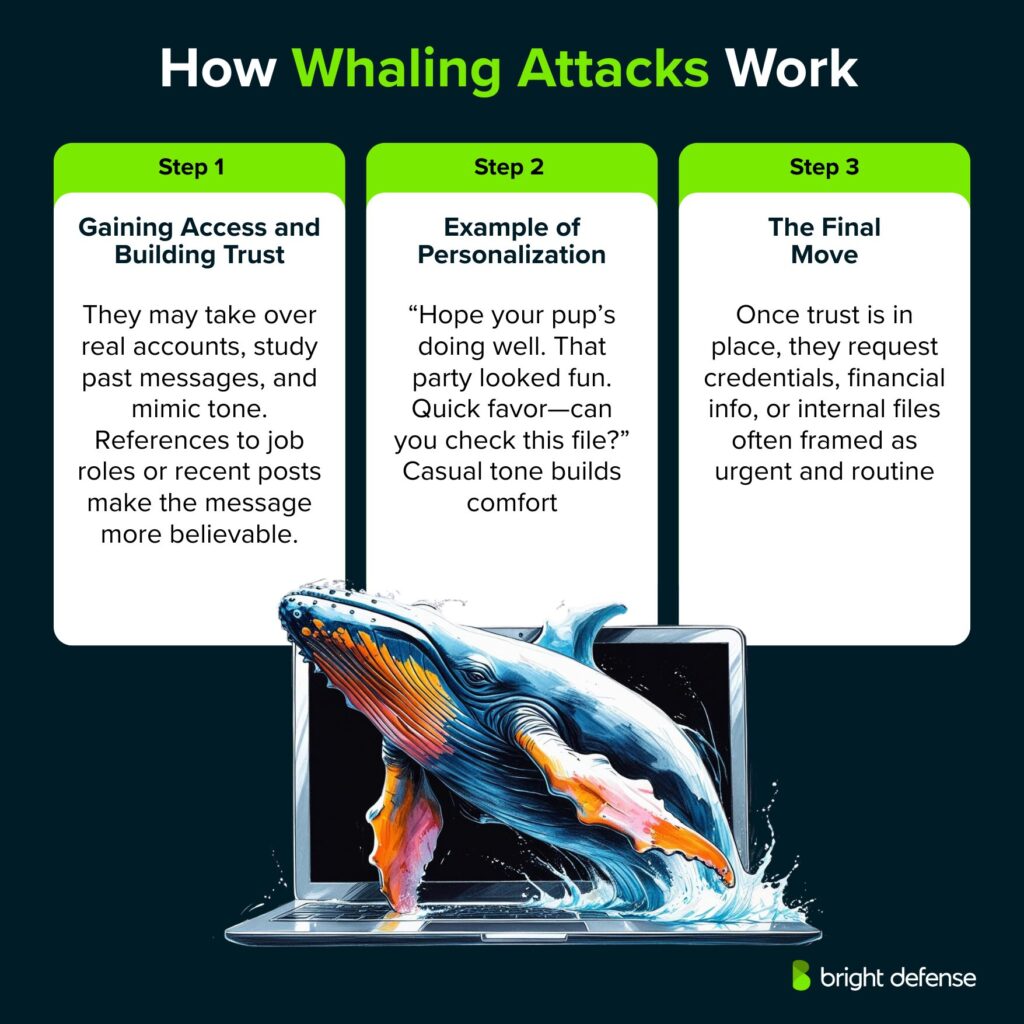
1. Gaining Access and Building Trust
In more advanced cases, the attacker gains access to the actual email account of the impersonated individual. Once inside, they review past conversations, observe writing habits, and send messages directly from the compromised account.
To make their communication more believable, attackers often reference specific personal or professional details. These may include job roles, company events, or recent posts on LinkedIn or other social platforms. The more personalized the message, the harder it is for the target to spot the deception.
2. Example of Personalization
Imagine an executive recently shared a post about their new dog and a past holiday party. An attacker could reference both in a message like:
“Hope your new pup is settling in. That end-of-year party looked fun—wish I could’ve made it. Quick thing—can you review this file before I send it off?”
This casual, friendly tone lowers suspicion and increases the chance of compliance.
3. The Final Move
Once trust is established, the attacker shifts toward their actual goal. This usually involves asking for login credentials, internal documents, or financial information. The request often carries a sense of urgency or appears part of a routine workflow.
At this stage, the attacker may also gather more information to use in future fraud or identity theft. Because the message seems to come from a known contact and fits expected communication patterns, the victim may respond without hesitation.
Who Is Vulnerable to Whaling Attacks?
Whaling attacks focus on individuals with access to sensitive data, financial authority, or decision-making power. These roles are attractive to attackers because they can often bypass approval layers or trigger high-impact actions quickly.
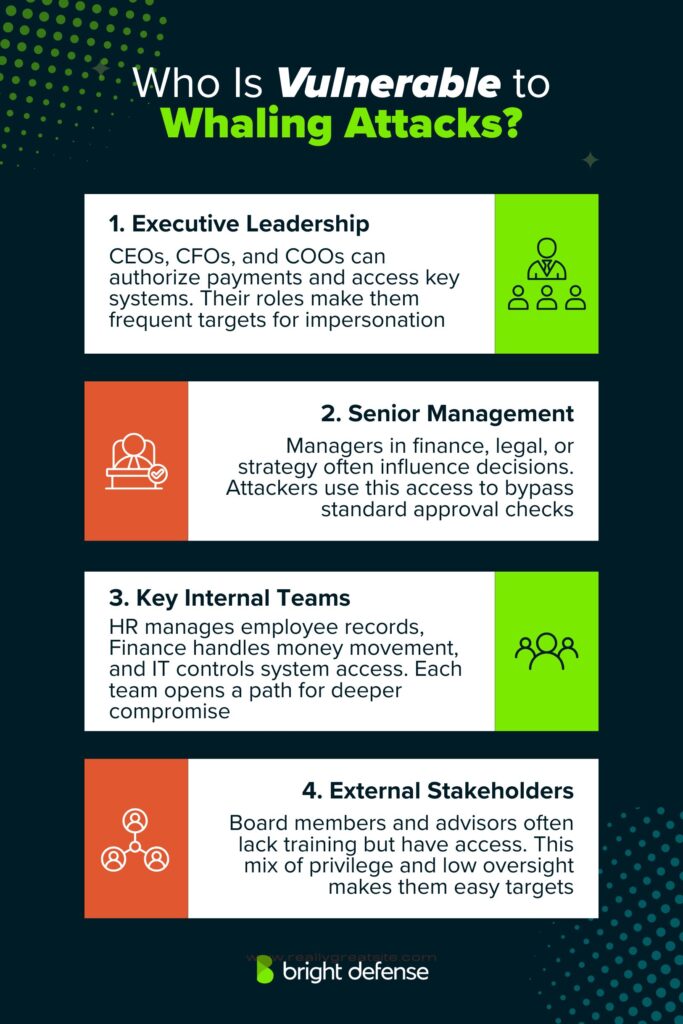
1. Executive Leadership
Top-level executives such as CEOs, CFOs, and COOs are common targets. Their ability to approve transactions, authorize access, and oversee company-wide operations makes them prime candidates for social engineering.
2. Senior Management
Department heads and senior managers in finance, legal, or strategy roles are also at risk. Attackers often target these individuals because they can influence core processes without raising red flags.
3. Key Internal Teams
The key internal teams susceptible to whaling attacks are:
- Human Resources: Often handles payroll, tax forms, and personal employee data—all of which are valuable to attackers.
- Finance: Manages invoices, wire transfers, and banking systems, offering direct paths to financial fraud.
- IT Departments: Hold admin-level control over systems, credentials, and access privileges. Compromising IT staff can lead to deeper network infiltration.
4. External Stakeholders
Board members, advisors, and consultants with privileged access may be overlooked in security planning. When these individuals lack awareness of internal security protocols, they become easy targets.
The shared trait among these groups is access, whether to money, systems, or sensitive records. When cyber awareness training is outdated or inconsistent, the risk grows quickly.
What Are the Consequences of a Whaling Attack?
The impact of a whaling attack can reach across multiple areas of an organization, affecting both immediate operations and long-term reputation.
These attacks are highly targeted and often designed to extract the most sensitive or high-value assets. Unlike standard phishing attacks, whaling often mimics legitimate communication and uses social engineering tactics to deceive senior leadership.
Let’s find out more about the different consequences of whaling:
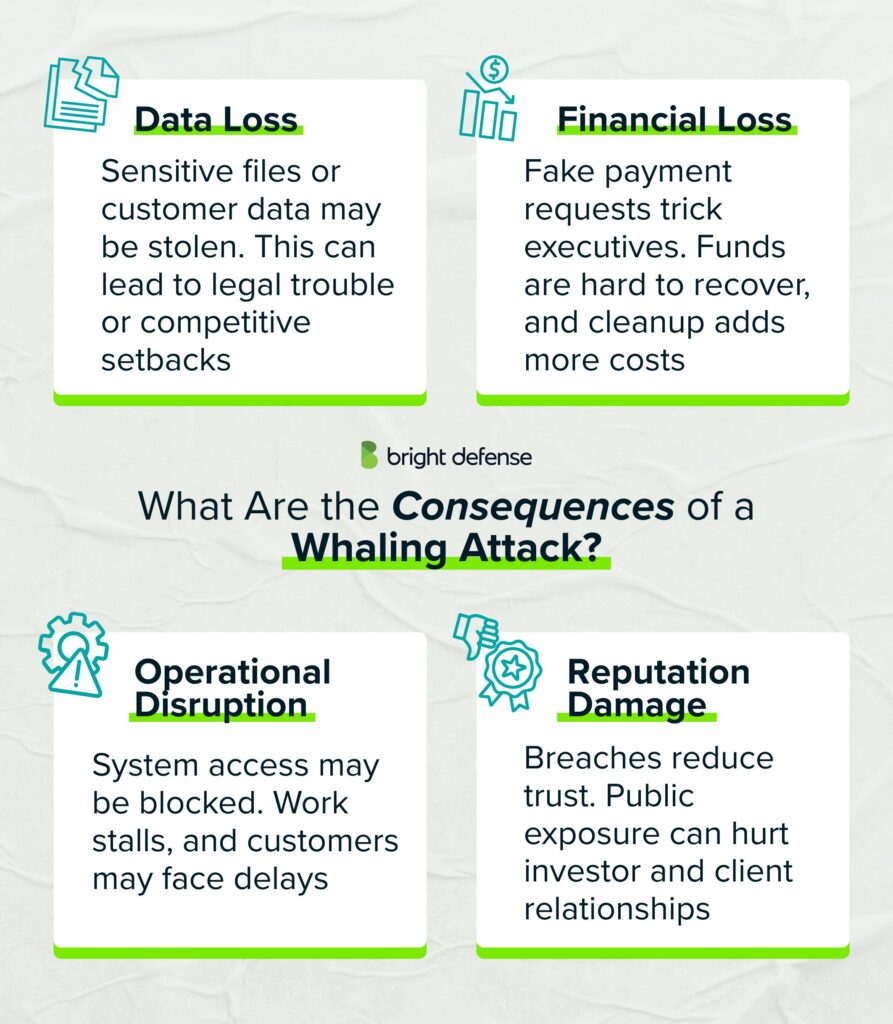
1. Data Loss
A successful attack may result in the unauthorized release of internal documents, trade secrets, legal contracts, or customer information. In some examples of whaling attacks, threat actors have stolen confidential information like board meeting minutes or financial forecasts. Once exposed, this data may not be recoverable and can place the organization at legal or competitive risk.
2. Financial Loss
Attackers may trick executives into authorizing fraudulent wire transfers or redirecting legitimate payments to phishing scams. These types of financial transactions are difficult to reverse. In addition to direct financial loss, businesses often face expenses tied to containment, forensic investigation, insurance claims, and legal support.
3. Operational Disruption
If internal systems are compromised, business functions may be delayed or halted. These whaling attack emails can contain malware or lead to account takeovers, similar to spear phishing attacks, resulting in system lockdowns or data corruption. Teams may lose access to essential files, workflows may pause, and customers may experience service outages or delivery delays.
4. Reputation Damage
Publicly disclosed attacks, especially those involving sensitive client or employee data, erode trust. The reputational fallout from a successful whaling attempt is often severe. Rebuilding brand credibility after a breach is time-consuming and costly. Stakeholders, including investors and customers, may reconsider their relationship with the company.
Whaling attacks carry serious consequences due to their precision and the seniority of the individuals involved. These are not just phishing attempts aimed at random employees, but calculated efforts that mirror tactics seen in internet scams.
How to Block Whaling Attacks or Whaling Phishing?
Preventing whaling attacks requires more than a single control. These threats target human behavior and exploit trust, so a multi-layered security strategy is essential. Below are several methods organizations can implement to reduce exposure and improve resilience:
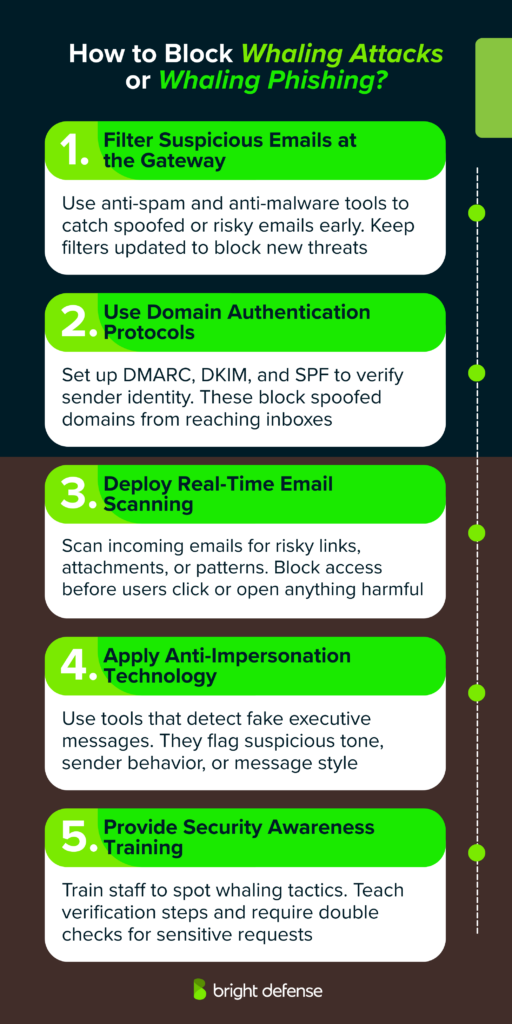
1. Filter Suspicious Emails at the Gateway
Deploy advanced anti-spam and anti-malware tools at the email gateway. These solutions help detect known malicious senders, flag questionable content, and quarantine messages that display characteristics of phishing or spoofing. Regular updates and tuning improve their ability to block new threats.
2. Use Domain Authentication Protocols
Implement email authentication standards such as DMARC (Domain-based Message Authentication, Reporting and Conformance), DKIM (DomainKeys Identified Mail), and SPF (Sender Policy Framework). These protocols verify whether an email truly comes from an authorized sender and help prevent domain spoofing, which is a common tactic in whaling campaigns.
3. Deploy Real-Time Email Scanning
Email scanning and filtering solutions examine messages as they arrive. These tools check for unusual URLs, executable attachments, and suspicious metadata. If threats are detected, access to those elements can be blocked before users interact with them. This step reduces the risk of credential theft or malware execution.
4. Apply Anti-Impersonation Technology
Use anti-impersonation tools that detect social engineering patterns and recognize indicators of executive impersonation. These systems analyze message tone, content, sender behavior, and communication patterns to identify when someone is pretending to be a trusted figure inside the organization.
5. Provide Security Awareness Training
Educate staff, especially executives and finance teams, about the nature of whaling attacks. Training should include real examples, warning signs to look for, and simple verification procedures. Reinforce rules such as verifying any wire transfer or confidential request through a secondary communication channel before acting on it.
Whaling attacks target trust and authority rather than technical vulnerabilities. Combining technical defenses with informed users is the most effective way to reduce the success rate of these attacks.
What Is the Goal of Whaling Attacks / Whaling Phishing?
Whaling attacks are highly targeted and often motivated by specific goals that go beyond random disruption. Cybercriminals tailor these attacks toward senior executives or decision-makers to achieve outcomes that yield significant value. The goals typically include:

1. Financial Gain
Attackers may trick an executive into authorizing a wire transfer to a fraudulent account. These scams are often urgent in tone and disguised as legitimate internal or vendor-related transactions.
2. Privileged Access
Gaining access to administrator credentials or internal systems allows attackers to move laterally within a network. Once inside, they may seek to expand control, disable security tools, or create persistent access routes.
3. Targeting Supply Chains
Whaling attacks can serve as entry points into broader ecosystems. If an executive’s credentials are compromised, attackers may use that access to infiltrate connected vendors, partners, or service providers with weaker security measures.
4. Corporate Espionage
Some attacks are designed to extract proprietary data such as strategic plans, product designs, or trade secrets. This information can then be sold to competitors or used to give rival organizations a strategic advantage.
5. Malware Deployment
Attackers may use social engineering to persuade the victim to download a file or click a link. This opens the door to installing ransomware, keyloggers, or backdoor malware to further compromise the organization.
6. Reputation Damage or Personal Motive
Not all attacks are financially motivated. Some may be driven by a personal grudge or the intent to harm an individual’s reputation. In these cases, attackers may seek to leak sensitive emails, impersonate the executive publicly, or expose internal communications.
In every case, whaling attacks focus on extracting high-value results with minimal visibility. The impact extends beyond the individual targeted, often affecting the entire organization’s finances, data integrity, and reputation.
Examples Of Whaling Phishing Attacks
Some of the whaling phishing attacks include:
1. Seagate Technology (2016)
In 2016, Seagate experienced a whaling attack where an attacker impersonated a senior executive and requested W-2 tax documents from an HR employee. Believing the request was legitimate, the employee sent the documents, which included names, home addresses, Social Security numbers, and income details, affecting approximately 10,000 current and former employees. (Silicon UK)
2. FACC (2016)
Austrian aerospace manufacturer FACC suffered a financial loss of $47 million due to a whaling attack. The attackers posed as the company’s CEO and instructed a finance team member to transfer funds to an overseas account. The breach led to immediate consequences, including the removal of both the CEO and CFO from their positions. (Reuters)
3. Snapchat (2016)
Snapchat faced a whaling incident in 2016 when an attacker impersonated CEO Evan Spiegel and sent a convincing email to a payroll team member, requesting sensitive employee information. The employee responded without verifying the request’s authenticity, resulting in the exposure of personal payroll data. (Fortune.com)
4. Crelan Bank (2016)
Belgium-based Crelan Bank lost over €70 million to a whaling attack. Attackers impersonated high-ranking executives and convinced an employee to initiate unauthorized wire transfers. The fraud was discovered through an internal audit. ( Help Net Security)
5. Barbara Corcoran (2020)
In 2020, “Shark Tank” investor Barbara Corcoran was targeted in a whaling scam where her bookkeeper received a fake invoice for $388,700. The attacker mimicked her assistant’s email address and used real estate terminology to make the message believable. The bookkeeper approved the payment. (Barracuda)
6. Toyota Boshoku (2019)
A subsidiary of Toyota, Toyota Boshoku, suffered a financial loss of $37 million due to a whaling email. Attackers pretended to be business partners and instructed a finance executive to transfer the funds as part of a fake transaction. (CPO Magazine)
7. Pathé Films (2018)
In 2018, French cinema giant Pathé lost nearly €19 million to a whaling scheme. The attackers posed as top executives from the company’s Dutch office and instructed the finance team to send funds to accounts in Asia, claiming it was part of a confidential acquisition. (Variety)
8. Mattel (2015)
In 2015, toy manufacturer Mattel was targeted by cybercriminals who, after studying the company’s internal procedures, impersonated a high-ranking executive and requested a transfer of $3 million to a bank in China. The transfer was executed, but Mattel was able to recover the funds after realizing the fraud. (CSO Online)
How Can We Help
At Bright Defense, we help organizations reduce the risk of whaling attacks through targeted employee education and strategic phishing defenses. Our managed security awareness training, powered by KnowBe4, includes curated phishing simulations and ongoing assessments designed to build long-term vigilance.
While whaling targets executives, it often succeeds because attackers exploit gaps in communication and verification processes. We assist clients in closing those gaps by:
- Running customized phishing simulations that include whaling scenarios
- Educating leadership teams on social engineering tactics
- Supporting incident response planning for executive-level email threats
- Delivering clear metrics through training progress reports
If your organization needs to train senior staff or improve resilience against executive-level phishing, Bright Defense can help structure a solution that fits.
Frequently Asked Questions
Whaling is a phishing tactic aimed at executives or high-ranking personnel within an organization. These emails are carefully written and highly personalized, making them more dangerous than other phishing attacks because they often bypass typical security filters and employee skepticism.
Phishing targets a broad range of users using generic and mass-distributed emails. Whaling, in contrast, uses precision and social engineering techniques to target top-level decision-makers with messages that appear to come from trusted internal contacts.
Signs of a whaling attack include emails that imitate executives but contain slight anomalies in the sender’s email address and request urgent actions involving money or data. The tone may discourage verification and mirror internal language to lower suspicion.
Whaling is a high-level form of spear phishing focused on individuals with significant authority such as CEOs or CFOs. These attacks often result in greater damage because the targets can authorize large transactions or access sensitive systems.
Immediately stop communication with the sender and report the message to your IT or security team. If any action has already been taken, start an investigation and follow your incident response protocol to limit the impact.
Whaling emails are crafted with more care, aimed at manipulating executives through realistic, high-stakes messages. Traditional phishing is broader and often relies on volume, using malicious links or basic trickery.
Executives like CEOs, CFOs, and HR directors are prime targets because they hold decision-making power and rarely face internal challenges. Their roles allow attackers to execute fraudulent wire transfers or gain access with minimal resistance.
These attacks can cause significant financial loss, reputational damage, or exposure of customer data and employee records. Legal consequences and executive job losses often follow if the breach involves compliance failures.
A simulated whaling attack helps identify gaps in executive awareness and trains leadership to detect subtle phishing signs. Regular simulations also reduce the risk of real-world breaches by reinforcing habits.
A simulated whaling attack helps identify gaps in executive awareness and trains leadership to detect subtle phishing signs. Regular simulations also reduce the risk of real-world breaches by reinforcing habits.
11. What are the differences between phishing, spear phishing, and whaling attacks?
| Type | Target | Personalization | Common Goal |
|---|---|---|---|
| Phishing | Anyone | Low | Steal credentials, spread malware |
| Spear Phishing | Individuals/Groups | Medium–High | Targeted access or data |
| Whaling | Executives/C-suite | Very High | Steal funds or access systems |
Whaling stands out for its precision and is often part of broader business email compromise efforts involving targeted deception.
12. Why do attackers target executives?
Executives often bypass standard checks and hold broader access to strategic and financial systems. This makes them ideal targets for attacks involving funds or sensitive items like employee payroll information.
13. Can whaling occur outside email?
Yes, whaling can also take place over text messages, collaboration tools, or messaging apps. Vendor email compromise may allow attackers to send convincing messages from trusted platforms like Slack or Teams.
14. Why are whaling emails harder to detect?
They contain realistic language, no spelling errors, and often reference current projects or team members. These fraudulent requests are hard to catch because they mimic real internal communication perfectly.
15. How can executives avoid whaling attacks?
Executives should verify any high-risk requests through a second method, such as phone or internal tools. Training combined with anti phishing software helps them recognize risky emails before taking action.
16. What belongs in a whaling response plan?
The response plan should include clear containment steps, legal consultation, forensic review, and notification procedures. It must also comply with internal data protection policies and prepare the organization for similar future attempts.
17. How common are whaling attacks?
While less frequent than traditional phishing, whaling attacks are increasing rapidly due to their high return. Executives are now over 12 times more likely to be targeted in social engineering attacks than before.
18. What’s the financial impact of a whaling attack?
Losses can range from thousands to millions, depending on the target and action taken. The Anti Phishing Working Group has reported several seven-figure incidents caused by executive impersonation.
19. How long does it take to detect whaling?
Whaling attacks often take longer to discover because of their subtlety and reliance on trust. Many result in long-term data theft and go undetected for months.
20. How many train for whaling-specific threats?
Less than half of companies offer executive-focused phishing training. Many rely on generic employee education, though some now add spam filters and high-risk user monitoring.
21. What percent of executives fall for simulations?
Executives are more likely to click on deceptive emails, especially those framed with a sense of urgency or authority. Simulations show up to 60% failure rates among senior staff.
22. How to defend against whaling attacks?
Use executive training, dual approval processes, and layered email protection. These methods significantly help defend against whaling attacks and reduce risk organization-wide.
23. Do whaling emails use fake websites?
Yes, some include links to malicious websites that impersonate internal login pages or invoice platforms. This increases the chance of users entering sensitive data without suspicion.
24. Do attackers use fake bank details?
Attackers may redirect payments to fraudulent bank accounts with convincing invoices and altered payment instructions. These changes often go unnoticed until funds are lost.
25. Why do whaling attacks work?
Whaling attacks often work because the impersonation is subtle and plays on the recipient’s respect for hierarchy. Recipients may hesitate to question or verify requests from people in power.
Get In Touch



