
60+ Healthcare Data Breach Statistics for 2026
The team at Bright Defense has put together a detailed collection of healthcare data breach statistics for 2025. This report covers curated statistics on:
- Breach volume across healthcare organizations
- Common causes of data breaches in the healthcare sector
- Year-over-year trends in breach incidents
- Impact of breaches by type (ransomware, phishing, insider threats)
- Regulatory consequences and HIPAA violation patterns
- Geographic distribution of major healthcare breaches
Let’s get straight to the numbers.
Healthcare Data Breach Statistics
- A 2015 cyberattack on Anthem Inc. compromised the personal data of 78.8 million health plan members (HIPAA Journal).
- In 2023, OCR fined four hospitals ~$1.3M total for failing to prevent snooping on celebrity patients’ records (HIPAA Journal).
- Numerous other breaches include LifeLabs (Canada, 2019 – 15M), SingHealth (Singapore, 2018 – 1.5M), HCA Healthcare (USA, 2023 – 11.27M), and Medibank (Australia, 2022 – 9.7M) (Compliancy Group, HIPAA Journal, Reuters).
- In 2024, ~275 million healthcare records were breached in the U.S. (HIPAA Journal).
- From 2018 to 2021, large breaches nearly doubled (+93.7%) (HIPAA Journal).
- In 2019, 49% of breaches were due to hacking, rising to 80% by 2023 (HIPAA Journal).
- Hacking-related breaches jumped 239% from 2018–2023; ransomware surged 278% (HIPAA Journal).
- In 2022, hacking accounted for 71.4% of breaches and 84.6% of compromised records (HIPAA Journal).
- 70% of breach actors in 2024 were internal; 39% in 2022 (Verizon DBIR).
- Business associate breaches increased 337% since 2018 (HIPAA Journal).
- In 2022, only ~18% of breaches came from loss/theft; prior to 2015, that figure was around 50% (HIPAA Journal).
- In Brazil (2020), 16 million COVID-19 patient records leaked after a GitHub error (Tech Times).
- In Canada (2019), 15 million patient records were stolen from LifeLabs (Compliancy Group).
- In Australia (2022), 9.7 million Medibank records were leaked (Reuters).
- In 2024, healthcare made up 23% of all global data breaches (HIPAA Journal).
- Between 2018–2022, ransomware hit 654 healthcare organizations, exposing 88.8 million records (Becker’s).
- In 2023 alone, 143 ransomware incidents were reported (HIPAA Journal).
- 46 U.S. hospital systems (141 hospitals) were affected in 2023 (HIPAA Journal).
- 560 U.S. healthcare facilities were hit in 2020 (Becker’s).
- 44% of healthcare ransomware attacks resulted in care disruption (HIPAA Journal).
- Hospital admissions fell 17–25% after ransomware attacks (HIPAA Journal).
- A patient died in Germany (2020) after being rerouted during a ransomware event (HIPAA Journal).
- An Alabama newborn death was tied to ransomware-caused downtime (HIPAA Journal).
- 42–67 Medicare patients may have died from ransomware-delayed care (2016–2021) (HIPAA Journal).
- In the past year, 92% of healthcare organizations in the United States experienced at least one cyberattack. (HIPAA Journal)
- WannaCry cost NHS £92M and caused 19,000 appointment cancellations (National Health Executive).
- Ireland’s HSE took nearly 4 months to recover from a ransomware attack in 2021 (HHS.gov).
- Barcelona hospital ransomware (2023) led to 150 canceled surgeries and 3,000 delays (Silicon UK).
- 88% of healthcare workers clicked phishing links in tests (HIPAA Journal).
- Stolen credentials caused 19% of breaches in 2022; phishing accounted for 16% (IBM).
- Unauthorized access/disclosure grew 162% recently (HIPAA Journal).
- 24% of physicians couldn’t detect malware; 50% were at risk of privacy breaches (Ponemon).
- A misconfigured database exposed 38 million COVID tracing contacts in 2021 (HIPAA Journal).
- 39% of organizations discovered breaches only after months (HIPAA Journal).
- Average breach lifecycle in healthcare: 277 days; ransomware cases take 320 days (IBM).
- Only 12% of breached firms recovered fully within 3 months in 2023 (HIPAA Journal).
- Ransomware causes ~17 days of downtime; some cases hit 3–4 weeks (Becker’s).
- Downtime costs ~$1.9M/day for hospitals (Becker’s).
- $21.9B lost from downtime (2018–2023) due to ransomware (Becker’s).
- 47% of healthcare ransomware victims paid ransom in 2023 (HIPAA Journal).
- Average ransom demand in 2023 was $1.5M, up from $5,000 in 2022 (HIPAA Journal).
- 2023 average healthcare breach cost: $10.93M; 2024: $9.77M (HIPAA Journal, HIPAA Journal).
- Healthcare breach cost per record: $408 vs ~$148 global average (HIPAA Journal).
- Breach cost in 2019: $6.45M; 2022: $10.10M (HIPAA Journal).
- Ransomware-specific breaches in 2022 cost $4.54M (UpGuard).
- Mega-breaches cost ~9× more than standard ones (IBM).
- 2015 Anthem breach cost ~$380M (HIPAA Journal).
- 2023 Change Healthcare breach (190M records) will likely surpass all prior totals (HIPAA Journal).
- HIPAA penalties can reach $1.9M per violation (HIPAA Journal).
- HHS OCR had 850+ open investigations in early 2024 (HIPAA Journal).
- 45% of victims accepted credit monitoring in 2024, up 85% from 2023 (HIPAA Journal).
- 38% of providers reported patient medical identity theft (Ponemon)
- 51% of breached orgs planned to increase cybersecurity spending (ProAssurance).
- Healthcare allocates <6% of IT budgets to security (HIPAA Journal).
- Average cyber maturity score for healthcare: 54% (HIPAA Journal).
- 25% of healthcare employees lacked phishing awareness training (HIPAA Journal).
- India saw 1.9M healthcare cyberattacks (Jan–Nov 2022) (Cyber Sierra).
- 89% of U.S. health IT leaders faced cyberattacks in 2022 (GetAstra).
- Average of 43 attacks per organization in 2022 (GetAstra).
- 66% of providers see insider breaches as more likely than external ones (HIPAA Journal).
- 94% of healthcare orgs report vendor access to internal systems; 72% give high-level permissions (HIPAA Journal).
- 473% rise in BEC attacks in healthcare (HIPAA Journal).
- ~96 email fraud attempts per quarter in healthcare (HIPAA Journal).
- 74% of ransomware attacks in healthcare targeted hospitals (HIPAA Journal).
- Ransomware attacks in 2021 were 5× more frequent than in 2017 (HIPAA Journal).
Major Healthcare Data Breaches in 2025
1. Manpower Staffing Agency RansomHub Attack (August – 2025)
From December 29, 2024, to January 12, 2025, Manpower’s Lansing, Michigan franchise was compromised in a ransomware attack carried out by RansomHub. Disclosed on August 12, 2025, the breach affected 144,189 individuals and involved the theft of 500GB of sensitive data, including passport scans, Social Security numbers, financial details, and employment histories. Attackers used persistent access and double-extortion tactics, exfiltrating data before deploying ransomware.
While the breach was confined to the Lansing franchise, the exposure of complete identity profiles and client business records created significant risk. Operations at other locations continued without disruption, but security controls across the franchise network required urgent reinforcement. The FBI initiated an investigation, and regulatory notifications began in August.
This incident underscores the need for consistent franchise security standards, improved third-party oversight, data minimization, and resilience planning for payroll and HR systems.
2. Yale New Haven Health Breach Hits 5.6 Million Patients
Yale New Haven Health reported a data breach on March 8, 2025, affecting 5.56 million people. Hackers accessed a network server and copied patient data, including names, birthdates, contact info, race or ethnicity, and medical record numbers. No medical or financial data was exposed.

The attack briefly disrupted phone and internet services, but patient care and the Epic EMR system were not affected. Yale is working with law enforcement and has set up a support line at 1-855-549-2678.
Two class-action lawsuits have been filed, claiming basic security measures could have prevented the breach. This is the largest breach in Yale’s history and follows an earlier 2023 incident that influenced the system’s decision to abandon a hospital acquisition deal.
(Source: CT Insider)
Data breaches are hitting harder than ever. Check out 120 data breach stats that show how often they happen, what causes them, and how much they cost.
3. Episource Breach Exposes Data of 5.4 Million Patients
A ransomware attack on medical billing firm Episource compromised the personal and health information of over 5.4 million people. Discovered on February 6, 2025, the breach lasted from January 27 to February 6, allowing attackers to access and copy sensitive data.
Stolen information includes names, contact details, Social Security numbers, birthdates, insurance policy info, Medicaid/Medicare IDs, and medical data such as diagnoses and treatment records.

Episource, part of UnitedHealth Group, provides risk adjustment services to healthcare providers. The company has offered free identity protection and notified law enforcement. Sharp Healthcare confirmed the attack involved ransomware.
Security experts say this breach highlights growing threats from attacks on third-party vendors rather than hospitals directly, increasing risk across the healthcare supply chain.
(Source: Infosecurity Magazine )
4. Blue Shield of California Data Leak Impacts 4.7 Million
Blue Shield of California exposed the data of 4.7 million members to Google Ads due to a misconfigured Google Analytics setup used between April 2021 and January 2024. The breach was unintentional but allowed protected health information to reach Google, which may have used it for targeted advertising.

Exposed data included insurance plan types, ZIP codes, city, gender, family size, account IDs, member names, and health-related search queries. No Social Security numbers, financial data, or driver’s license details were leaked.
After identifying the issue, Blue Shield disabled the misconfiguration and reviewed all web tracking tools. The company is now notifying users who accessed its sites during the affected period. This incident highlights the privacy risks of using analytics tools without strict controls in healthcare environments. (Source: Malwarebytes)
Cybercrime isn’t slowing down — it’s accelerating fast. Take a look at 250+ cybercrime stats that break down the trends, costs, and global impact.
5. Lockton Companies Southeast Breach – U.S., February 2025
Lockton Companies’ Southeast Series division, a prominent employee benefits broker, discovered a significant data breach on February 5, 2025. The intrusion began on November 20, 2024, when attackers gained unauthorized access to a single employee computer and associated account. During a forensic review, Lockton confirmed the compromise of personally identifiable information for approximately 1,055,380 individuals.

Exposed data included:
- Full names
- Addresses
- Social Security numbers
- Dates of birth
- Health insurance details
- Medical and some financial information
The breach involved one account but affected multiple employee-benefit plans across dozens of employer groups served by Lockton’s Southeast division. Notifications began on March 7, 2025, and Lockton initiated reporting to state attorneys general, the U.S. Department of Health and Human Services, and regulatory agencies
Affected individuals were offered 24 months of identity protection, including credit monitoring and identity restoration via Experian IdentityWorks, with up to $1 million in insurance coverage. (Source: HIPAA Journal)
6. Allianz Life Salesforce Data Breach
On July 16, 2025, Allianz Life suffered a major data breach after ShinyHunters tricked employees into granting access to its Salesforce CRM system. Disclosed between August 13 and 19, the incident exposed the personal data of 1.1 million customers, including Social Security numbers, contact information, and financial identifiers. Attackers exfiltrated 2.8 million records through malicious Salesforce integrations, using advanced voice phishing and OAuth application abuse to bypass multi-factor authentication.

The breach formed part of a broader ShinyHunters campaign against global corporations and showed signs of collaboration with other extortion groups. While Allianz contained the intrusion within 24 hours and notified the FBI, the exposure of complete personal profiles created significant fraud and identity theft risks. Customers received 24 months of identity protection, and the company moved quickly to strengthen CRM security.
For CISOs, this incident highlights the vulnerability of cloud-based CRM platforms to social engineering. Priorities include stronger authentication beyond MFA, strict CRM access controls, employee training against vishing, and vendor security assessments for third-party integrations.
Phishing isn’t going anywhere — in fact, it’s getting worse. Check out 200+ phishing stats that show how these scams keep tricking people and businesses.
7. Community Health Center, CT (CHC) Network Intrusion – U.S., January 2025
In January 2025, Community Health Center, Inc.—a Middlesex County, Connecticut clinic network—announced a cyberattack that exposed data for 1,060,936 individuals. The breach began on October 14, 2024, and was detected on January 2, 2025.
Although contained within hours, the attacker retrieved sensitive patient data, such as names, contact details, dates of birth, Social Security numbers, medical record numbers, lab results, diagnoses, treatment information, insurance details, and COVID-19 testing/vaccine records for some.
No data was encrypted or destroyed, pointing to theft rather than disruption. CHC began notifying those affected by January 30, 2025, and offered 24 months of free identity protection and credit monitoring via IDX, alongside boosted system monitoring. The case stands out due to its speed—significant data theft happened in just a few hours—and the breadth of clinical, administrative, and demographic data accessed.
(Source:Cybersecurity News)
8. Frederick Health Ransomware Attack – U.S., January 2025
On January 27, 2025, Frederick Health in Maryland suffered a ransomware attack that caused system outages and patient diversions. By March, the breach was confirmed to have exposed data from 934,000 individuals.
Stolen details included names, Social Security numbers, driver’s license info, insurance data, medical record numbers, and clinical treatment information. The incident disrupted operations and raised privacy risks.

Frederick Health responded by offering credit monitoring and strengthening its cybersecurity measures. Despite these efforts, the event exposed how malicious actors continue to exploit system weaknesses and how organizations identified as vulnerable may be repeatedly targeted across different attack campaigns.
(Source:HIPAA Journal)
9. Medusind Breach Exposes Data of 360,934 Patients
Medical billing provider Medusind reported a cyberattack discovered on December 29, 2023, which compromised data from 360,934 individuals. Attackers accessed the company’s systems and stole a wide range of sensitive information.
Exposed data includes birthdates, contact details, medical history, prescription info, insurance claims, payment data, and government IDs such as Social Security and passport numbers. The exact data varied by individual.

Medusind, which supports over 6,000 healthcare providers, has offered affected patients two years of free identity protection. The company took its systems offline immediately and began working with cybersecurity experts.
(Source:Bitdefender)
10. Kelly Benefits (Kelly & Associates) Data Breach – U.S., December 2024 (Disclosed 2025)
Kelly & Associates Insurance Group (Kelly Benefits) reported a breach affecting nearly 264,000 individuals. The incident occurred between December 12 and 17, 2024, when hackers accessed and exfiltrated files containing names, birthdates, Social Security numbers, tax IDs, medical and insurance details, and financial account information.

Notifications are being sent on behalf of multiple affected clients, including CareFirst, Guardian Life, and Beam Benefits. While ransomware is suspected, no group has claimed responsibility. Kelly Benefits has not confirmed if a ransom was paid. The breach prompted renewed calls for stricter protocols across the healthcare industry, especially regarding third-party access. Analysts also noted the absence of standard tracking for data breaches reported in regional clearinghouses.
(Source: Security Week )
11. Numotion Email Breach Affects Customer Data
Between September 2 and November 18, 2024, unauthorized access occurred in several Numotion employee email accounts. While there’s no evidence of fraud, a review completed on January 22, 2025, found that some emails contained customer information.
The data may have included names, birthdates, product info, financial and health insurance details, and in some cases, Social Security numbers or driver’s license numbers.

Numotion mailed notifications to affected individuals and offered free identity theft protection for those whose SSNs were exposed. Customers are advised to monitor their accounts and credit reports. A support line is available at 866-450-2357. (Source: Numotion)
12. Serviceaide / Catholic Health Cloud Exposure – U.S., September–November 2024
Serviceaide, a California-based IT provider, reported that an Elasticsearch database it managed for Catholic Health was accidentally left publicly accessible between September 19 and November 5, 2024. The exposed data affects over 483,000 individuals.

While there’s no proof of exfiltration, the leak may have revealed names, SSNs, dates of birth, medical records, insurance details, clinical and prescription info, usernames, and passwords.
Serviceaide is notifying affected patients and offering 12 months of free credit monitoring and identity protection. (Source: Security Week)
13. Healthcare Cybersecurity Crisis: 275 Million Patient Records Exposed (2024–2025)
Between 2024 and 2025, the healthcare sector experienced over 700 data breaches, exposing more than 275 million patient records. This marked a 63.5 percent increase from 2023 and represented the largest healthcare data exposure in U.S. history. Threat actors such as RansomHub and ShinyHunters exploited widespread password vulnerabilities, making compromised credentials the primary attack vector. Since 2020, the American Hospital Association reports that over 590 million medical records have been compromised, meaning nearly every U.S. citizen has been affected, many multiple times.
The breaches followed familiar MITRE ATT&CK patterns, with spearphishing attachments and password spraying used for initial access, brute force attacks and stolen password stores for credential access, and ransomware deployments leading to data encryption and manipulation. These attacks disrupted patient care, created billions in financial losses, and eroded trust in healthcare’s digital infrastructure.
Healthcare remains vulnerable due to low cybersecurity investment, averaging 4 to 7 percent of IT budgets compared to 15 percent in financial services. Legacy systems, insecure medical devices, and third-party vendor risks further expand the attack surface. Compromised credentials accounted for 85 percent of successful breaches, with ransomware, supply chain compromises, and social engineering also playing major roles.
The incidents also intensified regulatory scrutiny. Updated HIPAA requirements now mandate multi-factor authentication for all electronic protected health information, stronger password management, audit trail enforcement, and a risk-based cybersecurity approach. To address these challenges, recommended strategies include HIPAA-compliant password managers, zero-trust data access, continuous authentication monitoring, targeted staff training, and resilience planning against ransomware.
For CISOs, the key takeaway is that patient safety and cybersecurity must operate together. Protecting clinical systems requires integrated threat intelligence, medical device vulnerability assessments, and incident response frameworks designed for environments where disruptions can directly impact lives. (FireCompass)
Major Healthcare Data Breaches in 2024
1. Change Healthcare Ransomware Breach – U.S., February 2024
In February 2024, Change Healthcare—a UnitedHealth subsidiary—suffered the largest healthcare data breach ever in the U.S. (affecting about 190 million people). A BlackCat/ALPHV affiliate entered through a Citrix portal lacking multi‑factor authentication, stole data, and deployed ransomware. This attack crippled claims processing and prescription services across the country.

UnitedHealth paid a $22 million ransom, but BlackCat didn’t restore the data and apparently scammed their affiliate. Subsequently, a separate group named RansomHub surfaced and leaked parts of the stolen information. Billions in loans were issued and weeks of Congressional hearings took place. CEO Witty acknowledged the ransom in testimony and cited security failures in their systems. (Source: Tech Monitor)
2. Kaiser Foundation Health Plan Tracking Pixel Breach – U.S., April 2024
In mid-April 2024, Kaiser Foundation Health Plan reported it had unintentionally exposed the personal data of up to 13.4 million individuals via tracking pixels from Google, Microsoft, and X embedded in its public sites and apps. These pixels sent visitor names, IP addresses, account login status, site navigation, and symptom-search details to third parties.

No external breach occurred, and Kaiser removed the flawed trackers. No critical identifiers like SSNs or financial credentials were involved, and no misuse has emerged yet. The incident prompted reports to HHS (April 12) and California regulators, sparked a lawsuit in June, and heightened industry focus on privacy risks tied to analytics tools in healthcare.
(Source: Reuters)
3. Ascension Health Black Basta Ransomware Attack – U.S., May 2024
In May 2024, Ascension, the second-largest hospital system in the United States, experienced a severe ransomware attack by the Black Basta group. The attack began via a malicious phishing email attachment that allowed attackers to gain initial access and subsequently move laterally to compromise seven critical servers.
As a result, operational systems across Ascension’s extensive network of 142 hospitals were severely disrupted, forcing clinicians to rely on paper documentation for nearly four weeks. Emergency services, including ambulance routing and elective medical procedures, were significantly impacted.

Initially, Ascension reported that only 500 patients were affected, but subsequent investigations revealed the scope was significantly broader, ultimately affecting 5,599,699 individuals. The compromised data encompassed patient names, addresses, birth dates, Social Security numbers, driver’s licenses, medical record numbers, test results, treatment dates, procedure codes, insurance claim details, and payment information.
Ascension began formal notifications to impacted individuals in December 2024, continuing into early 2025. The organization provided affected patients with 24 months of identity theft monitoring services and $1 million reimbursement insurance coverage. This ransomware incident underscored the significant operational and privacy risks posed to healthcare organizations by phishing attacks and highlighted the need for robust cybersecurity practices to prevent extensive data breaches. (Source: AP News )
4. HealthEquity SharePoint Vendor Breach – U.S., March 2024
In March 2024, HealthEquity, a financial firm specializing in managing health savings accounts (HSAs), disclosed a significant third-party data breach impacting approximately 4.3 million individuals. The breach occurred when an attacker gained unauthorized access to HealthEquity’s SharePoint cloud storage using stolen credentials belonging to a business partner. The compromised data included sensitive personal information such as names, addresses, Social Security numbers, health insurance details, prescription data, employee IDs, and partial payment card information.
HealthEquity confirmed that the breach did not involve their core banking and financial systems, and no evidence emerged indicating stolen funds or malicious activity within their primary operations. Following discovery on March 25, 2024, HealthEquity swiftly disabled compromised accounts, terminated unauthorized access, reset global passwords, and strengthened internal controls.
Security teams also conducted a full review of system logs and implemented stricter access protocols across partner accounts. The breach sparked broader discussions on gaps in cybersecurity regulations and the role of it professionals in maintaining defenses for financial entities operating in the healthcare sector.
Individual notifications began on August 9, 2024, offering affected users 24 months of credit monitoring and identity restoration services. Analysts noted that the cross industry average for breach detection time remains high, leaving systems exposed far longer than most organizations realize.
(Source: Wolf and Co)
5. Concentra / PJ&A Vendor Breach Fallout – U.S., January 2024
In January 2024, Concentra Health Services confirmed that approximately 3,998,162 of its patients were impacted by a substantial data breach originating from its transcription vendor, Perry Johnson & Associates (PJ&A). The breach occurred between March 27 and May 2, 2023, but Concentra received notification only in November 2023, prompting an extensive internal investigation.
The compromised data included highly sensitive personal and medical details, such as names, birth dates, addresses, Social Security numbers, medical record numbers, hospital account numbers, clinical notes, admission diagnoses, dates and times of service, laboratory results, medication information, and insurance data.

Patient notifications commenced in January 2024, continuing into February. In response, a class-action lawsuit was filed against Concentra, PJ&A, and Select Medical Holdings in early 2024, alleging negligence and inadequate data protection practices. The incident raised questions about how information stored by third-party vendors is monitored and secured across healthcare networks. It also highlighted persistent risks from automation tools used in medical transcription workflows and the absence of clear data compromises reporting procedures. Some critics cited internal issues at PJ&A that may have contributed to the delayed breach detection.
(Source: HIPAA Journal)
6. Centers for Medicare & Medicaid Services (CMS) MOVEit Breach – U.S., September 2024
In September 2024, CMS disclosed a breach affecting 3,112,815 Medicare beneficiaries caused by exploitation of the MOVEit Transfer vulnerability. The breach occurred through a compromised file-transfer server used by Wisconsin Physicians Service (WPS), a CMS contractor handling Medicare claims. Initially patched in May 2023, the breach went undetected until a forensic review in May 2024 confirmed data extraction.
Exposed data included names, Social Security numbers, taxpayer IDs, birth dates, addresses, Medicare Beneficiary Identifiers, hospital account numbers, and treatment dates. CMS began notifying affected individuals in July 2024, offering 12 months of complimentary credit monitoring through Experian and issuing new Medicare cards.
The delayed discovery highlighted significant concerns regarding timely detection and the security of third-party software used by federal healthcare programs, underscoring the risks of unsecured protected health information in outsourced systems. Critics pointed to breaches reported in similar contexts and a lack of accountability in tracking reported healthcare data breaches tied to federal contractors. The event also drew attention to how business email compromise attacks may create secondary access points within complex vendor ecosystems.
(Source: HIPAA Journal)
7. MediSecure Ransomware Attack – Australia, April 2024
In April 2024, Australian e-prescription provider MediSecure suffered a ransomware attack that compromised data from approximately 12.9 million individuals. The stolen data, totaling 6.5 terabytes, included names, birth dates, Medicare and concession card numbers, healthcare identifiers, prescription histories, and provider information. The breach affected records generated between March 2019 and November 2023.

Although MediSecure restored its systems by mid-May, it did not issue individual notifications, citing the scale and cost of identification. The incident drew national attention due to its size and followed other major breaches in Australia’s healthcare sector. MediSecure entered voluntary administration in June 2024 after losing its government contract and failing to secure financial support. Experts pointed to the need for stronger enforcement of accountability act requirements in digital health systems handling sensitive prescription data.
(Sources:New.com.au)
8. Acadian Ambulance Service Ransomware Attack – U.S., June 2024
In June 2024, Louisiana-based Acadian Ambulance Service was hit by the Daixin Team in a ransomware attack affecting around 2.9 million patients. The attackers accessed systems from June 19 to 21, stole sensitive files, and demanded $7 million. Acadian offered $173,000, which was rejected, and the data was later leaked online.
Stolen information included names, contact details, birth dates, Social Security numbers, dates of service, medical intake notes, and insurance data. Acadian reported the breach to the Department of Health and Human Services in August and began notifying individuals in November, offering free credit monitoring.
Emergency operations continued without disruption due to swift containment. Several class-action lawsuits followed. As of May 2025, Acadian had moved to dismiss the cases, citing lack of proven harm. The incident highlighted the growing threat ransomware poses to emergency medical providers and health insurance portability, especially when systems holding personal and billing data are compromised.
(Source:Databreach.com)
9. Sav-Rx Pharmacy Ransomware Attack – U.S., May 2024
In October 2023, Sav-Rx, a Nebraska-based pharmacy benefit manager, detected a network breach affecting about 2.8 million individuals. The issue was identified on October 8 and resolved the next day, but notification did not occur until April 30, 2024, following a lengthy investigation.
An unauthorized party accessed non-clinical systems and acquired files containing names, birth dates, contact details, Social Security numbers, insurance IDs, and addresses. No clinical or financial data was involved.

Sav-Rx stated that patient care and prescription services were not disrupted. The company reported the stolen data was destroyed and not spread further.
Security improvements included multi-factor authentication, network segmentation, and enhanced system hardening. Free credit monitoring was offered to affected individuals, helping to limit risk from phishing incidents that often follow data exposures.
(Source: Tech Target )
10. WebTPA Third-Party Administrator Breach – U.S., 2023–2024
WebTPA Employer Services, a Texas-based third-party administrator and subsidiary of GuideWell Mutual Holding Corporation, disclosed a data breach that affected more than 2.4 million individuals. The breach occurred between April 18 and April 23, 2023, but was not discovered until December 28, 2023, when suspicious activity was detected on its network.
The compromised data included names, contact details, dates of birth, dates of death, insurance information, and Social Security numbers. The specific data exposed varied by individual. Financial, credit card, and medical information were not involved.
WebTPA notified insurance partners on March 25, 2024, and began sending written notices to affected individuals in April. The company reported the breach to the U.S. Department of Health and Human Services on May 8, confirming that 2,429,175 individuals were impacted.
In response, WebTPA implemented additional network protections and is offering two years of free identity monitoring. Several lawsuits have been filed in the Northern District of Texas, and investigations are underway. Affected clients include Allied Pilots Association, Dean Health Plan, Gerber Life, The Hartford, and Transamerica Life Insurance Company. The delay in detection has raised concerns about data breach increased risks due to late response times in breach discovery.
(Source:Security Week )
11. Integris Health Patient Data Theft – U.S., November 2023 (Disclosed January 2024)
INTEGRIS Health disclosed a cyberattack in November 2023 affecting around 2.3 million patients. The breach led to direct extortion attempts, with hackers contacting patients and demanding payment. INTEGRIS updated its breach notice on February 6, 2024, after facing criticism over delayed and vague communication.

The organization reported the breach to HHS on January 26, 2024. Lawsuits soon followed, accusing INTEGRIS of negligence and failure to notify patients promptly. Critics also questioned whether more data was exposed than disclosed, due to dark web postings.
The breach added to a growing number of healthcare cyber incidents. In December 2023 alone, similar server breaches impacted more than 11 million individuals, underlining widespread vulnerabilities in the sector—including issues stemming from employee negligence.
(Source: PAU Box)
12. American Vision Partners (MMRG) Cyberattack – U.S., November 2023
Medical Management Resource Group (MMRG), operating as American Vision Partners, disclosed in February 2024 that a cyberattack impacted 2,350,236 patients across affiliated ophthalmology practices. Hackers breached the Arizona-based provider’s systems sometime in 2023, accessing data such as eye exam results, clinical notes, personal identifiers, and Social Security numbers. The breach affected patients in multiple states and clinics connected through shared IT infrastructure. This event demonstrated how attackers can compromise numerous medical entities at once by targeting centralized service providers with compromised credentials.(Source: HIPAA Journal)
13. Summit Pathology Ransomware Attack – U.S., April 2024 (Disclosed October 2024)
Summit Pathology, a Colorado laboratory services provider, suffered a ransomware attack in April 2024 that exposed the data of 1,813,538 individuals. The Medusa ransomware group infiltrated the network after an employee opened a malicious email attachment.

Stolen data included pathology test results, personal identifiers, and likely some billing records. Although Summit reported that none of the data had appeared online, the outcome suggests a ransom was paid. The incident underscored how lab services—holding sensitive diagnostic data—remain high-value targets for cyber criminals. (Source: HIPAA Journal)
14. OnePoint Patient Care Ransomware Attack – U.S., 2024
On October 14, 2024, Arizona-based OnePoint Patient Care disclosed a data breach impacting more than 795,000 individuals. The company, a major hospice pharmacy provider, detected suspicious activity on its network on August 8, 2024. An investigation confirmed that unauthorized access occurred between August 6 and August 8, during which attackers obtained files containing protected health information (PHI).
Exposed data included names, addresses, Social Security numbers, diagnoses, and medication histories. The INC Ransom group claimed responsibility and posted the stolen data on its dark web site after OnePoint refused to pay.
The company posted a breach notice and offered free credit monitoring services. It also stated that additional safeguards have been implemented to strengthen its data protection practices.
According to HHS filings, over 795,000 individuals were affected. OnePoint serves more than 40,000 patients daily through over 100 locations nationwide and maintains a network of 55,000 contracted pharmacies. The breach emphasized the increasing cybersecurity threats facing hospice and healthcare service providers, especially in other sectors that manage sensitive medical records.
(Source: HIPAA Times)
15. Synnovis NHS Pathology Disruption – UK, June 2024
On June 3, 2024, Synnovis, a pathology provider linked to SYNLAB and several NHS trusts—suffered a ransomware attack that disrupted diagnostics across southeast London.
The attack affected Guy’s and St Thomas’, King’s College Hospital, South London and Maudsley, Lewisham and Greenwich, Oxleas, Bromley Healthcare, and local primary care in six boroughs. Specialist testing for other hospitals was also impacted.

Blood testing delays led to canceled appointments and surgeries. Outpatient and community care continued mostly as normal. Patients were told to attend scheduled appointments unless contacted.
Emergency services remained available. NHS 111 and 999 operated without disruption.
The breach exposed risks in digital pathology and highlighted the growing threat of ransomware to U.K. healthcare infrastructure. Affected organizations have since reviewed contingency protocols to reduce future service disruptions.
(Sources: NHS Uk, Digital Health)
Major Healthcare Data Breaches in 2023
1. HCA Healthcare Breach – July 2023
On July 10, 2023, HCA Healthcare reported a data breach involving patient information that appeared on an online forum. The exposed data came from an external storage system used solely to automate email formatting. The compromised details included patient names, addresses (city, state, zip), email addresses, phone numbers, dates of birth, gender, and information about appointment dates and locations.
The incident did not involve clinical data such as diagnoses or treatments, nor did it include financial information, passwords, driver’s license numbers, or Social Security numbers. HCA confirmed there was no disruption to patient care or services and stated that the breach would not have a material effect on its operations or financial results.

In response, the company disabled access to the affected storage system and brought in forensic and threat intelligence experts. The investigation found no signs of malicious activity within HCA’s internal systems. Law enforcement has been notified, and the company will notify affected individuals and offer credit monitoring and identity protection services where appropriate.
HCA Healthcare operates 180 hospitals and 2,300 ambulatory care sites across 20 U.S. states and the UK. The organization handles over 37 million patient interactions each year and conducts large-scale clinical research.
(Sources: Investor.HCAHealthcare.com)
2. Perry Johnson & Associates (PJ&A) Breach – March–May 2023
The PJ&A data breach is now the largest U.S. healthcare breach of 2023, affecting over 14 million patients. Hackers accessed the medical transcription firm’s systems from March 27 to May 2, 2023, and stole data including names, birthdates, addresses, medical record numbers, diagnoses, treatment dates, Social Security numbers, and insurance details.
PJ&A’s clients, including Cook County Health, Northwell Health, and Concentra Health Services, have confirmed patient impacts. Concentra recently reported nearly 4 million affected patients, raising the total significantly.
This breach surpasses the HCA Healthcare breach, which exposed over 11 million records. Another recent disclosure linked to HealthEC involved 4.5 million patients from 18 providers.
(Source:SCWorld.com)
3. MCNA Dental Ransomware Attack – Early 2023
MCNA Dental, the largest U.S. dental insurer for Medicaid and CHIP programs, suffered a ransomware attack that exposed sensitive data belonging to 8.9 million patients. Hackers accessed the company’s systems between February 26 and March 7, 2023, stealing names, contact details, Social Security numbers, driver’s license numbers, Medicaid-Medicare IDs, treatment details, insurance data, and claims information.

The LockBit ransomware group claimed responsibility after MCNA reportedly refused to pay a $10 million ransom. The stolen 700GB of data was posted online on April 7 and is now for sale on the dark web.
MCNA began notifying affected individuals and is offering one year of identity theft protection. This breach became 2023’s largest healthcare cyberattack at the time.
Other ransomware attacks reported around the same time include Enzo Biochem (2.47 million affected), Harvard Pilgrim Health Care (2.55 million), and the 2021 attack on St. Margaret’s Health in Illinois, which contributed to the hospital’s closure in 2023 due to ongoing financial strain. (Source: Sangfor)
4. Welltok MOVEit Breach – May 2023
The MOVEit software breach in May 2023 impacted healthcare SaaS company Welltok, exposing data from 8.5 million individuals. Despite applying patches, hackers exploited the flaw to access names, contact details, some Social Security numbers, and insurance information tied to 20 healthcare groups, including Sutter Health and several Blue Cross plans.
Warren General Hospital reported a September 2023 breach affecting nearly 169,000 people. Hackers accessed personal, financial, and medical data over a nine-day period.
Mission Community Hospital also disclosed a breach from May 2023, with the investigation concluding in November. Exposed data included personal identifiers, medical records, and financial information. (Source: Tech Target)
5. PharMerica Ransomware Attack – March 2023
PharMerica and its parent company, BrightSpring Health Services, detected suspicious activity on their network on March 14, 2023. An investigation revealed that an unauthorized party accessed PharMerica’s systems between March 12 and 13, potentially obtaining personal and limited medical data. This included names, birthdates, Social Security numbers, medication lists, and health insurance information.
Though no fraud has been reported, PharMerica is notifying affected individuals and offering free identity protection and credit monitoring. The company recommends monitoring financial and benefit accounts for unusual activity and reporting any fraud to the proper authorities.
PharMerica has taken steps to strengthen its security and prevent future incidents. For further assistance, individuals can call the support line at (866) 347-4281 during weekday business hours. (Source:Pharmerica.com)
7. HealthEC Network Intrusion – July 2023
HealthEC, a population health management company, reported a data breach that affected nearly 4.5 million individuals. Between July 14 and July 23, 2023, an unauthorized actor accessed and stole files from its systems containing sensitive data provided by business partners.

The compromised information included names, birthdates, addresses, Social Security numbers, taxpayer IDs, medical details, insurance data, and billing information. HealthEC completed its review of the data in late October and began notifying affected customers shortly after.
The breach impacted numerous partners, including TennCare, Corewell Health, HonorHealth, and Alliance for Integrated Care of New York. Notification letters were sent starting December 22, advising individuals to watch for signs of identity theft and monitor credit activity.
(Source: Security Week)
8. Colorado HCPF MOVEit Breach – Mid-2023
The Colorado Department of Health Care Policy & Financing (HCPF) confirmed a data breach affecting over 4 million individuals due to the MOVEit file transfer vulnerability disclosed in May 2023 (CVE-2023-34362). The breach originated from HCPF’s technology partner, IBM, which used MOVEit to transfer HCPF files. The unauthorized access occurred around May 28, 2023.
HCPF’s internal systems were not compromised, but the accessed files contained sensitive information, including names, Social Security numbers, Medicaid and Medicare IDs, birthdates, addresses, income and demographic data, diagnoses, medications, lab results, and insurance information. Financial data like credit card numbers was not exposed.
The agency began notifying 4,091,794 impacted individuals on August 11 and is offering two years of free credit monitoring and identity restoration services through Experian. Victims are encouraged to monitor accounts, report suspicious activity, and consider placing credit freezes.
The breach at IBM is part of a wider MOVEit-related security incident that has affected numerous organizations, including other Colorado state agencies, the U.S. Department of Energy, and several global companies.
(Source: CPO Magazine)
9. Regal Medical Group Ransomware Attack – December 2022 / Reported 2023
Regal Medical Group, an affiliate of Heritage Provider Network in San Bernardino, California, suffered a ransomware attack in early December 2022 that affected nearly 3.4 million individuals. The attack began around December 1, when threat actors accessed Regal’s email servers, exfiltrated data, and later deployed ransomware to encrypt files.
The compromised data included names, contact details, dates of birth, Social Security numbers, diagnosis and treatment information, lab results, prescription records, radiology reports, and health plan member numbers. Patients of Lakeside Medical Organization, ADOC Medical Group, and Greater Covina Medical were also affected.
Regal has implemented added security measures, including enhanced email spam filtering, and is offering 12 months of free credit monitoring through Norton LifeLock. The breach has been reported to the Department of Health and Human Services, marking it as the largest U.S. healthcare data breach reported in 2022.
Multiple class-action lawsuits have since been filed, alleging failures in protecting sensitive patient information and violations of HIPAA and other privacy laws. (Source: HIPAA Journal)
10. Cerebral PHI Exposure – Disclosed 2023
Cerebral, a mental health telehealth provider, exposed the data of over 3.1 million patients to platforms like Google, Meta, and TikTok through tracking pixels used since October 2019. The shared data included names, contact info, IP addresses, insurance details, treatment info, and mental health assessment responses.

After discovering the issue in January 2023, Cerebral removed the tracking tools and updated its security practices. The breach is under investigation by the HHS Office for Civil Rights for potential HIPAA violations. U.S. senators have called for more transparency, and the FTC is also reviewing the incident.
(Source: Compliance Group )
11. NationsBenefits GoAnywhere Breach – Early 2023
NationsBenefits, a healthcare benefits provider, confirmed it was impacted by the January 2023 ransomware attack on Fortra’s GoAnywhere file-transfer tool. Hackers exploited a zero-day vulnerability, stealing data from dozens of organizations. In a filing with New Hampshire’s attorney general, NationsBenefits reported over 7,100 state residents had personal data stolen. The company did not disclose the total number of affected individuals nationwide, despite serving over 20 million members across the U.S.
The Clop ransomware group claimed responsibility for the mass attack, which also affected companies like Community Health Systems, Procter & Gamble, and the City of Toronto. NationsBenefits acknowledged it only learned about the vulnerability after contacting Fortra directly. Fortra has been criticized for its delayed disclosure and inconsistent communication with affected customers. (Source: Tech Crunch)
12. ESO Solutions Ransomware Attack – 2023
ESO Solutions, a healthcare software provider, experienced a ransomware attack on September 28, 2023, affecting 2.7 million individuals. The attackers accessed and encrypted ESO’s systems, leading to the exposure of personal and protected health information (PHI) belonging to patients of its hospital, EMS, and government agency clients.
Exposed data included names, birthdates, phone numbers, medical record numbers, injury and treatment details, and in some cases, Social Security numbers. ESO took affected systems offline, brought in forensic experts, and notified federal law enforcement. By October 23, it confirmed PHI had been exfiltrated.
Notification letters were mailed beginning December 12, and free credit monitoring and identity protection were offered. While there’s no evidence of misuse so far, the breach highlights the risks of storing massive patient datasets with third-party vendors. The incident adds to a growing list of large-scale 2023 breaches involving business associates, including those linked to the MOVEit software vulnerabilities.
(Source: The HIPAA E Tool)
13. Harvard Pilgrim Health Care Breach – March 2023
Harvard Pilgrim Health Care has updated the number of individuals affected by its April 2023 ransomware attack to nearly 2.9 million. The breach, first disclosed last spring, was carried out by an unidentified ransomware group that infiltrated the company’s systems from March 28 to April 17, 2023. The attack disrupted services for several days.

The latest breach notification submitted to regulators in Maine shows the total impacted population has risen to 2,860,795—about 12% higher than initial estimates. The compromised data may include personal and protected health information for current and former subscribers, dependents, and healthcare providers.
Harvard Pilgrim, which operates primarily in Massachusetts, Maine, New Hampshire, and Connecticut, is part of Point32Health, a nonprofit formed by the 2021 merger of Harvard Pilgrim and Tufts Health Plan. Point32Health serves over 2.2 million members, making it the second-largest insurer in Massachusetts. (Source: The Record )
14. Enzo Clinical Labs Ransomware Attack – April 2023
In April 2023, hackers breached Enzo Biochem’s systems, stealing clinical test data from 2.47 million people and 600,000 Social Security numbers. Enzo disclosed the incident in a May SEC filing, noting operational disruptions and expected ongoing costs.
The company, which provides diagnostic services, is subject to HIPAA and plans to notify affected individuals and regulators. At least one class-action lawsuit has been filed, with more expected. The breach highlights the financial and legal risks of weak cybersecurity in healthcare.
(Source: The HIPAA E Tool)
15. Tampa General Hospital Breach – May 2023
In May 2023, Tampa General Hospital was breached by hackers who accessed patient data over nearly three weeks. Detected on May 31, the breach exposed names, contact details, birthdates, Social Security numbers, insurance data, and medical record numbers for over 2.4 million individuals.
The hospital faced backlash for delaying notification until July 19. A class-action lawsuit followed, claiming the breach was preventable. Tampa General launched an investigation with third-party experts and offered free credit monitoring to affected individuals. The FBI is also involved in the ongoing investigation.
(Source: Twingate)
16. PurFoods (Mom’s Meals) Breach – Early 2023
PurFoods, the parent company of Mom’s Meals, experienced a ransomware attack earlier in 2023 that may have compromised the personal data of approximately 1.2 million people. The breach, which occurred between January 16 and February 22, involved encrypted files and signs of potential data exfiltration, although no misuse of data has been confirmed.

Those affected include customers, employees, and contractors. Exposed data may include birth dates, driver’s license or state ID numbers, financial and payment information, Medicare/Medicaid IDs, medical records, treatment and diagnosis details, health insurance info, and meal-related data. Fewer than 1% of affected records included Social Security numbers.
PurFoods began mailing notification letters on August 25 and is offering free credit monitoring and identity restoration services. A dedicated helpline is available at (866) 676-4045. The company confirmed the incident was unrelated to the MOVEit breaches. Several law firms are already investigating potential legal action.
(Source: Threat Down)
Cybersecurity never stands still. Take a look at 200+ cybersecurity stats that capture the latest trends, risks, and defenses shaping today’s digital world.
17. PH Tech MOVEit Breach – Mid-2023
On May 30, 2023, hackers exploited a vulnerability in the MOVEit file transfer software, breaching PH Tech and compromising the protected health information (PHI) of approximately 1.75 million health plan members in Oregon. PH Tech, a business associate serving community health plans like Health Share Oregon, confirmed the breach on June 16.
The stolen data included names, birthdates, Social Security numbers, member and plan IDs, diagnosis and procedure codes, email addresses, and claims information. The incident has triggered multiple class action lawsuits—Ballard v. Performance Health Technology and Malo v. Performance Health Technology—filed in Oregon’s U.S. District Court. The lawsuits accuse PH Tech of negligence, failing to meet HIPAA and FTC standards, and violating Oregon’s Unfair Trade Practices Act.
Though the flaw was in MOVEit software, PH Tech remains accountable for its security practices. Plaintiffs claim the breach puts their medical identity at risk and seek over $5 million in damages. PH Tech is now facing a HIPAA investigation and is expected to tighten its data security measures. ( Source: The HIPAA E Tool)
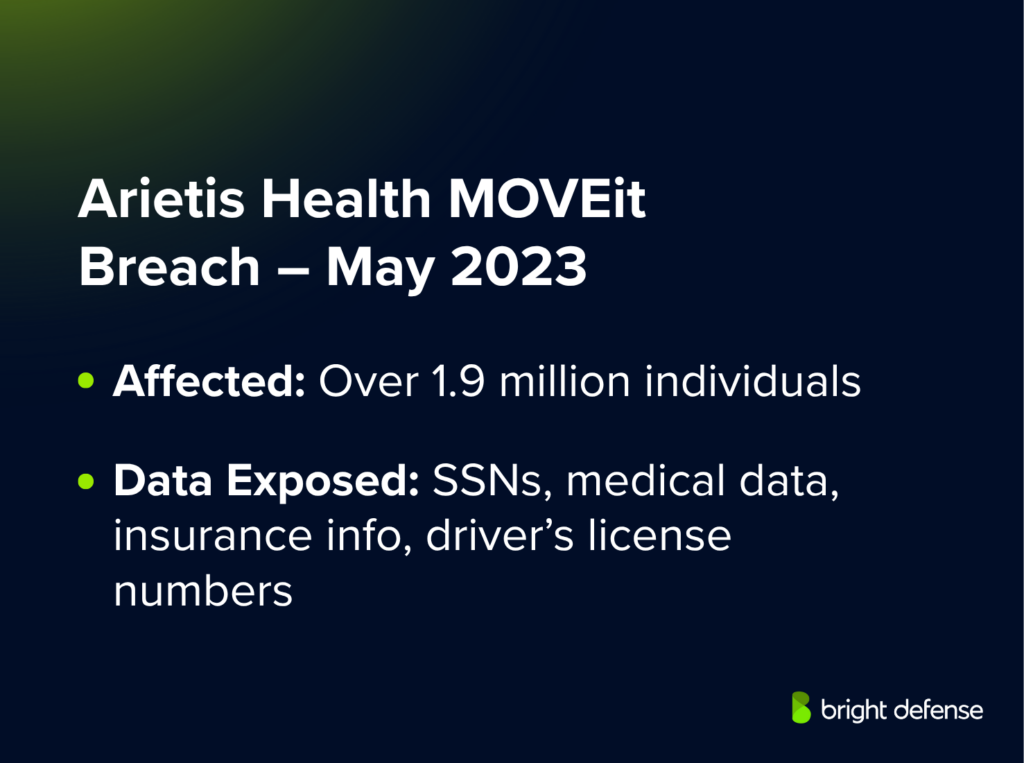
18. Arietis Health MOVEit Breach – 2023
Arietis Health agreed to a $2.8 million settlement to resolve a class action lawsuit over a May 2023 data breach tied to the MOVEit file transfer platform. The breach affected over 1.9 million individuals, exposing Social Security numbers, medical data, insurance details, driver’s license numbers, and more.
Eligible individuals can claim:
- Up to $5,000 in out-of-pocket loss reimbursement (with documentation)
- Up to 4 hours of lost time at $25/hour
- 4 years of medical and credit monitoring
The deadline to file a claim is April 3, 2025 at ArietisDataSettlement.com. Benefits will be distributed after final court approval and resolution of any appeals. The breach affected data tied to at least 54 healthcare providers through Arietis’ billing services for NorthStar Anesthesia. (Source: Classaction.org)
19. Geisinger Data Breach Impacts 1.2 Million Patients
Geisinger Health reported a breach involving a former Nuance Communications employee who accessed patient data two days after termination. The incident, discovered in late November 2023, affected over 1.2 million individuals.
The data accessed may include names, dates of birth, addresses, medical record numbers, phone numbers, facility names, and admission or discharge codes. Social Security numbers, insurance, and financial information were not involved.
Nuance, a Microsoft subsidiary, disabled access and contacted law enforcement. The former employee has been arrested and is facing federal charges. Patient notifications were delayed at law enforcement’s request. The breach adds to rising cybersecurity concerns in healthcare, with over 134 million people affected by large-scale breaches in 2023.
(Source: Healthcare Dive )
20. Thai Army Sergeant Identified in Data Breach of 55 Million Citizens
Authorities in Thailand have identified an army sergeant as the alleged hacker behind the massive data breach involving the personal information of 55 million Thais. The hacker, known online as “9Near,” obtained the data from the Mor Prom app, originally developed by the Ministry of Public Health for COVID-19 vaccination services.

The sergeant’s wife, a nurse, reportedly had access to the system and is also being questioned. The hacker had posted on BreachForums offering the data for sale and made threats to release the full dataset unless contacted by the targeted agency.
The leaked data included:
- Full names
- ID card numbers
- Birthdates
- Phone numbers
- Home addresses
Authorities blocked the website 9near.org and issued an arrest warrant. The Cyber Crime Investigation Bureau charged the suspect with inserting false information into a computer system. The suspect’s military unit is cooperating with law enforcement.
The breach triggered calls for stronger data protection policies, especially concerning access by third-party personnel in public health infrastructure. (Source: Bangkok Post)
Healthcare Data Breaches FAQs
From 2013 to 2023, 4,994 breaches of unsecured PHI affecting 500+ individuals were reported to HHS, which works out to about 454 large breaches per year on average
Those 2013–2023 breach reports impacted over 461.7 million individuals, and a cleaned analytic dataset in the same study counted 4,186 breaches impacting over 387.7 million individuals
In the 2013–2023 HHS breach-portal dataset analyzed in a peer-reviewed study, 100% of breaches involved personal data, 86% involved health data, and 21.9% involved financial information
Verizon’s 2025 DBIR Healthcare Snapshot reports 1,710 healthcare incidents and 1,542 with confirmed data disclosure, with breaches attributed to external actors 67%, internal actors 30%, and partners 4%, and the most-cited compromised data types listed as medical 45% and personal 40%
HHS reported that the Change Healthcare incident impacted approximately 192.7 million individuals as of July 31, 2025, and Reuters reported the same figure from the HHS listing
Start with the steps on IdentityTheft.gov/databreach, then change passwords for the affected accounts, turn on multi-factor authentication where available, and monitor accounts for misuse
Yes, when the exposed data can support identity fraud, a free credit freeze can make it harder for someone to open new accounts in your name
HIPAA’s Breach Notification Rule requires notice to affected individuals without unreasonable delay and no later than 60 days after discovery of a breach of unsecured protected health information
The largest reported U.S. healthcare breach is the Change Healthcare cyberattack, which HHS said impacted about 192.7 million individuals.
This claim usually means human error plays a major role, such as clicking phishing links, weak password practices, misdelivery of data, or misconfigurations, but reputable datasets do not treat 80% as a universal constant.
A common answer is phishing email, because CISA states that more than 90% of successful cyber-attacks start with a phishing email.
This claim usually means human error is involved as a contributing factor, and it appears in sources such as IBM-related reporting and Mimecast’s human-risk research, while Verizon’s DBIR executive summary uses a lower benchmark of about 60% of breaches involving the human element.
Get In Touch



