What is IoT Penetration Testing?
The growth of Internet of Things (IoT) devices has brought new entry points for attackers. Many of these systems, such as medical wearables, factory controllers, and connected vehicles, operate without strict access controls or regular software updates.
IoT penetration testing focuses on finding weak spots in how these devices communicate, store data, and interact with the broader network. It helps reveal what can go wrong before someone else tries to exploit it.
In this blog, we’ll explain what IoT penetration testing involves, why it matters, and the main types of tests used to assess device and network security.
Let’s jump right in!
What is IoT Penetration Testing?
IoT penetration testing is a security assessment that simulates real-world attacks on Internet of Things devices and their supporting infrastructure. The goal is to find weak points that could allow unauthorized access, data theft, or control of the device.
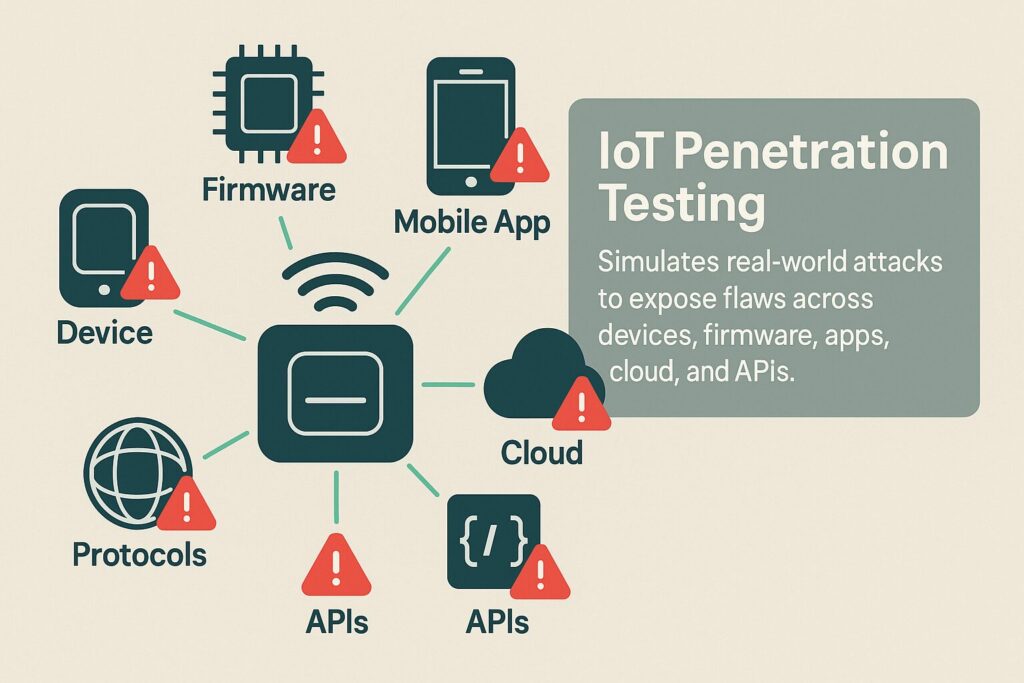
Unlike standard penetration tests, IoT testing covers a wider range of components. These include the physical device, embedded firmware, mobile apps, cloud services, communication protocols, and APIs. Each of these parts can expose unique risks depending on how they are built and connected.
Why Should You Perform an IoT Penetration Test?
IoT devices often operate with limited security controls, making them attractive targets for attackers. Performing an IoT penetration test helps expose issues that may not appear in traditional audits or automated scans.
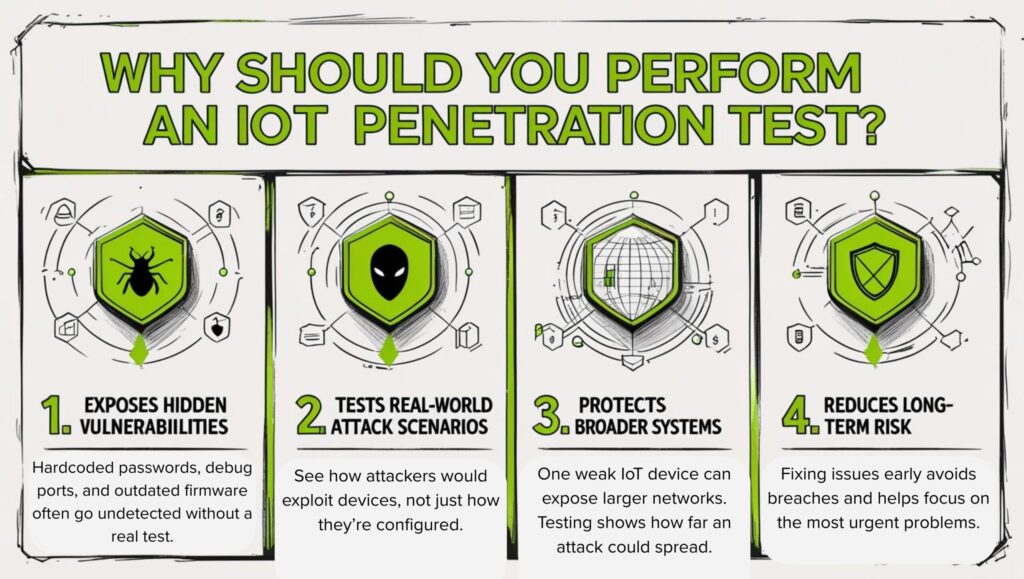
Here are the following reasons you must perform an IoT pen test:
- Exposes Hidden Vulnerabilities: Standard reviews often miss flaws like hardcoded passwords, exposed debug ports, or outdated firmware. A penetration test helps find these weak spots before attackers do.
- Tests Real-World Attack Scenarios: Penetration testing simulates how an attacker would actually try to exploit a device, offering insights beyond basic configuration checks.
- Protects Broader Systems: A single IoT device can serve as an entry point to more critical systems. Testing reveals how one compromise could spread across your environment.
- Reduces Long-Term Risk: Fixing security issues early can prevent data breaches and service outages. It also helps teams focus on problems that pose the most immediate threats.
What are the Threats in IoT Devices According to OWASP?
The OWASP Top 10 for IoT highlights critical security risks found in Internet of Things (IoT) devices. These threats are especially relevant for manufacturers, developers, and security teams managing smart devices. Below is an overview of each category:
1. Weak, Guessable, or Hardcoded Passwords
Many IoT devices ship with default credentials or hardcoded passwords. Attackers can gain unauthorized access if these are not changed.
Examples:
- Default admin/admin logins
- Unchangeable root passwords
2. Insecure Network Services
IoT devices often run unnecessary or vulnerable network services, which can be exploited for remote access or denial-of-service attacks.
Examples:
- Open telnet or FTP ports
- Unsecured APIs
3. Insecure Ecosystem Interfaces
Interfaces such as web apps, mobile apps, and cloud APIs often lack proper authentication, encryption, or input validation.
Examples:
- Poorly secured REST APIs
- Mobile apps sending credentials in plaintext
4. Lack of Secure Update Mechanism
Devices that do not support secure firmware updates remain exposed to known vulnerabilities.
Examples:
- No update capability
- Unauthenticated update delivery
- Unencrypted update files
5. Use of Insecure or Outdated Components
IoT firmware often contains libraries or modules with known vulnerabilities, which attackers can exploit.
Examples:
- Outdated OpenSSL versions
- Deprecated operating systems
6. Insufficient Privacy Protection
Sensitive user data is collected and stored insecurely or without proper consent, increasing the risk of data exposure.
Examples:
- Location data stored unencrypted
- Unclear data retention policies
7. Insecure Data Transfer and Storage
IoT systems often fail to protect data at rest or in transit, which exposes it to interception and theft.
Examples:
- Lack of TLS
- Unencrypted local data logs
8. Lack of Device Management
Devices without proper tools for asset management, monitoring, or security oversight are hard to secure once deployed.
Examples:
- No remote lockdown or wipe
- Inability to inventory devices
9. Insecure Default Settings
Devices often ship with insecure configurations, which users rarely change.
Examples:
- Disabled firewalls
- Enabled debug ports in production
10. Lack of Physical Hardening
Many devices are physically accessible, and attackers can extract sensitive data or firmware using ports like UART or JTAG.
Examples:
- Exposed debug interfaces
- Removable storage containing passwords
Types of IoT Security Testing
Securing IoT systems requires targeted testing methods that address both software and hardware vulnerabilities. Since these devices operate in complex environments, testing must evaluate their resilience from multiple angles. The three primary types of IoT security testing are outlined below.
1. IoT Penetration Testing
This method tests how an attacker might exploit weaknesses in an IoT system. It focuses on evaluating both digital and physical attack vectors through controlled, real-world exploitation attempts.
Key Areas Tested:
- Network protocols (e.g., MQTT, CoAP)
- Web interfaces, APIs, and mobile apps
- Device authentication and encryption
- Communication between IoT device and backend
Approach:
Security professionals mimic the behavior of threat actors to reveal vulnerabilities such as:
- Open ports
- Insecure credentials
- Weak access controls
- Cross-site scripting or buffer overflows
Outcome:
This helps expose exploitable flaws before real attackers do and informs remediation priorities based on real risk levels.
2. Firmware Examination
Firmware examination testing inspects the software embedded in IoT devices to uncover security issues such as hardcoded secrets, outdated libraries, and unsafe configurations.
Key Methods:
- Static analysis to scan source code or binaries for vulnerabilities
- Dynamic analysis to observe how the firmware behaves in a simulated or live environment
- Reverse engineering when source code is unavailable
Common Findings:
- Hardcoded credentials or cryptographic keys
- Hidden debug features or test scripts
- Use of insecure libraries
- Configuration files that leak sensitive info
Outcome:
Firmware examination provides insight into internal logic flaws and unsafe coding practices, especially in closed-source devices.
3. Threat Simulation
This evaluates how well an IoT ecosystem can resist specific threat scenarios based on attacker goals and methods. Unlike general pen testing, this method follows predefined attacker models and tactics.
Simulation Types:
- Man-in-the-middle (MitM) attacks
- Replay or injection attacks
- Physical tampering or sensor spoofing
- Malware infection and propagation
Tools Used:
- Custom scripts to emulate threat actions
- Emulated environments to observe device behavior
- Packet crafting tools to manipulate communication flows
Outcome:
Threat simulation reveals how devices respond under pressure and shows whether alerts, fail-safes, or defenses activate as intended.
How to Perform an IoT Penetration Test
Testing IoT systems requires a thorough approach that includes both software and hardware analysis. The process below outlines each phase of an IoT pen test, from initial discovery to final reporting.
Step 1: Reconnaissance and Asset Mapping
An IoT pen test starts with mapping the environment. This involves identifying the device’s hardware specifications, physical interfaces such as USB, UART, or JTAG, and any connected systems like cloud platforms, mobile applications, and backend APIs. Analyzing network traffic helps reveal which communication protocols the device uses, such as MQTT, HTTP, or Bluetooth. Tools like Wireshark and Nmap are often used to gather this initial information.
Step 2: Attack Surface Analysis
After discovery, the next phase focuses on identifying possible entry points. This includes examining physical access paths, open network ports, exposed services, firmware update methods, and available APIs. The goal is to find insecure configurations, unnecessary services, or weak authentication mechanisms that could give an attacker a foothold.
Step 3: Firmware and Software Testing
Firmware testing involves extracting and analyzing the code running on the IoT device. This can be done using hardware access or by retrieving firmware from over-the-air updates. Static analysis is used to look for hardcoded credentials, embedded keys, or debug functions, while dynamic analysis allows observation of how the firmware behaves when running. Reverse engineering tools like Binwalk and Ghidra help uncover hidden issues in the binary code.
Step 4: Communication and Protocol Testing
This phase focuses on how data moves between the device and other systems. The tester evaluates whether data in transit is encrypted, if messages can be spoofed or replayed, and whether proper session handling is enforced. Packet interception and manipulation tools simulate attacks to see how the system responds to tampered or intercepted data.
Step 5: Web and Mobile App Testing
Applications connected to the device—such as mobile apps or web interfaces—are tested for weaknesses. This includes checking if the mobile app stores data insecurely, if it communicates with APIs without proper authentication, or if web-based controls are vulnerable to common attacks like cross-site scripting or broken access control. These components are often soft targets in IoT ecosystems.
Step 6: Exploitation and Reporting
In the final stage, the tester attempts to exploit the identified vulnerabilities under controlled conditions. Examples include gaining unauthorized access, manipulating device functions, or causing a service to crash. A detailed report is then created to summarize the findings. It includes descriptions of each issue, impact assessments, proof-of-concept steps, and practical remediation advice.
What are Some of the Commonly Used IoT Penetration Testing Tools?
Here’s a breakdown of some commonly used tools in IoT penetration testing. These tools help examine different layers of the IoT ecosystem—from network traffic to firmware analysis and hardware probing.
- Nmap: Scans the device for open ports, running services, and operating system fingerprints. Helps define the device’s exposed surface.
- Wireshark: Captures and analyzes network traffic between the IoT device and other systems. Useful for spotting unencrypted data and unexpected communication.
- Binwalk: Extracts and analyzes firmware images. Reveals file systems, configuration files, or embedded scripts inside firmware.
- Ghidra: A reverse engineering tool for inspecting binary code. Helps uncover hidden logic flaws or hardcoded secrets.
- Burp Suite: Intercepts and tests web interfaces and APIs. Effective for finding vulnerabilities in mobile or web control systems tied to the device.
- Scapy: Allows custom packet creation and manipulation. Used to simulate attacks on communication protocols and observe device responses.
- Shodan: Searches for internet-exposed IoT devices. Highlights devices with open ports or known vulnerabilities across the web.
- MobSF (Mobile Security Framework): Analyzes Android and iOS mobile apps for weak storage, hardcoded keys, and insecure network calls.
- Firmware-Mod-Kit: Helps modify and repack firmware. Useful for testing how a device handles altered firmware payloads.
- JTAGulator / Bus Pirate: Hardware tools for probing physical debug ports. Enable memory extraction or direct command input through hardware interfaces.
How Much Does IoT Penetration Testing Cost?
IoT penetration testing typically costs between $5,000 and $150,000. A simple test on one device might cost around $5,000 to $15,000. Testing multiple devices or a smart home setup can run $15,000 to $40,000. For large environments like industrial systems or healthcare IoT, the cost often exceeds $40,000.
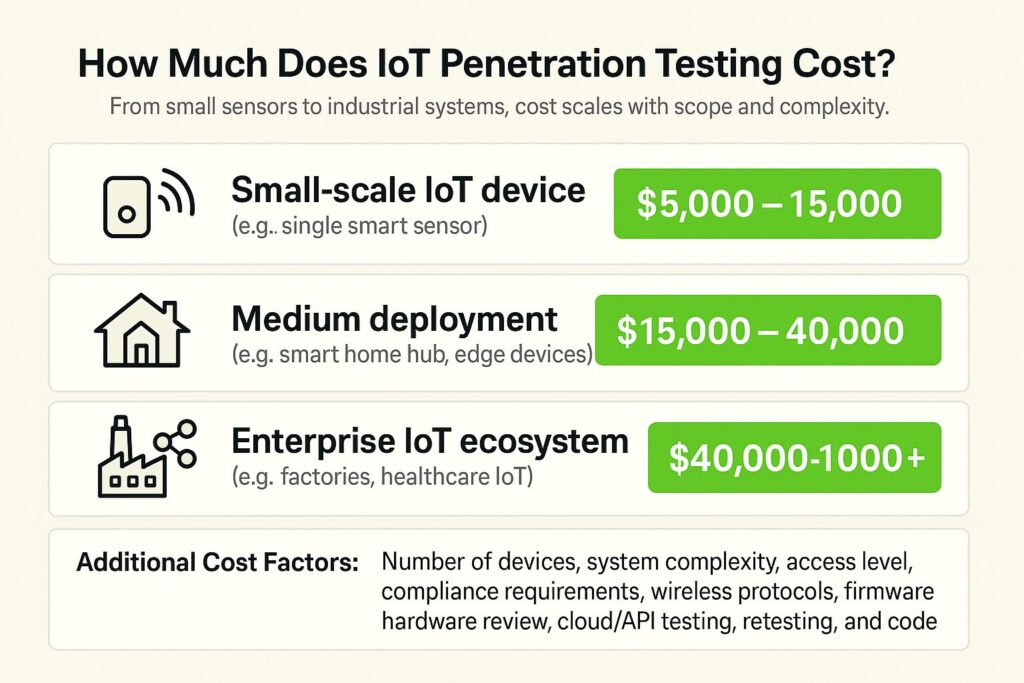
| Scope | Estimated Cost (USD) |
| Small-scale IoT device (e.g., a single smart sensor) | $5,000 – $15,000 |
| Medium deployment (e.g., smart home hub, edge devices) | $15,000 – $40,000 |
| Enterprise IoT ecosystem (smart factories, healthcare IoT) | $40,000 – $150,000+ |
Factors that drive the price include the number of devices, system complexity, whether testers get full access or not, and any required compliance checks. The test usually covers wireless protocols, firmware, hardware ports, cloud APIs, and connected apps. Extra services like retesting or code review increase the price.
How Can Bright Defense Help You With IoT Penetration Tests?
Bright Defense tests IoT systems for real-world vulnerabilities across hardware, firmware, cloud APIs, wireless protocols, and connected apps. Whether you’re deploying smart devices at home or managing industrial IoT, we expose critical security gaps before attackers do.
Why Choose Bright Defense for IoT Pen Testing?
- Practical Results: Reports prioritize exploitable flaws with fixes you can apply to your specific device types and architectures.
- Flexible Packages: Select Basic (single device), Connected (smart environments), or Industrial (large-scale, compliance-bound systems).
- Full-Stack Testing: We go beyond surface scans to inspect firmware, local ports, mobile apps, and backend integrations.
- Built for Regulated Environments: Testing supports HIPAA, FDA, and IEC 62443 security assessments.
FAQs
IoT penetration testing involves simulating cyberattacks on Internet of Things devices and their networks to identify security vulnerabilities. This process examines components such as firmware, APIs, wireless communication, and cloud services to pinpoint weaknesses that attackers might exploit.
Penetration testing, or pen testing, is a simulated cyberattack on a system, network, or application to identify vulnerabilities that could be exploited by malicious actors. It involves ethical hackers who use various tools and techniques to probe security defenses, assess potential weaknesses, and provide recommendations for improving security.
IoT testing refers to the process of verifying the functionality, performance, and security of Internet of Things devices and systems. This includes assessing how these devices interact with each other, ensuring reliable data transmission, and confirming that they operate as intended under various conditions.
IoT security testing focuses on evaluating Internet of Things devices and systems to identify potential security vulnerabilities. This involves checking for issues like weak authentication, insecure data storage, and unencrypted communication channels, aiming to protect against unauthorized access and data breaches.
Common vulnerabilities include weak or hardcoded passwords, outdated firmware, insecure communication protocols (like unencrypted HTTP), exposed ports, and poor authentication mechanisms. These issues make devices easier targets for attackers.
IoT systems combine hardware, software, wireless communication, and cloud platforms. Unlike traditional systems, IoT testing must account for physical tampering, device constraints (limited memory and processing), and complex data flows between components.
Firmware analysis involves extracting and inspecting the software that runs on IoT devices. Testers look for hardcoded credentials, insecure configurations, and backdoors that may not be visible during normal operation but can be exploited.
IoT devices rely on constant communication across local and internet-connected networks. Testing network traffic helps detect vulnerabilities such as man-in-the-middle risks, data leaks, and weak encryption during device communication.
Common tools include Wireshark (for traffic analysis), Nmap (for network scanning), Burp Suite (for web interface testing), Binwalk (for firmware analysis), and Metasploit (for exploit simulation). These help assess both device and ecosystem-level security.
APIs are often used to control and manage IoT devices remotely. Weak authentication, rate-limiting issues, and poor input validation in APIs can give attackers access to device functions or sensitive user data.
Get In Touch



