
Role of Cyber Threat Intelligence in Incident Response
Cyber threat intelligence (CTI) supports incident response through timely and relevant information that shapes decisions during cybersecurity incidents. As attacks grow more advanced and frequent, organizations rely on CTI to guide their actions and limit potential damage.
According to a 2024 SANS report, 78% of security teams reported faster incident resolution when CTI was integrated into their response workflows.
In this blog, I’ll outline how cyber threat intelligence fits into incident response, focusing on its key functions, strategic applications, common challenges, and supporting data.
What is Cyber Threat Intelligence?
Cyber threat intelligence refers to evidence-based knowledge about cyber threats, gathered through the collection and analysis of data from various sources. It includes information about threat actors, their behaviors, tools, infrastructure, and known targets.
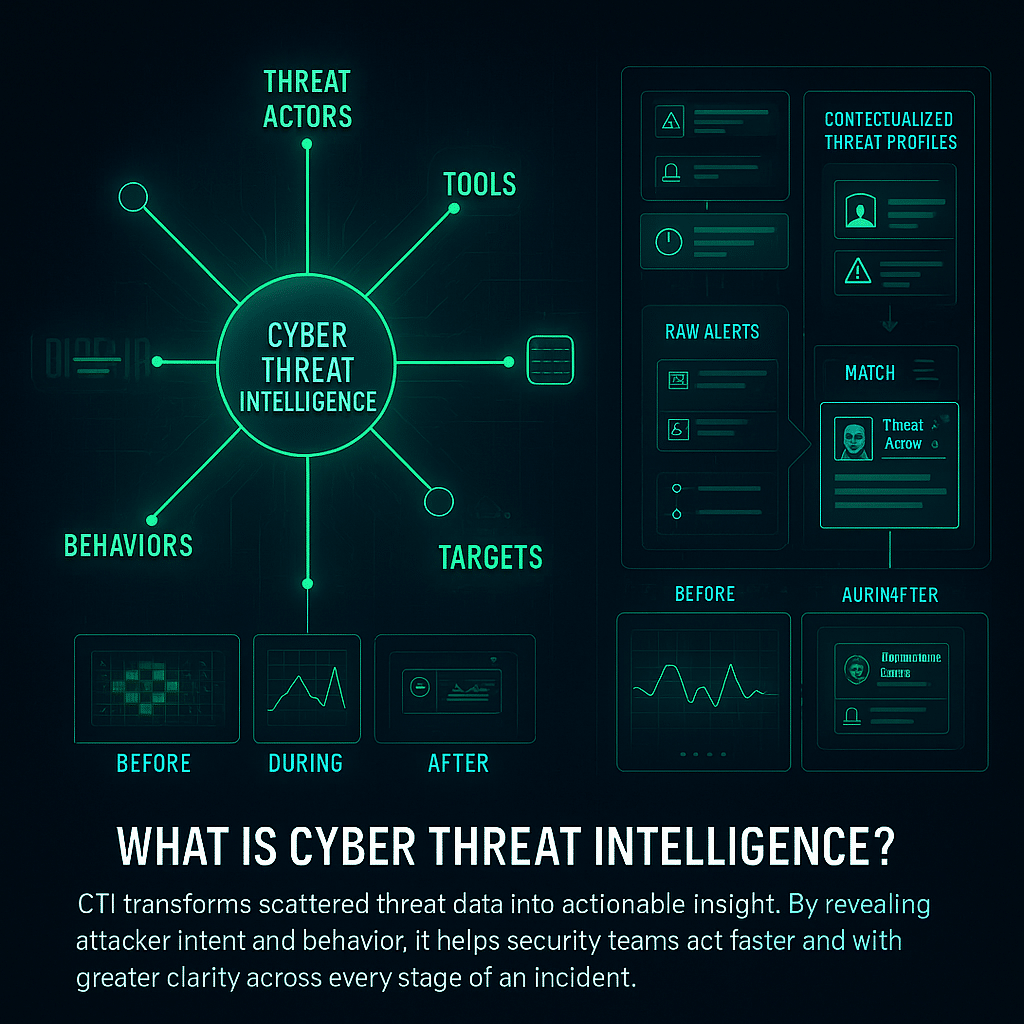
The goal is to create a usable profile of potential risks that can inform security teams before, during, and after incidents. Unlike raw data or unfiltered alerts, CTI adds context that helps distinguish between routine activity and actual threats.
This allows organizations to prioritize responses, adjust defenses, and make informed decisions based on relevant and timely threat information.
What is Incident Response?
Incident response refers to the structured approach an organization takes to detect, investigate, and recover from cybersecurity events.
These events can include data breaches, ransomware attacks, unauthorized access, or any other activity that threatens the confidentiality, integrity, or availability of systems and data.

The goal is to handle the situation quickly, contain the damage, and restore normal operations while limiting impact. A typical incident response process follows defined steps:
- Preparation: Developing plans, assigning roles, and setting up tools ahead of time.
- Detection and analysis: Identifying the incident and understanding its scope.
- Containment: Isolating affected systems to prevent further harm.
- Eradication: Removing the root cause and any lingering malicious code.
- Recovery: Restoring systems and verifying they are safe to use.
- Post-incident review: Analyzing the response to improve future readiness.
This approach helps security teams respond with consistency, reduce downtime, and improve the organization’s ability to manage future threats.
How Cyber Threat Intelligence and Incident Response Working Together
Cyber threat intelligence supports every phase of incident response, improving both speed and accuracy during a security event.
According to a 2023 Ponemon Institute study, organizations utilizing CTI reduce incident response time by approximately 32%, highlighting the critical advantage of integrating intelligence into security operations.
While incident response focuses on reacting to threats, threat ingelligence helps shape those responses with relevant context. CTI supports incident response through the following:
1. Early Threat Detection
CTI delivers early warnings and indicators of compromise (IoCs), enabling organizations to detect threats before they materialize into significant breaches.
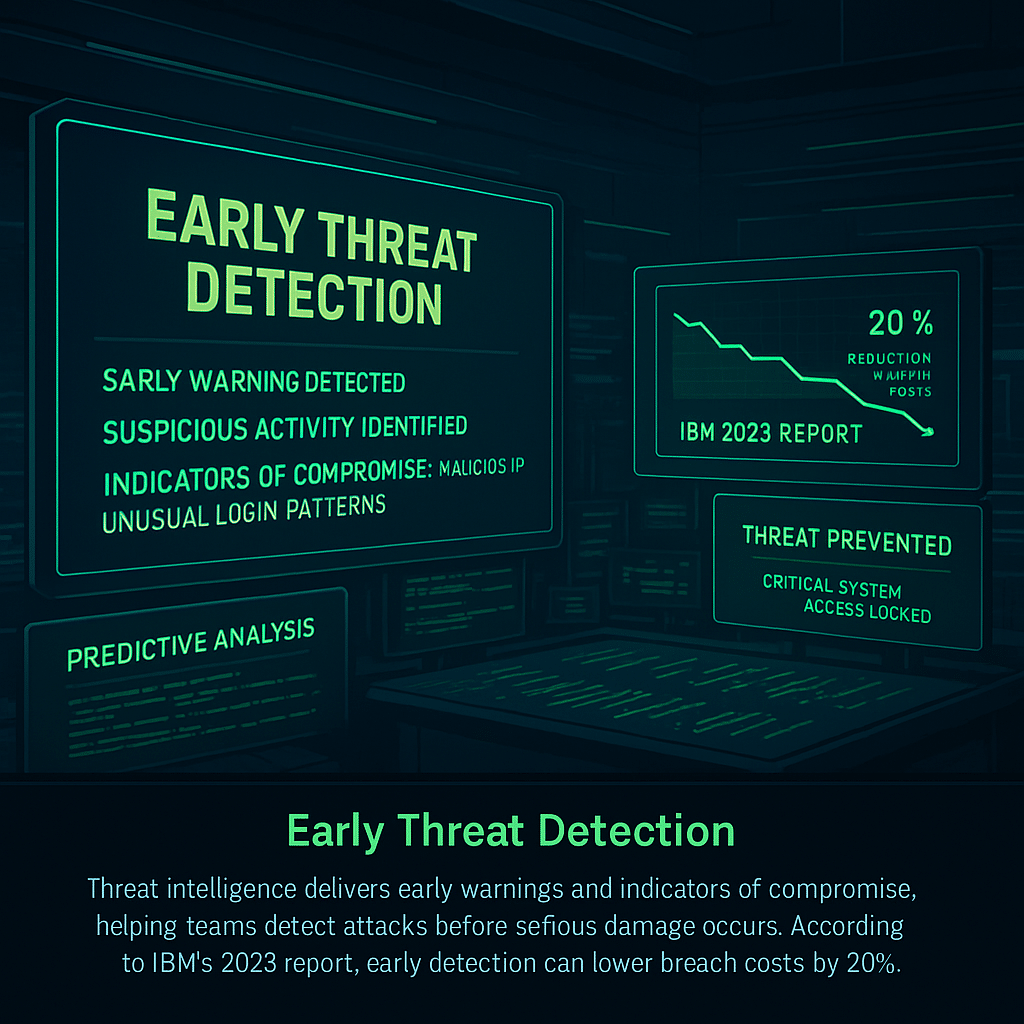
Early detection substantially reduces potential damages and associated costs. IBM’s 2023 Cost of a Data Breach Report notes that organizations using advanced threat intelligence reduce breach costs by 20% compared to those without such tools.
2. Informed Analysis
When a security incident occurs, cyber threat intelligence provides context about the attacker’s intent, behaviors, and previous activities. This includes information on specific threat actors, their usual targets, and typical methods.
Analysts can then match incoming alerts with known attack patterns to better understand the incident’s scope and goals. Such insights speed up decision-making and close gaps in the incident response plan.
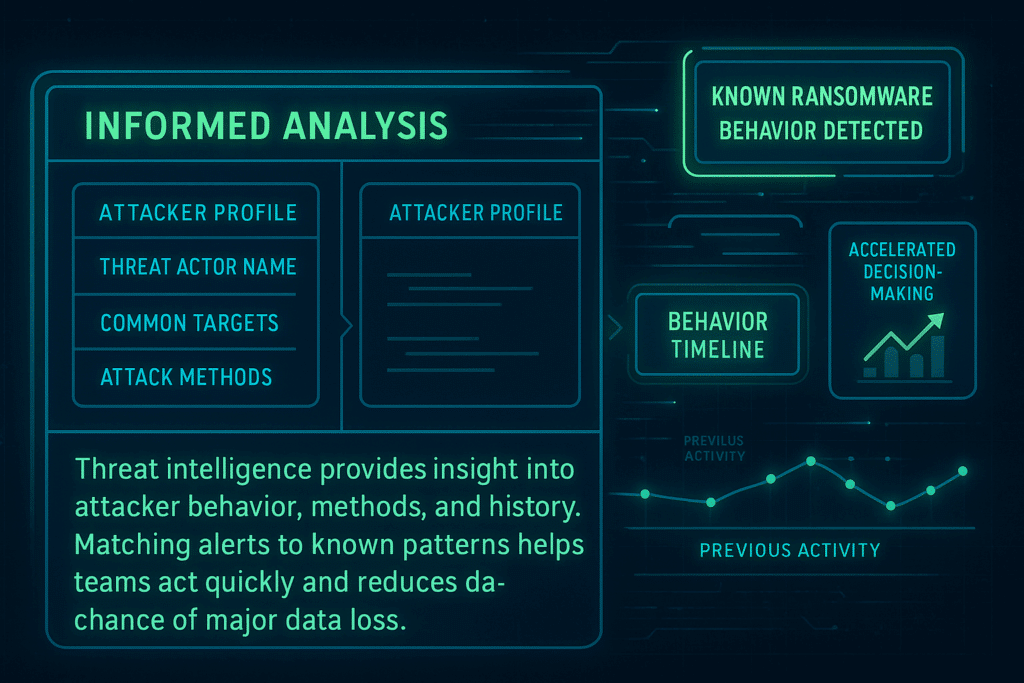
For example, identifying a known ransomware group’s modus operandi allows quicker defensive actions, reducing potential data losses significantly.
3. Improved Situational Awareness
Situational awareness during incidents means understanding threats as they happen and anticipating potential attacker actions.
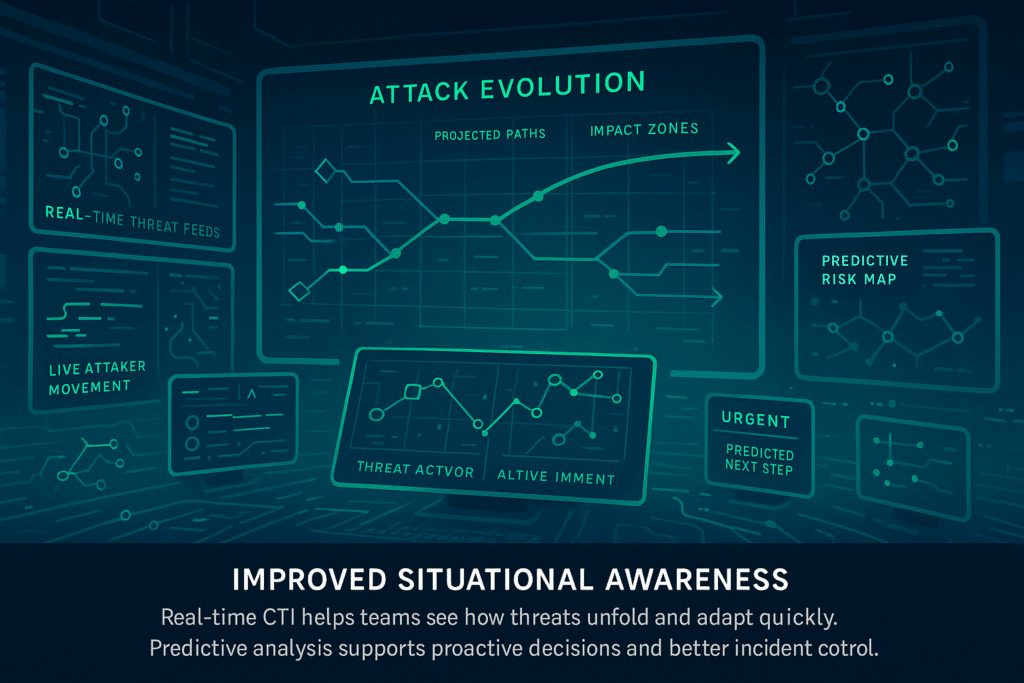
Cyber threat intelligence significantly supports this with real-time threat feeds and predictive analyses. Teams can anticipate how an attack might evolve, adjusting responses proactively.
4. Smarter Threat Containment and Eradication
Knowing how a threat actor typically moves through networks, exploits access, or maintains persistence helps responders contain threats effectively. Threat intelligence clarifies which systems need isolation and identifies areas at risk for further compromise.
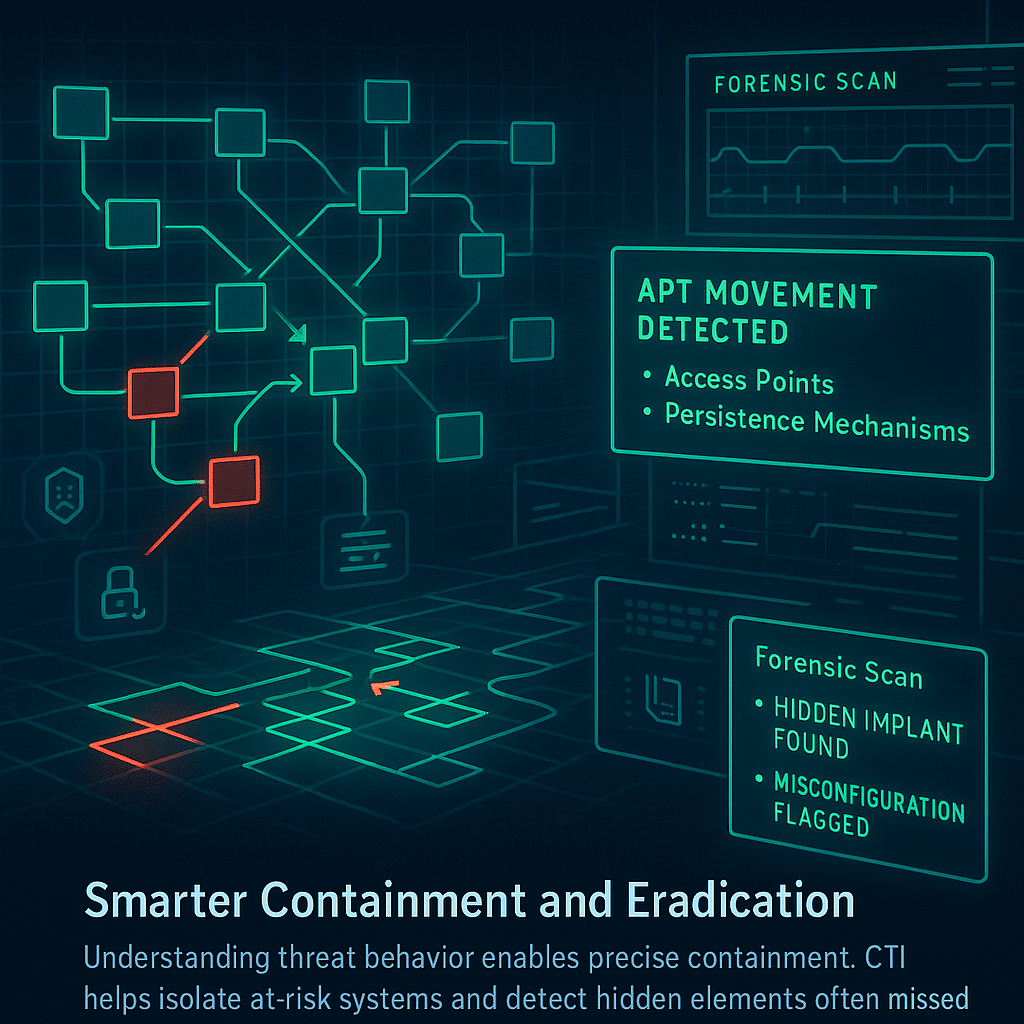
This reduces unintended disruptions and improves the chances of completely eliminating the threat. Information linked to advanced persistent threats or specific attacker tools also helps responders spot hidden implants or misconfigurations that manual searches often overlook.
5. Better Recovery Decisions
Threat data collected during containment helps set recovery priorities. Knowing about active campaigns, reinfection techniques, or evasion methods allows teams to plan restoration efforts while avoiding further exposure.
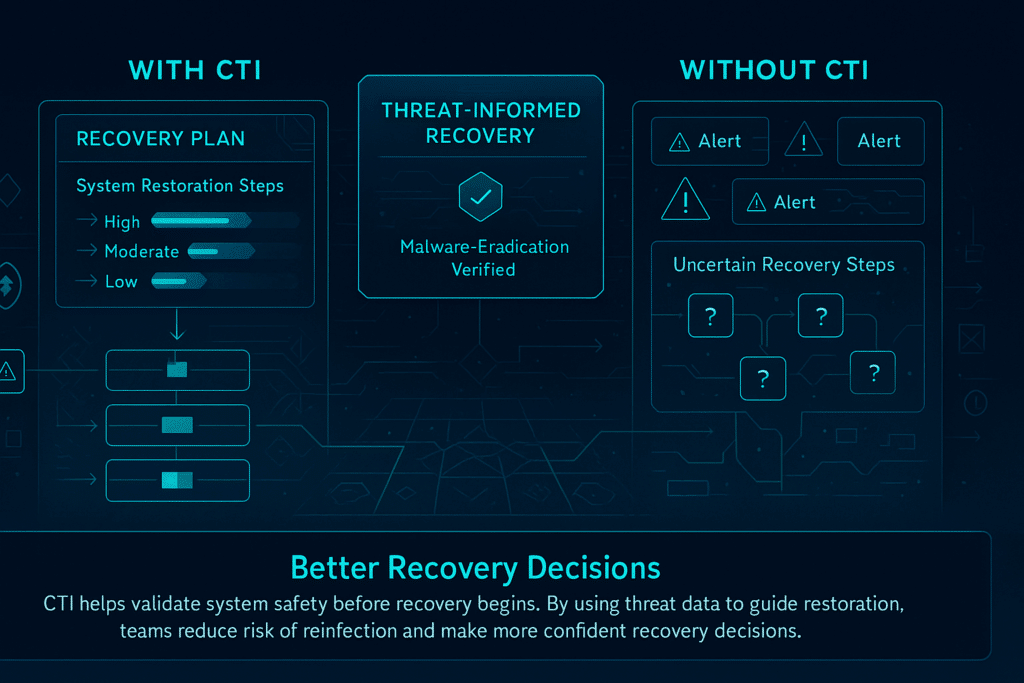
Cyber threat intelligence also supports temporary controls during ongoing ransomware attacks or supply chain attacks. Recovery plans informed by reliable intelligence reduce the chance of repeat cybersecurity incidents and help tighten security controls over time.
6. Post-Incident Improvements
Once a case is resolved, the intelligence gained remains useful. Security teams pull patterns and gaps from the event to improve detection rules, update response procedures, and harden systems.
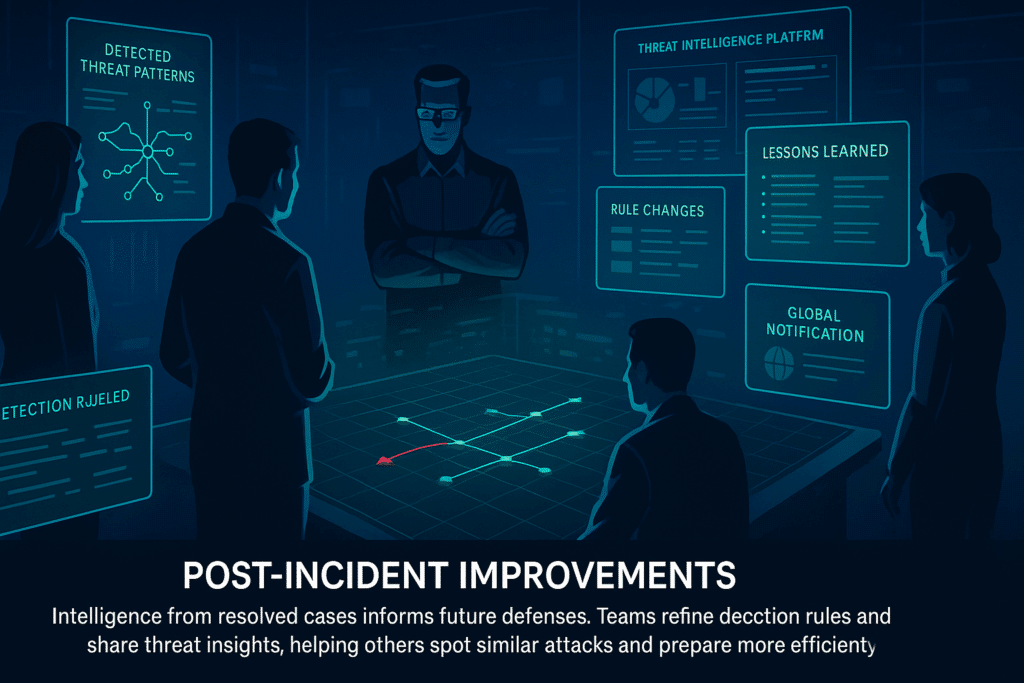
Adding this information to threat intelligence platforms helps others recognize similar attacks and adjust their defenses. These updates strengthen security and help responders prepare for incidents with similarities to past cases.
Incorporating CTI into Incident Response Strategies
Using cyber threat intelligence (CTI) in incident response helps teams act with better focus and context. Below are key ways to bring CTI into response efforts:
1. Integration into Incident Response Plans
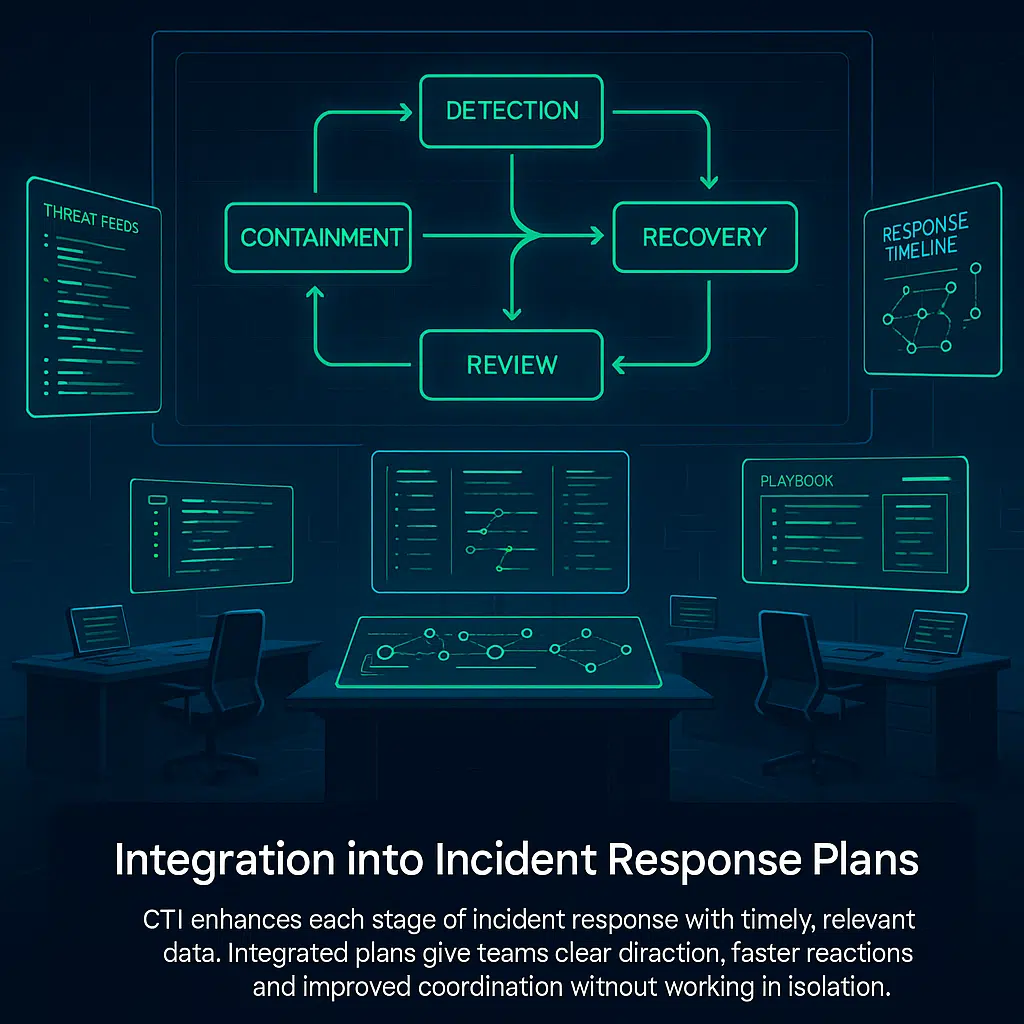
Cyber threat intelligence supports every stage of the incident response plan, detection, containment, recovery, and review. When teams follow defined roles and workflows, they can act faster and with better focus. Intelligence needs to be accessible, not isolated. Integrated plans let incident response teams respond with clear direction and context.
2. Automation and Response Tools
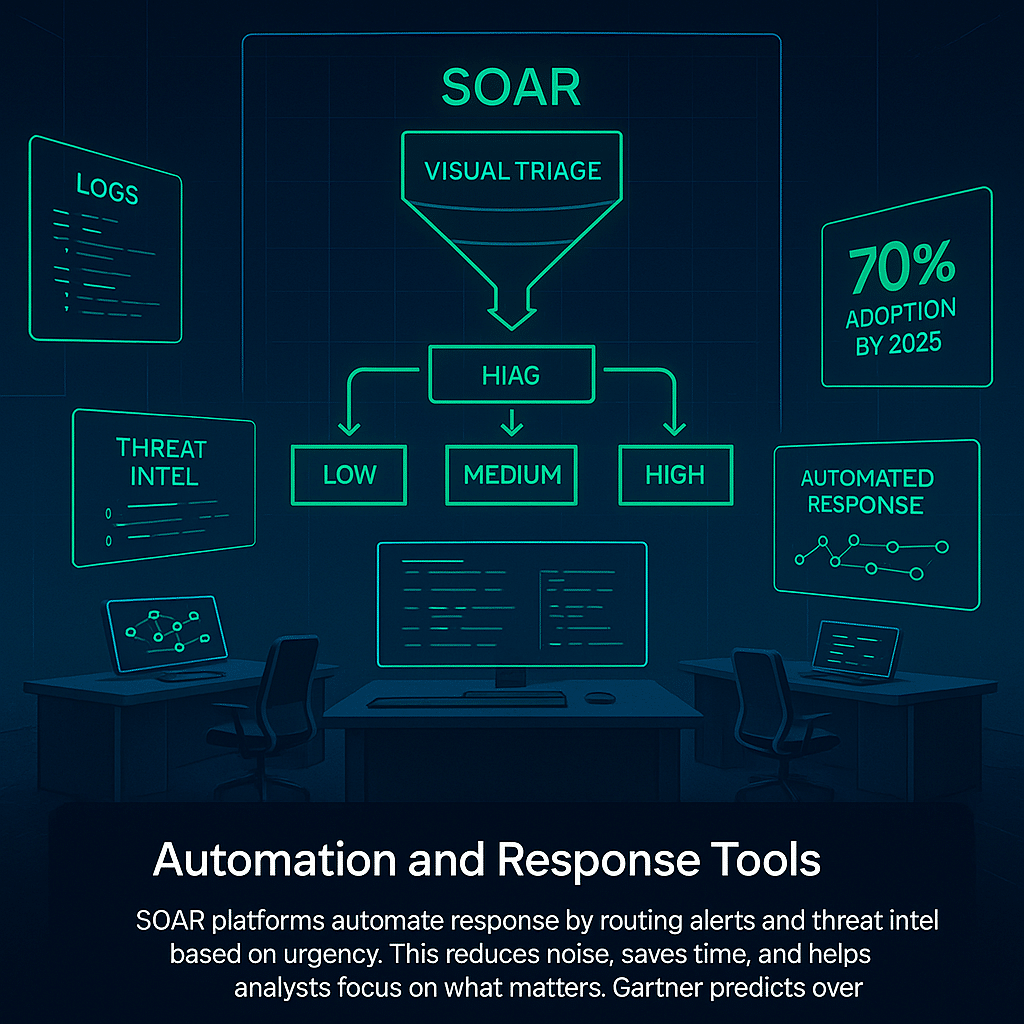
SOAR platforms reduce response time. They collect alerts, logs, and threat intelligence feeds, then route them based on urgency. Analysts can focus on relevant threats instead of sorting through raw data. Gartner reports that over 70% of organizations will adopt SOAR tools connected to threat intelligence for incident response by 2025. This shift cuts noise and saves time.
3. Collaborative Intelligence Sharing
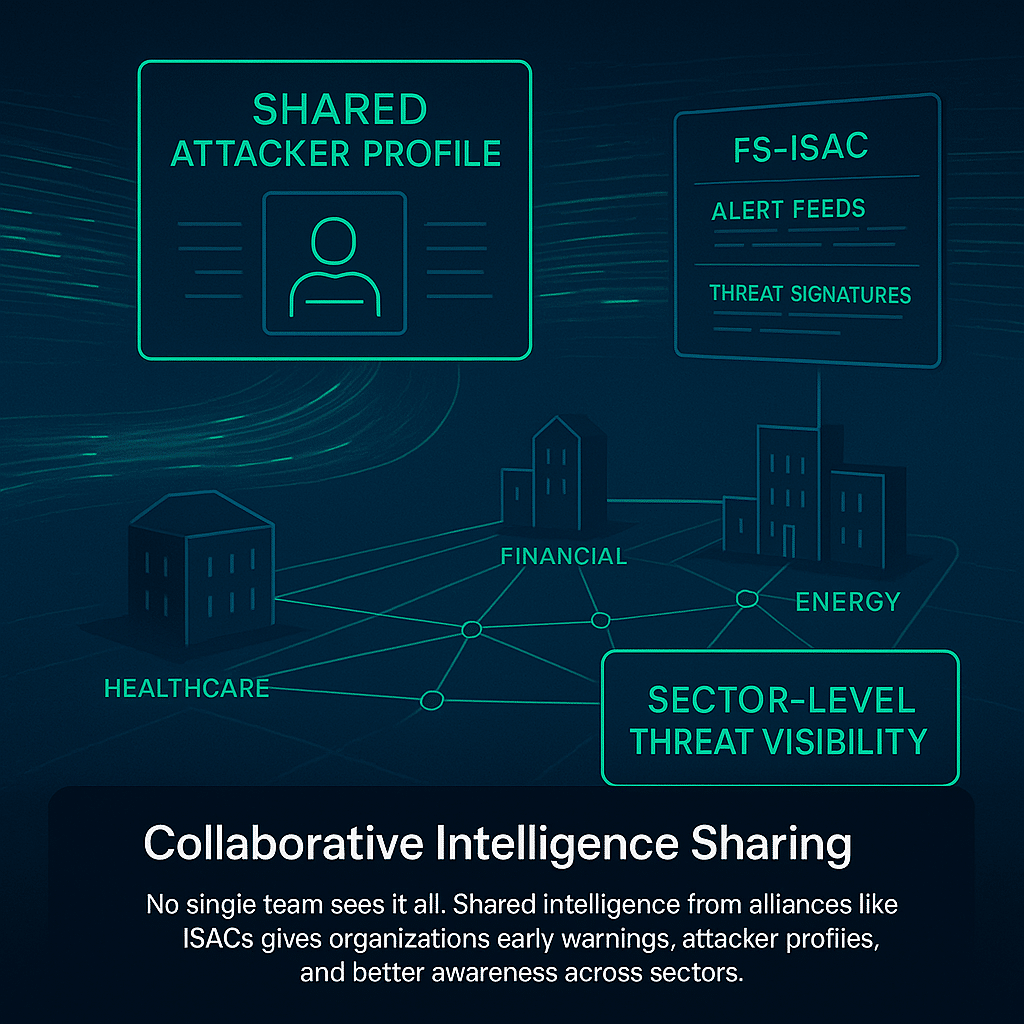
No single organization sees every threat. That’s why collaborative sharing remains essential. Through industry-specific alliances like ISACs, security teams gain early visibility into what others are facing.
The Financial Services ISAC (FS-ISAC), for instance, has helped prevent coordinated cyber attacks through real-time alerts and shared attacker profiles.
This approach benefits not just one firm but entire sectors. It builds a stronger network against threat actors and adds depth to each organization’s view of potential threats.
Challenges of Implementing Cyber Threat Intelligence
Using cyber threat intelligence (CTI) brings several operational challenges. If not addressed early, these issues can reduce the value of CTI in incident response and overall security decision-making.
Below are some of the key challenges organizations often face:
1. Information Overload
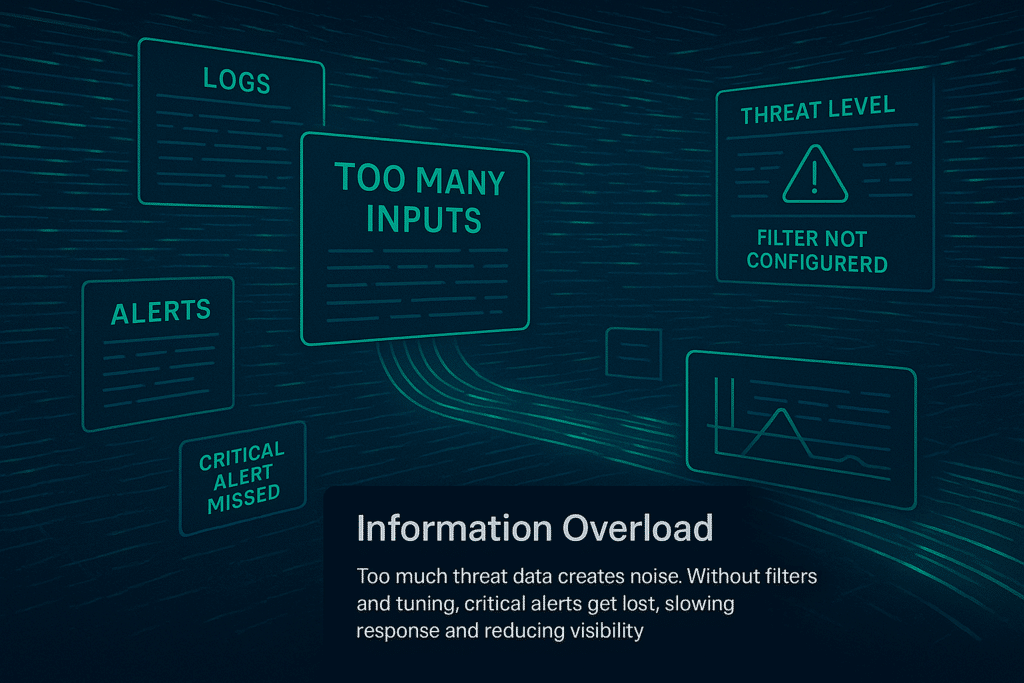
Large volumes of threat data create noise that can slow response. Without filtering mechanisms or proper analysis, teams risk overlooking critical threats while chasing irrelevant ones. Security tools that support automating threat detection can help narrow focus, but they require tuning. Unchecked overload affects both visibility and decision speed.
2. Quality and Timeliness
Threat intelligence sources should be reviewed routinely, with validation processes in place to support confident action. Delayed or flawed input undercuts the entire incident response process and damages trust in the system.
Maintaining awareness of the evolving threat landscape helps filter outdated data from actual threats. Without these checks, the organization may miss signs of cyber incidents or misallocate resources in response to irrelevant threats, weakening the organization’s security posture.
3. Skilled Personnel Shortage
Interpreting cyber threat intelligence requires deep expertise. But the talent pool remains shallow. With millions of roles still vacant, finding analysts who can translate raw input into actionable insights poses a serious hurdle.
This gap hinders effective incident response and slows the application of strategic intelligence during active threats. Security operations center staff often juggle too many roles, increasing fatigue and the chance of missed signals.
Addressing this issue requires integrating threat intelligence processes that reduce false positives and surface the most relevant threats. Without a proactive approach, organizations struggle to stay ahead of future incidents, leaving their overall security posture exposed.
Stronger support for incident response efforts and investment in threat intelligence capabilities can reduce the burden on incident responders and help detect potential security incidents earlier.
Real-World Applications of CTI
Here are some of the ways cyber threat intelligence (CTI) has been applied during real incidents. These cases show how CTI helps organizations respond faster and reduce impact during active threats.
Case Study 1: Ransomware Attacks
In recent ransomware incidents, organizations utilizing CTI demonstrated superior response capabilities. The WannaCry ransomware attack in 2017 exemplified the advantage of actionable threat intelligence. Entities leveraging shared intelligence identified attack vectors promptly, applying patches and mitigating further damages effectively. (Wikipedia)
Case Study 2: Financial Sector Incidents
Financial institutions frequently encounter targeted attacks. In 2022, CTI significantly reduced response times for banks during widespread phishing campaigns, cutting potential financial losses substantially. Rapid dissemination of threat indicators via ISACs allowed banks to neutralize phishing websites swiftly. (Time)
How to Measure CTI Effectiveness?
Measuring the effectiveness of Cyber Threat Intelligence (CTI) involves tracking how well an organization can detect, understand, and respond to security threats using intelligence-driven insights.
Two widely used performance indicators are:
- Mean Time to Detect (MTTD): The average amount of time it takes for a security team to become aware of a potential threat or incident after it begins.
- Mean Time to Respond (MTTR): The average amount of time it takes to contain, remediate, or mitigate a threat after detection.
A recent ESG survey found that organizations using CTI saw a 40% reduction in MTTD and a 45% reduction in MTTR. This shows that CTI can lead to faster detection and quicker responses to security incidents.
In addition to MTTD and MTTR, organizations may also monitor:
- Incident Volume Trends: Comparing the number of incidents before and after CTI integration
- False Positive Rates: Tracking changes in alert accuracy
- Threat Attribution Accuracy: Measuring how often CTI leads to correct identification of threat actors or attack methods
- Threat Intelligence Usage Rates: Observing how often CTI feeds are used in daily operations or investigations
- Analyst Productivity: Noting whether CTI shortens investigation time or supports faster decision-making
Final Thoughts
Cyber Threat Intelligence significantly influences incident response effectiveness. The ability to anticipate, contextualize, and rapidly address cyber threats depends heavily upon high-quality, timely intelligence.
Despite challenges such as information overload and skill shortages, CTI remains an indispensable asset in modern cybersecurity. Continued investment in CTI capabilities, training skilled personnel, and adopting advanced technological solutions will further strengthen organizational defenses against evolving cyber threats.
FAQs
CTI is moving toward more automation, stronger use of AI and machine learning, and deeper integration with security tools like SIEM and XDR.
It will focus more on providing relevant, real-time insights tailored to each organization’s environment and threat profile, helping teams detect and respond to threats faster and with better context.
Threat intelligence provides context on threats, helping security teams detect, analyze, and respond to incidents more effectively.
It offers insights into attacker tactics and indicators of compromise, which can guide containment and remediation efforts.
Cyber intelligence involves collecting and analyzing information about potential cyber threats.
It helps organizations understand attacker behaviors and anticipate future attacks, allowing for proactive defense measures.
Cyber Threat Intelligence (CTI) teams are responsible for gathering threat data, analyzing it to identify risks, and sharing actionable insights. Their duties include monitoring threat actors, assessing vulnerabilities, and supporting incident response efforts.
Incident response is the process of identifying, managing, and mitigating cybersecurity incidents. It aims to minimize damage, recover affected systems, and prevent future breaches through structured procedures and coordination.
Get In Touch



