What is Network Penetration Testing?
Network penetration testing simulates real-world attacks to uncover weak points before they are exploited. It focuses on finding the kinds of vulnerabilities attackers actively search for, especially those exposed to the internet.
A network pen test helps determine how easily an attacker could break in from the outside. It begins with scanning for exposed systems and follows the same path a real attacker would take, revealing the risks that need attention.
If you want to understand how this testing works, what it exposes, and why it is a key part of any security program, keep reading.
Key Takeaways
- Network penetration testing simulates real world attacks to expose how intruders could break into external or internal systems
- The process uncovers vulnerabilities such as outdated software, open ports, and weak access controls that attackers might exploit
- Testers follow a methodical approach starting from reconnaissance to exploitation to assess the network’s actual risk exposure
- External tests examine internet facing systems while internal tests focus on threats that could originate from inside the network
- The final report includes detailed findings, risk impact, and concrete remediation steps to reduce exposure and validate improvements
What is Network Penetration Testing?
Network Penetration Testing is a method used to assess the network security of a system by conducting simulated attacks from malicious outsiders or insiders.
It identifies vulnerabilities, misconfigurations, and potential entry points that could be exploited. Ethical hackers, specialists trained to think like attackers, use manual and automated tools to mimic real-world attack techniques, attempting to gain unauthorized access to systems, devices, and data.
This helps organizations understand their exposure and apply specific fixes before real attackers exploit weaknesses.
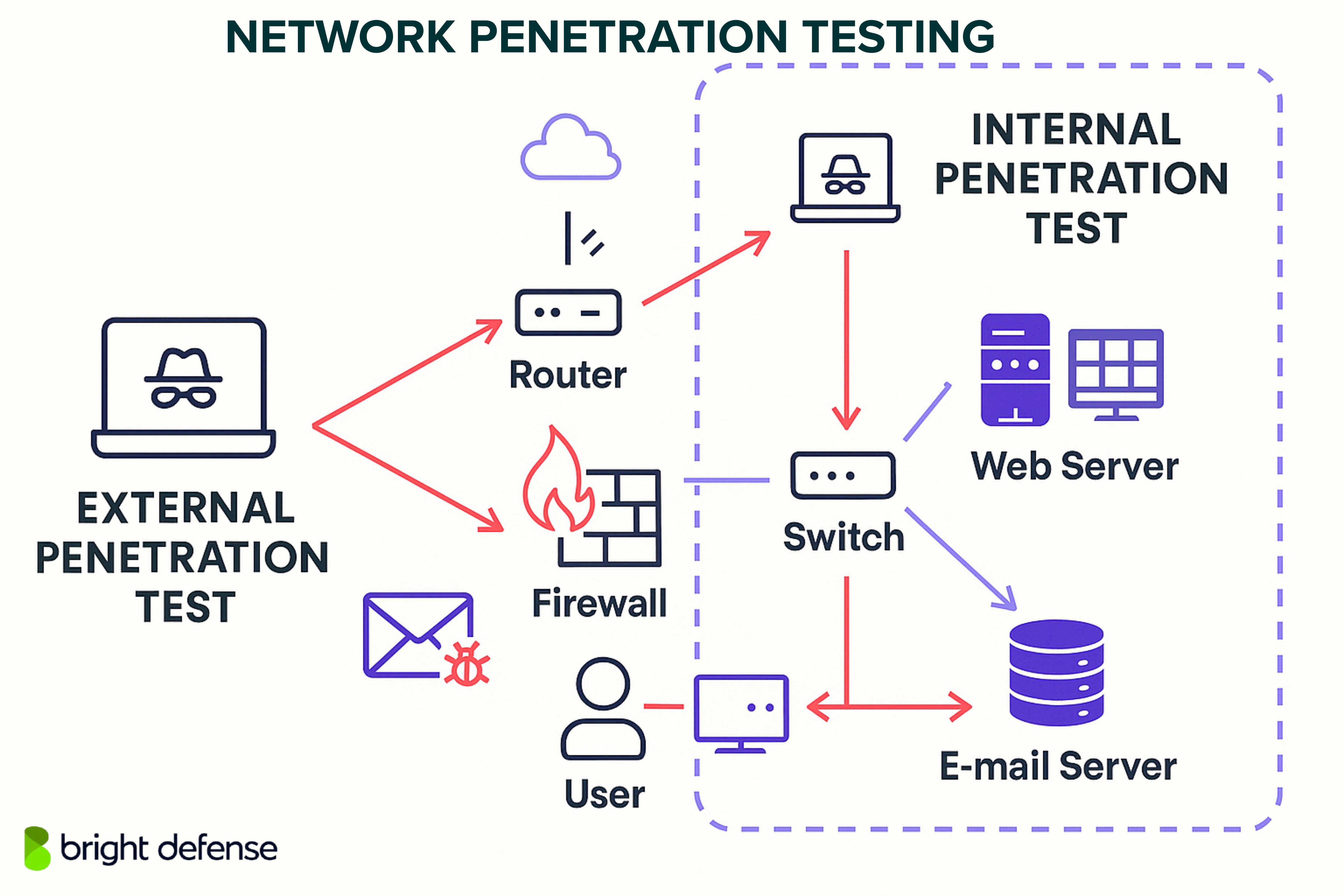
Network pen test is divided into two parts: internal and external penetration testing.
Internal network penetration testing simulates an attack from inside the organization’s firewall. It helps uncover internal threats like a malicious employee, a compromised device, or poor access controls. This type of penetration testing focuses on how much damage could occur if an attacker already has some level of access.
External pen test, on the other hand, targets the public-facing systems such as websites, VPNs, email servers, and others. The goal is to assess how easily an outside attacker could break into the environment. It often begins with scanning for exposed services and misconfigurations that could lead to a breach.
How to Perform Network Penetration Testing?
Network penetration testing follows a structured and disciplined approach to evaluate the security posture of an organization’s infrastructure. Each phase is crucial for accurate findings and safe execution.
Step 1 – Pre-Engagement and Planning
This initial phase defines the test’s scope, goals, legal boundaries, and communication channels. A Rules of Engagement (RoE) document is prepared. It outlines which systems are in scope, what methods are allowed, and who to contact in case of emergencies. This step also includes a Non-Disclosure Agreement (NDA) to protect sensitive data and clarify responsibilities.
Key tasks:
- Define scope (internal vs. external, IP ranges)
- Set timelines and deliverables
- Determine risk tolerance
Step 2 – Reconnaissance and Discovery
This is the information-gathering stage. Passive reconnaissance involves collecting data without touching the target, such as using WHOIS records, DNS lookups, and public databases. Active reconnaissance uses tools like Nmap to scan for open ports, identify services, and fingerprint operating systems.
The goal is to map out the network, identify hosts, and understand potential entry points without alerting defense systems too early.
Step 3 – Vulnerability Analysis
Once systems and services are identified, the tester analyzes them for known vulnerabilities. This includes checking outdated software, weak configurations, default credentials, and missing patches.
Tools like Nessus, OpenVAS, or manual techniques are used here. Correlating service banners with CVEs (Common Vulnerabilities and Exposures) is a common tactic.
Key goals:
- Prioritize vulnerabilities based on impact and exploitability
- Prepare a shortlist of attack vectors for the next phase
Step 4 – Exploitation and Gaining Access
This is the offensive phase. Using the insights from the previous step, the tester attempts to exploit vulnerabilities to gain unauthorized access to systems or escalate privileges. Exploits can be either public (e.g., from Exploit-DB) or custom-made for specific scenarios.
Popular frameworks include Metasploit, Cobalt Strike, and manual shellcode execution. The goal is to demonstrate the risk, not cause damage, so exploits must be carefully tested in staging environments beforehand.
Step 5 – Post-Exploitation and Persistence
After gaining access, the tester assesses what data or control can be achieved. This includes checking access to internal resources, attempting lateral movement, and evaluating the organization’s ability to detect the intrusion.
Persistence techniques—such as adding new users or planting backdoors—are tested with permission to simulate real-world threat actor behavior.
Step 6 – Analysis and Reporting
This final phase documents all findings in a detailed report. The report includes exploited vulnerabilities, methods used, data accessed, and the business impact. It also provides actionable remediation steps and risk ratings.
Deliverables include:
- Executive summary for non-technical stakeholders
- Technical breakdown for security teams
- Recommendations for patching, configuration changes, and detection improvements
Step 7 – Remediation and Retesting
After delivering the network pen test report, the client addresses the identified vulnerabilities. Once fixes are applied, such as patching systems, changing configurations, or segmenting the network infrastructure, the penetration tester conducts a focused retest.
Retesting verifies whether:
- Security vulnerabilities were correctly addressed
- Exploits no longer work
- No new issues were introduced
Each phase must be conducted ethically, within defined limits, and with a focus on improving the target organization’s resilience.
A final report may include updated results and validation of the applied fixes. This step often includes re-running vulnerability scanning and inspecting for any lingering or multiple vulnerabilities that could impact the overall security posture.
What Should Be Included in a Network Pen Test Report?
A well-structured network penetration test report is essential for helping both technical teams and decision-makers understand the findings, evaluate risk, and take corrective action. Here’s what a thorough report should include:
- Executive Summary: Brief overview of the test purpose, key findings, and business impact.
- Scope and Methodology: Outline of what was tested, how it was tested, and tools used.
- Findings Summary Table: List of vulnerabilities with severity, affected assets, and reference IDs.
- Detailed Technical Findings: Description of each issue, how it was found, potential impact, and fix.
- Post-Exploitation Summary: Summary of access gained, data reached, and internal movement tested.
- Remediation Recommendations: Specific steps to fix vulnerabilities and improve configurations.
- Retesting Guidance: Instructions for verifying whether fixes were effective.
- Appendices: Raw data, logs, screenshots, and scan results for reference.
Why Companies Need Network Penetration Testing?
Network penetration testing plays a critical role in modern cybersecurity strategies. It provides organizations with a controlled method to simulate real-world attacks and evaluate how well their defenses hold up under pressure. Here’s why this process is essential:
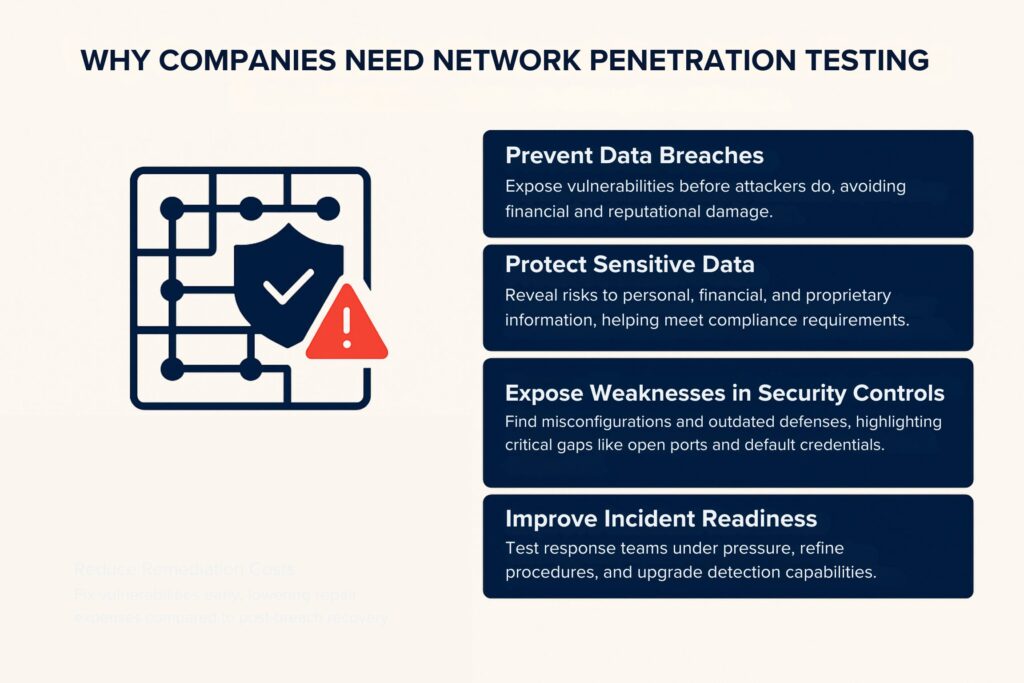
1. Prevents Data Breaches
One of the main reasons companies invest in network penetration testing is to prevent a data breach. By simulating how attackers operate, pen testers identify vulnerable systems and insecure configurations before malicious actors do.
This proactive approach can stop unauthorized access to customer records, financial data, and internal communications, which could otherwise lead to reputational damage, legal issues, and financial loss.
2. Protects Sensitive Data
Many organizations handle personal, financial, or proprietary information. Network penetration testing services reveal if this sensitive data can be accessed from the outside or moved across internal networks without proper controls.
It helps assess whether encryption is applied correctly, whether access controls are too relaxed, and whether target systems are exposed. Keeping sensitive information secure is often tied to compliance requirements, especially for industries like finance, healthcare, and e-commerce.
3. Reveals Weaknesses in Security Controls
Firewalls, intrusion prevention systems, antivirus tools, and endpoint protection platforms all form layers of defense, but no system is perfect.
Network penetration testing uncovers gaps, misconfigurations, or outdated components that attackers might exploit. It also highlights overlooked issues like open ports, default credentials, or unmonitored wireless access points. These findings point to flaws in security controls that need attention.
4. Improves Incident Readiness
Tests often reveal how a company’s detection and response teams react to real attack behavior. This includes how alerts are generated, how logs are reviewed, and whether responses are timely and accurate.
Findings help shape better procedures, update detection rules, and improve training for the information security team. These exercises can be structured as gray box testing or black box testing depending on the test objectives.
5. Reduces Remediation Costs
Finding existing vulnerabilities early, before attackers do, reduces long-term repair costs. Fixing an exposed service during a test is far less expensive than responding to a full breach.
Pen testing allows security teams to prioritize based on real-world risk, supporting more efficient resource use and better overall outcomes.
6. Strengthens Overall Security Posture
Penetration testing does more than highlight weaknesses, it validates what works. It confirms whether policies are enforced and which parts of the system hold up under pressure.
Over time, regular tests build confidence in security systems and support the creation of stronger policies and infrastructure. They also help verify whether protections are effective across both external penetration testing and internal penetration testing scenarios.
In short, network penetration testing is not just a technical exercise. It functions as a security assessment that supports long-term defense and continuity planning. From identifying flaws to validating fixes, it plays a vital role in managing risk.
How Can Bright Defense Help You With Network Pen Tests?
At Bright Defense, we understand the difficulty organizations face when trying to secure networks against new and persistent threats. Our network penetration testing services focus on exposing vulnerabilities and offering practical guidance to improve your defenses.
Why Choose Bright Defense for Network Penetration Testing?
- Customized Testing Plans: We offer specific testing packages for different business needs. The Ignite Plan suits startups and small teams, focusing on the most critical endpoints. The Elevate Plan covers broader assets for growing businesses. The Summit Plan fits large enterprises that manage complex systems.
- Skill and Tools: Our team uses specialized tools and proven methods to inspect applications, networks, and APIs. We search for flaws that attackers might use and give you the knowledge to fix them before problems arise. During testing, we may simulate attack paths through a web application or attempt limited simulated attacks under safe, controlled conditions.
- Support for Compliance: We follow multiple standards, including SOC 2, ISO 27001, HIPAA, and CMMC. These services help your business stay in line with regulatory needs while keeping defenses in place. Early testing can also support risk analysis when evaluating your overall exposure.
- Actionable Reporting: Post-assessment, we provide detailed analysis with clear remediation steps and recommendations. This empowers your security experts and technical teams to address security weaknesses effectively.
FAQs
External network testing focuses on attack paths from the internet-facing perimeter, while internal network testing focuses on what an attacker could do after gaining internal access, including lateral movement and access to sensitive systems.
Scope often includes IP ranges, network services, remote access paths, firewalls and segmentation controls, exposed management interfaces, and identity paths tied to administrative access, with explicit exclusions written down ahead of time.
Vulnerability scanning focuses on automated detection of known issues, while a penetration test validates exploitability and impact through controlled attacker-style actions under agreed rules.
A signed rules of engagement document plus written authorization should define scope, timing, contacts, escalation paths, and stop conditions before any testing begins.
A fast start usually needs an in-scope asset list, test window, points of contact, constraints such as no disruption testing, and a draft rules of engagement for signature.
A critical finding usually triggers controlled proof only, immediate notification to the right internal owner, and a pause or stop if the activity risks expanding impact beyond what the rules allow.
Post-report work usually starts with risk-based triage, assigned owners and deadlines for fixes, scheduled retesting for corrected items, and retention of the report as evidence for customers and audits.
A network penetration test is an authorized simulated attack against networked systems that checks whether weaknesses can be exploited and what impact an attacker could achieve, often using both external and internal test scenarios.
Penetration in networking refers to a security incident where an intruder gains, or attempts to gain, access to a system or network resource without authorization.
The purpose of network testing is to check whether a network is ready and functioning as intended and to evaluate the network for weaknesses so teams can prioritize fixes and reduce operational and security risk.
Network security testing is a structured set of technical tests and examinations that look for weaknesses in network security controls and produce findings that drive mitigation work and security improvements.
Get In Touch



