
Tim Mektrakarn - CISSP | CISA | ISO 27001
June 28, 2025
NIST CSF 2.0 Updates
The National Institute of Standards and Technology (NIST) introduced Cybersecurity Framework (CSF) in 2014 as a voluntary framework primarily intended for critical infrastructure organizations to manage and mitigate cybersecurity risk based on existing standards, guidelines, and practices. However, its adoption has spread across various sectors due to its flexibility and effectiveness.
The release of NIST CSF 2.0 brings significant updates and changes, reflecting the evolving cyber threat landscape and incorporating feedback from stakeholders to enhance its usability and applicability across different organizational and regulatory environments. Here’s an overview of the key changes in NIST CSF 2.0:
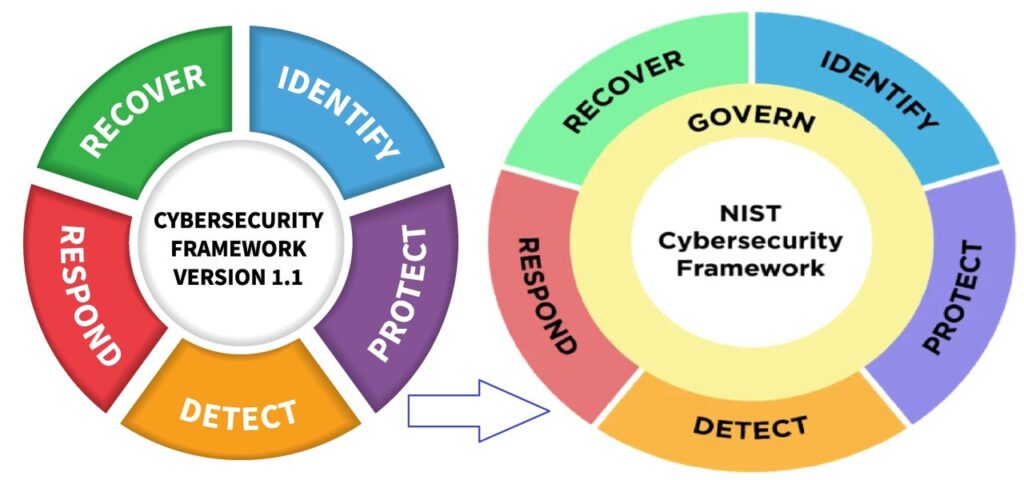
Govern Added to Core Function of NIST CSF 2.0
The addition of the Govern (GV) Function to the NIST CSF 2.0 framework represents a significant enhancement. It emphasizes the importance of cybersecurity governance within an organization’s overall risk management strategy. This update underscores the need for a structured approach to managing cybersecurity risks that align with the organization’s mission and the expectations of its stakeholders. Here’s a summary of the key aspects of the Govern Function:
Cybersecurity Risk Management Strategy
The GV Function mandates the establishment of a comprehensive cybersecurity risk management strategy that is well-communicated and monitored throughout the organization. This strategy serves as the foundation for making informed decisions on prioritizing cybersecurity efforts in alignment with organizational goals and stakeholder expectations.
Integration into Enterprise Risk Management (ERM)
By including governance activities as a core component, the GV Function ensures that cybersecurity is seamlessly integrated into the broader enterprise risk management strategy. This holistic approach facilitates a unified view of the organization’s risks, including cybersecurity-related ones, and promotes a coordinated response strategy.
Understanding Organizational Context
The GV Function emphasizes the importance of understanding the organizational context, including its mission, objectives, and the cybersecurity landscape. This understanding is crucial for tailoring the cybersecurity strategy to address specific risks effectively and challenges the organization faces.
Definition of Roles, Responsibilities, and Authorities
Clear delineation of roles, responsibilities, and authorities within the cybersecurity domain is a critical aspect of the GV Function. This clarity ensures accountability and facilitates effective decision-making and implementation of cybersecurity measures across the organization.
Policy Development and Oversight
The GV Function includes the development, communication, and enforcement of cybersecurity policies that support the organization’s strategy and compliance requirements. Regular oversight of these policies ensures they remain effective and relevant in the face of evolving cybersecurity threats.
Prioritization of Cybersecurity Activities
By providing outcomes that inform the organization’s actions, the GV Function helps prioritize the outcomes of the other five Functions (Identify, Protect, Detect, Respond, and Recover) within the NIST CSF. This prioritization is based on the organization’s specific context, mission, and stakeholder expectations. This ensures that resources are allocated efficiently to address the most significant risks.
In summary, the Govern Function in NIST CSF 2.0 underscores the critical role of governance in cybersecurity risk management. It provides a structured framework for establishing, communicating, and monitoring a cybersecurity strategy that is aligned with organizational goals and integrated into the overall enterprise risk management approach. This addition enhances the framework’s ability to support organizations in developing a comprehensive, strategic approach to managing cybersecurity risks.
Emphasis on Supply Chain Security
One of the major updates in CSF 2.0 is the heightened focus on supply chain security. Recognizing the increasing threats and vulnerabilities associated with supply chains, NIST has comprehensively expanded its recommendations to address supply chain risk management (SCRM). This includes guidance for identifying and managing cybersecurity risks across its supply chain partners.
Integration of Privacy Controls in NIST CSF 2.0
Reflecting the growing intersection between cybersecurity and privacy, NIST CSF 2.0 integrates privacy considerations more directly into the framework. This change aims to help organizations better manage privacy risks in conjunction with cybersecurity risks. It also encourages a more holistic approach to information security and privacy.
Expanded and Clarified Implementation Tiers
The implementation tiers in the framework, which provide context on how an organization views and manages cybersecurity risk, have been expanded and clarified. The updates aim to offer a clearer pathway for organizations to progress from one tier to the next. This facilitates a more strategic approach to enhancing cybersecurity maturity over time.
Enhanced Guidance for Small and Medium-Sized Businesses (SMBs)
Recognizing the unique challenges faced by SMBs in implementing robust cybersecurity practices, NIST CSF 2.0 includes enhanced guidance known as Quick Start Guides (QSGs) tailored to the needs and resources of smaller organizations. This is intended to make the framework more accessible and actionable for SMBs. It also encourages wider adoption and improving cybersecurity resilience across busienss sectors.
Inclusion of Emerging Technologies and Threats
NIST CSF 2.0 addresses the need to stay abreast of emerging technologies and the threats they bring. This includes expanded considerations for cloud computing, Internet of Things (IoT) devices, and artificial intelligence (AI). Incorporating these elements ensures that the framework better prepares organizations to manage the risks associated with adopting new technologies.
Improved Measurability
Another significant update is the focus on improving the measurability of cybersecurity practices. NIST CSF 2.0 provides clearer guidance on measuring and demonstrating cybersecurity measures’ effectiveness. This helps organizations communicate their cybersecurity posture more effectively to stakeholders and make informed decisions about where to invest.
Alignment with Other Standards and Frameworks
NIST CSF 2.0 enhances its alignment with other international standards and frameworks, such as ISO/IEC 27001. This alignment facilitates easier adoption for organizations already compliant with or considering compliance with multiple frameworks. This harmonization aims to reduce the burden on organizations and promote a more unified approach to managing cybersecurity risk.
Conclusion
The updates in NIST CSF 2.0 reflect a comprehensive effort to address the evolving cybersecurity landscape. It makes the framework more relevant, actionable, and accessible for organizations of all sizes and sectors.
By focusing on areas such as supply chain security, privacy, measurability, and the inclusion of emerging technologies, NIST aims to provide organizations with a robust tool for improving their cybersecurity posture. As cyber threats increase in sophistication and impact, adopting and implementing frameworks like NIST CSF 2.0 becomes crucial for protecting critical infrastructure and sensitive information.
Bright Defense Delivers NIST Compliance Solutions!
If you are looking to achieve NIST compliance, Bright Defense can help. Our monthly engagement model delivers a cybersecurity program that will allow your business to meet compliance frameworks, including NIST, SOC 2, CMMC, and ISO 27001. We combine our fractional CISO services with compliance automation to increase efficiency and lower the cost of compliance.
Start your journey to NIST compliance today with Bright Defense!
Get In Touch



