
John Minnix - Compliance Strategist
June 29, 2025
CMMC Level 2 Compliance: A Step-by-Step Strategy Guide
Are you ready to tackle CMMC Level 2 compliance but unsure where to start? Meeting the 110 security controls required for CMMC Level 2 can secure your position as a trusted defense contractor and protect vital Controlled Unclassified Information. This guide cuts through the complexity, offering actionable steps toward compliance and a more secure organization.
CMMC Levels 1-3: An Overview
The Cybersecurity Maturity Model Certification (CMMC) is a standardized framework developed by the U.S. Department of Defense (DoD) to ensure that organizations handling Federal Contract Information (FCI) and Controlled Unclassified Information (CUI) implement appropriate cybersecurity measures.
The CMMC framework consists of three levels. Each represents a higher degree of cybersecurity sophistication and maturity.
Here’s a closer look at these levels and their respective roles in the defense industrial base (DIB).
CMMC Level 1: Foundational
CMMC Level 1 sets the baseline for cybersecurity across the Defense Industrial Base (DIB). It focuses on fundamental practices to protect Federal Contract Information (FCI), information provided by or generated for the government that is not intended for public release.

Level 1 includes 17 basic safeguards, such as:
- Using secure passwords
- Applying software updates
- Maintaining basic incident response procedures
These controls form the entry point for all contractors working with the Department of Defense.
CMMC Level 2: Advanced
CMMC Level 2 applies to contractors that handle Controlled Unclassified Information (CUI) and builds on Level 1 by requiring additional safeguards.

Key requirements include:
- Enforcing access control policies
- Restricting system access to authorized users
- Applying encryption and secure session management
- Segmenting critical systems to prevent unauthorized access
Organizations must implement formal policies and procedures across domains such as network security, access control, and data protection. Level 2 addresses more complex threats and helps ensure that sensitive defense-related information is handled securely.
Achieving Level 2 signals that your organization is capable of protecting CUI and meeting DoD expectations for stronger cyber defense.
CMMC Level 3: Expert
Level 3 is intended for organizations that manage highly sensitive DoD information and face advanced persistent threats. It requires a fully mature cybersecurity program with continuous monitoring and response capabilities.
Key expectations include:
- Advanced threat detection and response
- Strict access controls across all systems
- Ongoing risk analysis and mitigation
- Detailed incident handling procedures
CMMC Level 3 demonstrates that an organization is equipped to defend critical national security information and operate securely under constant threat.
In summary, the CMMC framework provides a tiered approach to cybersecurity:
- Level 1 protects FCI with basic controls
- Level 2 protects CUI with advanced safeguards
- Level 3 protects the most sensitive data through expert-level security programs
Each level builds on the one before it, giving DoD contractors a clear roadmap for strengthening their cybersecurity posture and meeting federal requirements.
Key Components of CMMC Level 2 Compliance
Achieving CMMC Level 2 compliance requires organizations to meet stringent security standards designed to protect CUI.
These standards are derived from the National Institute of Standards and Technology Special Publication (NIST SP) 800-171, encompassing 110 security controls across 15 domains.
These domains collectively cover a comprehensive range of cybersecurity practices, each critical to maintaining a secure environment within the defense industrial base. Understanding these components is essential to achieving compliance and ensuring the safety of sensitive information.
Let’s take a look at some of the CMMC domains:
CMMC Domain Overview
CMMC Level 2 introduces additional domains that go beyond basic cyber hygiene. Each domain addresses a specific aspect of cybersecurity needed to protect Controlled Unclassified Information (CUI) and reduce exposure to targeted threats.
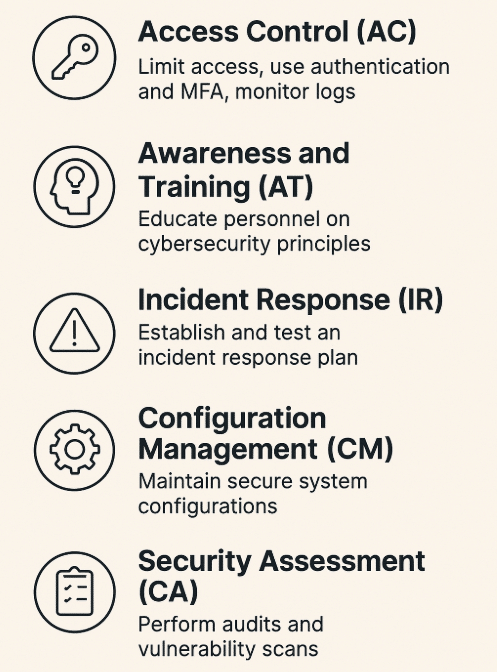
1. Access Control (AC)
This domain focuses on controlling who can access systems and data. It requires organizations to implement strict identity and access management policies. Key practices include user authentication, role-based access control, use of multi-factor authentication, and regular monitoring of access logs to detect unauthorized activity.
2. Awareness and Training (AT)
Organizations must ensure that all personnel understand basic cybersecurity principles. This includes ongoing training on how to spot phishing attempts, securely handle data, and follow proper procedures during incidents. Building consistent awareness across teams helps reduce user-driven security risks.
3. Incident Response (IR)
This domain outlines how to detect, manage, and recover from cybersecurity incidents. A complete incident response plan should cover detection, analysis, containment, eradication, recovery, and lessons learned. A tested plan limits damage and shortens recovery time after an attack.
4. Configuration Management (CM)
Maintaining secure and consistent system configurations is essential. This includes setting baseline configurations, applying change control procedures, and performing regular audits to catch unauthorized changes. Proper configuration reduces system vulnerabilities and supports ongoing compliance.
5. Security Assessment (CA)
Organizations must regularly test their security controls. This includes internal audits, control assessments, and vulnerability scans or penetration tests. The goal is to identify weaknesses, verify that protections are working, and adjust as needed to stay compliant with CMMC Level 2 standards.
Additional Domains
Other CMMC domains also contribute to a strong security posture, including:
- Audit and Accountability: Track user activity and retain logs for analysis.
- Identification and Authentication: Require unique user identification and strong login controls.
- System and Communications Protection: Secure data in transit and at rest.
- Maintenance: Control and document system maintenance activities.
- Risk Management: Assess and prioritize risks based on business impact.
- Physical Protection: Restrict physical access to equipment and sensitive areas.
Each domain plays a role in reducing exposure to critical security risks and supporting ongoing compliance. CMMC Level 2 builds on the foundation set at Level 1, requiring broader and deeper control coverage.
Does My Business Need CMMC Level 2?
You likely need CMMC Level 2 if your business receives, stores, processes, or transmits Controlled Unclassified Information (CUI) on behalf of the Department of Defense. This level applies to contractors and subcontractors that handle CUI as part of their work within the defense industrial base.
The following conditions will require your business to meet CMMC Level 2 requirements:
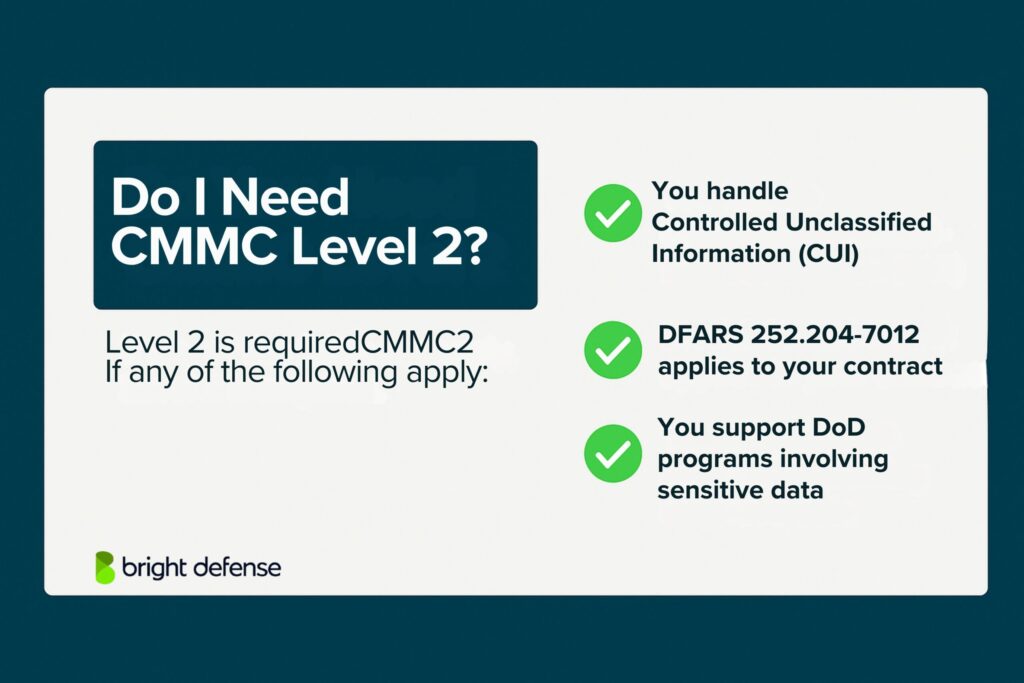
- You receive, store, process, or transmit Controlled Unclassified Information (CUI)
- Your contracts include DFARS clause 252.204-7012
- You support Department of Defense programs that involve sensitive but unclassified data
- You act as a prime contractor or subcontractor and handle CUI in any capacity
- You must comply with the security requirements in NIST SP 800-171
If your work involves only Federal Contract Information (FCI) and not CUI, CMMC Level 1 may be sufficient. But once CUI is part of the picture, Level 2 becomes a requirement.
Does Your Business Handle Controlled Unclassified Information (CUI)?
If your business deals with Controlled Unclassified Information (CUI), you likely need CMMC Level 2 compliance. CUI refers to sensitive but unclassified information that requires safeguarding or dissemination controls. Examples include:
- Technical data related to defense projects
- Engineering designs and blueprints
- Manufacturing processes and specifications
- Sensitive personnel records
Are You a Defense Contractor or Subcontractor?
If your business has contracts with the DoD or works as a subcontractor for a primary defense contractor, CMMC Level 2 compliance will likely soon be mandatory. This requirement ensures that all entities in the defense supply chain maintain a consistent level of cybersecurity to protect sensitive information.
Are You Planning to Bid on DoD Contracts?
If your business plans to bid on DoD contracts in the future, CMMC Level 2 compliance might be a prerequisite. The DoD is incorporating CMMC requirements into its contracts, focusing on Level 2 for most defense-related work. This inclusion means businesses seeking DoD opportunities must demonstrate compliance with CMMC standards.
Are You Looking for a Competitive Advantage?
Achieving CMMC Level 2 compliance can give your business a competitive edge. Demonstrating that your cybersecurity practices meet stringent standards shows potential clients and partners that you take security seriously. This assurance can help your business stand out in a crowded market.
Are You Required to Follow Federal Regulations?
CMMC Level 2 aligns with several federal regulations, such as the Federal Acquisition Regulation (FAR) and the Defense Federal Acquisition Regulation Supplement (DFARS). If your business is subject to these regulations, CMMC Level 2 compliance might be necessary to meet legal and contractual requirements.
Do You Want to Reduce Cybersecurity Risk?
Even if your business isn’t directly involved with DoD contracts, achieving CMMC Level 2 compliance can help mitigate cybersecurity risks. The robust cybersecurity practices required by CMMC Level 2 can protect your business from cyber threats, reducing the risk of data breaches, financial losses, and reputational damage.
Practical Steps for Achieving CMMC Level 2 Compliance
Below are the core activities involved in reaching compliance, along with what each one involves and how it strengthens your security posture:
Steps for Achieving CMMC
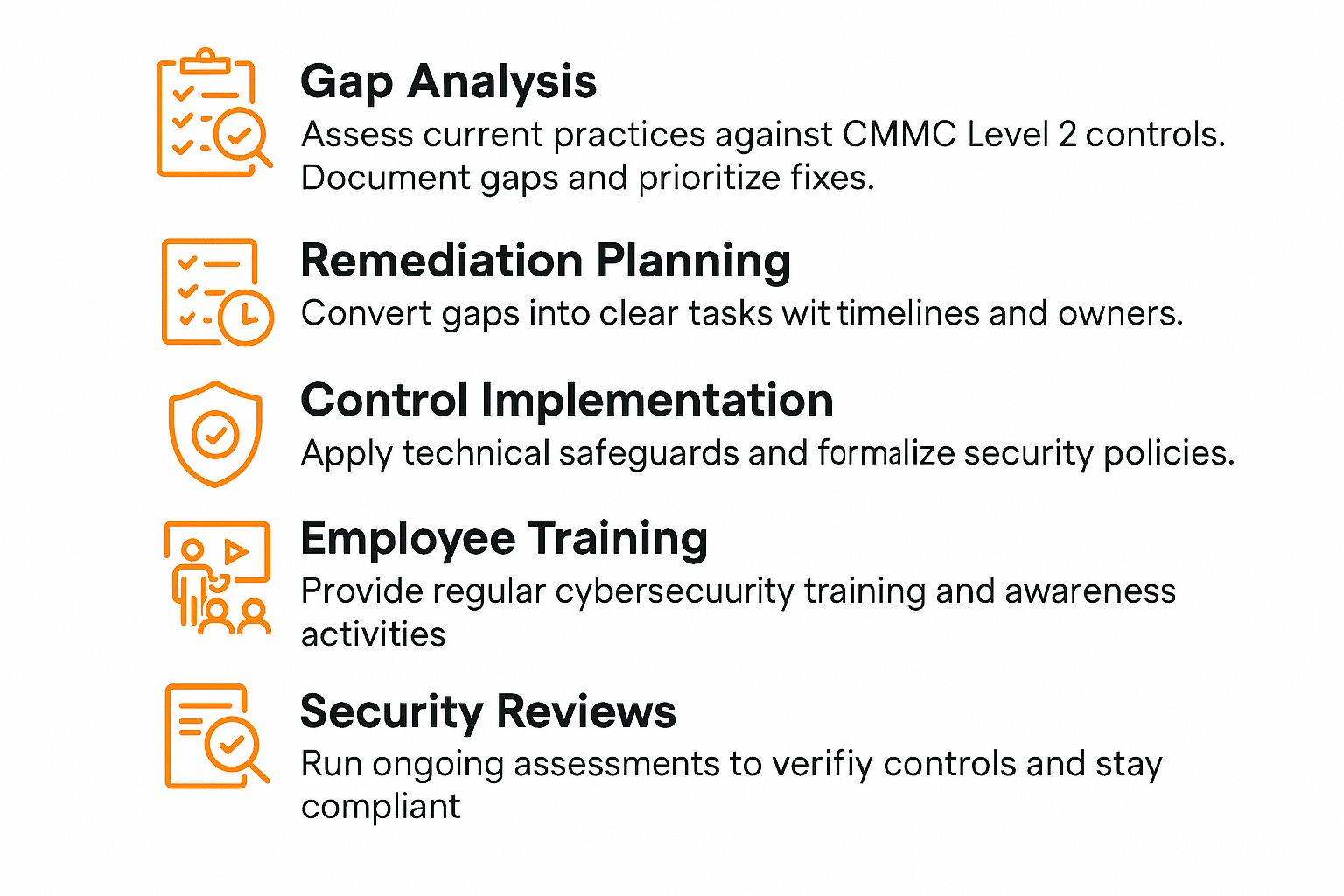
1. Conducting a Gap Assessment
Conducting a CMMC gap assessment is one of the most important parts of CMMC compliance. Start by reviewing the CMMC Level 2 Assessment Guide to understand all 110 requirements across 15 domains. Compare each requirement against your current cybersecurity practices.
Document where your organization is fully, partially, or not compliant, and collect supporting evidence such as logs, configurations, or policy documents.
Use this comparison to build a clear map of your gaps, and prioritize them based on risk and complexity. This forms the foundation of your compliance plan.
Challenges:
Many organizations lack the internal expertise or tools to evaluate themselves against such a detailed standard.
How Bright Defense Helps:
We deliver comprehensive gap analyses that identify and prioritize the actions needed to meet every CMMC Level 2 requirement.
2. Developing a Remediation Plan
Once the gaps are identified, convert them into specific, actionable items. For each item, define what needs to be done, who will be responsible, and how much time and resources are required.
Create a schedule with realistic timelines and milestones. Make sure tasks are clearly assigned and progress is tracked regularly.
A strong remediation plan reduces uncertainty and helps keep your compliance efforts on schedule and within scope.
Challenges:
It can be difficult to create realistic timelines, assign resources, and map specific fixes to complex requirements.
How Bright Defense Helps:
We help build remediation plans that are both practical and aligned with CMMC expectations, including budgeting and milestone tracking.
3. Implementing Technical and Administrative Controls
To meet CMMC Level 2 requirements, your organization will need to enforce both technical safeguards and written policies. This includes secure configurations, data encryption, role-based access control, and endpoint protection.
At the same time, you should formalize policies covering access control, incident response, system use, and other critical areas. Each control must be implemented, tested, and documented to demonstrate compliance.
Challenges:
Organizations may lack staff with the experience to deploy security controls or formalize policies.
How Bright Defense Helps:
Our consultants assist in deploying both the technical and procedural elements required under CMMC Level 2.
4. Training Employees and Building a Security Culture
Employees should receive regular training on cybersecurity best practices, including how to identify phishing attempts, report incidents, and handle sensitive data.
Use training platforms to assign content and track completion. Reinforce training with simulated phishing tests and ongoing awareness campaigns. A security-aware workforce strengthens your defenses and supports long-term compliance.
Challenges:
Consistent training is hard to maintain, especially across distributed or large teams.
How Bright Defense Helps:
We deliver tailored training programs and serve as a KnowBe4 managed service provider to support ongoing education and awareness.
5. Conducting Regular Security Assessments and Reviews
CMMC compliance isn’t a one-time event. Regular reviews are necessary to ensure controls stay effective. Use automated tools where possible to monitor control performance and gather evidence. Review system logs, control settings, and training records to verify that practices remain in place.
Document any findings and take corrective actions as needed. If possible, consider bringing in a third party to validate your controls and provide external insight.
Challenges:
Frequent audits can stretch internal teams thin and are often overlooked once initial certification is reached.
How Bright Defense Helps:
We perform assessments, review control effectiveness, and provide actionable recommendations to maintain compliance.
Navigating the CMMC Assessment and Certification Process
Navigating the CMMC assessment and certification process might seem daunting. However, understanding it can considerably ease the journey. CMMC Third-Party Assessor Organizations (C3PAOs) play a crucial role in this process. They are responsible for conducting complete CMMC assessments.
Understanding the Role of C3PAOs in CMMC Certification
Certified Third-Party Assessment Organizations (C3PAOs) are central to the CMMC process. C3PAOs conduct thorough assessments to determine whether an organization meets the specific requirements of the CMMC framework.
These assessments are detailed and cover a wide range of cybersecurity practices and processes, including access controls, data encryption, incident response, and employee training.
The assessment outcomes determine if an organization is granted CMMC certification, which is essential for obtaining or maintaining contracts with the DoD.
C3PAOs must be authorized and certified by the CMMC Accreditation Body (CMMC-AB). This certification process ensures that C3PAOs have the expertise and integrity to carry out rigorous assessments.
The CMMC-AB provides training and sets strict criteria that C3PAOs must meet before they can conduct CMMC assessments. This approach ensures a high level of consistency and reliability across all C3PAOs, providing confidence in the certification process.
CMMC Rule-Making Process and Timeline
The Cybersecurity Maturity Model Certification (CMMC) framework is undergoing a comprehensive rule-making process, designed to ensure that its requirements are practical, comprehensive, and adaptable to the evolving cyber threat landscape. This process involves several key stages, including public commentary, regulatory review, and finalization.
Overview of the Rule-Making Process
The rule-making process allows the U.S. Department of Defense to refine the CMMC framework based on feedback from stakeholders, ensuring it aligns with current cybersecurity trends and risks. The ultimate goal is to create a robust certification program that enhances the cybersecurity posture of the defense industrial base.
As of now, the DoD is in the final stages of this process, with a planned rollout of the updated CMMC 2.0 framework. Defense contractors are encouraged to start preparing for these changes, as the implementation timeline depends on the rule-making process’s completion.
Timeline Highlights
- November 2021: The DoD announces CMMC 2.0, a simplified and streamlined version of the original model. The estimated timeframe for rule-making is set at 9-24 months.
- March 2023: The proposed CMMC rule is submitted to the Office of Management and Budget (OMB) for regulatory review.
- November 2023: The regulatory review process concludes, allowing for the publication of the proposed rule.
- December 25, 2023: The proposed CMMC rule is published in the Federal Register, initiating a 60-day public comment period where stakeholders can provide feedback.
- Early 2024 (Tentative): The DoD addresses public comments and issues the final version of the CMMC rule.
- Q1 2025 (Estimated): CMMC requirements start appearing in new DoD contracts, marking the beginning of a phased implementation process.
Current Stage and Next Steps
The DoD is nearing the release of the proposed rule, and stakeholders are encouraged to review its details and prepare to offer feedback during the public comment period. The input received will help the DoD refine the rule before issuing the final version.
Following the rule’s finalization, the DoD will gradually integrate CMMC requirements into new contracts. Contractors should take a proactive approach by aligning their cybersecurity practices with the updated framework to ensure compliance when the CMMC requirements become mandatory.
Summary
CMMC Level 2 compliance is a transformative step towards enhanced cybersecurity. It requires a thorough understanding of the core components, access control strategies, system security plans, incident response preparedness, and protective measures for physical infrastructure and personnel security. Moreover, adopting a risk management approach and a culture of continuous improvement is crucial. Navigating the CMMC assessment and certification process can seem daunting, but understanding the role of C3PAOs and preparing your organization effectively can ensure a successful journey.
Bright Defense Delivers CMMC Compliance!
If you’re ready to achieve CMMC compliance, Bright Defense can help. Bright Defense’s CMMC Registered Practitioners will build a robust cybersecurity program that meets NIST and CMMC standards. Our continuous compliance offering also automates your compliance journey, improving efficiency and lowering the cost of compliance.
Do you need to meet multiple security frameworks? No problem. We can also help you achieve SOC 2, HIPAA, ISO 27001, PCI, and more. Contact Bright Defense today to get started on your compliance journey.

Frequently Asked Questions
What is CMMC Level 2 compliance?
CMMC Level 2 compliance extends the protection of federal contract information to include Controlled Unclassified Information (CUI) and guards against sophisticated cyber threats, contributing to national security.
What is the role of C3PAOs in CMMC certification?
C3PAOs play a crucial role in the CMMC certification process by evaluating and verifying an organization’s compliance with CMMC standards.
What is the importance of a System Security Plan (SSP) in CMMC Level 2 compliance?
A System Security Plan (SSP) is crucial for CMMC Level 2 compliance as it details how an organization is implementing required cybersecurity policies and procedures. This is important to ensure adherence to the mandated security measures.
What are the key components of CMMC Level 2 compliance?
The key components of CMMC Level 2 compliance include satisfying all 110 security controls from NIST SP 800-171, which span across 15 domains and cover a broad range of cybersecurity practices.
What does incident response preparedness under CMMC Level 2 entail?
Under CMMC Level 2, incident response preparedness entails maintaining an operational incident-handling capability and regularly testing an incident response plan to effectively respond to security incidents. Testing this plan is crucial for readiness.
How does CMMC differ from NIST SP 800-171?
CMMC Level 2 requires full implementation of NIST SP 800-171 controls, but also includes a certification process conducted by third-party assessors. NIST SP 800-171 alone relies on self-attestation, while CMMC adds formal verification.
Who needs to comply with CMMC Level 2?
Any organization handling Controlled Unclassified Information (CUI) as part of a Department of Defense (DoD) contract will need to achieve Level 2 certification before being awarded the contract.
How often must organizations undergo CMMC assessments?
For Level 2, assessments must be completed every three years by an authorized C3PAO. Interim self-assessments may also be required depending on contract terms or internal policy.
What happens if an organization fails a CMMC Level 2 assessment?
If an organization fails, it receives a failed determination report. The organization can then correct the gaps and request a reassessment within a specified timeframe, usually up to 180 days.
Yes, if subcontractors handle CUI, they must meet the same CMMC Level 2 requirements as the prime contractor. This ensures all parties with access to sensitive data meet the expected cybersecurity baseline.
CMMC Level 2 includes 110 practices, identical to those in NIST SP 800-171. These practices are grouped into 14 families, such as Access Control, Audit and Accountability, and Incident Response.
At a minimum, organizations must maintain a System Security Plan (SSP), a Plan of Action and Milestones (POA&M), and supporting evidence for each implemented practice. Auditors will review these documents during the assessment.
A POA&M outlines any deficiencies or incomplete practices and the plan to correct them. While CMMC assessments require most practices to be fully implemented, limited use of a POA&M may be allowed under specific conditions and timeframes.
The scope includes all assets that process, store, or transmit Controlled Unclassified Information (CUI). Defining the scope helps limit the environment being assessed, reducing the number of systems that must meet all 110 controls.
Assets are classified as CUI assets, security protection assets, contractor risk-managed assets, or specialized assets. Only CUI and security protection assets must meet all applicable practices.
eMASS is a platform used to manage and store assessment artifacts and results. It serves as the central repository for tracking an organization’s compliance and assessment status for the Department of Defense
Costs vary based on organization size, complexity, and assessor rates. Estimates range from $30,000 to over $100,000 for initial certification. Preparing for the audit often adds additional cost for consulting, gap analysis, and remediation.
Auditors may request system screenshots, configuration files, access logs, employee training records, incident reports, and interview transcripts to validate compliance with each practice.
Only DoD contractors that do not handle CUI may be exempt or fall under CMMC Level 1, which involves fewer requirements. All contractors with CUI exposure must meet at least Level 2.
The Department of Defense expects to phase in CMMC Level 2 across contracts starting in fiscal year 2025. Full enforcement is expected by 2026, pending final rulemaking.
Get In Touch



